Penetration Testing Methodologies for Cloud Applications
EC-Council’s whitepaper on Penetration Testing Methodologies for Cloud Applications, authored by Mirza Khasim, Senior Principal IT Security Analyst at Oracle, delves into the importance of conducting regular penetration testing of cloud-based applications to identify potential security vulnerabilities and mitigate them before malicious actors can exploit them.
The whitepaper provides a comprehensive overview of the various penetration testing methodologies and tools that can be used to identify and exploit vulnerabilities in cloud applications. It emphasizes the need for a structured approach to penetration testing that includes defining clear objectives, identifying potential threats, selecting appropriate testing methods, and conducting thorough testing to identify vulnerabilities. The whitepaper also highlights the importance of compliance with regulatory standards such as the Payment Card Industry Data Security Standard (PCI-DSS) and the General Data Protection Regulation (GDPR) when conducting penetration testing of cloud applications. Adherence to these standards is critical for ensuring the security of cloud-based applications and protecting sensitive data from unauthorized access.
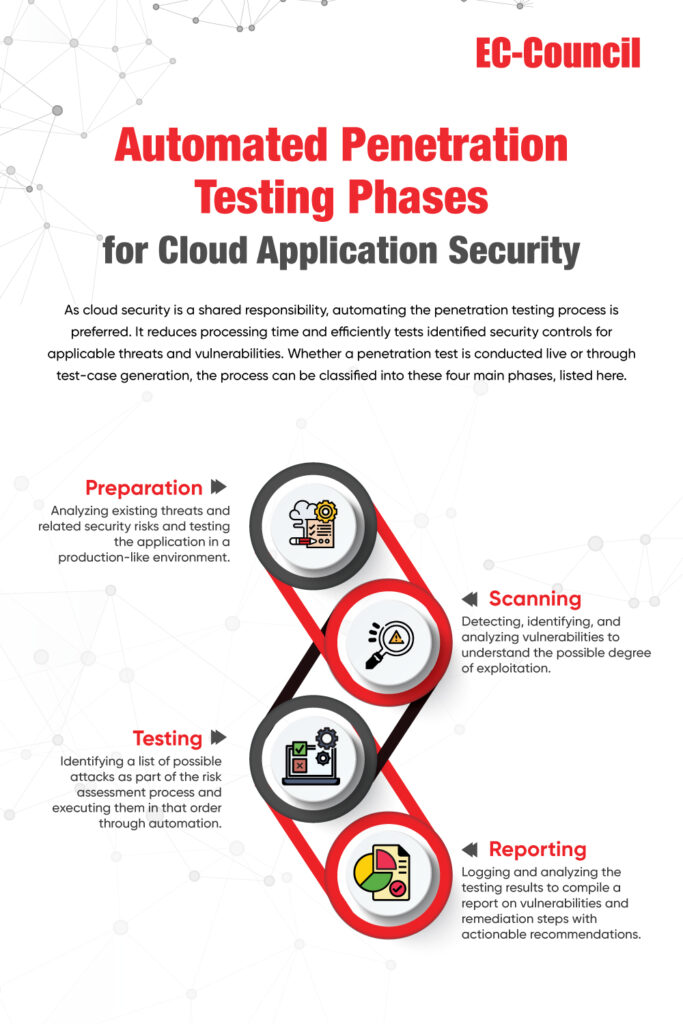
One of the key takeaways from the whitepaper is the importance of selecting the right penetration testing tools and methodologies based on the specific requirements of the cloud application being tested. The whitepaper further stresses the need for a customized approach that considers factors such as the type of application, the underlying infrastructure, and the potential attack vectors that attackers could use.
Overall, the whitepaper provides a valuable resource for IT security professionals and organizations looking to enhance the security of their cloud-based applications through regular penetration testing. It offers a wealth of practical advice and guidance on designing and executing effective penetration testing programs, as well as insights into the latest penetration testing tools and techniques.
In conclusion, the whitepaper is a must-read for anyone responsible for the security of cloud-based applications, including IT security professionals, application developers, and compliance officers. By following the recommendations and best practices outlined in the paper, organizations can significantly improve the security of their cloud applications and reduce the risk of data breaches and other security incidents.
To download the whitepaper and learn more about the best practices for conducting penetration testing of cloud applications, submit your details in the form below.









