The governance, risk, and compliance (GRC) framework lies at the core of an organization’s information security policies. This regulatory approach allows businesses to minimize risk to their digital infrastructure and data while operating in a digital environment teeming with information security threats. This article is based on a recent webinar from EC-Council’s CyberTalks, which delved into the process of understanding, developing, and implementing a compliant risk management framework.
To maintain a resilient security posture, organizations should integrate risk, compliance, and resilience into a unified framework that operates in synergy. The interconnection between these three components ensures that an organization can effectively navigate challenges while aligning with legal, regulatory, and strategic objectives.
Risk management begins with identifying and understanding potential risks. Following this, a risk assessment determines the likelihood and potential impact of these risks on operations and overall company performance. Finally, risk mitigation strategies are developed to counter the identified risks.
Compliance focuses on adherence to applicable laws, regulations, and industry-specific standards. Organizations must also establish internal policies, procedures, and standards to embed compliance into daily operations.
Resilience cannot be achieved unless both risk and compliance are effectively managed. Once risks have been identified and compliance measures implemented, the foundation for long-term organizational resilience is established. When determining the most effective framework for their needs, organizations must consider the broader business landscape, overall strategic direction, and operational orientation.
How Information Security Unites GRC
A common question may arise regarding the significance of GRC in information security. In today’s digital landscape, where most business operations rely on information, the importance of information security cannot be overstated.
In the past, knowledge was considered the key to everything. However, in today’s information-driven era, success depends on having the right information and implementing an effective management system to utilize it properly and derive value from it.
Several critical outcomes can be achieved by developing, implementing, and managing a security program within an organization:
- Strategic alignment at the organizational level
- Establishment of a robust risk management system
- Extraction of value from data
- Resource optimization
- Effective performance measurement
- Integration of assurance processes
Risk Assessment and Management
Risk identification is the foundation of a successful information systems management framework. It is widely acknowledged that all risk-related processes begin at this stage.
A commonly used risk assessment framework—illustrated in the image below—outlines key steps that provide a structured approach to identifying and managing risks. While the framework is flexible and can be adapted to suit organizational needs, most risk assessment approaches follow a similar structure to ensure effective evaluation.
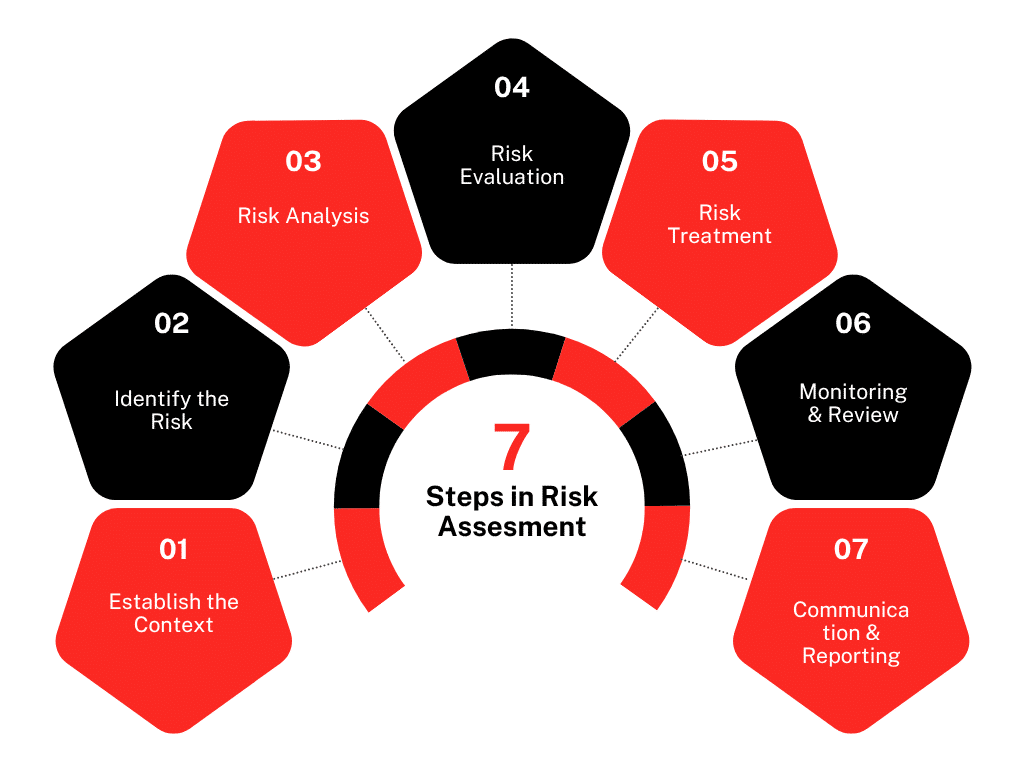
Risk Tolerance and Response
Once a structured risk assessment approach is in place, the next step is to define risk appetite and tolerance, where the former reflects the type of risk the organization is willing to accept, and the latter defines the maximum level of acceptable risk. These factors can be regulated via risk limit metrics that translate into measurable thresholds to ensure exposures remain within acceptable limits. Effective risk management involves a clear understanding of five key concepts: risk capacity, risk appetite, risk tolerance, risk target, and risk limit. These elements guide the selection of appropriate risk treatment strategies once risks are identified. Without a solid understanding of these principles, risk treatment decisions may lack relevance or effectiveness. After identification and analysis, the focus shifts to implementing appropriate responses—both technical and organizational. Risks should never be ignored; doing so can lead to significant operational disruptions or long-term harm. Unaddressed risks often escalate, becoming more damaging over time. Proactive management ensures resilience and sustained performance. Upon identifying a risk and evaluating possible responses, organizations choose from four standard response options:- Risk Termination: If a risk is deemed too severe, with a potential impact that far exceeds the organization’s risk appetite and tolerance, the related activity may be terminated altogether.
- Risk Transfer: If the risk is moderate but the organization lacks the necessary human or technological resources to manage it effectively, it may be transferred to a third party, such as an external service provider better equipped to handle it.
- Risk Mitigation: If the risk is manageable and its impact is not significantly harmful, organizations can implement measures to reduce its likelihood or severity.
- Risk Acceptance: If the risk’s potential impact is low and unlikely to affect security, privacy, or legal obligations, it may be accepted as a part of operational reality.
Effective Risk Management
Effective risk management doesn’t end with strategy development—it hinges on continuous performance evaluation. Field experience across various industries shows that even the most advanced risk management systems can fail without proper tools to assess their effectiveness. The selection of key risk indicators (KRIs) must be tailored to each organization and its sector. However, several guiding criteria can help identify meaningful metrics:- Focus on KRIs linked to high-impact risks. These indicators offer the most value and provide a strong foundation for risk measurement.
- Prioritize indicators that can be easily implemented, measured, and reported when multiple indicators offer similar sensitivity to risk changes.
- Combine quantitative (e.g., percentages, incident counts) and qualitative indicators (e.g., expert judgment, employee feedback) for a well-rounded assessment.
- Select KRIs that are reliable predictors or outcome indicators, as effective KRIs should show a high correlation with the risk they measure.
- Choose indicators that accurately reflect shifts in risk levels and directly represent the specific risks being tracked.
Compliance
Compliance is often misunderstood as solely a legal or HR issue; however, it’s a shared responsibility across all business units and leadership. For global companies, compliance is critical for avoiding penalties, protecting trust, and enabling secure cross-border operations. Maintaining compliance across jurisdictions requires ongoing legal, technical, and HR coordination, along with regular risk assessments and policy updates. Continuous employee training and the use of automation tools are essential to stay ahead of regulatory changes. Ultimately, compliance must be integrated into long-term business strategy, aligning with and supporting the organization’s evolving goals and risk landscape.Becoming and Staying Compliant
Compliance is not a one-time task but an ongoing process requiring continuous effort. Key frameworks like the General Data Protection Regulation (GDPR), which applies globally to any company handling EU citizens’ data, set the standard for data privacy. In cybersecurity, ISO/IEC 27001 guides the development and improvement of information security systems, which demonstrates strong data protection practices. The EU Cybersecurity Act further enhances trust by certifying ICT products and services against high-security standards. Together, these frameworks highlight the evolving nature of compliance and the need for sustained organizational commitment.Compliance Management Tools
Several compliance management tools are widely used across the industry. OneTrust, for example, is a comprehensive platform that supports privacy, security, and third-party risk management. It offers multiple components that assist organizations in maintaining compliance across various operational areas. MetricStream and WeComply are also recognized for their effectiveness in GRC management. These tools provide real-time alerts, support risk assessment activities, and help companies monitor their compliance status continuously. Based on firsthand experience, these tools have demonstrated strong value and reliability in maintaining compliance. In addition to these platforms, performance optimization techniques such as KPI benchmarking and balanced scorecards are recommended. The choice of tools and techniques ultimately depends on the organization’s specific needs and context. Companies are encouraged to evaluate which solutions best align with their compliance and performance objectives.Resilience
Resilience is rooted in agility, strength, confidence, motivation, and a readiness to embrace challenges and change. At its core, resilience in a business context means effectively integrating GRC. While the process may be complex, organizations must remember that the key lies in motivating people—the individuals working behind the scenes, who need to understand why staying compliant matters and how their role contributes to the organization’s broader resilience. To be truly resilient against incidents, cybersecurity threats, and unforeseen disruptions, a company cannot afford to let GRC operate in silos. GRC components must converge, forming a unified system where people collaborate, not in parallel, but in full synchronization. A solid and successful resilience framework naturally follows when teams align their efforts and integrate GRC effectively. To integrate GRC in practice, organizations should focus on the following six key elements:- Aligning security and business strategies
- Understanding organizational objectives
- Collaborating cross-functionally
- Cultivating a risk-aware culture
- Harmonizing policies
- Leveraging established frameworks
- Establishing metrics for successful GRC
- Define Key Metrics: Identify metrics that are meaningful for their industry, such as uptime for critical systems (tech) or customer data security (retail).
- Automate Data Collection: Use GRC platforms or automated tools to collect and analyze metrics like compliance rates, patching times, or incident trends.
- Set Benchmarks: Compare metrics against industry standards (e.g., average remediation time) to assess performance.
- Communicate Metrics Effectively: Create visual dashboards for executives, showing how metrics tie to business outcomes, such as cost savings from reduced fines or downtime.
- Review and Refine Regularly: Reassess metrics at least quarterly to ensure they remain relevant as business needs and risks evolve.
Challenges in GRC
Below are some of the most pressing challenges in GRC and practical strategies to address them:- Fragmented GRC Frameworks: Lack of integration between governance, risk management, and compliance functions leads to inefficiencies and duplication of efforts. To address this issue, organizations must implement an integrated GRC framework using technology platforms that unify processes and improve collaboration.
- Evolving Regulatory Landscape: Frequent shifts in regulations, such as GDPR updates and ESG mandates, make compliance increasingly complex. Organizations can manage these challenges by maintaining a dedicated compliance team and leveraging automated tools to monitor and adapt to regulatory changes.
- Cybersecurity Threats: Increasing reliance on digital platforms also increases the risk of cyberattacks. These threats can be mitigated by strengthening cybersecurity defenses with multi-layered security protocols, regular vulnerability assessments, and employee training.
- Global Operations and Cultural Differences: Organizations operating across multiple regions face challenges harmonizing GRC practices due to varying laws and cultural norms. To address this, organizations must develop localized GRC policies aligned with regional requirements while maintaining overall consistency.
- Lack of Real-Time Risk Monitoring: Traditional risk management approaches may fail to identify and address risks in real time. Deploying real-time risk monitoring systems that leverage artificial intelligence and machine learning to detect potential threats proactively could help resolve this challenge.
Conclusion
In order to build an agile cyber resilience, businesses must unify risk management, compliance, and resilience into a cohesive strategy. By identifying and mitigating risks, adhering to regulatory standards, and integrating these practices into operations, organizations can navigate the uncertain threat landscape with confidence and align security efforts with long-term strategic goals.About the Author

Ljubica Pendaroska
Ljubica Pendaroska is an award-winning cybersecurity expert, recognized as one of the Top 50 Women of Influence in Cybersecurity in Europe in both 2019 and 2021. She is a senior consultant, international trainer, and speaker specializing in data management, personal data protection, and privacy. Lubicha is the founder and President of Women4Cyber North Macedonia, part of the global Women4Cyber initiative.
With extensive experience leading projects for international organizations—including the European Union, World Bank, UN, and UNICEF—she has played a pivotal role in shaping data governance frameworks across both public and private sectors. Her tailored training programs have empowered professionals in future-focused companies across Europe and the Middle East. Ljubica’s work spans key markets such as the EU, Saudi Arabia, Qatar, the UAE, and Oman, where she continues to advance compliance, privacy, and cybersecurity awareness through strategic advisory and capacity-building efforts.









