Who is a Certified Ethical Hacker?
Ethical hackers are information security professionals who are trained to identify and mitigate vulnerabilities in networks and perform security assessments to prevent data breaches. Ethical hacking is a promising career path with extensive growth opportunities. Certified Ethical Hackers (CEH’s) hold various job titles in cybersecurity; their core work is critical to testing and securing an organization’s assets. Ethical hackers are trained and skilled in the same Tactics, Techniques, and Procedures (TTP) used by malicious/black-hat hackers to break into organizations’ systems through a repeatable, methodical process that uncovers and exploits weaknesses. In CEHv13, CEH’s are not just becoming a certified ethical hacker, you will become an AI powered Certified ethical hacker. CEH’s will learn not just to automated most of the ethical hacking skills but also learn Ai driven cybersecurity skill and hacking AI attack systems to bring more efficiency in your cyber defense skills and gain double productivity.
C|EH Program Information
C|EH is divided into 20 modules and delivered through a carefully curated training plan that typically spans across 5 days. As you progress through your training, each module has extensive hands-on lab components that allow you to practice the techniques, and procedures taught in the program in real-time, and on live machines.
The 20 modules are designed to help you master the foundations of ethical hacking and prepare you to challenge for the C|EH certification exam.
5 Phases of Ethical Hacking
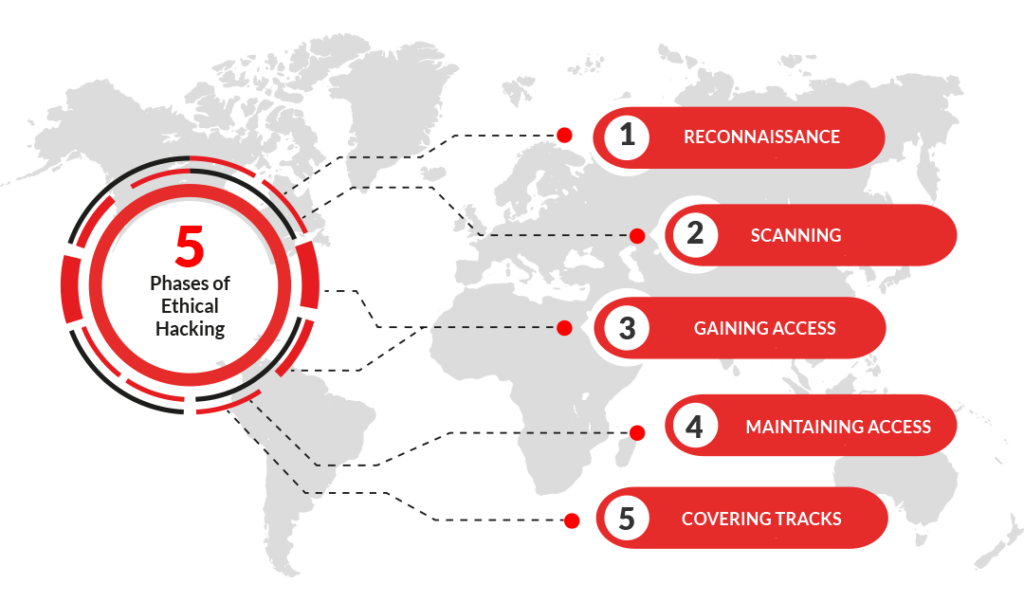
- Reconnaissance refers to the preparatory phase where an attacker seeks to gather information about a target prior to launching an attack.
- Scanning utilizes different tools to collect information on websites, networks, or file systems to detect vulnerabilities.
- Gaining Access is where an attacker gets access to a system or application that is on a network or computer.
- Maintaining Access also referred to as persistence. This allows an attacker continued access on a target whether the machine is rebooted, or the user is logged off.
- Covering Tracks After gaining access to a target, removing any artifacts is critical to ensure you as an attacker does not leave a trace. This may include deleting logs, removing any tools, scripts, or applications that were installed on the target.
What is new in C|EH v13
C|EH v13 is a renewed program that teaches you everything you need to know about ethical hacking with training, labs, assessment, a mock engagement(practice) and even a series of global hacking competitions – all part of the C|EHV13!
C|EHv13 New Learning Framework
C|EH v13 has designed a new learning framework that uses a 4-phase methodology that includes: Learn, Certify, Engage and Compete.
This approach to learning ensures that students who go through the C|EH v13 program receive an in-depth learning experience that provides comprehensive training, prepares learners for the certification exam, all while providing the hands-on labs, and practice range experiences to step into the workforce. This is a unique learning framework that only C|EHv13 offers to cybersecurity professionals.
C|EHv13 New Learning Framework
C|EH v13 has designed a new learning framework that uses a 4-phase methodology that includes: Learn, Certify, Engage and Compete.
This approach to learning ensures that students who go through the C|EH v13 program receive an in-depth learning experience that provides comprehensive training, prepares learners for the certification exam, all while providing the hands-on labs, and practice range experiences to step into the workforce. This is a unique learning framework that only C|EHv13 offers to cybersecurity professionals.
4-Phase Learning Framework for C|EH v13
C|EH v13 incorporates Training, Hands-on Learning Labs, Certification Assessments, Practice Cyber Ranges, Cyber Competitions, and opportunities for continuous learning all into one comprehensive program curated through our new Learning Framework: Learn, Certify, Engage, and Compete. Now let us go into detail about the 4-Phase Learning Framework for C|EH v13.

1. C|EHv13 Learn
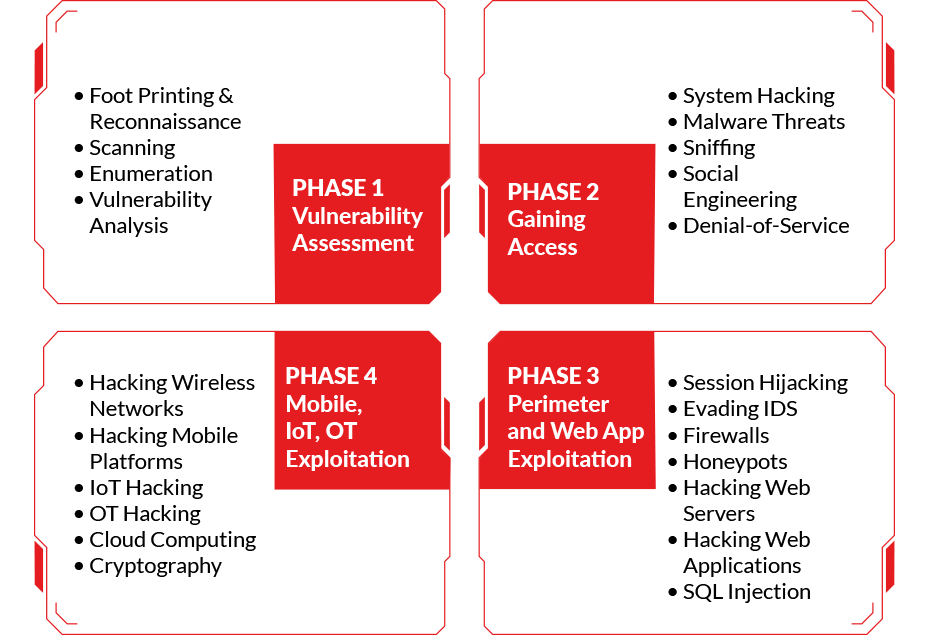
The C|EH v13 training program curates 20 modules covering a wide variety of technologies, tactics, and procedures providing prospective Ethical Hackers with the core knowledge needed to thrive in the cyber profession. Concepts covered in the training program are balanced 50/50 with knowledge and hands-on application through our Cyber range.
Every tactic discussed in training is backed by step-by-step labs conducting in a live virtualized environment with live targets, live tools, and vulnerable systems. With over 221 LABS, and our Lab technology, you will have comprehensive hands-on practice to learn and apply the knowledge you attain.And access to specially designed unique labs to practice your AI driven cybersecurity skills.
20 Modules that Help You Master the Foundations of Ethical Hacking and Prepare You to Challenge
the C|EH Certification Exam
Learn how to use the latest techniques and tools to perform footprinting and reconnaissance, a critical pre-attack phase of the ethical hacking process.
Learn about the various system hacking methodologies used to discover system and network vulnerabilities, including steganography, steganalysis attacks, and how to cover tracks.
Learn about different types of malware (Trojan, viruses, worms, etc.), APT and fileless malware, malware analysis procedures, and malware countermeasures.
Learn about packet-sniffing techniques and their uses for discovering network vulnerabilities, plus countermeasures to defend against sniffing attacks.
Learn social engineering concepts and techniques, including how to identify theft attempts, audit human-level vulnerabilities, and suggest social engineering countermeasures.
Learn about different Denial of Service (DoS) and Distributed DoS (DDoS) attack techniques, plus the tools used to audit a target and devise DoS and DDoS countermeasures and protections.
Learn the various session hijacking techniques used to discover network-level session management, authentication, authorization, and cryptographic weaknesses and associated countermeasures.
Learn about firewall, intrusion detection system (IDS), and honeypot evasion techniques; the tools used to audit a network perimeter for weaknesses; and countermeasures.
Learn about web server attacks, including a comprehensive attack methodology used to audit vulnerabilities in web server infrastructures and countermeasures.
Learn about web application attacks, including a comprehensive web application hacking methodology used to audit vulnerabilities in web applications and countermeasures.
Learn about SQL injection attack techniques, evasion techniques, and SQL injection countermeasures.
Learn about different types of encryption, threats, hacking methodologies, hacking tools, security tools, and countermeasures for wireless networks.
Learn mobile platform attack vectors, Android and iOS hacking, mobile device management, mobile security guidelines, and security tools.
Learn different types of Internet of Things (IoT) and operational technology (OT) attacks, hacking methodologies, hacking tools, and countermeasures.
Learn different cloud computing concepts, such as container technologies and serverless computing, various cloud computing threats, attacks, hacking methodologies, and cloud security techniques and tools.
Learn about encryption algorithms, cryptography tools, Public Key Infrastructure (PKI), email encryption, disk encryption, cryptography attacks, and cryptanalysis tools.
Hands-On Learning labs
- 100% virtualization for a complete learning experience
- After login, you will have full access to pre-configured targets, networks, and the attack tools necessary to exploit them:
- Pre-configured vulnerable websites
- Vulnerable, unpatched operating systems
- Fully networked environments
- 4,000 hacking tools
- And much more!
- Wide range of target platforms to hone your skills
- 550 attack techniques covered
- Objective-oriented flags for critical thinking and applied knowledge assessment
- Cloud based cyber range
- Unique labs to
2. C|EHv13 Certify
Each of the Certification Domains are carefully vetted through industry practitioners ensuring the certification maps to current industry requirements. This exam undergoes regular psychometric evaluation and tuning to ensure a fair and accurate measure of the candidate’s knowledge in the Ethical Hacking domains.
Both the below exams are ANAB 17024 Accredited and approved under US DoD 8140 directive.
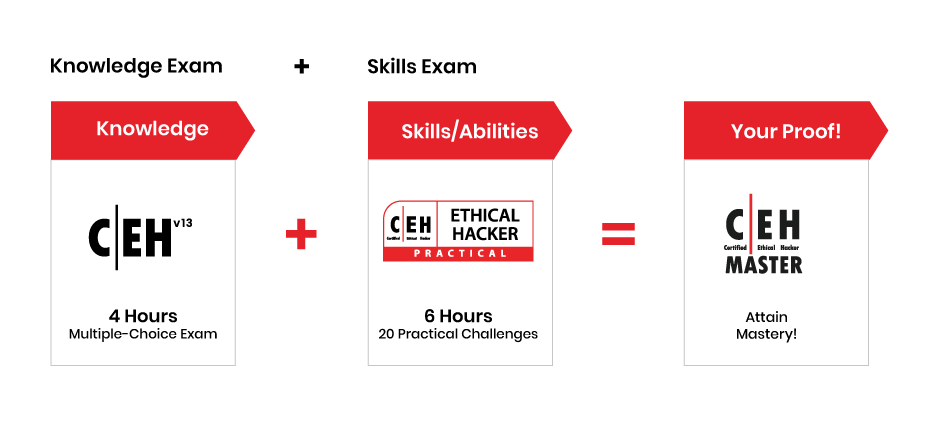
CEH Knowledge Based Exam:
The Certified Ethical Hacker Credential is the most trusted certification across the globe, and is the baseline measurement of ones grasp on the concepts in ethical hacking and security testing. The 125 question, 4-hour proctored exam is recognized across the globe as the original, and most trusted tactical cyber security certification for ethical hackers.
CEH Practical Exam:
CEH Practical exam that consists of 20 practical challenges in a 6-hour period. Clearing CEH Practical exam and knowledge exam, will entitle you with CEH Master Certification.
Just envision your title as a C|EH Master, this credential will set you apart from you fellow peers.
3. C|EHv13 Engage
In the engage phase of learning: you will apply the 5 phases to ethical hacking while conducting real-world ethical hacking assignments. They include:
- Reconnaissance
- Scanning
- Gaining access
- Maintaining access
- Covering your tracks
4. C|EHv13 Compete
The compete phase, new to C|EH v13, the C|EH Global Challenges run every month providing Capture-The-Flag style competitions exposing Certified Ethical Hackers to a variety of modern technologies and platforms from Web Applications, OT, IoT, SCADA and ICS systems, to Cloud and Hybrid environments. Our Compete structure allows C|EH’s to fight their way to the top of the leader board each month in these 4-hour curated CTF’s.
Objective based flags are designed around the Ethical Hacking process keeping the C|EH’s skills current, assessing their critical thinking abilities and covering the latest vulnerabilities and exploits as they are discovered. The capture-the-flag competitions are hosted 100% online in EC-Council’s Cyber Range.
Candidates race the clock in scenario-based engagements against fully developed Network and application environments with operating systems, real networks, real tools, and real vulnerabilities.
| Month | Skill Challenge |
|---|---|
| October 2024 | Windows Wreckage: Unravelling Code & Hunting Threats |
| November 2024 | Web Warriors: Defend Against the OWASP Menace |
| December 2024 | Operation ATT&CK Unveil: Decoding Cyber Tactics |
| January 2025 | RansomWar: Battle for Decryption |
| February 2025 | Supply Chain Siege: Unravel the Hidden Links |
| March 2025 | Operation Nexus: Breach the Grid |
| April 2025 | Identity Infiltration: Breach the Directory |
| May 2025 | API Apocalypse: Breach the Gateways |
| June 2025 | Data Fortress Breach: Cracking the Core |
| July 2025 | Operation Deep Breach: Hack, Escalate, Pivot |
| August 2025 | eCommerce Rampage: Defend the Digital Marketplace |
| September 2025 | Cloud Clash: Battle for Infrastructure Security |
Key Updates to the C|EH v13
- New Learning Framework: 1. Learn 2. Certify 3. Engage 4. Compete
- AI-driven cybersecurity skills
- AI integrated in 5 phases of ethical hacking
- Learn Hacking AI attacks systems based on OWASP Top 10 Attacks and Vulnerabilities
- Compete: New challenges every month!
- 100% compliance with the NICE 2.0 Framework
- Based on comprehensive industry-wide job task analysis
- Hands-on Learning Labs
- Designed Labs to Practice AI driven skills
- Practice Range to engage in real ethical hacking assignments
- Global C|EH community competitions
- Cheat sheet
- Coverage of the latest malware
- Lab-intensive program (every learning objective is demonstrated using labs)
- Hands-on program (50% of training time is dedicated to labs)
- Lab environments that simulate real-time environments
- Covers the latest hacking tools (based on Windows, macOS, and Linux)
- Latest OS covered and a patched testing environment
- Updated versions of tool screenshots, tool listing slides, and countermeasure slides
- Active Directory Attacks
- Ransomware Attacks and Mitigation
- AI and Machine Learning in Cybersecurity
- Critical Infrastructure Vulnerabilities
- Extended Detection and Response (XDR)
- Quantum Computing Risks and Attacks
- Post-Quantum Cryptography
- Deepfake Threats
- Zero Trust Architecture
- Cloud Security
- IoT Security Challenges
- Critical Infrastructure Vulnerabilities
| 4600+ Pages of Student Manual Pages | 2000+ Pages of Lab Manual |
| 4000+ Hacking & Security Tools | 221 Hands-On Lab (Practical) |
| 550 Attack Techniques | 20 Refreshed Modules |
Are You Ready to Become a Certified Ethical Hacker?
What type of job roles are available if I get my C|EH certification?
Having your C|EH certification will open doors to over 20+ different career roles. They include:
- Mid-Level Information Security Auditor
- Cybersecurity Auditor
- Security Administrator
- IT Security Administrator
- Information Security Analyst 1
- Infosec Security Administrator
- Cybersecurity Analyst (Level 1, Level 2, & Level 3)
- Network Security Engineer
- SOC Security Analyst
- Network Engineer
- Senior Security Consultant
- Information Security Manager
- Senior SOC Analyst
- Solution Architect
- Cybersecurity Consultant
- Cyber Defense Analyst
- Vulnerability Assessment Analyst
- Warning Analyst
- All-Source Analyst
- Cyber Defense Incident Responder
- Research & Development Specialist
- Senior Cloud Security Analyst
- Third-Party Risk Management
- Threat Hunting Analyst
- Penetration Tester
- Cyber Delivery Manager
- Application Security Risk
- Threat Modelling Specialist
- Web Application Penetration Tester
- SAP Vulnerability Management- Solution Delivery Advisor
- Ethical Hacker
- SIEM Threat Responder
- Product Security Engineer / Manager
- Endpoint Security Engineer
- Cybersecurity Instructor
- Red Team Specialist
- Data Protection & Privacy Officer
- SOAR Engineer
- AI Security Engineer
- Sr. IAM Engineer
- PCI Security Advisor
- Exploitation Analyst (EA)
- Zero Trust Solutions Engineer / Analyst
- Cryptographic Engineer
- AI/ML Security Engineer
- Machine Learning Security Specialist
- AI Penetration Tester
- AI/ ML Security Consultant
- Crypto Security Consultant
As you can see, the job opportunities are endless when you get your C|EH. When recruiters and potential employers see you have the C|EH certification, they know you are equipped to fill any of these roles, the C|EH certification makes you more marketable.
As you can see, the job opportunities are endless when you get your C|EH. When recruiters and potential employers see you have the C|EH certification, they know you are equipped to fill any of these roles, the C|EH certification makes you more marketable.
C|EH Jobs Are in Demand!
C|EH is the most in demand certification and the current supply is not sufficient? This is not only a US shortage, but across the globe. There are more jobs that advertise C|EH than any other certification in the world for ethical hacking. The threats in the cyber world is going to continue to grow and the industry needs professionals like you to take on the threats and attacks that occur in organizations across the globe.
So what does this mean for you?
This means opportunity awaits!
Analyzing this pay chart, according to Salary.com, the average Ethical Hacker salary in the United States is $110,757 as of 8th September, 2024, but the salary range typically falls between $88,381 and $137,958
This average salary increased by approximately $6,800 compared to 2022.
While certification provides a great measure of knowledge and serves as an excellent baseline, we built C|EH v13 with critical job skills in mind and an all-new Learning process that takes our students through the complete Learn, engage, Certify, and Compete process. This ensures we not only transfer knowledge, but we build capable, skilled, and Job Ready certified members.
This certification is probably one of the most valuable certifications you can get to invest in your future!
Department of Defense utilizes Certified Ethical Hackers to defend their networks!
The C|EH training and certification is one of the best ethical hacking courses that the Pentagon utilizes from EC-Council, to train their network defenders against hackers.
https://edition.cnn.com/2010/TECH/03/10/pentagon.hacking/index.html
C|EH v13 immerses current and future cyber security professionals in the Tactics, Techniques, and Procedures also referred to as (TTP’s) to build technologists, who can uncover weaknesses on a target system before the criminals. Having a thorough knowledge of what C|EH v13 provides, gives you the knowledge on how to apply those TTPs in the field!! And with version 13, youll understand the methods.
The Certified Ethical Hacker has been battled hardened over the last 20 years creating hundreds of thousands of Certified Ethical Hackers employed by top companies, the military, and governments all over the world. While the process is consistent, the technology is constantly changing. Staying on top of the changing technologies and threats is critical to ensuring your organization is secure, and ready to respond with minimal impact in the event of a breach or incident.
Getting your C|EH v13 allows you to invest for your future to help you land into one of 20+ Cybersecurity job roles. During this presentation you gained some insightful information on the overall process of EC-Council’s 4-phase learning framework and how it can prepare you for the next step in your career. Whether you are new or experienced in the cyber field, this certification will prepare you for an exciting career as an ethical hacker or cyber professional. You choose your path to help fill those critical roles that are in demand. The challenge is rewarding and you will never fall short of your skills with our life-long learning opportunities through our CyberQ challenges. Now ask yourself are you ready?
Become a Certified Ethical Hacker!
At EC-Council













