Cyber Forensics for Modern Technologies: Tracking Cybercriminals Across Attack Vectors
EC-Council’s whitepaper on Cyber Forensics for Modern Technologies: Tracking Cybercriminals Across Attack Vectors, authored by Lucy Engel, CISO at BNP Paribas, is an insightful guide on how to investigate and mitigate cybercrime across various attack vectors.
The whitepaper begins with an overview of the evolution of cybercrime and the increasing sophistication of cybercriminals. It highlights how the proliferation of modern technologies such as the Internet of Things (IoT), cloud computing, and mobile devices have created new attack vectors that cybercriminals exploit. The whitepaper then delves into the need for cyber forensics, which involves investigating and analyzing digital evidence to identify the source of a cyber attack and track down the perpetrators. It emphasizes the importance of a robust cyber forensics strategy to prevent and mitigate cybercrime.
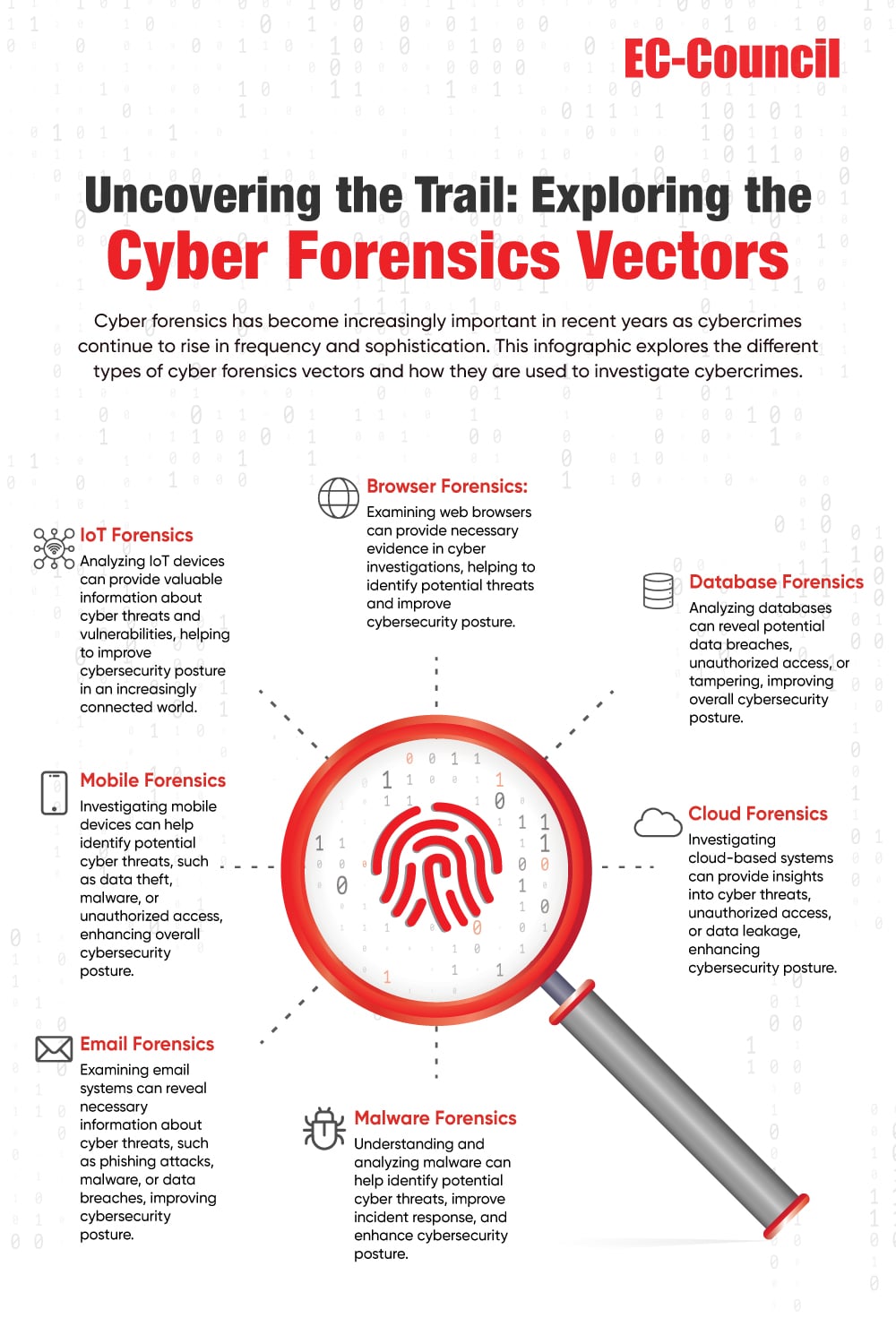
The whitepaper also highlights the challenges of investigating cybercrime, such as the volume and complexity of data, the lack of standardization in digital evidence collection, and the need for specialized skills and tools. It provides a comprehensive framework for conducting cyber forensics investigations, which involves a six-step process starting with incident response and ending with post-incident analysis.
One of the critical insights of the whitepaper is the importance of collaboration between different stakeholders in investigating cybercrime. This includes collaboration between law enforcement agencies, forensic experts, and organizations affected by cybercrime. The whitepaper also emphasizes the need for information sharing and mutual assistance in combating cybercrime.
The whitepaper also provides insights into the different types of cybercrime and attack vectors, including phishing, malware, ransomware, and social engineering. It highlights the importance of understanding the modus operandi of cybercriminals and staying up to date with the latest threats and vulnerabilities. Another key insight of the paper is the need for organizations to adopt a proactive approach to cybersecurity. This involves implementing security measures such as access controls, encryption, and multi-factor authentication and regularly monitoring and auditing their systems for potential vulnerabilities.
In conclusion, EC-Council’s whitepaper on Cyber Forensics for Modern Technologies: Tracking Cybercriminals Across Attack Vectors is an essential guide for organizations and individuals looking to enhance their cybersecurity posture. This whitepaper is a valuable resource for cybersecurity, digital forensics, and law enforcement professionals as it offers insights into the challenges of investigating cybercrime in today’s digital landscape and provides practical guidance for conducting effective cyber forensic investigations. To download the whitepaper, submit the details in the form below.







