Incident Handling & Response Career Path
Master the Skills for:
Network Security | Ethical Hacking | SOC Operations
Digital Forensics | Incident Response
Become an Incident Handling & Response Specialist
"*" indicates required fields
CERTIFIED PROFESSIONALS
IN 145 COUNTRIES






Incident Handling & Response Career Path
Master the Skills for:
Network Security | SOC Operations
Ethical Hacking | Incident Handling
Forensics Investigations
CERTIFIED PROFESSIONALS
IN 145 COUNTRIES






Become an Incident Handling & Response Specialist
"*" indicates required fields
Incident response is a structured approach to handling various security incidents, cyber threats, and data breaches. The incident response methodology aims to identify, contain, and minimize the cost of a cyberattack or a live incident. Cybersecurity professionals pursuing incident handling and response as a career require comprehensive training on Incident Handling and Response (IH&R) concepts and real-world scenarios. To help you build a career in Incident Handling and Response, we have created a career path that shows you the certification pathway you need to take to thrive as an Incident Handling and Response professional.

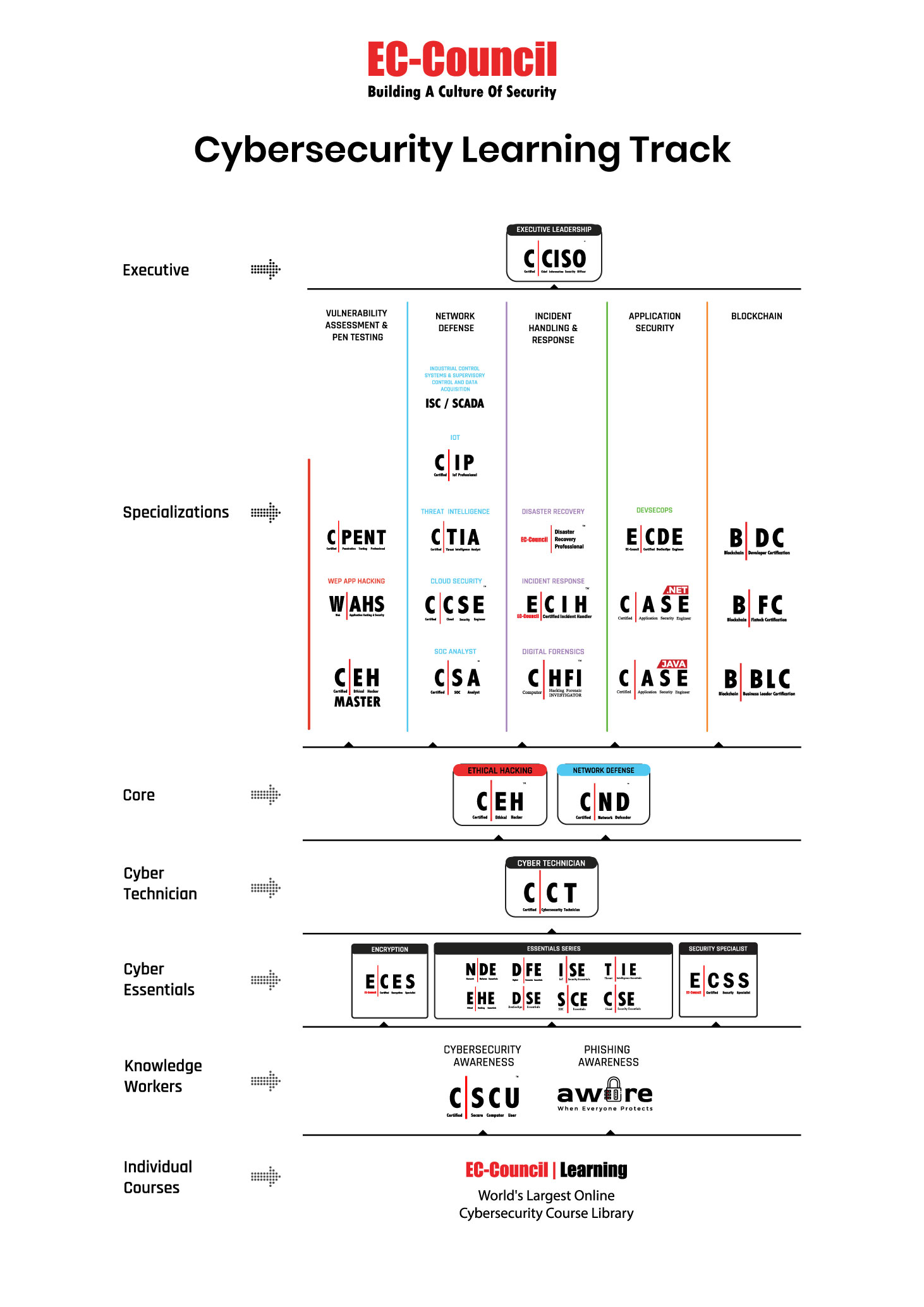
Your Pathway to An Incident Handling & Response Career:
CYBER ESSENTIAL
E|HE
N|DE
D|FE
C|SE
D|SE
I|SE
S|CE
T|IE
BEGINNER
C|CT
CORE
C|ND
C|EH Master
ADVANCE/SPECIALISATION
C|SA
C|HFI
E|DRP
E|CIH
Attain a basic core certification of the Certified Cybersecurity Technician (C|CT) to begin your professional cybersecurity course. C|CT will immerse students into well-constructed knowledge transfer through training, accompanied by critical thinking challenges and immersive, hands-on lab experiences allowing candidates to apply their knowledge and move into the phase of skill development right in the class.
Post C|CT, you need to grow your career path with the Certified Network Defender certification. You will learn to examine network traffic at the binary level, master TCP/IP protocol, introduce vulnerability assessments and hacking methodology, and much more. These are essential skills that a VAPT professional should possess, a good foundation to become a network security expert.
Once you have a solid foundation, you will be ready to move into ethical hacking with Certified Ethical Hacker (C|EH) course, Worlds No.1 Ethical hacking certification. C|EH learning framework Learn, Certify, Engage and Compete framework covers a comprehensive training program to prepare you for the certification exam and the industry’s most robust, in-depth, hands-on lab experience of any cybersecurity program available. The C|EH certification will help you get into the Hackers mindset and expose you to the 5 phases of ethical hacking, which will allow you to acquire the skills to become a competent professional in the world of incident handling and response.
In the Next course Certified SOC Analyst (C|SA) you will learn the fundamentals of SOC operations, before relaying the knowledge of log management and correlation, SIEM deployment, advanced incident detection, and incident response.
In the Computer Hacking Forensic Investigator (C|HFI) course; it will give you a firm grasp of digital forensics and evidence analysis that also pivots around the Dark Web, IoT, and Cloud Forensics. With C|HFI, you will learn a methodological approach to searching and seizing, chain-of-custody, acquisition, preservation, analysis, and reporting of digital evidence with hands-on experience in various forensic investigation techniques and tools.
Prepare to Handle and Respond to Cybersecurity Incidents with EC-Council Certified Incident Handler (ECIH)
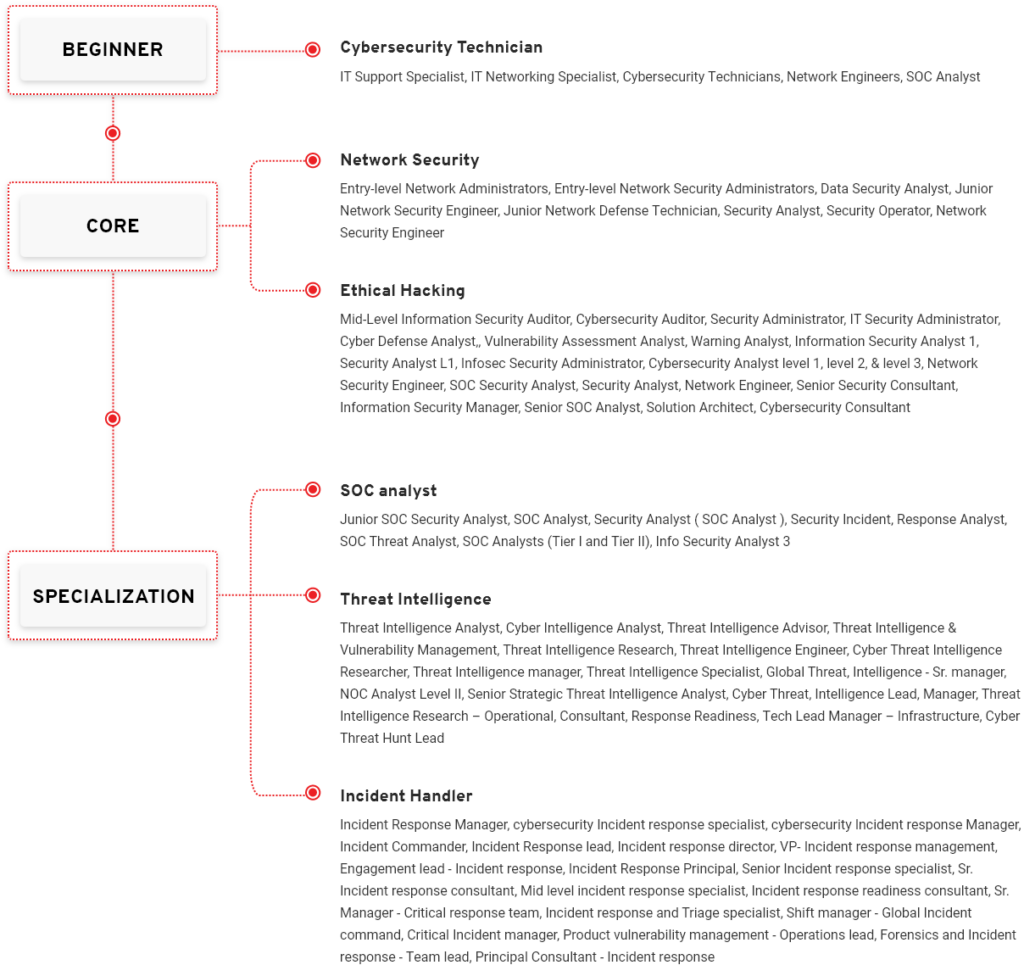
Job Roles Mapped to INCIDENT HANDLING & RESPONSE Career Path
Job Roles Mapped to Application Security Career Path
IT Support Specialist, IT Networking Specialist, Cybersecurity Technicians, Network Engineers, SOC Analyst
EC-Council Certifications Roadmap
Your Experience
Job Roles / Careers
Job Roles
Careers
Foundational Level
No Experience Required
Entry Level
1-2 years Basic Computer Knowledge
Core
More than 2 years Networking Knowledge
Specialisations
Core cybersecurity knowledge
Executive Leadership
5 years+
Job Roles
- Cloud Security Specialist / Engineer
- Security Architect
- Security Consultant
- Application Security Engineer
- Incident Responder
- Threat Intelligence Analyst
- Security Analyst
- Network Security Engineer
- Cloud Security Engineer
- DevSecOps Engineer
- Security Automation Engineer
- Red Team / Penetration Tester
- Malware Analyst
- CISO
Careers
- Blue Team
- DFIR
- Security Operations Team
- VAPT / Pen-Testing
Your Experience
Job Roles / Careers
Job Roles
Careers
Foundational Level
No Experience Required
Core
More than 2 years Networking Knowledge
Specialisations
Core cybersecurity knowledge
7 Reasons to choose INCIDENT HANDLING &
RESPONSE Career Path
- Growing Industry: Considering the recent hacks across the globe, it has become imperative for companies to keep their information and business secure, for which they need a formidable team of cybersecurity professionals skilled, especially in network security.
- Job Vacancies : Apply for Different Job Roles mapped to network security Career Path. With almost 3 million job vacancies globally, cybersecurity is an attractive industry.
- Rewarding : The salary of a network security engineer is $93,845 (as per salary.com), and that's just the beginning of your career.
- Begin and Build Your Rewarding Cybersecurity Career with World's No.1 and Highly Sought Cybersecurity Credentials.
- Accreditations : C|EH and C|ND courses are ANSI Accredited, and DoD (US. Department of Defense) Approved.
- Expert, Experienced Trainers & SMEs: Career path courses are developed and taught by EC-Council with 20 years of experience in cybersecurity training, industry experts, and professionals along with professional instructors with years of cybersecurity experience.
- Lab intensive courses to develop real world job skills.
Accreditations, Recognitions & Endorsements















