Guide to Current Web Application Penetration Testing Practices
Web application penetration testing is one of the most popular strategies deployed by organizations to conduct a thorough evaluation of a company’s security posture. It is done by performing real-time simulations of how attacks are carried out, giving end-users a perspective on how to gain unauthorized access to their sensitive information. Penetration testing can help pinpoint the origin sources of both internal and external threats, discover hidden security threats, and uncover target machines that are most likely to be susceptible to these attacks.
Good web app pen testing practices help organizations identify security vulnerabilities and prevent security breaches. It fortifies defenses, secures web hosts and servers, and provides comprehensive insights and analytics, letting organizations take appropriate threat remediation measures for the present and future. It also tests the effectiveness of the latest cybersecurity policies, firewalls, DNS, and mobile security, and detects the most vulnerable routes to incident and investigation.
This whitepaper discusses some common challenges faced during web application penetration testing. It covers the costs of these pen tests, tools and workflows, and pitfalls experienced by end-users due to poor password setting and account management use cases. The whitepaper also emphasizes the importance of continuous testing and encourages organizations to integrate the latest pen testing workflows into their overall security strategy. It provides deep insights into the pros and cons of different pen testing methodologies, summarizing which measures are appropriate for varying threat scenarios. Automated testing may produce false positives, so manual intervention is sometimes needed. The best approach to security is adopting a holistic approach and combining the best of smart technologies, automation, and manual web penetrating testing solutions.
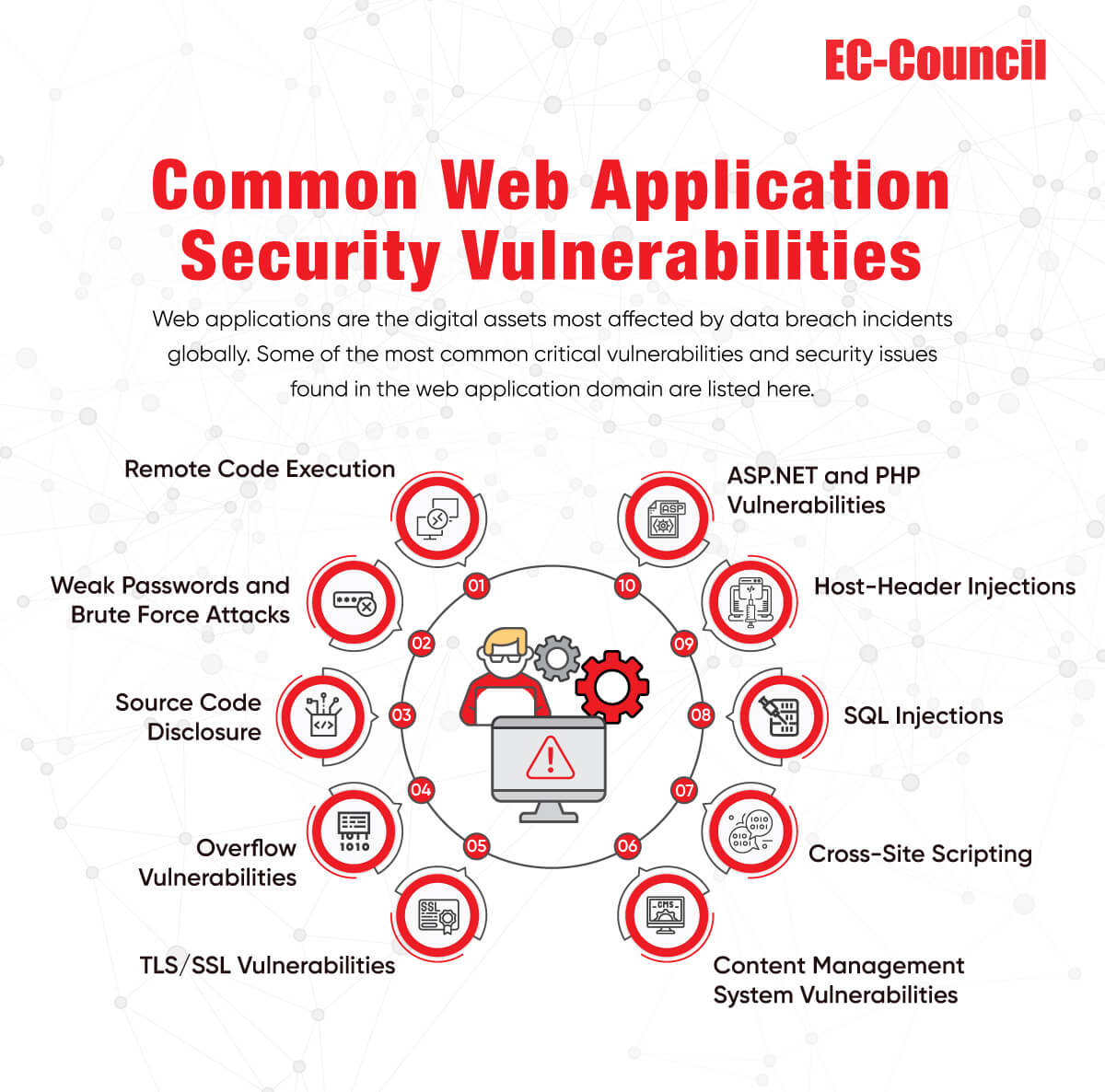
Learn how to prevent sophisticated attacks such as SQL injections, broken authentication, server attacks, cross-site scripting, session management, and other hidden threats in this whitepaper. The goal is to improve cyber awareness and learn how to safeguard users’ accounts and data so that perpetrators do not hijack access. There are multiple penetration testing strategies worth following, and we will cover the most common ones in this paper. Read on to understand more about sealing cybersecurity loopholes and protecting your organization with world-class web application penetration testing methodologies today!









