With demand for cybersecurity jobs on the rise, many IT professionals are seeking to transition into information security roles. However, transitioning to a cybersecurity specialization can be challenging without structured guidance. To understand how the CEH certification enables professionals to confidently transition into security-focused roles and excel in them, EC-Council reached out to Saif Qusous, a certified ethical hacker and information security specialist in the FinServ industry. In this interview, Saif reveals how CEH helped him transition from IT to cybersecurity. He states that CEH significantly enhances real-world skills by strengthening professionals’ understanding of threats, defensive capabilities, and practical ethical hacking techniques. Combined with AI-driven automation and analysis, CEH-certified professionals gain deeper visibility into attacks, improved accuracy in assessments, and greater efficiency across all phases of ethical hacking.
What motivated you to pursue the Certified Ethical Hacker (CEH) certification?
My passion for cybersecurity and my expectations in the field motivated me to pursue the CEH certification. The CEH course not only met those expectations but exceeded them. It gave me exactly the kind of structured, practical, and valuable learning experience I was looking for.
How did the CEH certification contribute to your career goals and other aspects of your professional growth?
One of the most essential benefits of CEH was gaining access to a community of cybersecurity engineers. The practical experience, hands-on labs, and the depth of knowledge I gained significantly expanded my skills and confidence in cybersecurity.
Did CEH help you get higher pay, promotion, or the job you wanted?
Yes. I was initially an infrastructure engineer, and CEH enabled me to make a complete career shift. I have always been drawn to a career in information security, and today I serve as an Information Security Specialist at Ciaro Amman Bank. This transition occurred as a result of the CEH program.
What aspects of the CEH program were most valuable to you, and how did they contribute to your professional development?
The red-team and blue-team modules were extremely valuable. Although I had limited experience before, CEH opened my eyes to professional tools, realistic labs, and virtual machines that allowed me to practice effectively.
These skills directly enable me to defend my organization and apply cybersecurity methods in real-world environments. CEH strengthened my practical expertise and supported my current role.
In your experience, how widely recognized and respected is CEH in the cybersecurity industry and within your organization?
CEH is highly respected in the industry. In the organization where I currently work, the CEH certification is required prerequisite for joining the cybersecurity department.
I personally respect CEH because of its detailed modules, step-by-step explanations, and the depth it provides. You don’t need to constantly search for answers elsewhere; the course covers everything from A to Z. I strongly recommend it to my colleagues and other professionals.
Have you completed other cybersecurity courses? How does CEH differ in skills, knowledge, career opportunities, and overall value?
Yes, I have completed approximately 13 cybersecurity certifications and plan to pursue additional ones. However, CEH was my first certification, and it was the one that truly opened my eyes. It gave me strong foundational knowledge, —whether I was working as an IT, technical, or infrastructure engineer.
CEH taught me how to protect servers, routers, and entire environments. It provided tremendous value for both my career and my personal growth.
Have you completed Security+? How does CEH differ from Security+ and other certifications?
Yes, I have completed Security+. However, CEH is one of the most essential certifications for any IT or cybersecurity professional. It builds the core foundation needed to speak confidently about cybersecurity.
If you want to be a speaker, researcher, or industry contributor, CEH provides you with the tools, historical context, major attack case studies, impacts, reasons, and remediation strategies.
Mastering CEH provides a broader perspective —and if you are an instructor, it enables you to deliver real value to your audience.
Do you think IT professionals should pursue the CEH certification, and why is it important today?
Yes, absolutely. I was a perfect example of someone who benefited from CEH as an IT professional. I was a system administrator working with Windows servers, when I completed CEH in 2022, and it completely changed how I understood real-world attacks. The certification taught me how to defend Active Directory, identify DNS poisoning attempts, and recognize various other types of threats that I later encountered in real-world environments.
My awareness, skills, and ability to secure Windows systems against both insider and external attacks expanded significantly. Earning CEH while still a System Administrator was one of the best decisions I ever made.
Tell us about your journey as a cybersecurity professional.
My journey began with certifications. Even 10 years ago, I dreamed of working in cybersecurity. Recently, I completed a boot camp with the Central Bank of Jordan, and it was a turning point in my career. The boot camp included certifications such as CEH, CCT, CHFI, NDE, DFE, EHE, and more.
I am very glad to have attended that boot camp and proud of completing these certifications and the training provided by EC-Council.
Today, I work as an Information Security Specialist, and I genuinely feel this is the field where I belong. I am passionate about cybersecurity and excited to continue learning and expanding my knowledge in this field.
I still have three more EC-Council certifications planned, including CND, CCT, and CFI. In summary, I have found my purpose in cybersecurity, and I am deeply passionate about this field.
How has the integration of AI tools enhanced your ethical hacking skills and real-world efficiency?
AI now plays a significant role in almost every task. Instead of doing everything manually, you can ask AI to generate scripts, analyze data, automate tasks, or simulate attacks. AI has both positive and negative aspects. On one hand, it can help security professionals automate tasks, strengthen detection, and accelerate defensive strategies. On the other hand, it can also be used by threat actors to improve attack accuracy and success rates. In ethical hacking, AI is now essential for both offense and defense, and it must be considered in modern cybersecurity strategies.
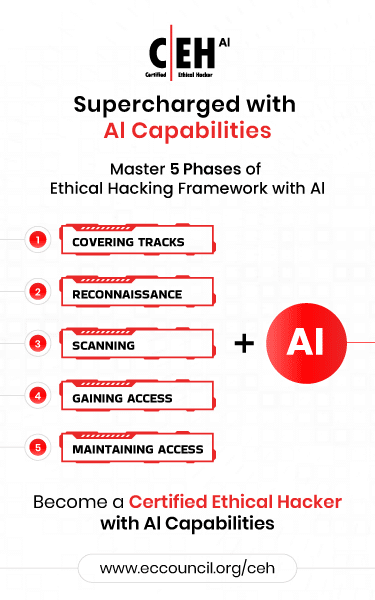
Can you share an experience where AI played a crucial role in one of the five phases of ethical hacking?
From my experience, AI can support every phase of ethical hacking.
For example:
- Reconnaissance/Footprinting: AI can generate tools or gather detailed information about companies or banks quickly.
- Scanning: AI can identify open ports, services, vulnerabilities, and misconfigurations far faster than manual scanning.
- Gaining Access: With CEH v13 integrating AI, ethical hackers can create AI-driven tools that automate exploitation.
- Persistence: AI can help generate scripts to maintain persistence efficiently.
- Covering Tracks: AI can assist in clearing logs or hiding activity in a more automated way.
AI is extremely powerful. It is —capable of assisting with both beneficial and detrimental tasks. It cannot distinguish intentions, which makes it essential for cybersecurity professionals to understand how to defend against AI-driven attacks.
Conclusion
CEH remains a highly valuable certification for IT and cybersecurity professionals, especially as AI reshapes modern attack and defense techniques. With the integration of AI in CEH v13 professionals can enhance their organization’s security posture, expedite threat detection, and remain prepared for evolving cyber risks. CEH remains a decisive step toward career advancement.
About the Interviewee
Saif Qusous is an accomplished Information and Cyber Security professional with expertise in enterprise security technologies, as well as defensive and offensive security practices. Committed to continuous learning and excellence, he recently completed a comprehensive boot camp with the Central Bank of Jordan, earning multiple industry-recognized certifications.