Need for a Scalable Privacy Program
Many organizations raise awareness about cybersecurity, information security, and data privacy by emphasizing fear—fear of serious incidents, reputational damage, operational risks, regulatory penalties, and scrutiny from authorities. While these concerns are valid and organizations should remain vigilant, fear should not be the primary driver of action. Instead, the focus should be on the tangible benefits of compliance and good data practices. When fear is set as the foundation, and such incidents don’t occur, these topics may gradually lose importance within the organization. A more sustainable approach is to highlight how privacy and security initiatives support business goals, build trust, and fulfill legal, contractual, and industry-standard obligations. Given the complexity and diversity of legal, regulatory, contractual, and standard requirements, building a scalable privacy program requires thoughtful design and planning. It starts with identifying the relevant regulatory frameworks and extracting applicable requirements. This process must not happen in isolation—it should be integrated with the organization’s reality, involving people, processes, and technology to achieve balanced and effective outcomes. Ultimately, compliance should be driven by strategic value, not fear. It should reflect commitments to customers, partners, suppliers, and stakeholders, and align with recognized international standards, evolving gradually through continuous improvement.Privacy and Data Protection Landscape
The modern privacy and data protection landscape is shaped by several critical factors and evolving threats. Cyberattacks are becoming increasingly sophisticated, frequent, and targeted, with risks such as ransomware, phishing, malware, and insider threats posing serious challenges. At the same time, regulatory requirements are expanding, with frameworks like Europe’s GDPR, U.S. laws such as CCPA, HIPAA for healthcare, and other regional regulations becoming more stringent and geographically diverse. Compliance now demands a thorough understanding of these laws and their implications. Additionally, the volume of data being generated and stored is growing exponentially across on-premise servers, cloud environments, and mobile devices, while the sensitivity of that data—ranging from personal information and financial records to intellectual property—continues to increase. To address these, organizations must stay informed, adapt practices, and adopt scalable, agile security principles.Data Privacy Measures:
- Regulatory Compliance: Understanding and adhering to applicable laws and regulations, including data breach notification obligations, subject rights requests (access, rectification, erasure, etc.), and cross-border data transfer restrictions.
- Risk-Based Approach: Prioritizing efforts according to the risks associated with specific data assets and business processes, supported by regular risk assessments.
- Data Minimization: Collecting and processing only the data necessary for a specific purpose.
- Purpose Limitation: Using data solely for the purpose for which it was collected.
- Transparency and Consent: Being open about data practices and obtaining informed consent when required.
Data Protection Measures:
- Security: Establish technical and organizational measures to protect data against unauthorized access, use, or disclosure.
- In-Depth Defense: Apply multiple layers of preventive, detective, and corrective controls throughout the data lifecycle, including encryption for protection of data in transit and at rest.
- Automation and Orchestration: Streamline security tasks, reduce human error, and coordinate responses across systems.
- Continuous Monitoring: Ensure policies and controls adapt to evolving threats and regulatory changes.
- Vendor Risk Management: Ensure third parties meet security standards.
- Incident Response: Prepare organizations to effectively manage breaches, with regular testing to ensure readiness.
- Security Awareness: Equip staff to recognize and mitigate cyberthreats.
Privacy and Data Protection Strategies
Before organizations can build a formal privacy program, they must first establish clear strategies that set direction and priorities. Strategies define the guiding principles that ensure the program is designed with purpose and alignment to business goals. Without strategies in place, a program risks becoming reactive, fragmented, or driven solely by compliance checklists, rather than serving as a proactive, sustainable framework. The following key strategies provide a practical roadmap for building and sustaining strong privacy practices.Key Strategies for Implementation:
- Conduct privacy assessments to identify gaps.
- Develop clear, comprehensive privacy policies.
- Implement breach response plans with notification and remediation steps.
- Provide regular privacy training to employees.
- Monitor and audit practices for compliance.
- Automate repetitive privacy tasks where possible.
Fostering a Privacy-Conscious Culture
Fostering a privacy-focused culture starts with strong leadership commitment, as visible support from senior management demonstrates the organization’s dedication to protecting privacy. Regular employee training ensures that all staff understand privacy principles, while clear and effective communication of policies and procedures reinforces expectations. Incentives can encourage good privacy practices, and accountability measures ensure employees are held responsible for their actions, especially in cases of violations or incidents. Ultimately, a strong privacy program depends on building an organization-wide culture of awareness and accountability.Building a Robust Privacy Program
By refining their strategy, organizations can develop robust privacy programs that secure data, ensure regulatory compliance, and build trust with stakeholders.
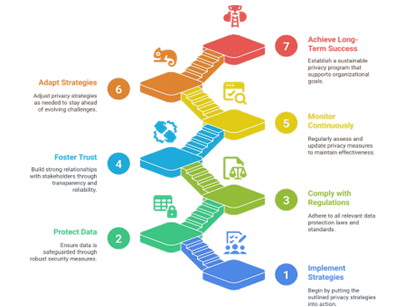
A seven-step approach to building an effective privacy program includes:
- Put the outlined privacy strategies into action.
- Ensure data is safeguarded through robust security measures.
- Adhere to all relevant data security laws and standards.
- Build strong relationships with stakeholders through transparency and reliability.
- Regularly assess and update privacy measures to maintain effectiveness.
- Adjust privacy strategies as needed to stay ahead of evolving challenges.
- Establish a sustainable privacy program that supports organizational goals.
Building a Scalable Privacy Program
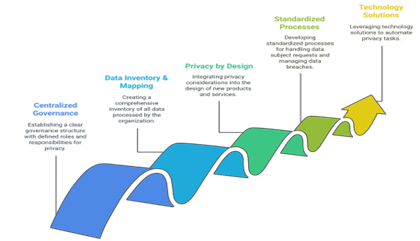
Scalability ensures privacy programs adapt as operations grow. Core elements include:
- Centralized governance with defined roles and a designated privacy officer.
- Data inventory and mapping to visualize flows and identify risks.
- Privacy by design in products, services, and systems.
- Standardized processes for impact assessments, requests, and breach handling.
- Technology solutions for automating privacy tasks like data discovery and consent management.
Implementing Scalable Strategies for Data Protection
Leveraging the right technologies can significantly strengthen data protection and enhance an organization’s overall security posture.
- Cloud-Native Security: Use cloud-native security services to protect data stored in the cloud, with features like encryption, access control, and threat detection.
- Identity and Access Management (IAM): Implement systems to control data access, including multi-factor authentication (MFA) to verify user identities.
- Data Loss Prevention (DLP): Deploy solutions to prevent sensitive data leaks.
- Security Information and Event Management (SIEM): Collect and analyze security logs from multiple systems to detect and respond to security incidents.
- Vulnerability Management: Scan systems regularly for vulnerabilities and apply patches promptly.
- Penetration Testing: Conduct regular tests to identify and address weaknesses in security controls.
Data Anonymization
Data anonymization is a valuable technique for protecting personal information while maintaining its usefulness for analysis and research. It can be applied to secure data in transit, in storage, or as part of privacy-by-design initiatives that integrate security throughout the data lifecycle. Methods range from simple suppression to advanced approaches, each with its own strengths and suitability for different data types and use cases.
When applied effectively, anonymization supports compliance with data security regulations while still allowing organizations to extract valuable insights—such as predicting customer trends and improving products or services.
Data Anonymization Techniques:
- Data Suppression: Suppression involves removing specific data elements that could identify an individual, such as names, addresses, or phone numbers. It is the simplest form of anonymization and is easy to implement. However, removing data can significantly reduce analytical value. Careful consideration is needed to avoid excessive data loss that may limit usefulness.
- Data Generalization: Generalization replaces precise values with broader categories or ranges—for example, converting exact ages into ranges (20–29, 30–39) or replacing specific locations with regions. This preserves some analytical value while reducing identifiability. The main risk is re-identification if applied carelessly, which can compromise privacy.
- Data Masking: Masking substitutes sensitive values with placeholders or artificial values, such as replacing a credit card number with masked digits. It protects original data but may limit analytical utility unless statistical properties are maintained. When masking numerical patterns, ensure that essential structures (e.g., bank identifiers) remain meaningful for permitted analysis.
- Data Pseudonymization: Pseudonymization replaces identifiers with codes or pseudonyms, with the mapping stored separately and securely. This allows re-identification when necessary (e.g., for research with consent). While it supports controlled linkage, it is not considered full anonymization under GDPR if the re-identification key exists, requiring strict security controls.
- Data Swapping: Data swapping randomly exchanges attribute values between different records, such as swapping salaries between employees. It preserves statistical distributions but can distort relationships between variables, which may affect certain types of analysis.
- Data Perturbation: Perturbation adds random noise or small modifications to data—such as altering numerical values slightly—to obscure individual records while retaining overall trends. It helps protect privacy but can reduce accuracy and reliability if excessive noise is introduced.
- Differential Privacy: Differential privacy adds mathematically calibrated noise to query results, limiting the information that can be inferred about individual records. It offers strong privacy guarantees but can be complex to implement and may reduce accuracy. Careful parameter selection is crucial to balance privacy and data utility.
Considerations for Choosing a Technique
Choosing the right anonymization technique depends on multiple factors, including the type of data (e.g., numerical, categorical, text), the goal of minimizing data loss while maximizing privacy, the risk of re-identification based on available data and external sources, applicable regulatory requirements such as GDPR or CCPA, and the computational cost of the method. In some cases, combining techniques may be necessary to achieve the optimal balance between privacy and utility. Ultimately, organizations should regularly review and update their strategies to address evolving privacy risks and regulatory requirements.
Tags
About the Author