A Security Operations Center (SOC) is a team of cybersecurity personnel dedicated to monitoring and analyzing an organization’s security while responding to potential or current breaches. The team is responsible for scanning all the security systems in real time. This first line of defense works around the clock to protect an organization’s security infrastructure from potential cyber threats.
The average total cost of a data breach in 2020 was $3.86 million.
– Source: IBM
In the first three quarters of 2020, there were 2,935 publicly reported breaches.
– Source: Security Magazine
The data clearly shows that the increase in the probability of a breach is directly proportional to the cost of a data breach. It indicates how desperately businesses need human involvement to constantly keep an eye on possible security threats and create strategies to eliminate them. Integrating a SOCs security team into the overall security strategy can help limit the risk of being targeted by malicious threats.
The World Needs SOC Security Staff
(Source: LinkedIn Jobs)

Industries That Must Have a (SOC)
Why Must Organizations Have Log
Management and a SOC Team?
Log management is an organized approach to deal with large volumes of computer-generated log data. It allows multiple operations on data like generation, collection, centralization, parsing, transmission, storage, archival, and disposal.
- Comply with applicable regulatory standards such as PCI-DSS, HIPAA, RMiT, ISO 27001, and others.
- Protect servers storing sensitive data from internal and external threats.
- Secure proprietary information and intellectual property.
Besides log management, Security Operations Center analysts can also integrate Security Information and Event Management (SIEM tools) in their process. These software tools aggregate security data from multiple sources, such as network devices, servers, and other locations. SIEM tools then connect the dots to discover the trends and detect cyber threats so that organizations can act on the alerts.
SIEM SOC for Threat Intelligence
Industry-Wise Analysis
- Healthcare industry: Deals with health data on consumers – enough said.
- Manufacturing industry: Owns a lot of intellectual properties and Technologies
- Financial services: Deals with data on monetary transactions, real-time monitoring of activities is vital.
- Government Agencies: They may store personal information along with criminal records, religious and political inclinations.
- Education Industries: Change in personal records in schools, universities, and training institutes can misrepresent individuals and their skills.
How Does a SOC Help?
According to the federal trade commission, credit card fraud jumped 104-percent from the first quarter to 2019 to the first quarter of 2020. Putting that into perspective, a recent study from Credit Card Insider showed the number of fraud reports during the same timeframe in 2017, 2018 and 2019 only grew by 27 percent
For the Payment Card Industry (PCI), it is mandatory to maintain a Security Operations Center. According to the PCI Compliance Security Standard Council, any merchant processing and storing credit card data should be PCI compliant. PCI compliance helps to ensure secure online transactions and protection against identity theft.
In such a scenario, a SOC security helps to:
- Monitor firewalls, their logs, and any configuration change to identify an irregularity.
- Increase the speed of incident remediation.
- Check firewall and router configuration standards by comparing them with documented services, ports, and protocols.
Cyberattacks against healthcare entities rose 45 percent since November, while the sector continues to be the most impacted overall and accounted for 79 percent of all reported data breaches during the first 10 months of 2020, according to reports from Check Point and Fortified Health Security.
As the healthcare industry contains crucial health data, such as holistic reports of patients including personalized diagnoses and treatments, it is an alluring target to cybercriminals. Threat actors monetize patient data by selling it to the highest bidder or blackmailing the victim.
For keeping protected health information (PHI) secure, healthcare organizations require a SOC 2 audit. SOC 2 compliance ensures:
- Customer trust
- Brand reputation
- Business continuity
- Competitive advantage
A recent report shows that ransomware attacks were up 25 percent across all industries in Q1 of this year. No industry was safe but the manufacturing industry was shown to be the most at risk, with an increase in ransomware attacks of 156 percent.
The manufacturing sector has always been a vulnerable industry as it possesses intellectual property and advanced technologies. Consider a Department of Defense (DoD) contractor for example: It is a must to meet the NIST cybersecurity standards to maintain DFARS (Defense Federal Acquisition Regulation Supplement) compliance. The NIST SP 800-171 outlines guidelines for Audit and Accountability, Configuration Management, Identification, and Authentication, with several other criteria.
SOC analysts are needed in the manufacturing industry to:
- Set up alerts to monitor potential threats.
- Promptly remediate ongoing and possible security threats.
According to the Official Cybercrime Report published by Cybersecurity Ventures, Cyber-crime damages will cost the world $6 trillion annually by 2021, up from $3 trillion just a year ago.
Do you know that financial services are the #1 target? This is because of the treasure trove of information that they require from customers, according to Verizon’s Data Breach Report.
Cybercriminals are eyeing financial services for their bulk transactions and real-time monitoring of activities. Apart from external attacks, institutions are also vulnerable to lost employee devices (like phones) and insider threats.
Banking and Financial services should perform SOC Type 1 and SOC Type 2 audits along with annual SOC 1 SSAE 18 reports. Being in clear nexus with the Internal Control Over Financial Reporting (ICFR) concept, these audits effectively report on internal controls. They reveal:
- Weaknesses in security controls like improperly provisioned information systems, weak authentication parameters, lack of multiple layers of security, and others.
- Shortcomings in operational controls.
- Flaws in documentation.
In 2020, a major cyberattack by a group backed by a foreign government penetrated thousands of organizations globally including multiple parts of the United States federal government, leading to a series of data breaches
As government agencies store personal information along with criminal records and religious and political inclinations, they are a prized target for cyber attackers.
Government institutions need SOC teams for:
- Network monitoring in real time.
- Analyzing activities on servers, endpoints, and databases.
- Looking for an incident or signs of a breach.
Verizon’s Mobile Security Index 2020 Report found that 44% of educational organizations suffered a security compromise involving a mobile device.
Education establishments are easy targets for cybercriminals. They not only carry personal data but also valuable research data and allow access to larger networks.
A Security Operations Center can help an educational institution’s IT staff respond to growing security threats by:
- Identifying and monitoring institutional assets and data.
- Neutralizing threats.
- Providing cybersecurity metrics to the IT staff.
How SOCs Work?
A SOC acts as the hub or central command post, taking telemetry from across the IT infrastructure of an organization, including its networks, equipment, appliances, and data stores, wherever those assets reside. Essentially, for every event logged within the organization that is being monitored, the SOC is the correlation point. The SOC must decide how they will be managed and acted upon for each of these events.
In addition to designing security plans and implementing defensive measures, the SOC team is responsible for identifying, evaluating, and responding to security incidents. Often, additional tasks, such as forensic analysis, cryptoanalysis, and reverse engineering, are addressed by the team.
What Are the Roles and Responsibilities of a Security Operations Center?
A Security Operations Center team uses strategic methodologies and processes for active surveillance and real-time analysis of an organization’s security infrastructure. The team carries out the following tasks:
| Task | Description |
| Identify assets | A SOC team’s operations start with gaining a holistic understanding of the tools and technologies at their disposal. The team learns about the hardware and software running on the systems. Their in-depth understanding helps in the early detection of potential cyber threats and existing vulnerabilities. |
| Proactive monitoring | A Security Operations Center primarily focuses on detecting malicious activities on the network before they can lead to substantial harm. |
| Manage logs, configuration change, and response | Thorough management of activity logs help a cyber forensic investigator trace back to the point where something may have gone wrong. |
| Rank alerts as per their severity | Whenever a SOCs security personnel detects a threat or irregularity, they are responsible for ranking the severity of the incident. This data helps in prioritizing the response to the event. |
| Adjust defenses | A SOC team adjusts its defenses by vulnerability management and increasing its awareness about threats. It helps the team stay vigilant for breaches. |
| Check compliance | SOC teams can check if the organization complies with applicable regulations and standards. |
| Notify on security breach | Organizations aim for minimal or no network downtime when hit by unexpected security incidents. A SOC team alerts the stakeholders as quickly as possible to ensure business continuity. |
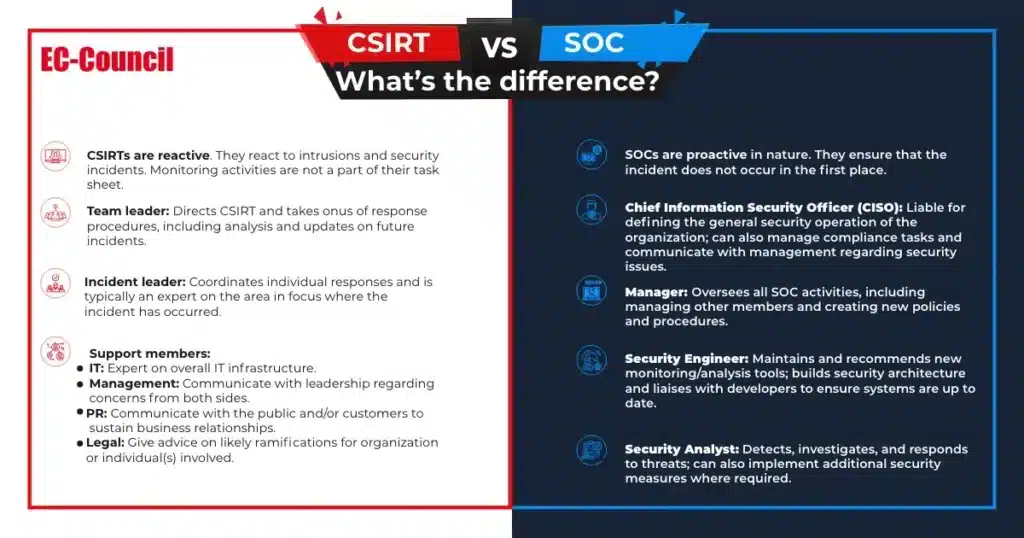
How Is a SOC Different from CSIRT?
The below infographic shows how the primary responsibilities of a SOC analyst or a SOC manager are different from that of an incident leader or any other CSIRT member.
For those who want to make a career in a Security Operations Center, EC-Council offers its Certified SOC Analyst (CSA) certification. Our course will help you get the industry-demanded CSA training required for the position and establish yourself as a certified Security Operations Center analyst.