Certifications, courses, labs, and CTFs—all in one place
Build a cyber-ready workforce with the world’s largest online cybersecurity course library.
Turn regulatory requirements into real-world resilience with EC-Council Learning: hands-on labs, global certifications, and workforce analytics that build strong teams and prove compliance.
Backed by two decades of global leadership, we empower organizations with scalable, structured training featuring expert-led courses, accredited certifications, hands-on labs, real-world simulations, and specialized content on AI-driven threats and defenses.
We Help You Achieve:
"*" indicates required fields
EC-Council Learning transforms workforce training into measurable risk reduction.
With courses, practice labs, cyber ranges, and role-specific certification pathways, your teams build applied skills to detect, defend, and lead. Trusted by governments, militaries, and 7 of the Fortune Top 10, EC-Council Learning ensures your organization is audit-ready and your teams battle-ready.
"*" indicates required fields
Get a high-level view of the core security categories your teams can train in. From offensive security to compliance, each domain reflects real-world functions, risks, and capabilities critical to enterprise resilience.
Get a high-level view of the core security categories your teams can train in. From offensive security to compliance, each domain reflects real-world functions, risks, and capabilities critical to enterprise resilience.
Artificial Intelligence for Cybersecurity
Defensive Security
Governance Risk and Compliance
Application Security
IT Essentials
Digital Forensics and Incident Response
This course develops Metasploit capabilities across scanning, exploitation, and post-exploitation to support professional-grade penetration testing.
Level
Hours of Learning
Video Lessons
…and more
This course develops practical Netcat skills for penetration testing, black box analysis, and network troubleshooting across real-world environments.
Level
Hours of Learning
Video Lessons
…and more
Enable teams to investigate, detect, and defend systems against modern threats through structured threat hunting techniques and industry-standard practices.
Level
Hours of Learning
Video Lessons
…and more
This course develops the ability to assess the Log4j vulnerability, identify organizational risk, and implement mitigation strategies when patching is not feasible.
Level
Hours of Learning
Video Lessons
…and more
This course develops foundational skills for assessing and securing AWS environments through pentesting techniques across key cloud services.
Level
Hours of Learning
Video Lessons
Enable teams to detect, contain, and eliminate breaches while reducing remediation costs through practical zero-day defense strategies and offensive techniques.
Level
Hours of Learning
Video Lessons
…and more
This course develops a foundational understanding of advanced persistent threats, equipping teams to detect, mitigate, and respond to APT attacks through practical strategies and analysis.
Level
Hours of Learning
Video Lessons
…and more
This course develops the skills required to use C++ for penetration testing, combining core programming knowledge with practical security applications.
Level
Hours of Learning
Video Lessons
…and more
This course develops the ability to identify, assess, and manage vulnerabilities using modern tools and techniques to reduce security risks and support organizational defense.
Level
Hours of Learning
Video Lessons
…and more
This course develops expertise in network security and ethical hacking methodologies to assess and strengthen network infrastructures against cyber threats.
Level
Hours of Learning
Video Lessons
This course develops the ability to apply computational intelligence techniques to enhance cybersecurity outcomes through adaptive and intelligent defense strategies.
Level
Hours of Learning
Video Lessons
…and more
This course develops the ability to enhance network security using AI techniques for threat detection, response, and strategic implementation within existing infrastructures.
Level
Hours of Learning
Video Lessons
…and more
This course develops foundational skills to secure robotic and autonomous systems, enhancing safety, reliability, and operational resilience.
Level
Hours of Learning
Video Lessons
…and more
This course develops the ability to simulate, detect, and prevent social engineering attacks using Generative AI and Large Language Models through practical applications and guided workflows.
Level
Hours of Learning
Video Lessons
…and more
This course develops foundational knowledge of information security principles, threats, and protections for IT and business environments.
Level
Hours of Learning
Video Lessons
…and more
This course helps in developing skills to automate repetitive administrative tasks using Bash shell scripting across Linux, DevOps, and cloud environments.
Level
Hours of Learning
Video Lessons
This course introduces foundational digital forensics techniques for identifying, analyzing, and documenting cyber incidents.
Level
Hours of Learning
Video Lessons
This course introduces core components of cybersecurity incident response planning, aligned with best practices and real-world operational frameworks.
Level
Hours of Learning
Video Lessons
This course explores advanced techniques for extracting, analyzing, and preserving forensic evidence from drones to support investigative operations.
Level
Hours of Learning
Video Lessons
This course introduces data mining techniques for identifying and mitigating financial fraud using real-world case studies and applied models.
Level
Hours of Learning
Video Lessons
This course provides strategies to define, track, and analyze key metrics for evaluating and improving incident response effectiveness.
Level
Hours of Learning
Video Lessons
This course covers foundational concepts and techniques for conducting forensic investigations on virtual machines.
Level
Hours of Learning
Video Lessons
This course introduces the principles and techniques used to investigate web-based incidents and analyze digital evidence across online environments.
Level
Hours of Learning
Video Lessons
…and more
This course explores forensic methodologies and investigative techniques for uncovering digital evidence in IoT ecosystems.
Level
Hours of Learning
Video Lessons
…and more
This course covers forensic memory acquisition and analysis to detect intrusions, reconstruct system activity, and support digital investigations.
Level
Hours of Learning
Video Lessons
This course focuses on adversary emulation using Atomic Red Team to validate security controls and enhance detection capabilities across the MITRE ATT&CK framework.
Level
Hours of Learning
Video Lessons
This course develops advanced skills in applying Generative AI and Large Language Models to enhance cybersecurity strategies and defend against evolving threats.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to apply computational intelligence techniques to enhance cybersecurity outcomes through adaptive and intelligent defense strategies.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to enhance network security using AI techniques for threat detection, response, and strategic implementation within existing infrastructures.
Level
Hours of Learning
Video Lessons
...and more.
This course develops foundational skills to secure robotic and autonomous systems, enhancing safety, reliability, and operational resilience.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to simulate, detect, and prevent social engineering attacks using Generative AI and Large Language Models through practical applications and guided workflows.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to apply Large Language Models in technical support environments to enhance troubleshooting, automate support tasks, and build simple AI-powered workflows.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to build and apply AI-driven tools to detect, simulate, and defend against phishing attacks using machine learning and generative AI techniques.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to integrate AI-powered security into DevSecOps workflows, supporting secure development, automated analysis, and continuous compliance.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to conduct efficient security audits using ChatGPT, streamlining compliance, improving accuracy, and addressing AI-related risks.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the skills to use AI and machine learning in penetration testing and bug bounty hunting, automating reconnaissance, exploitation, and reporting.
Level
Hours of Learning
Video Lessons
...and more.
This course develops Metasploit capabilities across scanning, exploitation, and post-exploitation to support professional-grade penetration testing.
Level
Hours of Learning
Video Lessons
...and more.
Enable teams to detect, contain, and eliminate breaches while reducing remediation costs through practical zero-day defense strategies and offensive techniques.
Level
Hours of Learning
Video Lessons
...and more.
Enable teams to investigate, detect, and defend systems against modern threats through structured threat hunting techniques and industry-standard practices.
Level
Hours of Learning
Video Lessons
This course develops the ability to assess the Log4j vulnerability, identify organizational risk, and implement mitigation strategies when patching is not feasible.
Level
Hours of Learning
Video Lessons
This course develops foundational skills for assessing and securing AWS environments through pentesting techniques across key cloud services.
Level
Hours of Learning
Video Lessons
This course develops practical Netcat skills for penetration testing, black box analysis, and network troubleshooting across real-world environments.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the skills required to use C++ for penetration testing, combining core programming knowledge with practical security applications.
Level
Hours of Learning
Video Lessons
...and more.
This course develops a foundational understanding of advanced persistent threats, equipping teams to detect, mitigate, and respond to APT attacks through practical strategies and analysis.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to identify, assess, and manage vulnerabilities using modern tools and techniques to reduce security risks and support organizational defense.
Level
Hours of Learning
Video Lessons
...and more.
This course develops expertise in network security and ethical hacking methodologies to assess and strengthen network infrastructures against cyber threats.
Level
Minutes of Learning
Video Lessons
...and more.
This course develops the ability to conduct ethical OSINT investigations using privacy-aware methods and industry tools within a secure Linux environment.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the skills needed to protect organizational networks from cyber threats using layered security approaches, VPNs, and vulnerability discovery techniques.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to identify, analyze, and mitigate cyber threats using industry frameworks, threat models, and intelligence tools.
Level
Hours of Learning
Video Lessons
...and more.
This course develops advanced skills in understanding, configuring, and troubleshooting next-generation firewalls to secure modern network environments.
Level
Hours of Learning
Video Lessons
This course develops foundational knowledge of digital twins, their security implications, and practical approaches to simulating and defending cyber-physical systems.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to apply deception strategies for early intrusion detection and infrastructure protection through practical tools and decoy deployment.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to use Microsoft Defender for Endpoint to prevent, detect, investigate, and respond to advanced threats across enterprise environments.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to trace digital footprints using OSINT tools and techniques to enhance organizational defense and reduce exposure.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the skills to secure PowerShell environments by identifying exploits, implementing controls, and applying scripting best practices.
Level
Hours of Learning
Video Lessons
...and more.
This course develops advanced skills in network intrusion detection using Suricata, PCAP forensics, and automation for scalable detection and response.
Level
Hours of Learning
Video Lessons
...and more.
This course develops foundational knowledge of information security principles, threats, and protections for IT and business environments.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the ability to identify, evaluate, and manage information security risks to strengthen organizational defenses and ensure continuous protection.
Level
Hours of Learning
Video Lessons
...and more.
This course develops essential skills to secure FinTech systems, address emerging risks, and align with regulatory frameworks across the financial technology landscape.
Level
Hours of Learning
Video Lessons
...and more.
This course develops the capabilities to identify, assess, and mitigate cyber risks in energy and smart grid systems through sector-specific strategies and controls.
Level
Hours of Learning
Video Lessons
This course develops the knowledge to implement and align organizational cybersecurity practices with ISO/IEC 27001:2022, focusing on compliance, control selection, and risk reduction.
Level
Hours of Learning
Video Lessons
This course develops foundational knowledge of data governance to help implement effective frameworks, align compliance and privacy programs, and manage the data lifecycle.
Level
Hours of Learning
Video Lessons
This course develops essential skills for implementing and maintaining PCI DSS compliance to protect cardholder data, reduce breach risks, and meet regulatory standards.
Level
Hours of Learning
Video Lessons
This course equips teams to oversee and maintain SOC 2 compliance with a structured approach to controls, audits, and ongoing assurance.
Level
Hours of Learning
Video Lessons
...and more.
Implement ISO 31000 to build a structured, scalable risk management framework that supports cybersecurity and business continuity.
Level
Hours of Learning
Video Lessons
Master the EU CRA and implement secure product practices throughout the digital lifecycle.
Level
Hours of Learning
Video Lessons
This course introduces foundational digital forensics techniques for identifying, analyzing, and documenting cyber incidents.
Level
Hours of Learning
Video Lessons
This course introduces core components of cybersecurity incident response planning, aligned with best practices and real-world operational frameworks.
Level
Hours of Learning
Video Lessons
This course explores advanced techniques for extracting, analyzing, and preserving forensic evidence from drones to support investigative operations.
Level
Hours of Learning
Video Lessons
This course introduces data mining techniques for identifying and mitigating financial fraud using real-world case studies and applied models.
Level
Hours of Learning
Video Lessons
This course provides strategies to define, track, and analyze key metrics for evaluating and improving incident response effectiveness.
Level
Hours of Learning
Video Lessons
This course covers foundational concepts and techniques for conducting forensic investigations on virtual machines.
Level
Hours of Learning
Video Lessons
This course introduces the principles and techniques used to investigate web-based incidents and analyze digital evidence across online environments.
Level
Hours of Learning
Video Lessons
...and more.
This course explores forensic methodologies and investigative techniques for uncovering digital evidence in IoT ecosystems.
Level
Hours of Learning
Video Lessons
...and more.
This course covers forensic memory acquisition and analysis to detect intrusions, reconstruct system activity, and support digital investigations.
Level
Hours of Learning
Video Lessons
This course focuses on adversary emulation using Atomic Red Team to validate security controls and enhance detection capabilities across the MITRE ATT&CK framework.
Level
Hours of Learning
Video Lessons
This course covers the basics of Selenium for automating browser interactions and how to validate web applications.
Level
Hours of Learning
Video Lessons
This course focuses on identifying and remediating common security vulnerabilities in Ruby on Rails, while strengthening application resilience through secure coding practices.
Level
Hours of Learning
Video Lessons
This course provides a hands-on, structured approach to applying advanced cryptographic tools correctly to secure enterprise systems.
Level
Hours of Learning
Video Lessons
This course prepares teams to strengthen Kubernetes security across the container lifecycle and supports readiness for the CKS certification.
Level
Hours of Learning
Video Lessons
This course provides foundational strategies to integrate security into the Software Development Life Cycle (SDLC) and defend against common application threats.
Level
Hours of Learning
Video Lessons
This course focuses on integrating security into CI/CD pipelines using GitHub Actions and automation tools.
Level
Hours of Learning
Video Lessons
This course explores cryptographic principles and libraries in Python to help secure applications and protect sensitive data.
Level
Hours of Learning
Video Lessons
This course outlines how to implement Microsoft SDL practices to integrate security throughout the software development process.
Level
Hours of Learning
Video Lessons
This course focuses on automating secure configurations and troubleshooting Ansible playbooks across Linux and Windows systems.
Level
Hours of Learning
Video Lessons
This course provides practical guidance to secure MySQL databases through access control, encryption, and threat mitigation strategies.
Level
Hours of Learning
Video Lessons
This course introduces foundational data science concepts with hands-on exercises using Python and visualization tools.
Level
Hours of Learning
Video Lessons
This course covers foundational programming with Python 3 through practical coding sessions and visualization tools.
Level
Hours of Learning
Video Lessons
This course covers essential Linux networking components, tools, and commands used in enterprise environments.
Level
Hours of Learning
Video Lessons
This course helps in developing skills to automate repetitive administrative tasks using Bash shell scripting across Linux, DevOps, and cloud environments.
Level
Hours of Learning
Video Lessons
This course covers the methodologies used to protect identities and data within cloud network and compute infrastructure to support strong security posture management.
Level
Hours of Learning
Video Lessons
Equip your teams with practical skills to identify, diagnose, and resolve issues across Linux systems with confidence and efficiency.
Level
Hours of Learning
Video Lessons
This course develops essential capabilities for IT support roles by developing core troubleshooting and system administration skills.
Level
Hours of Learning
Video Lessons
This course focuses on automating enterprise and cloud infrastructure using advanced Ansible deployment techniques.
Level
Hours of Learning
Video Lessons
This course introduces PHP fundamentals, MySQL integration, array handling, and web form processing for backend development.
Level
Hours of Learning
Video Lessons
This course provides foundational and practical knowledge of Rust for developing secure, high-performance software systems.
Level
Hours of Learning
Video Lessons
 Unified Learning Ecosystem
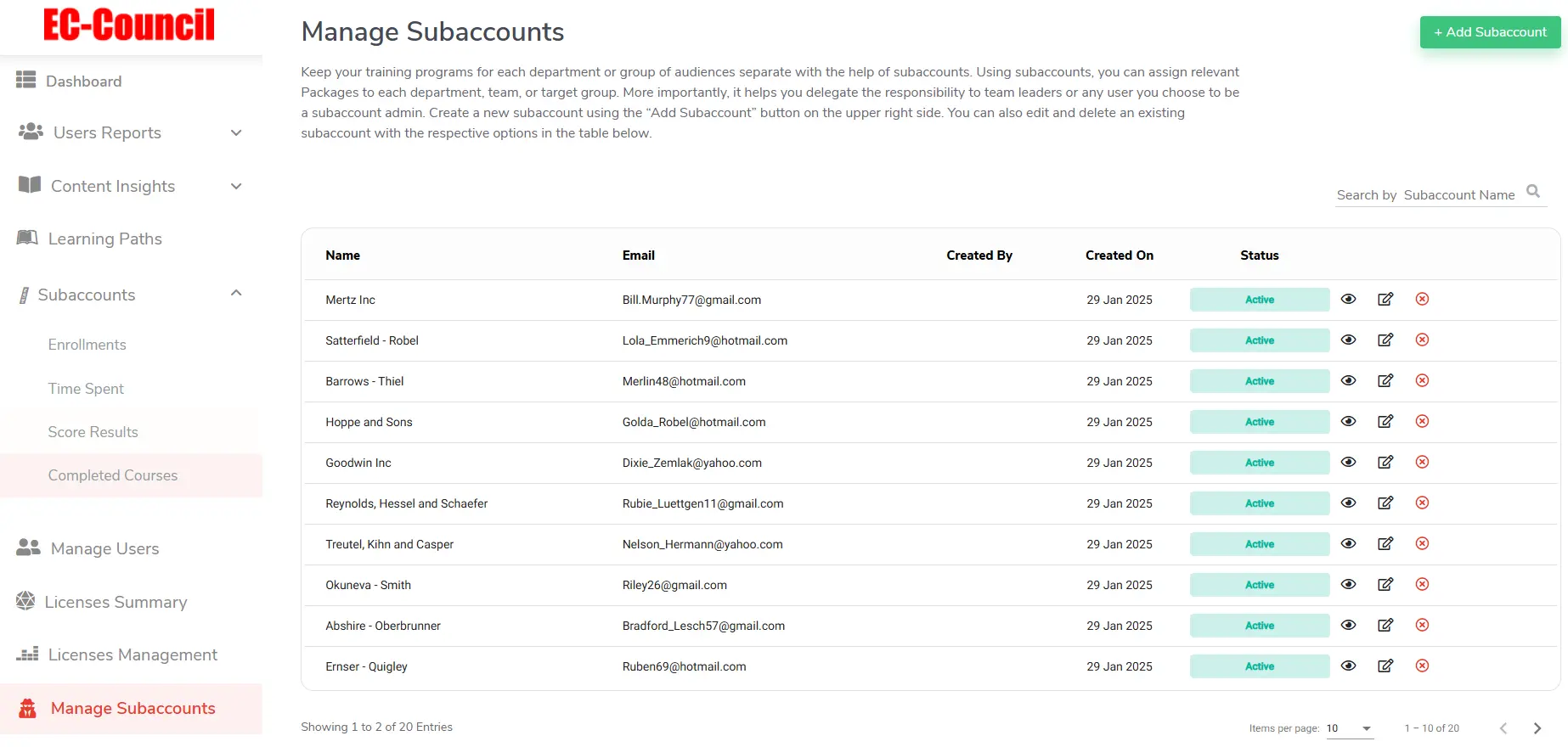
Unified Learning Ecosystem Sub-Account Management
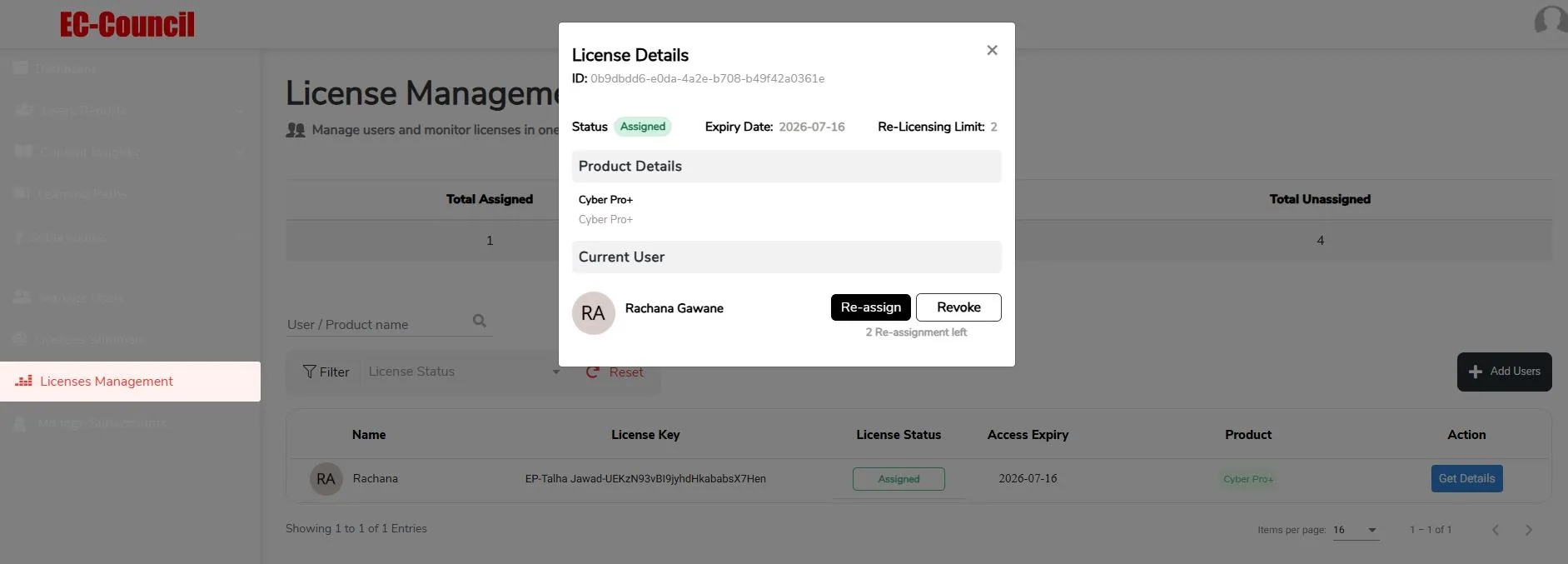
Sub-Account Management  License Reallocation
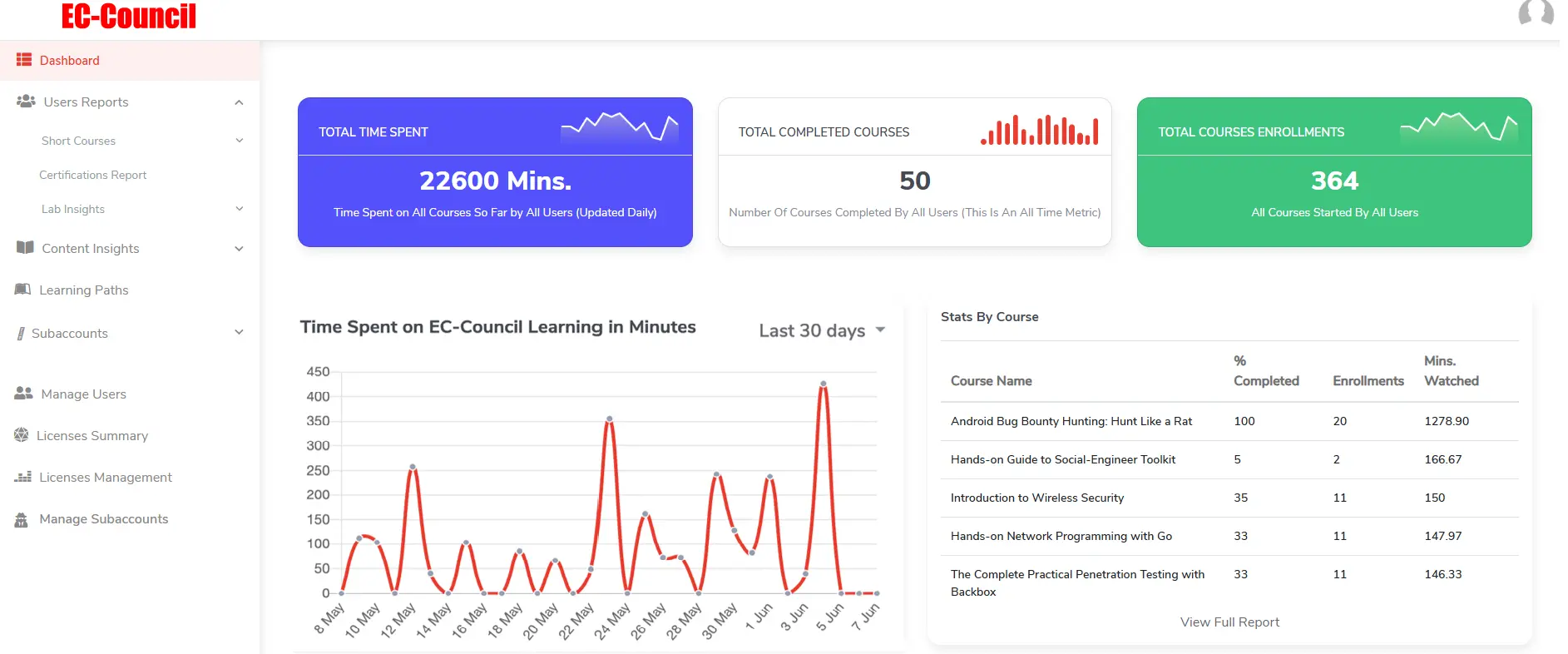
License Reallocation Advanced Analytics & Reporting
Advanced Analytics & Reporting Unified Learning Ecosystem
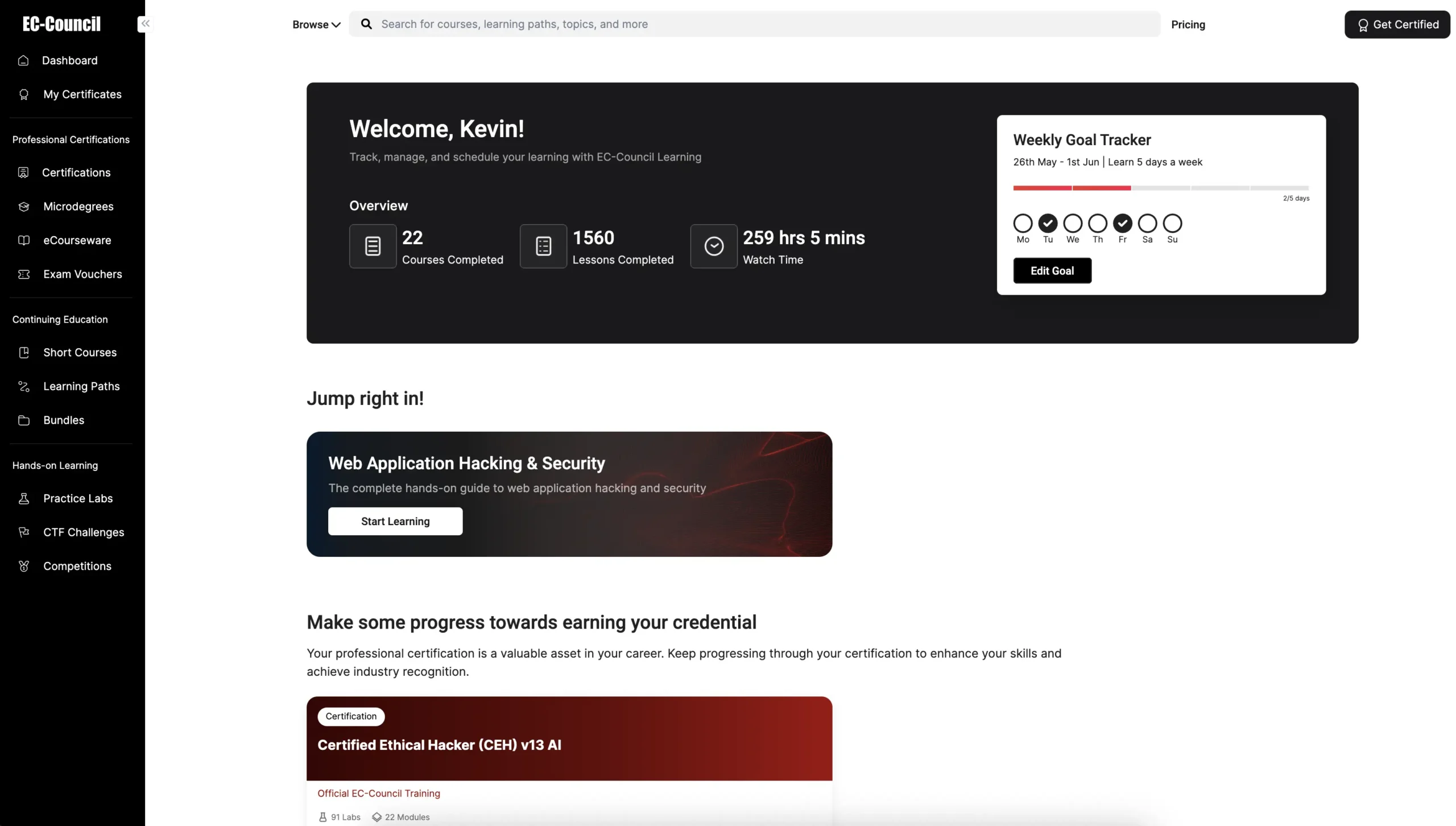
Unified Learning EcosystemCertifications, courses, labs, and CTFs—all in one place.
 Sub-Account Management
Sub-Account Management Delegate admin access by team or region. 
 License Reallocation
License ReallocationReallocate licenses to new users at no extra cost.
 Advanced Analytics & Reporting
Advanced Analytics & ReportingTrack progress, impact, and generate audit-ready reports.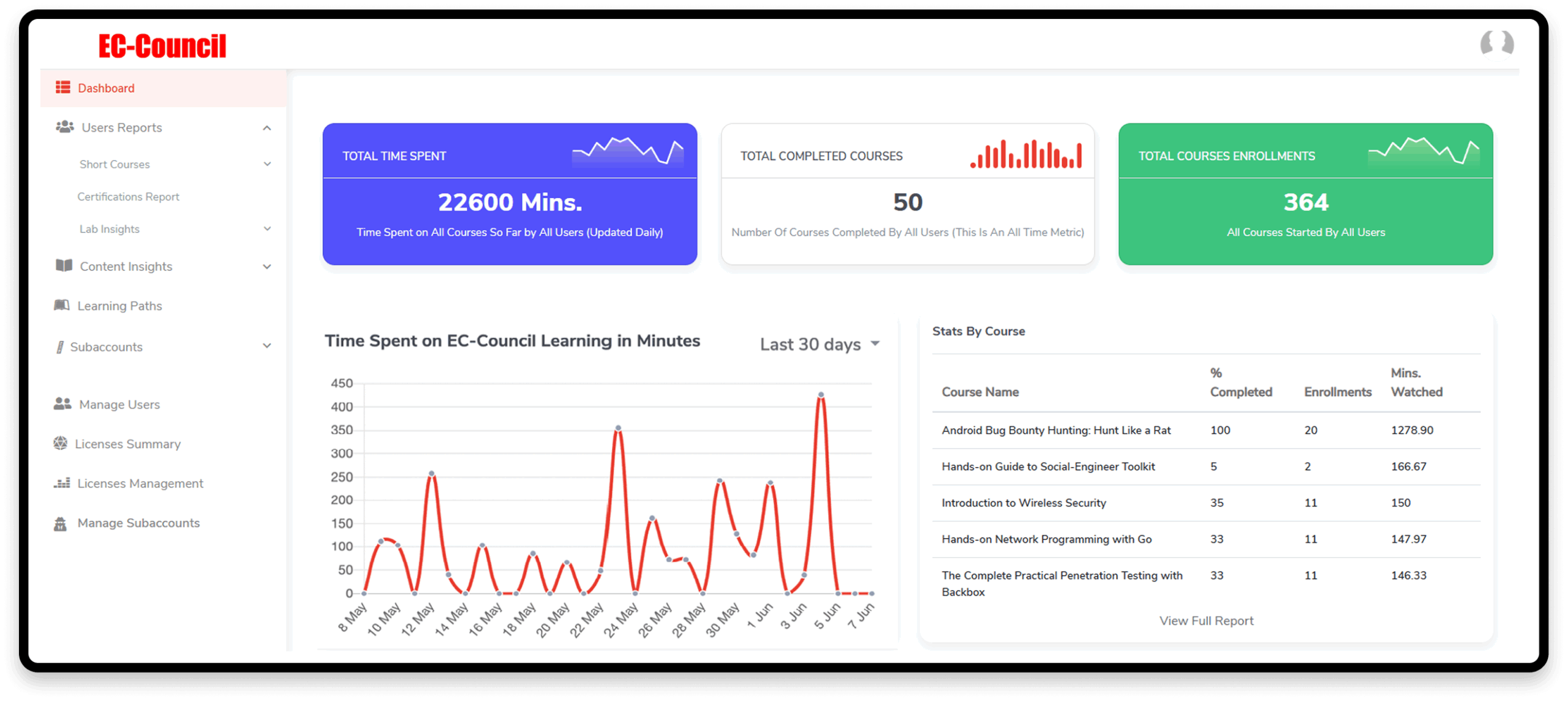
Purpose-built capabilities designed to meet the real needs of modern cybersecurity organizations.
Certifications, courses, labs, and CTFs—all in one place

Delegate admin access by team or region
Reallocate licenses to new users at no extra cost
Track progress, impact, and generate audit-ready reports.
Equip your workforce with practical cyber expertise through immersive, scenario-driven training—bridging the gap between knowledge and real-world execution.
Not Just Training. A True Cyber Range Experience
EC-Council Learning immerses your teams in realistic, high-stakes environments where they can safely make mistakes, learn fast, and harden defenses. Every experience builds measurable, lasting skills.
![]() 150+ CTF challenges for real-world readiness.
150+ CTF challenges for real-world readiness.
![]() Build skills and make learning stick, through hands-on practice.
Build skills and make learning stick, through hands-on practice.
Stronger Teams. Lower Risk. Real Results.
With EC-Council Learning for Teams, you get more than training; you get an always-on platform that builds resilience, sharpens skills, streamlines compliance, and proves ROI. Equip your workforce with the skills, pathways, and insights to stay prepared for tomorrow’s threats, today.
For Enterprise
Features
Pro
Pro+

Access to 800+ Courses & 50+ Learning Paths
800+ Practice Lab Exercises & 150+ CTF Challenges
Official EC-Council Essentials Certifications (3 certifications)
Globally Recognized EC-Council Certifications
Add On
Add On

User-Level Reporting (Individual & Teams)
Course-Level & Sub-Account Level Reporting

Course Assignment
Custom Learning Paths
Group Management Sub-Accounts
License Relocation
Admin Controls

Single Sign-Ons*
API Integrations*
Every hour of training should move your team closer to cyber-readiness. With EC-Council Learning for teams, you gain a proven framework for upskilling at scale, ensuring time, resources, and budget are focused on building measurable capabilities, not just ticking boxes.
Built For Impact. Backed by numbers.
Trusted by professionals worldwide.
Validated by real user feedback
Rated for quality, revelance, and depath.
For Enterprise
Features
Pro
Pro+
| Access to 700+ Courses and 70+ Learning Paths | ||
| 1400+ Practice Lab Exercises & 150+ CTF Challenges | ||
| Globally Recognized EC-Council Certifications | Add On | Add On |
| User-Level Reporting (Individual Teams) | ||
| Course-Level & Sub-Account Level Reporting |
| Course Assignment | ||
| Custom Learning Paths | ||
| Group Management Sub-Accounts | ||
| License Relocation | ||
| Admin Controls |
| Single Sign-Ons* | ||
| API Integrations* |
*Terms and conditions apply. The features are subject to eligibility and integration scope.
Home > Enterprise > Cybersecurity Training for Teams
"*" indicates required fields
"*" indicates required fields