What CISOs Need to Know About API Vulnerability Testing and Security
Application programming interfaces (APIs) are critical to business processes; however, data privacy, integrity, and trust can be jeopardized when businesses use APIs. In addition to violating the General Data Protection Regulation, security breaches can harm companies and their customers. Businesses undergoing digital transformations, in particular, tend to use more APIs, which, if not tested and secured, may create new vulnerabilities that attackers can exploit.
Chief information security officers (CISOs) must prioritize API security to prevent damage. The current whitepaper addresses what CISOs need to know about API security and the tools, techniques, challenges, and methodologies available to resolve API bugs, exploits, and other security-related issues.
Testing API Security
- Parameter tampering: By changing the values in API requests, it modifies their importance and induces the API to accept requests.
- Input fuzzing: A practice used by developers and security professionals to find vulnerabilities in software applications. It involves sending random data to an application via its API console, using automated or semi-automated techniques, and analyzing how it responds.
- Unhandled HTTP methods: When an application sends a request using an HTTP method, not on the list of permitted methods, the API infrastructure should reject it and send back a defined error message. If the API does not do this, it implies that it has security vulnerabilities.
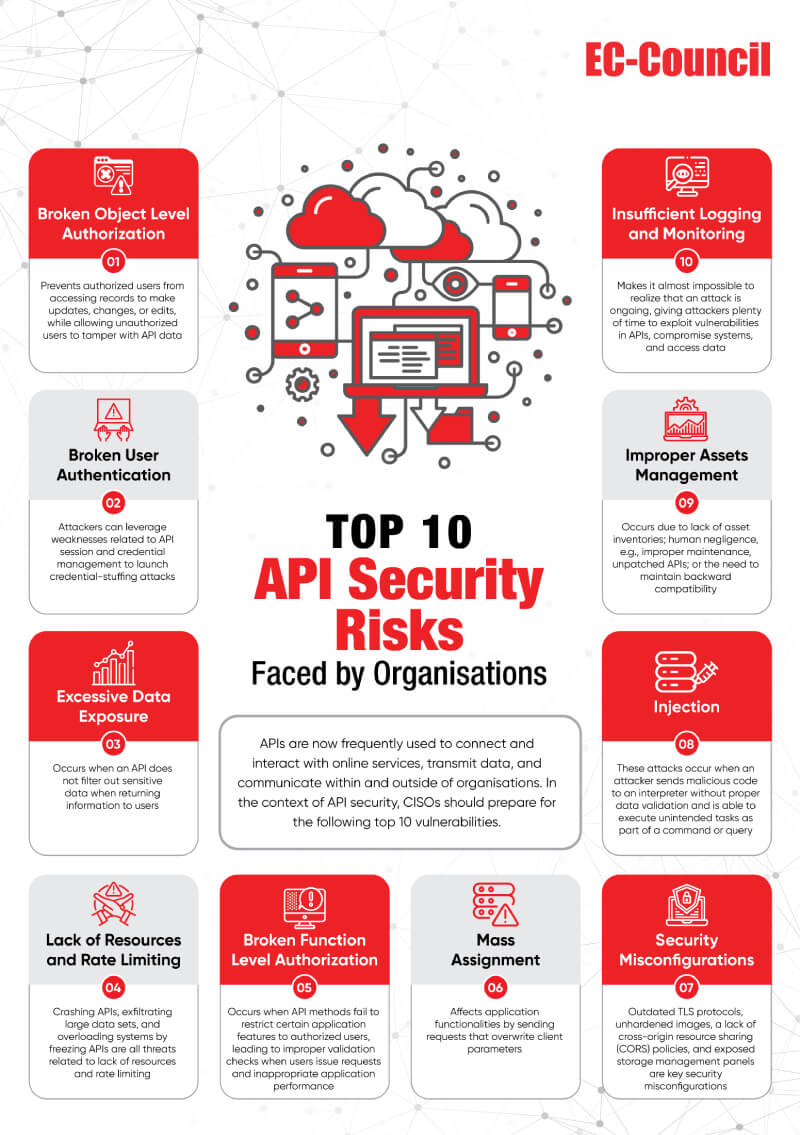
Despite an organisationʼs best efforts, some security risks are likely to remain, and their magnitude can be overwhelming due to skillset limitations or a lack of API security awareness among security professionals. Malicious hackers are aware of this fact and are often more alert than security professionals. Therefore, CISOs need to consider security risks and the implications of failing to address them. In this regard, this whitepaper describes the top API security risks organizations face today and outlines benchmarks for optimizing and maintaining API security. To help CISOs stay ahead of the curve, this whitepaper focuses on how to implement API services without introducing security vulnerabilities in the process of embedding these innovative technologies into business operations.









