In the current threat landscape, where cyberthreats are evolving rapidly, proactive network security is desperately needed to prevent and reduce the impact of cyber incidents. The article will shed light on the fundamentals of security architecture and its evolving role in modern cybersecurity. It will focus on the key concepts of security architecture, such as defense in depth, a foundational strategy that layers security controls, and also the principles of Zero Trust. The article will also take you through validating security controls once the architecture is in place and touch upon emerging technologies, such as generative AI and agentic AI, and how they’re reshaping security strategies and helping to defend against increasingly sophisticated threats.
Understanding Defense in Depth
Defense in depth is a network security architectural strategy that ensures multiple layers (technical, procedural, and human) of security controls, instead of relying on a single safeguard to protect systems and data. It uses overlapping defenses to reduce the risk of failure. While technology such as firewalls, endpoint detection and response (EDR), and intrusion detection systems (IDS) are essential, combining these with trained users and strong processes, including access management and incident response, will provide better resilience. Attackers always go for the weakest link, which could be a person or a flawed process, not just the system. So a holistic approach that integrates people, processes, and technology ensures a more robust and adaptive network security posture.
What Are Security Controls?
Security controls are technical or policy-driven safeguards that protect systems and data for alignment with information security compliance. These controls are among the building blocks of any network security strategy, and they are the most effective when layered together in a defense-in-depth strategy.
- Human-Based Controls: These types of controls involve mitigating risk using human intervention and expertise, such as SOC, monitoring, threat analysis, security awareness, managerial security roles, holistic security, and policies.
- Process-Based Controls: These involve established policies and procedures that guide secure operations and ensure the security mindset is embedded in daily operations. Examples include access management policies, device policies, vendor policies, incident response controls, etc.
- Technology-Based Controls: These controls include the most common and important network security technologies such as firewalls, antivirus, EDR, IDS, intrusion prevention system (IPS), etc.
One of the most relevant examples to demonstrate a defense-in-depth strategy is the defense against phishing attacks. This strategy involves the use of all the types of security controls mentioned above.
- Technology controls such as email filtering and outbound proxy block insecure incoming email and outbound redirection from suspicious links.
- Multi-Factor Authentication (MFA), endpoint security, and SIEM as part of process-based controls protect against suspicious activity and unauthorized access, combining technology and human oversight.
- User awareness training, as part of human-based controls, helps educate users in secure digital use and phishing mitigation, demonstrating proactive defense.
How to Build a Defense-in-Depth Architecture
Building a robust defense-in-depth strategy in a large organization involves a structured, continuous process:
Inventory the environment
Start by identifying what needs protection: critical assets, systems, and business processes. Understand what’s important and what should always remain operational.
Identify top cyber risks
Look beyond your organization to understand the broader threat landscape. Use threat intelligence reports from sources like Verizon DBIR, IBM, and Mandiant to pinpoint the industry’s most relevant attack vectors.
Plan and implement controls
For each risk scenario, design layered controls that address multiple threats. Prioritize versatile controls like:
- MFA: Blocks unauthorized access and persistence
- SIEM: Provides visibility and alerting across the network
- EDR: Detects and mitigates threats on devices
- Avoid relying on single-purpose controls; choose those offering broad coverage.
Validate controls
Test controls to ensure they work as intended. For example, deploying EDR is not enough; verify that it actively blocks threats. Validation helps uncover misconfigurations or gaps.
Repeat and improve
Defense in depth is not a one-time setup. Continuously reassess your environment, update your risk profile, and revalidate controls to stay ahead of evolving threats.
What Is Zero Trust?
Zero Trust Network Access (ZTNA) is a modern network security policy applicable to the entire architecture, changing the entire approach to holistic security and enabling defense in depth. It assumes that no user, device, or system, both internal or external, is safe and validates access controls for each of them every time. It does not rely on perimeter-based defenses but enforces strict access controls and continuous verification.
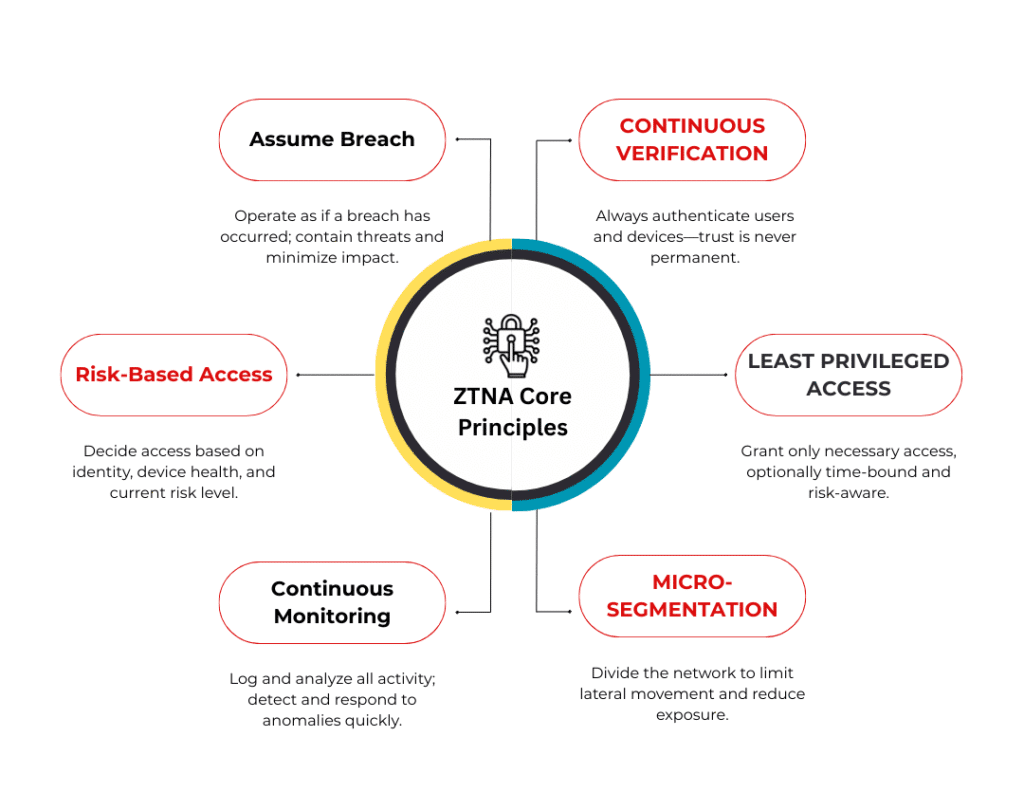
This security measure is predicated on the fact that attackers often gain initial access through compromised credentials or vulnerable devices. ZTNA ensures that every device, user, and their access permissions are continuously validated, preventing lateral movement by adversaries. Although implementing ZTNA can be complex, it has proven vital for organizations seeking to achieve cyber resilience.
Developing a Zero Trust Strategy
Zero Trust is a strategic approach that requires planning and cross-functional collaboration. It involves assessing the digital environment, identifying operational and security stakeholders, mapping critical processes and data, understanding risks and goals, etc. Implementing it requires important telemetries from users, devices, networks, applications, etc., so alignment across various business verticals is essential. You can’t build actionable ZTNA without understanding your infrastructure, risks, and business processes, as Zero Trust dictates a delicate balance between security and unhindered business operations.
Only once these processes have been completed can a tailored roadmap specific to the organization’s needs be developed. This sets the foundation for a scalable, effective ZTNA implementation. Some of the common best practices and pitfalls for Zero Trust applications include:
| Dos | Don’ts |
|---|---|
|
|
Validating Security Controls
To achieve an agile Zero Trust posture, continuous testing and security validation of the implemented ZTNA policies are necessary. As threats evolve, constant assessment is essential to stay relevant. Thus, the use of varied testing methods, such as adversarial simulations, is needed to challenge your defenses and avoid complacency. Testing should not just be about triggering alerts, but also about ensuring timely and actionable defense in real-world scenarios.
Methods for Control Validation
Some of the primary methods for security validation of the controls overlap with the approach of a proactive security, i.e., simulation-based testing of the security controls under a permissible environment.
- Penetration Testing: Hands-on testing that simulates real-world attacks to uncover vulnerabilities in applications or networks.
- Control Validation Testing: Testing specific security controls to ensure they function as intended, which is more targeted than general pen testing.
- Threat Modeling: A strategic, hands-off approach that analyzes your control environment against known threat behaviors (e.g., ransomware tactics) to identify gaps.
- Practical Exercises: Tabletop and functional exercises that evaluate the team’s response plan and approach in scenario and simulation environments.
- Incident Lessons Learned: Post-incident reviews to assess how controls performed during actual events and identify areas for improvement.
Types of Penetration Testing
Different forms of penetration testing (pen testing) exist; each targeting different aspects of an organization’s security posture- Application Pen Testing: Identifies vulnerabilities in web, mobile, or desktop applications, such as insecure APIs, authentication flaws, or input validation issues.
- Network Pen Testing: Assesses the security of internal and external networks, identifying misconfigurations, exposed services, and potential entry points.
- Physical Testing: Tests physical security controls by attempting unauthorized access to facilities, e.g., bypassing badge systems, exploiting camera blind spots, or tailgating.
- Social Engineering: Assesses human vulnerabilities through tactics like phishing, impersonation, or manipulating staff to reveal sensitive information or grant access.
- Adversary Simulation: Emulates real-world attacker tactics across multiple vectors to test defenses holistically. Unlike targeted pen tests, this approach mimics how attackers chain techniques to achieve objectives.
Each type of pen test requires different resources and expertise. For maintaining an agile security posture, it is necessary to combine multiple proactive security approaches. Some of the considerations and pitfalls of control validation testing are:
| Dos | Don’ts |
|---|---|
|
|
Emerging Technologies in Cybersecurity
As technology evolves, several emerging innovations are reshaping the digital and cybersecurity landscape. Organizations are rushing to incorporate novel technologies, such as generative AI and machine learning (ML), to boost their business operations. However, specific security challenges often accompany these innovations. Both generative AI and ML enhance the automation of processes and synthetic data generation, making work faster and more efficient. Quantum computing, another emerging technology, shows the potential to quickly solve complex problems, such as those involving cryptographic and data security operations. Similarly, the incorporation of agentic AI allows for the automation of machine intelligence, enabling the capable execution of complex workflows without human intervention. However, these also increase the number of unknown variables that fall outside the scope of security considerations.Securing Against Emerging Threats
New technologies bring new risks. Here’s how organizations are responding.
- Post-Quantum Cryptography: Traditional encryption may be undone by quantum computing in the future. To counter this, cryptographic systems are being redesigned to withstand quantum attacks. This is essential even today as attackers may still harvest encrypted data and decrypt it later once quantum capabilities become accessible.
- AI Model Firewalls: These protect AI systems from abuse, such as prompt injection or training data poisoning. Attackers may manipulate models to deliver harmful outputs or redirect users to malicious sites.
- AI Detection Tools: As AI-generated content becomes more prevalent (e.g., deepfakes, synthetic code), tools are being developed to distinguish between human-created and AI-generated outputs, critical for maintaining trust and authenticity.
Integrating Emerging Technology into Security Architecture
Emerging technologies such as AI can be utilized by both threat actors and security professionals for their respective goals. However, the focus should still remain on solving current problems, rather than chasing trends. It is essential for security teams to conduct continuous testing and reimagining objectives, while ensuring that adopted tools align with the organization’s needs.
AI is well-suited for repetitive, low-value tasks but may present uncalculated risks when dealing with complex and high-risk factors. However, AI may also misclassify threats, resulting in false positives or negatives. Hence, a critical process should always have a combination of technical, procedural, and human controls. To integrate AI safely, it is necessary to define its scope, restrict access, maintain human oversight for high-impact decisions, and align its use with your organization’s risk tolerance.
Tags
About the Author

Andrew Jarrett
Director, DTCC
Andrew Jarrett has over fifteen years of experience in technology, cybersecurity, and incident response in both the public and private sectors. Prior to joining DTCC, Andrew Jarrett launched and led multiple cybersecurity programs in highly regulated environments, including defense and finance. In addition to his work at DTCC, Andrew Jarrett is also an adjunct instructor with the Applied Cybersecurity Program at Texas A&M Engineering Extension Service and a volunteer advisor for multiple high school and college career technology education programs.