Web Application Security Strategy
Web applications are central to business operations and user experience development across many industries today. As web-based applications become more popular, so too do vulnerabilities that can compromise these systems.
Websites and web applications have become a growing resource for businesses to share their activities across platforms, improving the user experience. But these applications can also be an entry point for malicious attackers, increasing security risk significantly.
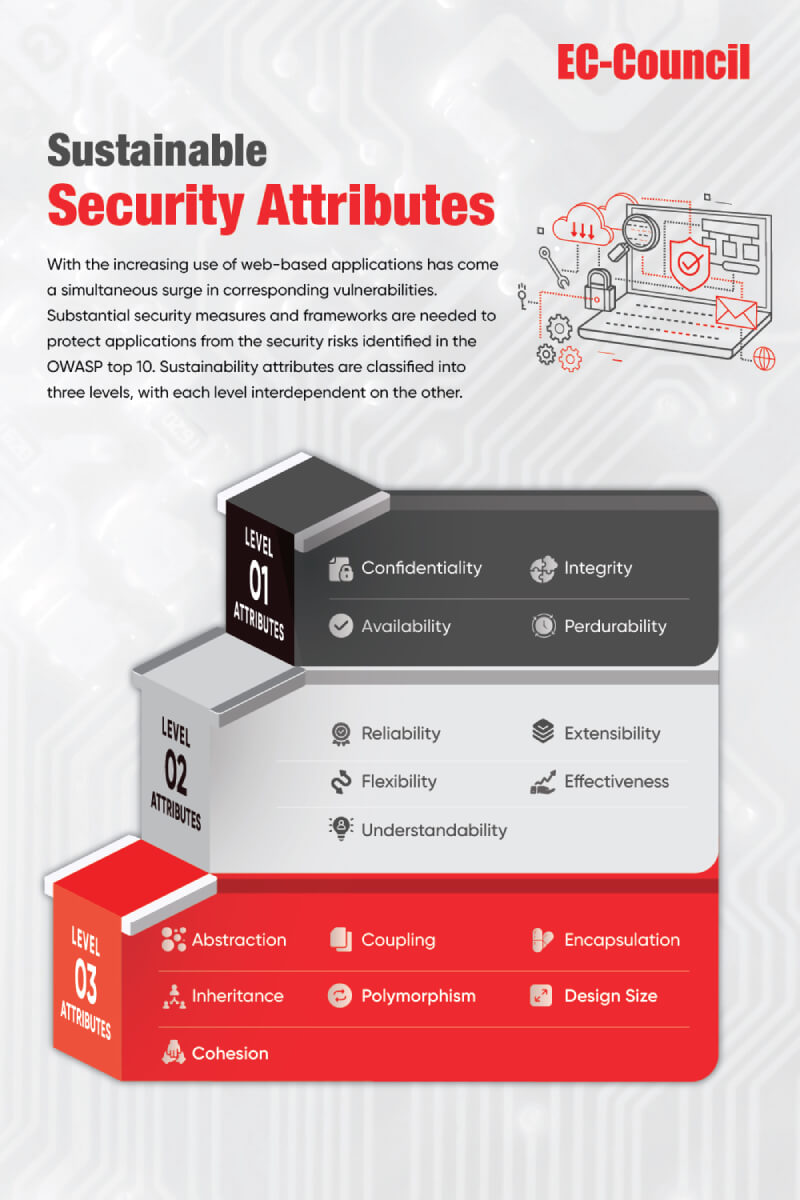
Hackers exploit vulnerabilities in code and design architectures to access sensitive information. We must implement substantial security measures and frameworks to protect applications from the security risks identified in the OWASP top 10.
Application security is constantly evolving to keep up with technological trends, which poses challenges for organizations that develop custom software for risk management. Many have responded to these issues by implementing primarily reactive measures.
Researchers have been motivated to develop new frameworks and strategies for implementation that would take place earlier in the software development lifecycle (SDLC), to enhance security and reduce time consumption. Some researchers point to a developer companion framework as a practical approach. In contrast, others recommend building increased collaboration into the implementation framework, using the obfuscation method during code construction, and using a comprehensive security model.
Traditional web application development has a weakness: achieving sustainable software security is challenging. But novel frameworks incorporating security tactics in the design phase early in the software development lifecycle can save time and other resources, reduce risk and improve application performance.
This whitepaper discusses the threat landscape described by OWASP in the context of relevant application security principles, the need for security during the SDLC lifecycle, and novel methods for achieving it. Read the complete whitepaper here upon submitting your details in the form below.









