The cybersecurity landscape is evolving, with new threats and defense strategies emerging in various situations. In this context, a principal requirement for any cybersecurity professional is an understanding of ethical hacking and adherence to the associated code of ethics. The emphasis in this topic is on ethics; a cybersecurity professional must follow a code of ethics when protecting the information and intellectual property of employees and customers, as this information is sensitive. Failing to do so can lead to the compromise of confidential data and a loss of trust.
Thinking Like an Attacker: The Foundation of Cyber Intelligence
Thinking like an attacker naturally leads to a deeper understanding of threats, whether from malicious actors or harmful activities. Given the constantly evolving threat landscape, it’s essential to develop a cyber intelligence capability that delivers accurate insights into how known adversaries might exploit existing vulnerabilities. This enables organizations to take appropriate measures to mitigate risks and protect their assets.
One definition of intelligence is the ability to acquire knowledge or skills. In the context of cybersecurity, this concept has two key definitions:
- Cyber intelligence refers to the ability to gather knowledge about an organization’s environment, including its current conditions and capabilities, in order to anticipate potential adversary actions that exploit vulnerabilities.
- Cyber threat intelligence, on the other hand, involves analyzing an adversary’s intent, opportunity, and capability to conduct malicious activities.
Analyzing the adversary’s intent in the cyber intelligence scenario is very important. Adversaries typically don’t launch a single, isolated attack; instead, they carry out a series of coordinated steps to infiltrate an organization and access sensitive data or services. These stages are collectively known as the Cyber Kill Chain.
The Cyber Kill Chain: Understanding Attack Stages
The concept of the Cyber Kill Chain originated in military contexts to describe the structure of physical attacks. Lockheed Martin later adapted this framework to the digital domain, coining the term “Cyber Kill Chain” to outline the stages advanced adversaries typically follow to compromise systems. The model consists of seven primary stages:
- Reconnaissance: The adversary gathers information about the organization’s environment, infrastructure, and personnel to identify potential targets.
- Weaponization: Based on the gathered intelligence, the adversary creates or customizes malware or malicious tools tailored to exploit specific weaknesses.
- Delivery: The malicious payload is delivered to the targeted assets, often through phishing emails, malicious links, or compromised websites.
- Exploitation: The adversary exploits vulnerabilities or security flaws in the target environment to gain initial access.
- Installation: After successful exploitation, the adversary installs malware or backdoors to establish persistent access, often with elevated privileges.
- Command and Control (C2): The compromised system establishes communication with the adversary’s external infrastructure, enabling remote control and further actions.
- Actions on Objectives: Finally, the adversary uses their access to achieve specific goals, such as stealing sensitive data, disrupting operations, or manipulating information for gain.
Due to increasingly sophisticated threats and often inadequate defenses, preventing security breaches has become more challenging, and detecting them takes significantly longer. On average, adversaries remain undetected within an organization for 11 days (Mandiant, 2025). Fully eradicating them can take weeks or even months (Kaspersky, 2024). This duration, during which an attacker maintains persistent access through malicious processes on one or more systems, is referred to as dwell time.
Reconnaissance: Mapping Adversary Behavior Through MITRE ATT&CK and the Pyramid of Pain
A very popular framework for threat actor analysis is the MITRE ATT&CK framework. This framework provides information on TTPs (tactics, techniques, and procedures).
The MITRE ATT&CK framework is a comprehensive knowledge base developed by the MITRE Corporation to classify threat actor objectives and document the specific tools, techniques, and behaviors used to achieve them. ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge.
This framework organizes adversarial techniques into 14 high-level tactics, with each tactic representing a specific short-term objective within an overall attack strategy. Below is the list of the 14 tactics.
- Reconnaissance
- Resource Development
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Exfiltration
- Impact
David Bianco created another important model called the Pyramid of Pain to enhance understanding of threat analysis scenarios. This model, as seen in Figure 1, illustrates the relationship between different categories of indicators and the effectiveness of defending against them.
The model highlights the impact of defensive measures by showing the effort required by a threat actor to alter their attack strategy once a robust defense is implemented for a specific category of indicators. For example, if an attacker changes the hash value of a malware sample by altering a single bit initially, they can do so at a low cost. Because this kind of change is trivial to execute, this type of modification is placed at the base of the Pyramid of Pain.
As you move up through the pyramid, from changing IP addresses to domain names to host artifacts, the challenges faced by adversaries move from “easy” to “annoying” because more activities are involved, and related expertise is needed to implement these modifications. The top of the pyramid involves a more difficult type of change; for example, changing a tool requires modifying algorithms and executing a collection of software tests to validate the modifications made. This process is expensive, complex, and time-consuming to execute and finish.
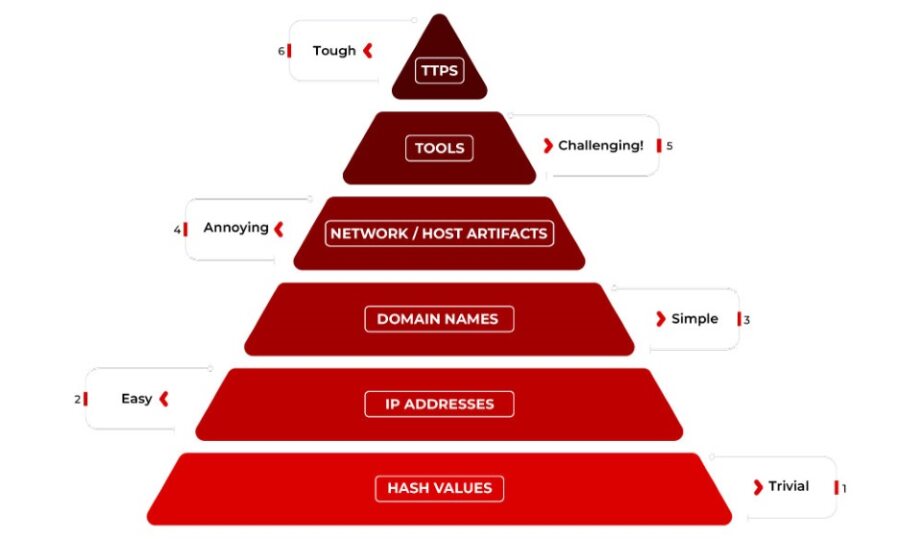
Figure 1. The Pyramid of Pain Model (David J. Bianco, 2014)
By integrating these concepts and frameworks, it is possible to initiate a critical activity known as threat hunting.
The primary goal of threat hunting is to reduce dwell time, thereby minimizing the damage and losses an organization may suffer as a result of security breaches. Threat hunting involves actively searching for evidence of malicious activities across organizational systems and networks to identify weaknesses, data breaches, or other signs of compromise.
This offense-driven approach adopts the adversary’s mindset, leveraging their tactics and techniques to detect and investigate threats that may bypass traditional security measures.
Effective threat hunting is:
- Proactive: Actively seeks out adversaries without waiting for alerts, identifying traces left even by the most advanced threat actors.
- Stealthy: Conducts investigations in ways that remain hidden from adversaries, avoiding detection during the hunt.
- Methodical: Follows a structured, logical approach to anticipate adversary behavior and pinpoint the most likely areas of compromise.
The hunting process must be capable of swiftly detecting and stopping adversaries at every stage of the Cyber Kill Chain, preventing them from gaining control of systems and minimizing potential damage to the organization.
Weaponization: Using Malware Analysis Insights
In the Cyber Kill Chain, step two is “weaponization,” and a very versatile and powerful cyber weapon is malicious software (malware) because of its high degree of customization and the profound impact it can have on the target.
In threat intelligence, malware analysis is critical to discovering how this weapon works, its capabilities and impact, and how to create signatures for threat detection.
- Signature-Based Detection: Static inspection of file checksums (MD5, SHA-1) and the presence of known strings or byte sequences in the binary
- Heuristic Detection: Static analysis of application behavior and identification of potentially malicious characteristics
- Sandboxing: Dynamic analysis of a program executed in a controlled environment where its actions are monitored
When malware bypasses defensive controls, the potential impact can be significant, depending on the specific malware family involved. Its presence within an enterprise environment often signals a gap or weakness in existing security measures. While identifying the malware family is a critical first step, failing to analyze its capabilities, persistence mechanisms, and other technical details can limit the ability to effectively triage and remediate the threat.
The process of malware analysis begins with examining and removing malicious code and applications. The primary objective is to recognize and understand the behavior, functions, and possible results of a malware sample and the threat it presents.
One essential tool used in the malware analysis process is Malcat. Malcat is an invaluable tool for inspecting binaries because it offers a powerful, feature-rich hexadecimal editor combined with a disassembler for Microsoft Windows and Linux. It supports examining more than 50 different types of binary files and has a fantastic capture of YARA signatures. Its intuitive GUI also makes the analysis easier and more fluid.
YARA signatures are powerful tools in malware analysis, enabling the identification of specific patterns within analyzed binary samples. They allow analysts to create descriptive rules for malware families based on textual or binary characteristics. Each YARA rule consists of a set of strings and a Boolean expression that defines the logic for matching those patterns.
A simple signature example is described in Figure 2.
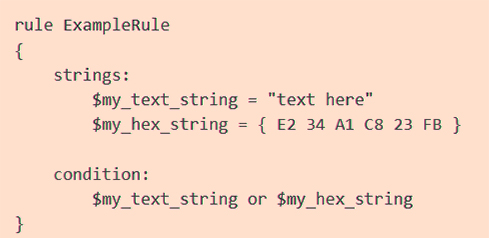
Figure 2. Simple Sample of Yara’s Signature
Figure 2 illustrates a rule consisting of two sections: string definitions and conditions. The string definition section specifies the strings that will be included in the rule. Each string is assigned an identifier that begins with a $ character, and these identifiers can be referenced in the condition section to refer to their corresponding strings. Strings can be defined in either text or hexadecimal formats.
Figure 3 illustrates some rules for analyzing a suspicious binary sample. It can be verified that this analyzed sample contains sensitive patterns involving changing browser configurations, downloading content from the internet, elevating privileges, and enumerating processes.
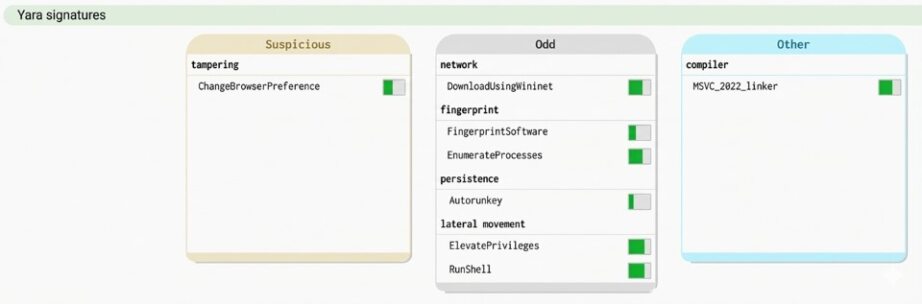
Figure 3. Real Signatures Classified by the Malcat Tool
Figures 4 to 6 illustrate rules for changing browser preferences, downloading content from the internet using the WinINet Windows API, and elevating privileges with the Windows API. In the three rules presented in these figures, we saw a specific string description for each matched case, and the condition was “any of them.” This means that the simple use of any of the strings detailed in the string section triggered this rule, and the tool signaled the presence of a suspicious sample in this binary sample.

Figure 4. Rule Description for Changing Browser Preferences
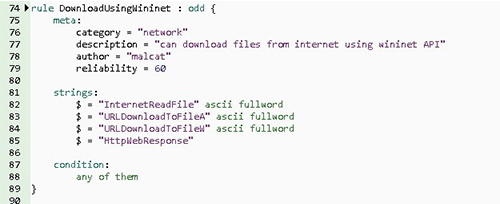
Figure 5. Rule Description for Downloading Internet Content
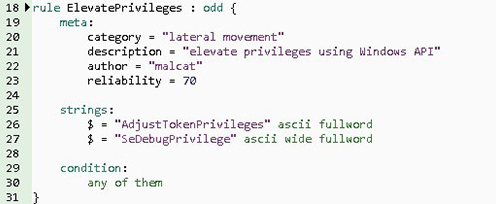
Figure 6. Rule Description for Elevate Privileges
Considering the dynamic global threat landscape, Mandiant released an interesting report in 2025 detailing the 10 most frequently observed MITRE ATT&CK techniques. Figure 7 presents this information, illustrating how attackers execute their strategies and providing insights into how we can effectively prepare to neutralize such attacks.
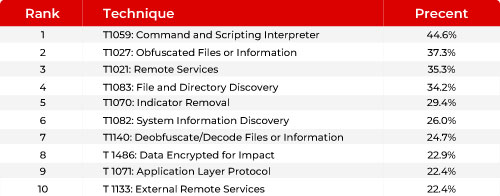
Figure 7. M-Trends 2025 Report: MITRE ATT&CK Techniques
Another important player in global threat monitoring is Netskope. Netskope Threat Labs releases an annual Cloud and Threat Report, offering strategic and actionable intelligence on emerging trends in cloud computing and cybersecurity threats impacting organizations globally. The most targeted applications for phishing campaigns in 2024 were cloud-based (Netskope, 2025). In these cases, attackers aim to sell stolen account access on illicit marketplaces where buyers may use it for business email compromise or to steal sensitive data.

Figure 8. Top Target for Phishing Campaigns
Conclusion
Ethical hacking, cyber threat intelligence, and malware analysis play important roles in cybersecurity. The main lessons related to these key aspects are how important it is to follow a code of ethics when conducting any activity in cybersecurity; this code of ethics should serve as a guide. The second main lesson is how important it is to have a solid knowledge of basic concepts, such as TTPs to classify threat actor objectives, organize adversarial techniques, and understand threat analysis scenarios. And finally, having a basic knowledge of malware analysis provides important skills that help in discovering how malware works, what your capabilities are, what your impact is, and how it’s possible to create signatures for threat detection.
Cybersecurity Tips
- To become an ethical hacker, it is essential to understand the responsibilities that come with handling private data.
- Familiarize yourself with the Cyber Kill Chain, the MITRE ATT&CK framework, and the concept of TTPs (Tactics, Techniques, and Procedures) for effective threat analysis.
- Learning about Yara Rules is an important first step in understanding how signature-based detection works.
- Stay informed about threat reports released by key players in threat analysis to recognize new malware trends and understand how they operate.
References
David J. Bianco. (2014, January 17). The Pyramid of Pain. https://detect-respond.blogspot.com/2013/03/the-pyramid-of-pain.html
Kaspersky. (2025). Kaspersky incident response report. https://content.kaspersky-labs.com/fm/site-editor/33/3318ec849851138088d24f26d236f469/source/irreport.pdf
Mandiant. (2025, April 24). M-Trends 2025 report. Google Cloud. https://cloud.google.com/security/resources/m-trends
Netskope. (2025). Cloud and threat report: 2025. https://www.netskope.com/resources/cloud-and-threat-reports/cloud-and-threat-report-2025
About the Author

Marcelo Diniz
Senior Software Engineer
Marcelo Diniz is a security researcher and senior software engineer with expertise spanning several areas, including security research, vulnerability assessment, reverse engineering, malware research and analysis, digital forensics, threat detection engineering, threat hunting, cyber intelligence, and penetration testing. He is currently employed at Netskope within the malware detection efficacy team, which is part of the Netskope Threat Research division. His responsibilities encompass developing the malware detection engine, conducting meticulous malware analysis, performing advanced reverse engineering, and designing and creating high-quality signatures and detection rules for mechanisms aimed at identifying malware and advanced threats.