Misconfiguration:
According to Trend Micro, 65 to 70% of security breaches in the cloud happen due to misconfiguration. One of the common reasons for misconfiguration is the unfamiliarity with the infrastructure. Most business owners lack the technical know-how of cloud-based infrastructure, making them susceptible to threats. Another reason is that they do not have complete visibility and control over the infrastructure.Cloud API vulnerabilities
Application user interfaces (APIs) streamline cloud computing processes and easily facilitate sharing data between two or more applications. However, insecure APIs can open lines of communications for attackers to exploit, such as accessing organization-sensitive data or launching DDoS (Distributed Denial of Service) attacks.Shared technology vulnerabilities:
Cloud computing involves many shared technologies such as cloud orchestration and virtualization. Malicious actors can cause damage to many cloud users by exploiting vulnerabilities in any part of these technologies. Security is essential to maximize the benefits of cloud services. Look at why businesses need cloud security programs:How to Ensure Data Security in Cloud Computing?
While cloud computing has several advantages, organizations must be equally aware that data can be compromised if they do not take appropriate measures to safeguard it. The vast data collection in the cloud attracts hackers lurking around the corner. Thus, investing in cloud security training has become a vital part of businesses to minimize the risk of cyberattacks. Here are a few defensive measures that can make your cloud experience risk-free.Classify your data
Before migrating to the cloud, every organization should take the most important step, i.e., to classify its data. For instance, regulated (PII (Personally Identifiable Information) and PHI (Protected Health Information)) and proprietary information should have the highest priority, and thus more security controls should be enforced to protect them.Use Identity and Access Management (IAM) Solution
IAM allows organizations to store users’ access credentials and associated access permissions (Authorization) in a centralized location. By doing so, organizations can enforce password policy (creating complex passwords, preventing password reuse) on all users and ensure they can access only the resources they need to perform their assigned work. Keep in mind that IAM will not only be used to store users’ credentials, but the digital identities of systems, applications, services, and devices are also maintained the same way, which enhances the overall security of the cloud environment.Ensure Local Backup
One of the most crucial aspects to consider while managing data is to ensure that you have a local backup for sensitive data. Losing sensitive data could lead to significant monetary loss and attract legal action. Another backup type used in cloud environments is performing a “cloud backup or online backup,” where a copy of an organization’s cloud data is transferred automatically to another cloud storage location. This effectively helps organizations achieve their data backup strategy without increasing the workloads on IT department staff.Encrypt your data
One of the most effective ways to secure digitally stored and transmitted data is through encryption; this additional layer of security will help protect your data from unauthorized access.Protect endpoints devices
User’s endpoint devices, such as laptops, workstations, smartphones, and Internet of Things (IoT) devices, are used to access cloud data and services. If malware infects one of these devices, the infection could quickly spread to cloud storage (e.g., as with the case of ransomware). Endpoint devices must be adequately protected using different security solutions, such as antivirus, antimalware, and installing personal firewalls on each device (if applicable).Give users the minimal level of access to cloud resources
Organizations should apply the Principle of Least Privilege (PoLP) when operating in cloud environments. Users should only grant the permission needed to access the required data and applications they need to accomplish their tasks and nothing else.Establish cloud usage policies
Cloud policies are guidelines that all employees must follow when accessing an organization’s cloud data, applications, and services. Organizations should monitor their employees’ access to cloud resources and ensure they follow the enforced usage policy.Test the security measures in place
It is extremely important to identify vulnerabilities in your existing security strategies. Hire ethical hackers to evaluate the security position and expose loopholes.How is Incident Response Different in the Cloud? What are the Steps in the Cloud Incident Handling Process?
An organization’s incident response is the set of measures to respond and protect against a cyberattack. A security breach can wreak havoc; an incident response plan aims to reduce the damage and aid in faster recovery. As incidents of cybercrimes increase on a significant scale, incident response plans have become indispensable to the company’s defenses. Incident response strategies for cloud-based infrastructure and systems are different due to the shared responsibility model. Three key elements that set cloud incident response apart from the traditional incident response are :

Governance

Visibility

Shared Responsibility
The incident handling process in the cloud can be divided into four phases:
What is Incident Detection in Cloud?
Incident detection is integral to a company’s infrastructure security. It is the practice of monitoring networks, servers, and IT assets for any suspicious activity. It helps find intruders in your infrastructure and chart out appropriate incident response strategies. Intrusion detection is conducted at the network layer in traditional data center environments. However, in cloud incident detection must be conducted at three levels:
- Cloud Layer
- Network layer
- Compute (Virtual machines, containers, etc.)
If a security incident is identified, incident response solutions enable security teams to defend cloud applications and infrastructure from account compromise, insider threat, and access misuse.
Importance of Cloud Incident Response
In a utopia, cybercrimes will never occur, but cyberattacks are unavoidable. Organizations today need secure plans and strategies to minimize the risk of security breaches. Reputation, revenue, and customer trust are at stake in the event of a cyberattack. Like most security practices related to cloud applications, incident response is also a shared responsibility. Planning for cloud incident response is critical to ensure you have the right tools and guidelines to minimize the damage, both monetary and reputational. Having an incident response strategy that can enable collaboration of internal and external teams, track incident response processes and automate key security tasks is paramount during a crisis to contain issues quickly and respond effectively.
Cloud Incident Response Lifecycle
The incident response lifecycle is a step-by-step framework or guideline for identifying and responding to a security threat. It is a critical facet of any security posture to ensure data protection, avoid information breach, and protect the organization from being infiltrated. The incident response lifecycle is the unsung hero that works behind the scenes to resolve issues quickly and enable operations to continue unhindered. Effective incident handling is an integral part of security management.
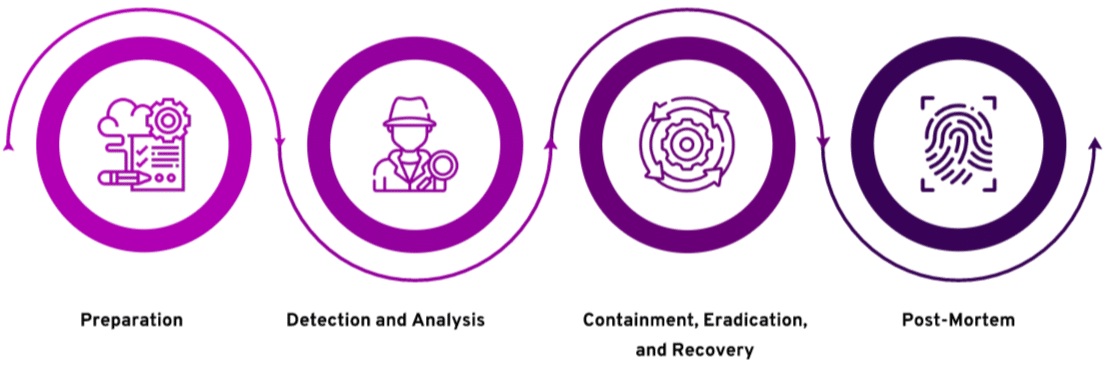
Preparation
Without predetermined guidelines, response teams cannot effectively address a security breach. Organizations must establish policies, procedures, and agreements for incident response management. It is important to create standards to enable seamless operations after an incident. Ensure you have the proper configuration and architecture to support incident response for faster detection and investigation.
Detection and analysis
Monitor security events to detect, alert and report on potential threats. Analysis can help organizations identify vulnerabilities and determine where to bolster the security posture.
Containment, eradication, and recovery
Isolate the compromised system or device from the rest of the network to prevent further spreading. Once all systems that the threat vector has compromised have been identified, perform a coordinated shutdown. Ensure all the infected devices have been wiped out and change passwords of all compromised accounts. Inherent cloud characteristics—such as auto-scale groups, API (Application Programming Interface) calls for changing virtual network or machine configurations, and snapshots—can speed up eradication, forensics, and recovery processes. The software-defined infrastructure allows you to rebuild from scratch in a clean environment.
Post-mortem
Conduct cloud forensics after each security breach to determine what worked and what didn’t. Cloud environments rely heavily on continuous improvement. Track and analyze incidents so that it helps you respond to future incidents more effectively. Identify patterns or weaknesses in your infrastructure and ensure additional security measures to prevent similar incidents. Cloud-based applications should leverage automation and orchestration to streamline and accelerate the response. An important aspect of incident handling for cloud-based resources is setting expectations around the customer versus the provider. In addition, it is important to embrace continuous and serverless monitoring of cloud-based resources to detect threats beforehand.
Best Practices for Cloud Incident Response
Since millions are at stake, businesses constantly evolve their incident response practices to thwart cyberattacks. To maintain a strong cybersecurity posture, organizations must constantly iterate their incident management process.
Here are some best practices to secure cloud computing:
Focus on monitoring systems
Use the best alerting tools
Protect your cloud logs
Follow shared responsibility model
Manage Access to Cloud Applications
Framework for Incident Handling in Clouds
- Preparation: Establish policies, procedures, and agreements to effectively address a security breach
- Detection and analysis: Monitor security events to detect, alert and report on potential threats and identify vulnerabilities
- Containment, eradication, and recovery: Ensures the cloud environment is brought back to its former functionality and use
- Post-mortem: Identify weaknesses and ensure additional security measures to prevent security breaches in the future
What is SOAR?
The term Security orchestration, automation, and response (SOAR) coined by the research firm Gartner refers to a collection of software programs that collects threat information, automates routine responses, and triages more complex threats, minimizing the need for human intervention. It allows organizations to streamline security operations in three key areas:



- Security Orchestration: Facilitates seamless operation between multiple software and hardware components
- Automation: Executes tasks such as scanning for vulnerabilities or searching for logs without human intervention and uses customized automation to deal with security risks.
- Response: What’s unique about SOAR is that it uses programmed automation to respond to security threats, for example, isolating devices or interrupting transfers.
Automation remains a vital component of responding to security incidents in a cloud environment. Automating incident response helps you scale your capabilities, rapidly reduce the scope of compromised resources, and reduce repetitive work by security teams. For instance, SOAR technology can be used as part of AWS incident response to unify workflows across cloud and on-premises infrastructure.
In today’s age of sophisticated cyberthreats, SOAR is the key to managing this unending stream of attacks. The main drivers for the rise in the adoption of SOAR are skills shortage, the evolution of advanced cyberthreats, and the increase of security alerts.
Benefits of SOAR
In an ever-growing digital world, cyberattacks have reached unprecedented sophistication. For analysts who are overworked and overwhelmed by the enormous volume of threat alerts, SOAR is like a knight in shining armor. The main purpose of SOAR is to provide a standardized process for data aggregation that automates threat detection and response processes, allowing analysts to take a breather. Many businesses have turned to this automated technology to ensure data security in cloud computing and improve their security posture.
Let us find out why companies need to invest in SOAR:
Improves efficiency
Monitoring many security technologies can be a huge strain on analysts. Instead of spending time on mundane tasks such as gathering and sorting through metrics and reports, SOAR platforms automate most of these tasks. Automated incident response takes the heat-of-the-moment guesswork out of event handling, limiting cyberattack dwell time and overall impact on the business.
SOAR helps organizations improve their productivity and capacity to address more threats. It helps security staff to work smarter rather than harder
Reduces response time
Optimizes Threat Intelligence
SOAR Increases Flexibility, Extensibility, and Collaboration:
SOAR provides organizations with the flexibility to either adapt the templated use case workflows or build new workflows and provides additional opportunities for collaboration. It collates all the data at everyone’s fingertips, making collaboration, problem-solving, and resolution easier and more effective.
Cutting business costs
Organizations will experience significant cost savings on reporting and alert handling. SOARs play a significant role in reducing the impact of breaches, as they minimize financial loss, disruptions to business operations and staffing costs.
How is SOAR different from SIEM?
Security Information and Event Management (SIEM) is a software solution that collects, analyzes, and stores security-related log data from different security tools (firewalls, ID/IPS, antivirus) and some networking appliances (e.g., proxies) for compliance or auditing purposes. In simpler terms, SIEM helps organizations recognize potential threats and vulnerabilities before disrupting business operations and ensuring data security in the cloud.
Though SOAR and SIEM have a lot in common, there are differences between their capabilities. They both collect data, but they differ in the quantity of data, type of data, and type of response. Let us explore some of their differences in detail:
Both SOAR and SIEM help security teams improve their efficiency. SIEM is better positioned for larger volumes of data with various kinds of sources and formats. SOAR takes the crown when it comes to automation capabilities, minimizing the need for human intervention to a great extent. Finally, SOAR stands tall due to its flexibility and extensive library of integration.
Security Incident Response in AWS
Organizations using Amazon Web Services (AWS) cloud should be prepared to detect and respond to security incidents and outline remediation methods that leverage automation to improve the response speed. It works under a shared responsibility model; this means AWS secures the underlying infrastructure, and cloud customers must protect their data and network. Security experts must continuously monitor the cloud environment and be equipped to respond to and mitigate the impact of potential breaches.
Here are some of the frameworks for AWS incident management:
- Establish the goal of responding to an incident
- Implement response patterns
- Preserve logs and other evidence in a centralized, secure cloud account
- Ensure that your response mechanisms are safe
- Automation is extremely useful. Build mechanisms that programmatically triage and respond to common situations and use human responses for new incidents
- Attempt to reduce response time
- Learn and improve your response process
The foundation of a successful AWS incident management program is to educate, prepare, simulate, and iterate:
- Educate your security team about cloud technologies and how your organization intends to use them
- Prepare the incident team to detect and respond to threats by ensuring access to necessary tools and services. Prepare runbooks, both manual and automated
- Gauge the effectiveness of your incident response by simulating security events within the cloud environment
- Iterate on the outcome of your simulation to enhance the effectiveness of cybersecurity posture
These should help security analysts develop and implement incident responses practices within the AWS cloud environment.
Security Incident Response in Azure
To secure the workspace environment in Azure, it is of paramount importance to set up incident response processes. Running incident response in the cloud can seem daunting; predefining roles and responsibilities improve efficiency. Azure’s incident response lifecycle is a five-step process- Detect, Assess, Diagnose, Stabilize, and Close.
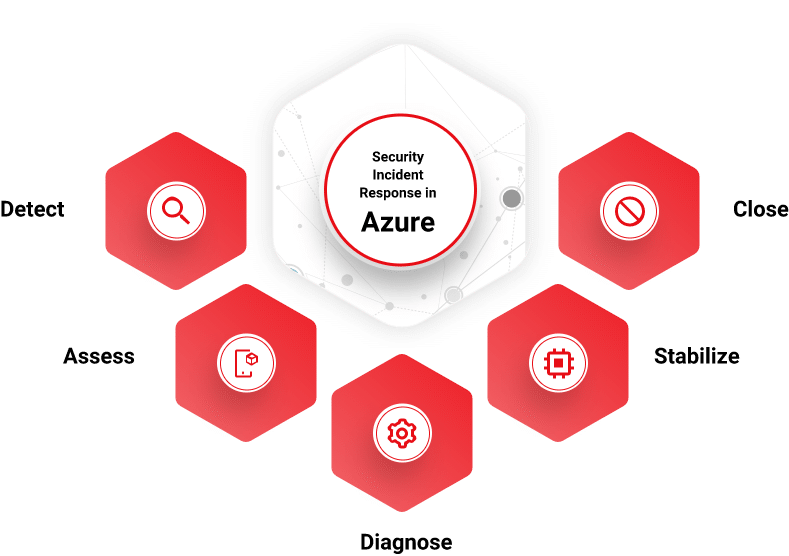
Detect
Security analysts need intelligence capabilities, detection tools, and incident management solutions to identify potential threats and suspicious activity.
Assess
Conduct a preliminary assessment. The security response team’s on-call member will then evaluate the threat and assess if there is a risk or not. It is imperative to assign the investigation an appropriate priority level. Events, where data is at imminent risk are treated as high severity and fixed as soon as possible. Assign a security incident manager to ensure that the incident response process is managed through the stages, including tracking cross-dependencies.
Diagnose
At this stage, analysts examine the collected data and information to better understand the event. The Security Incident Manager has the liberty to bring in additional subject matter expertise to aid in the investigation.
Stabilize and recover
This phase consists of processes designed to repair and restore services affected by a breach. This stage aims to take mitigation steps to resolve immediate security risks, ensure that threat has been successfully contained and corrective measures are being implemented, and identify additional mitigation strategies if needed. The process is tested to ensure that corrective measures are applied effectively to maintain operational success.
Close and post-mortem
After a security breach, an internal post-mortem will be conducted to identify technical or communications lapses, procedural failures, manual errors, process flaws that might have caused the incident. Response procedures are evaluated for sufficiency and completeness of operating procedures.
Security Incident Response in Google Cloud Platform
Identification
Automated and manual monitoring of security events to detect potential threats and vulnerabilities and report to the incident response team. Some of the tools and methodology employed by Google’s incident detection team are:- Automated analysis of network traffic
- Security alerts for incidents that may affect the company’s infrastructure
- Google employees detect an anomaly and report it
- External security researchers report potential technical vulnerabilities
- Conducts penetration tests, quality assurance measures, intrusion detection, and software security reviews
- Discovers hidden vulnerabilities and verifies if key security controls are implemented
- Automated tooling to enhance Google’s ability to detect incidents at the product level
- Employs machine learning systems to differentiate between safe and anomalous user activity across browsers, devices, apps, etc.
Coordination
When an incident occurs, triage will take place to assess the severity of the situation and engage the incident response team to evaluate the event. Assessment of severity is based on the following factors:- Potential for harm to customers
- Nature of the incident
- Type of data that might be affected
- Incident’s impact on customers’ use of the service
- Status of the incident
Resolution
The incident response team gathers facts about the security event, and the operations team will curb the damage, fix the underlying issue, and restore affected systems and services.











