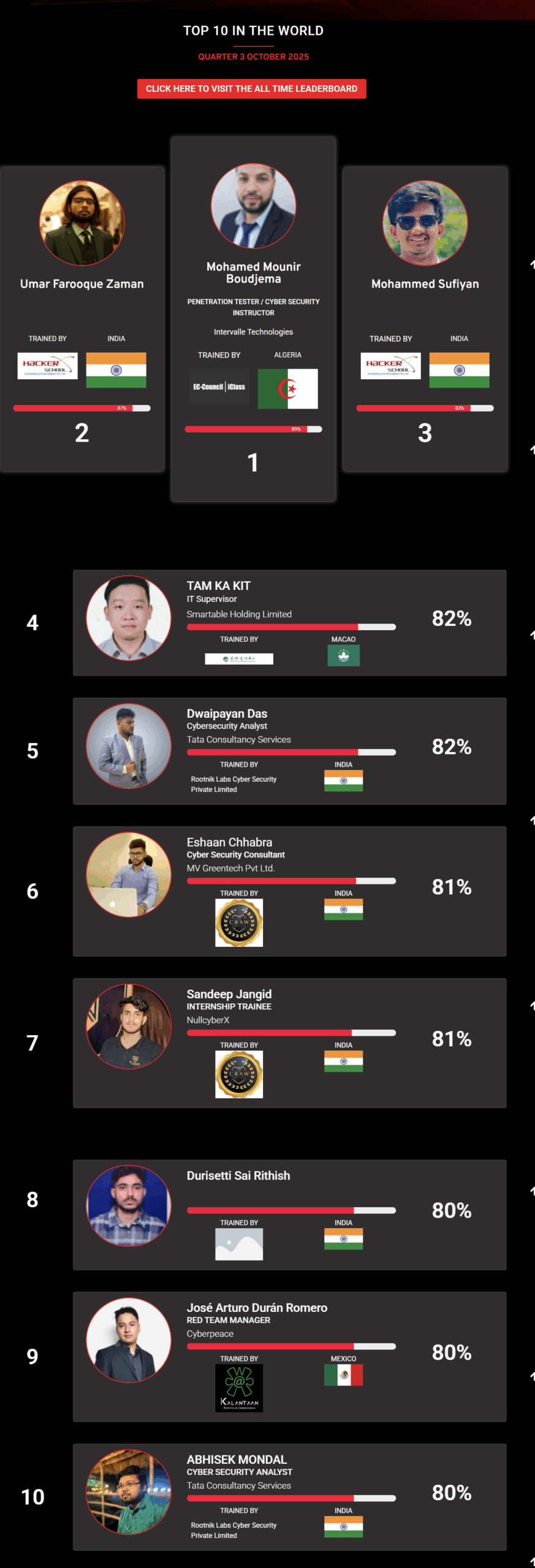
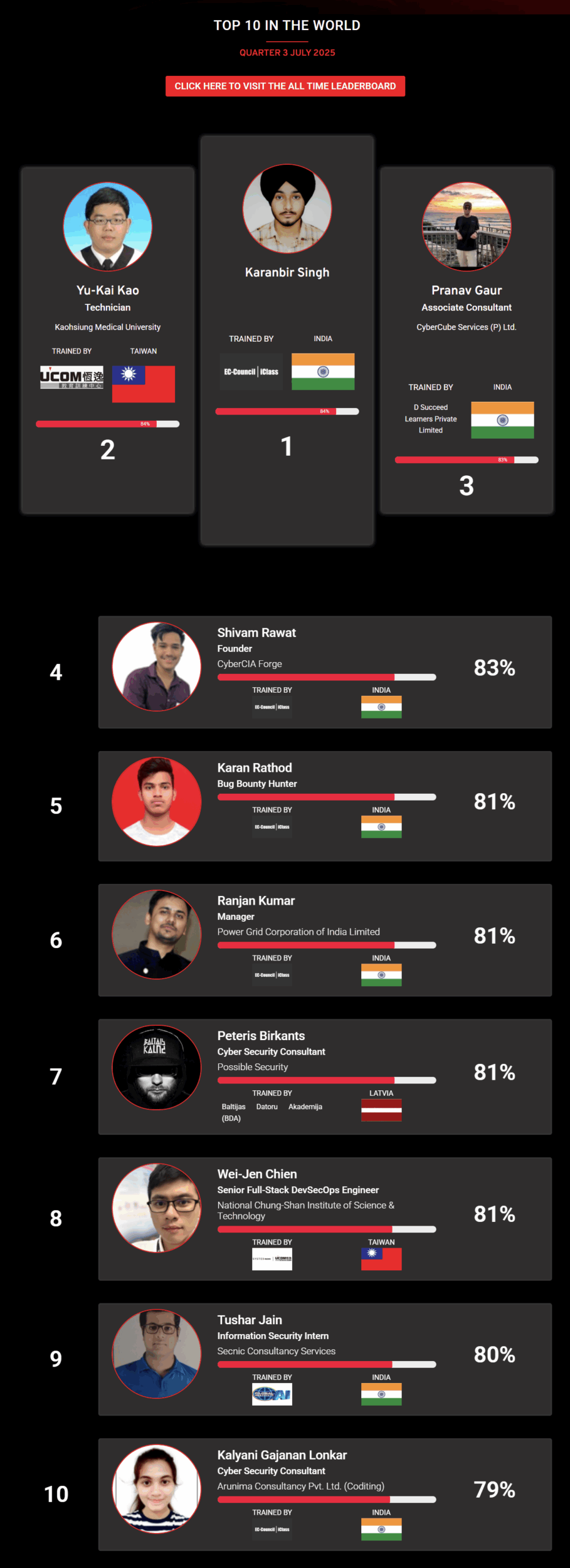
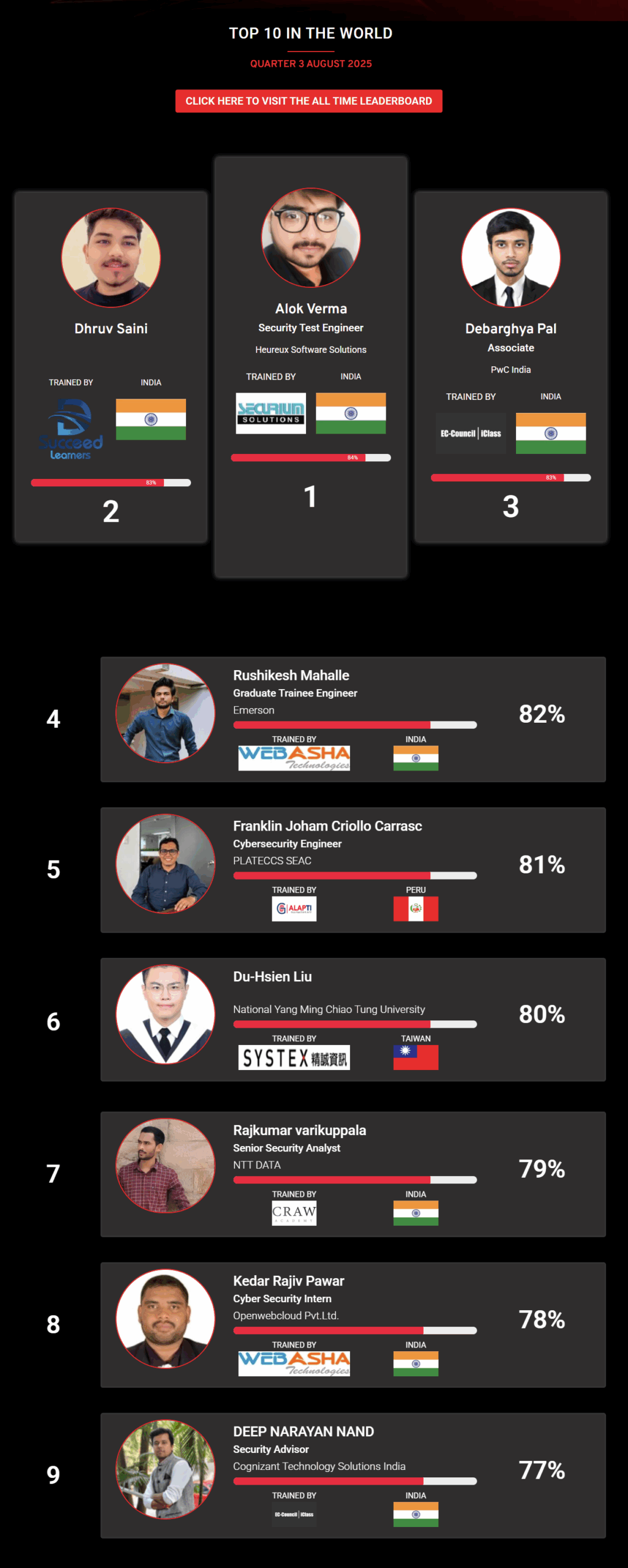
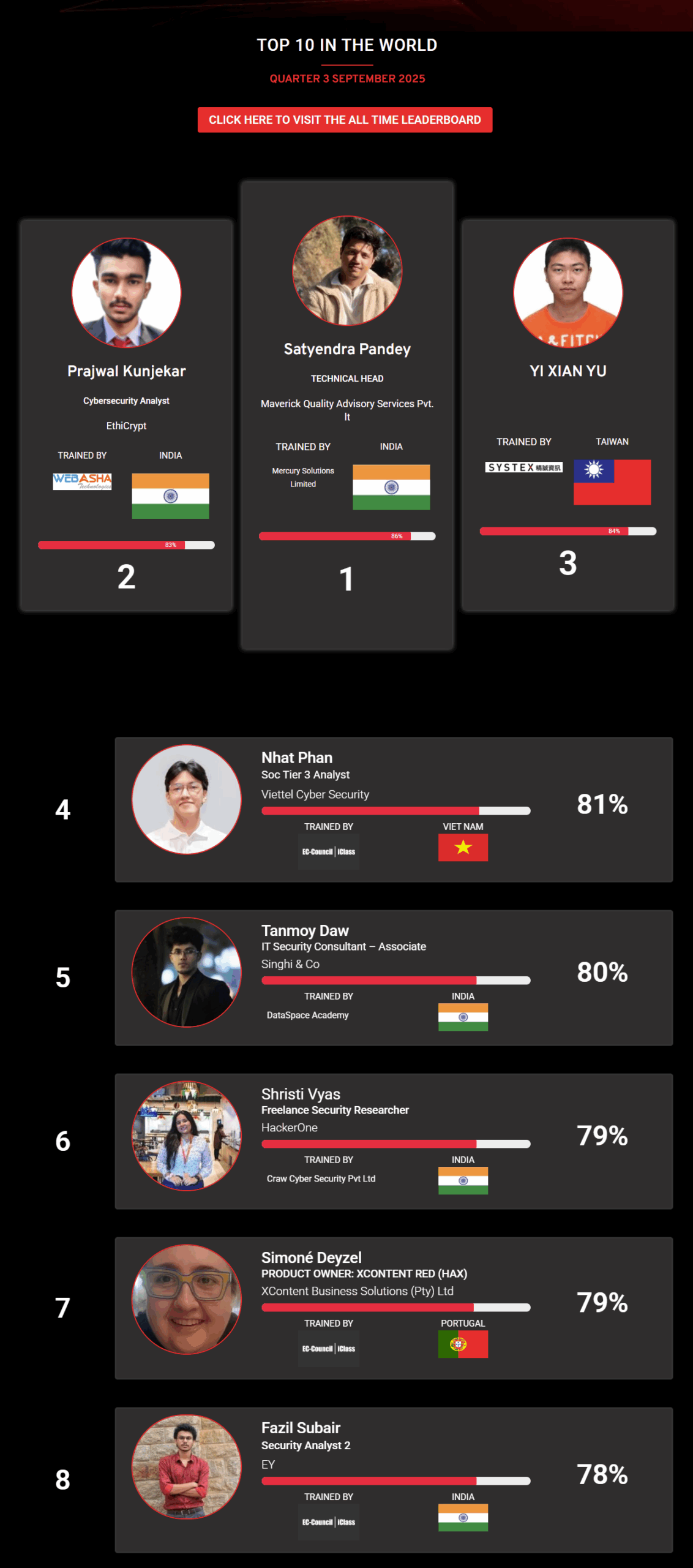
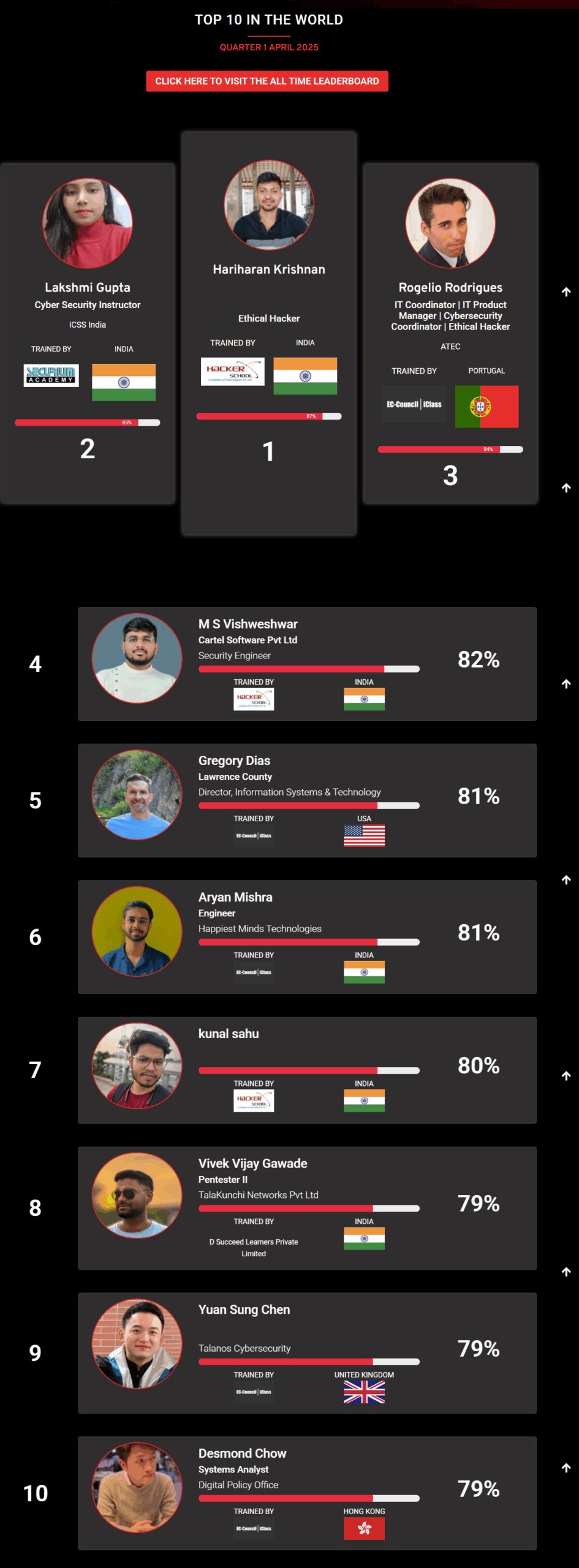
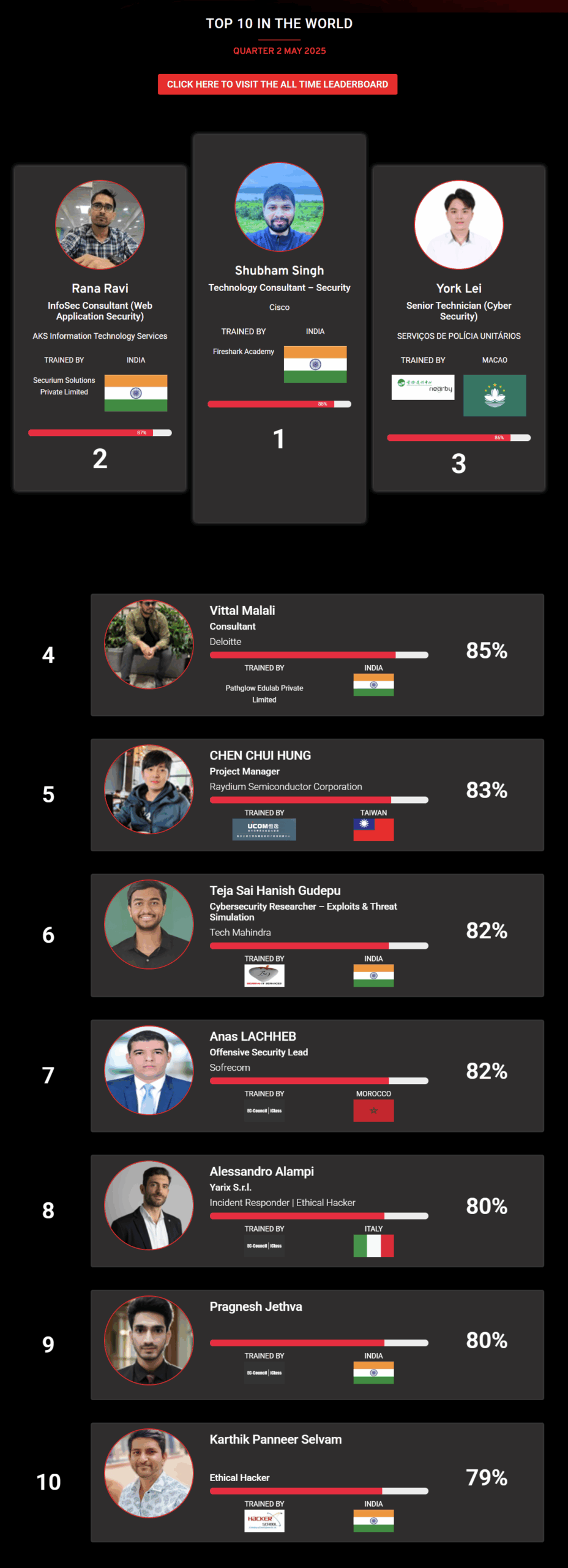
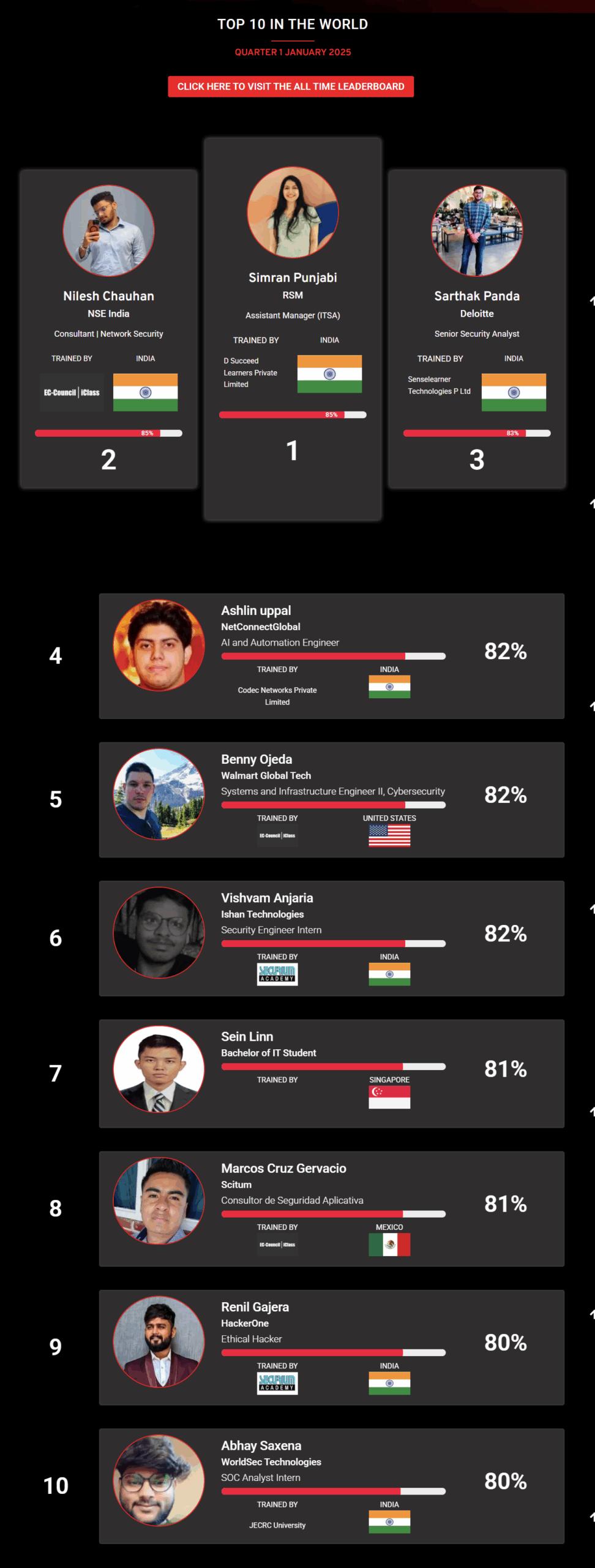
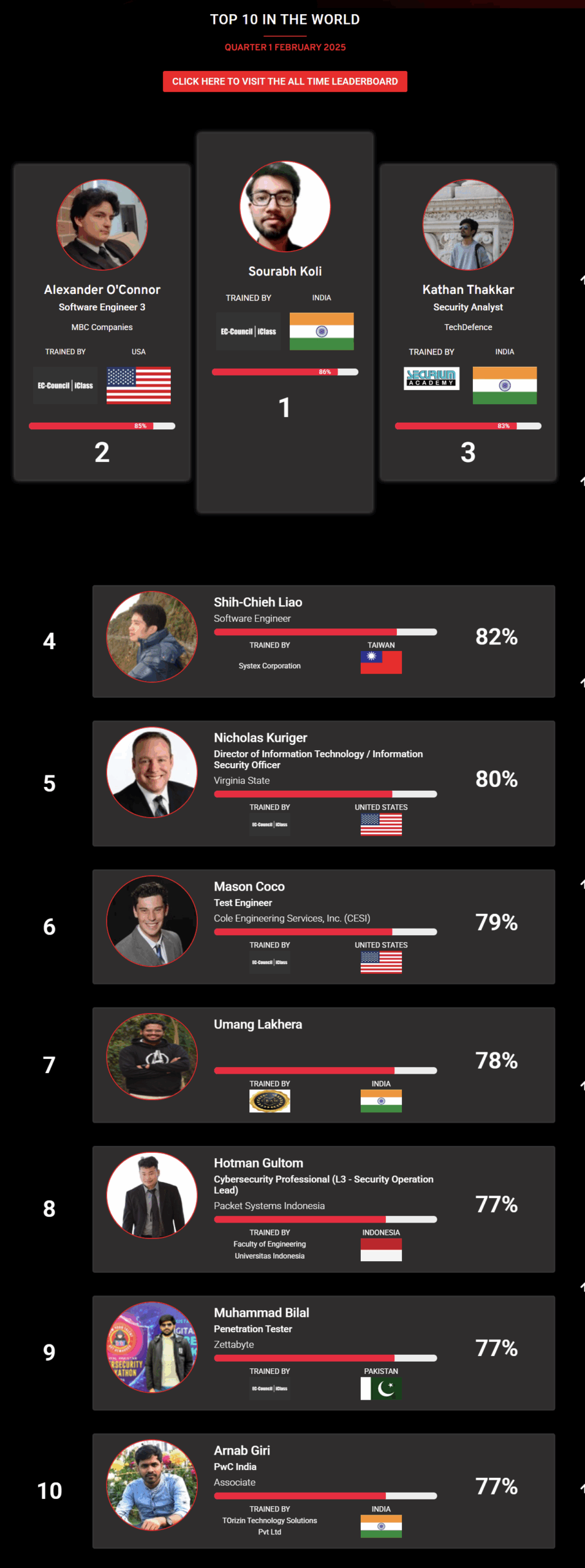
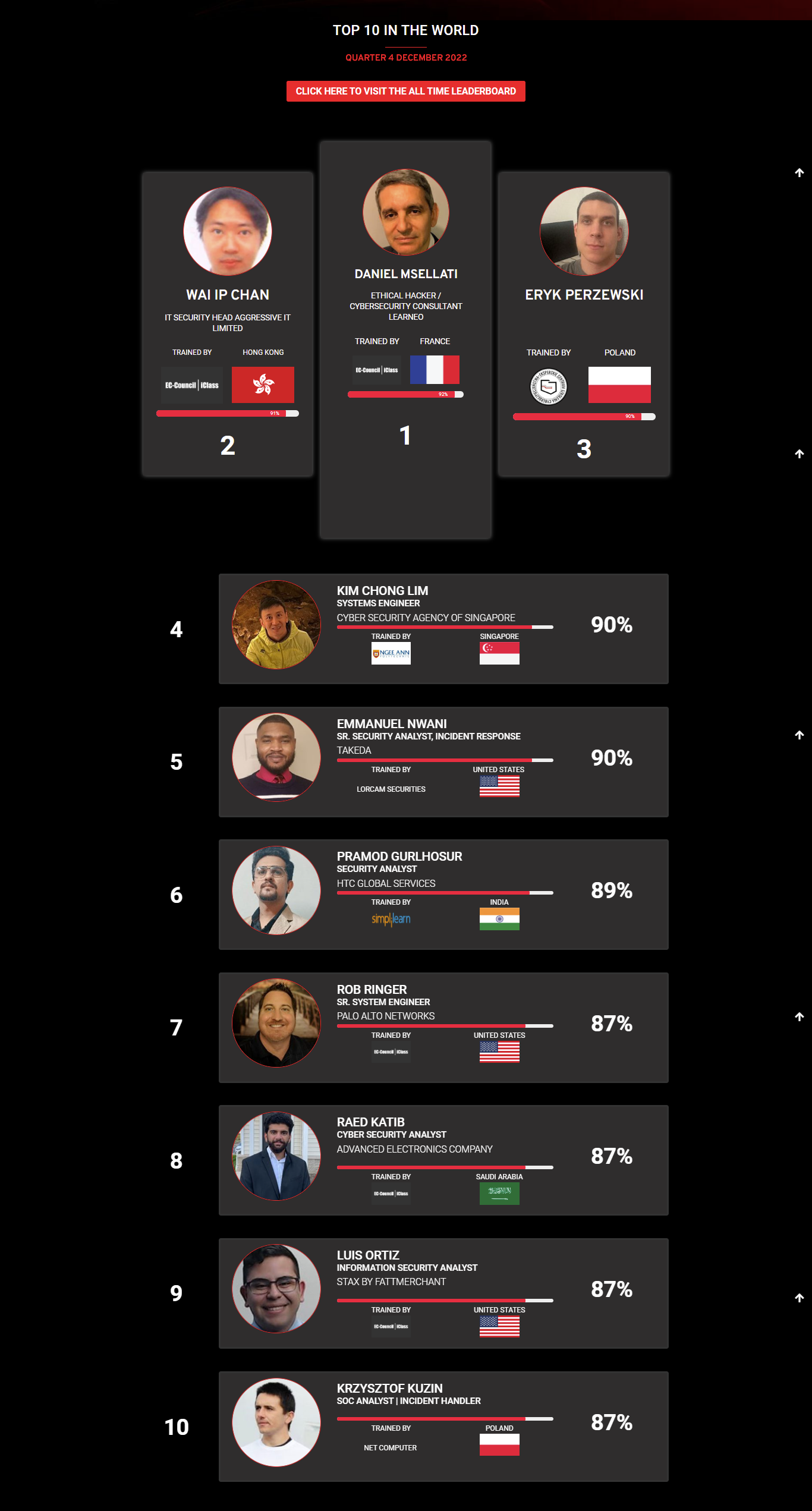
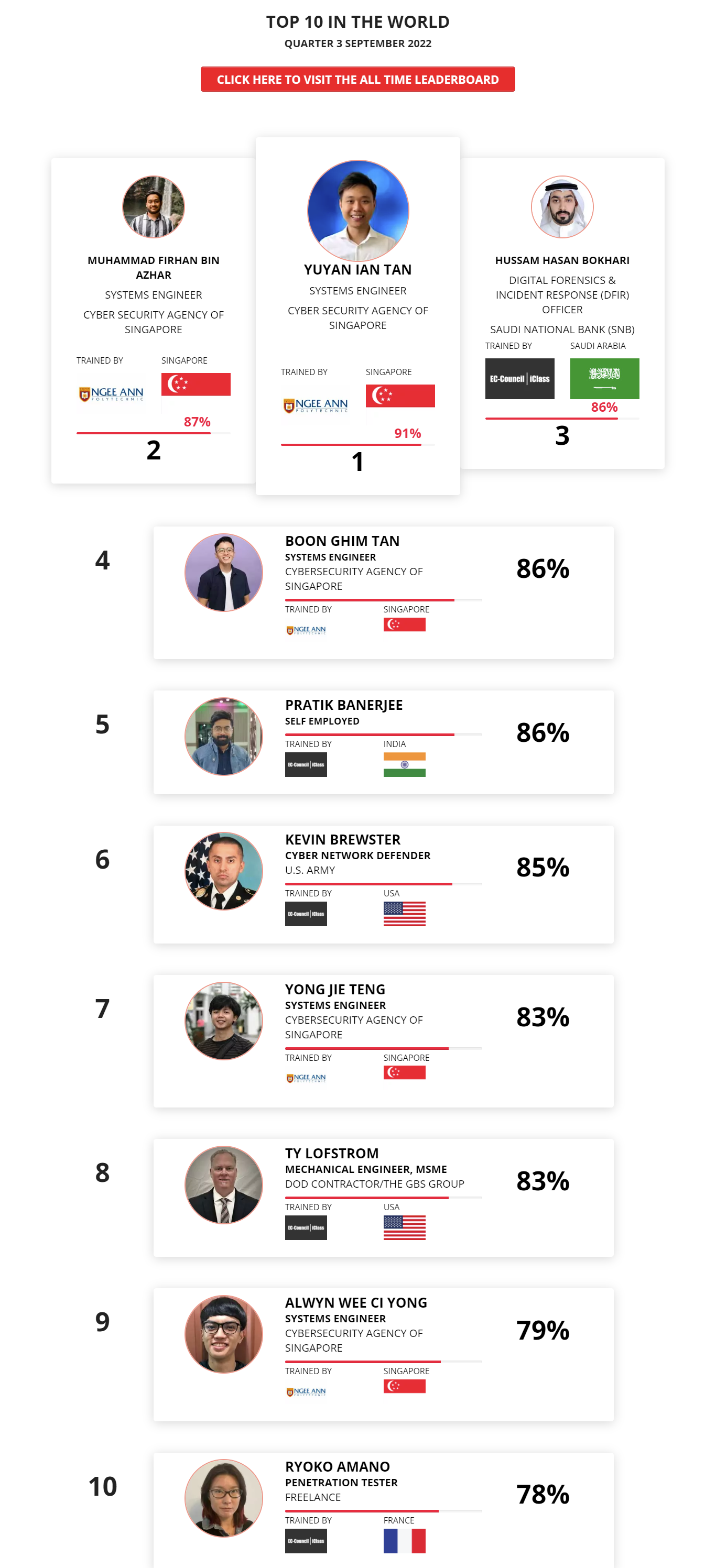
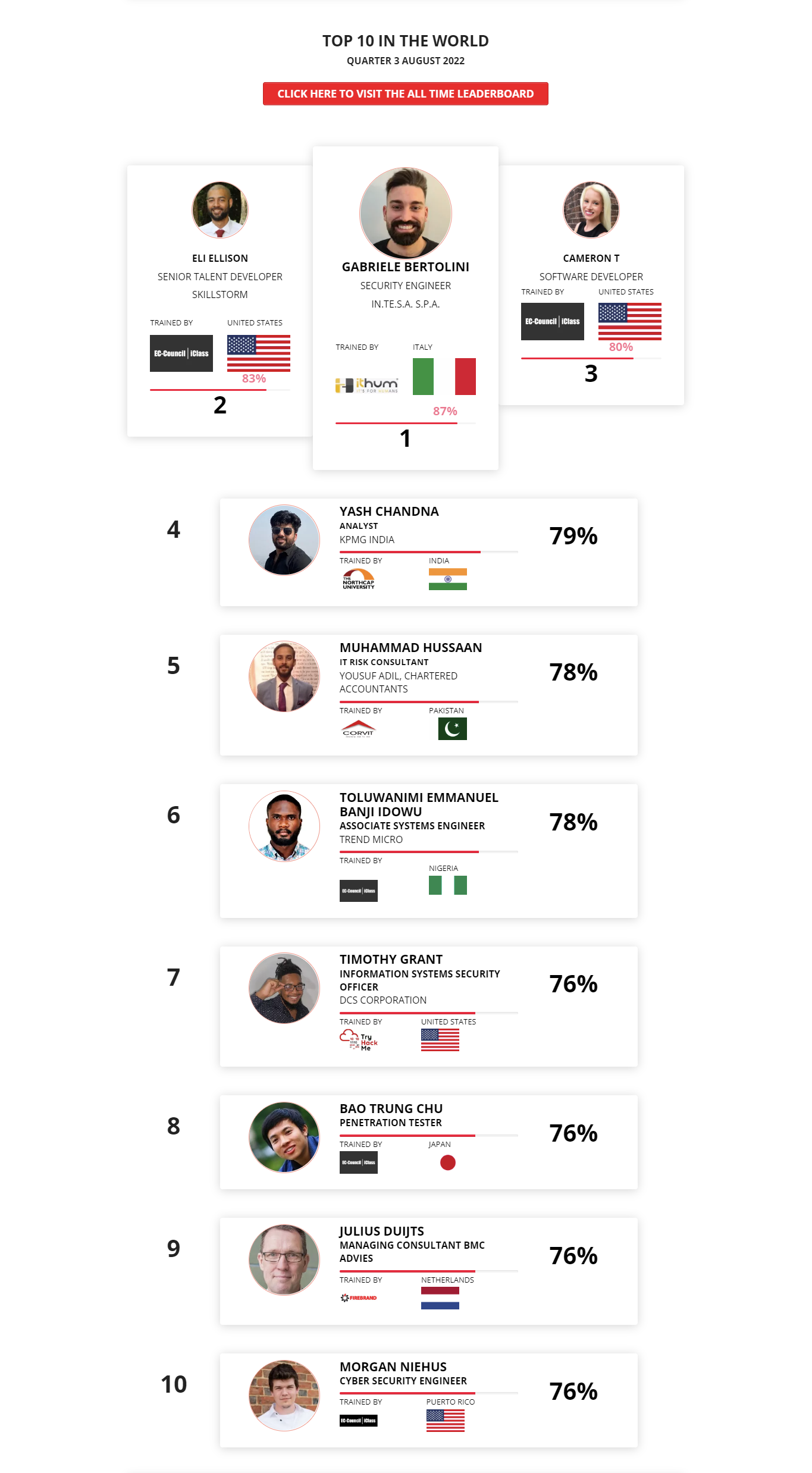
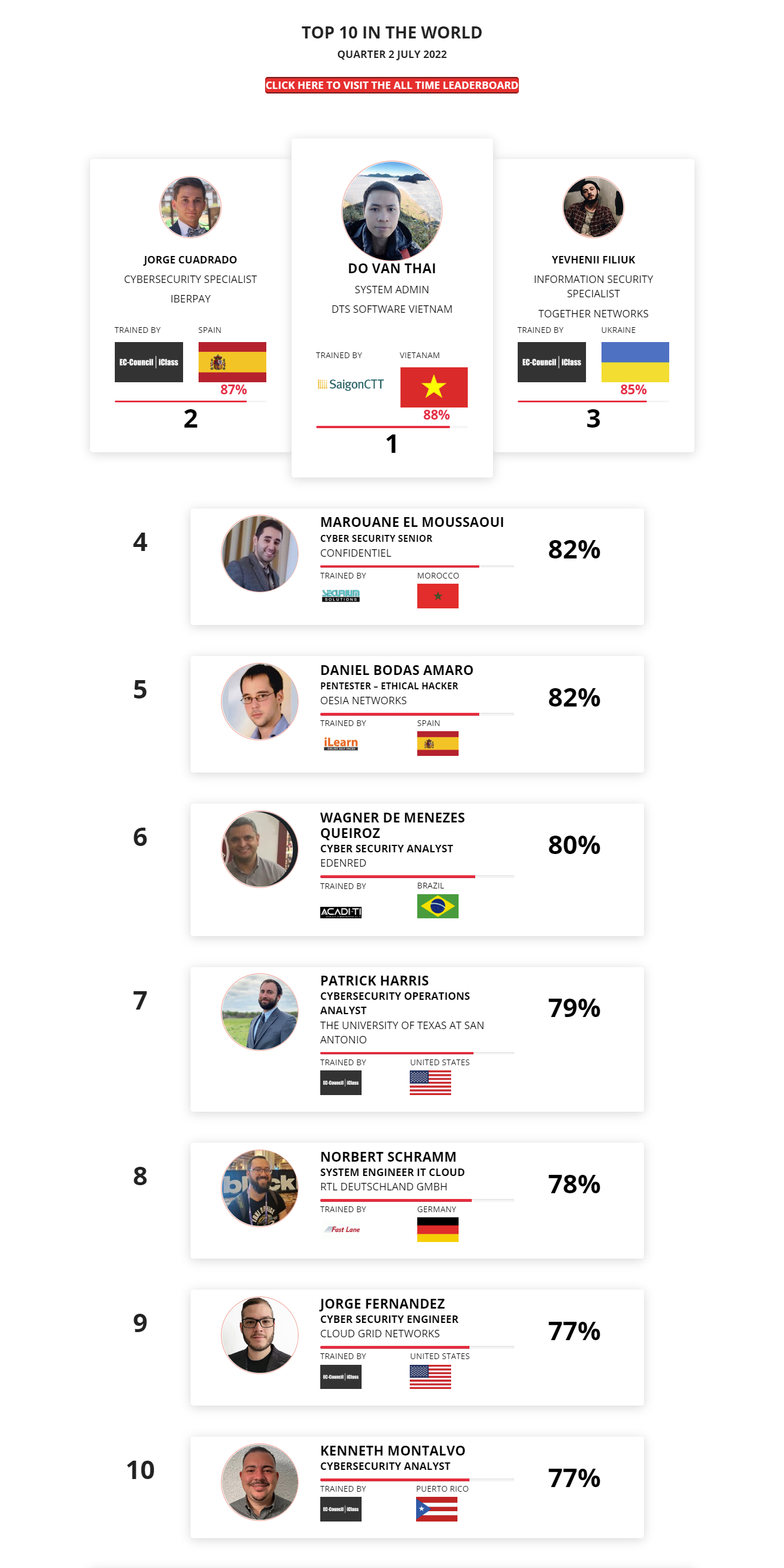
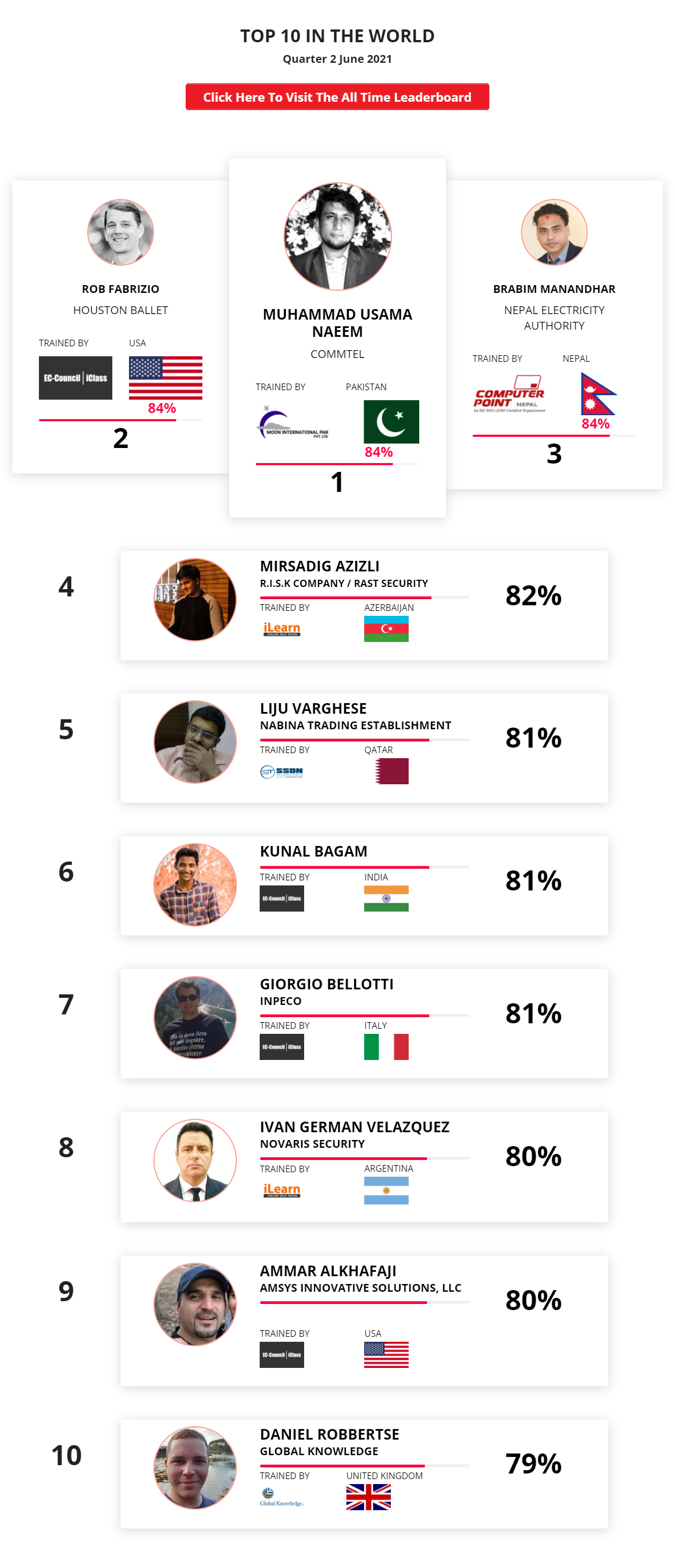
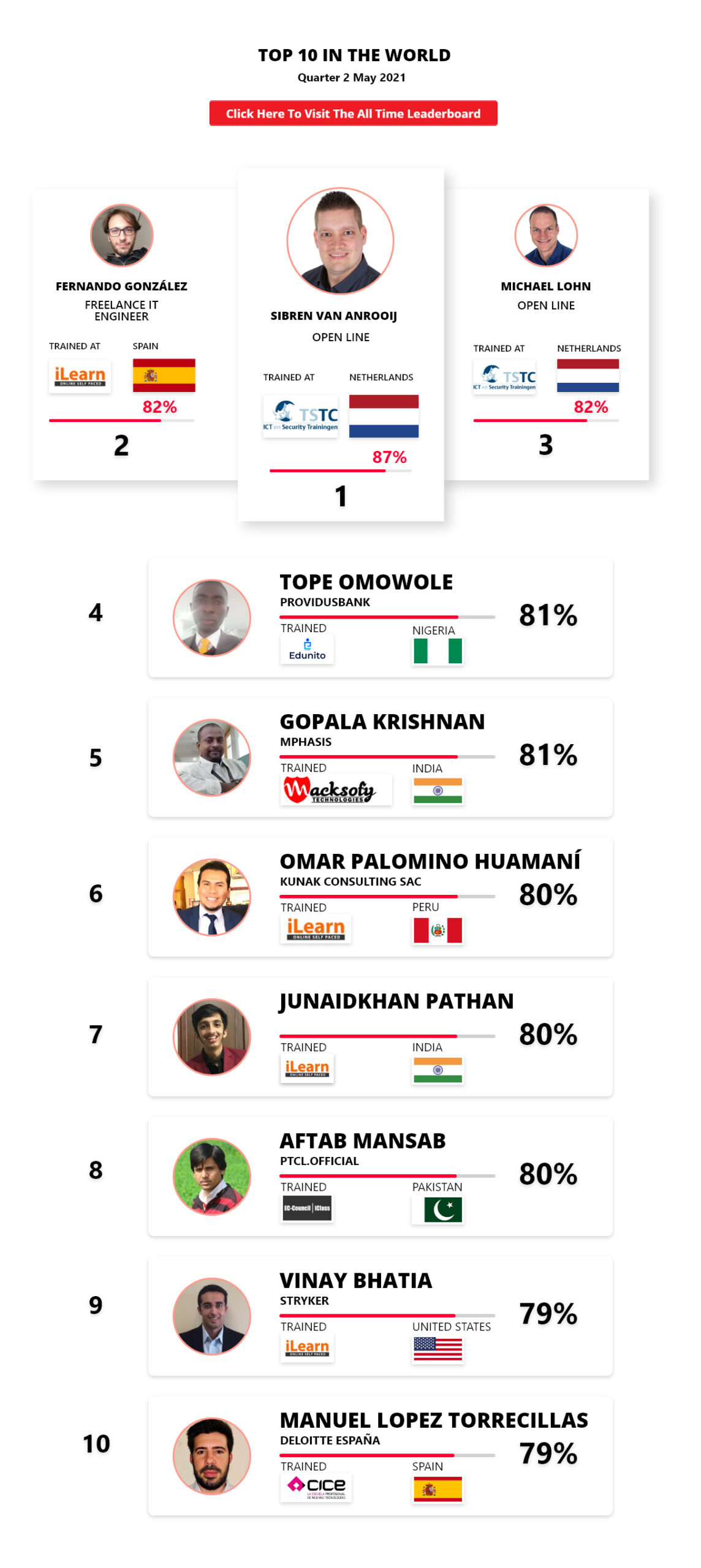
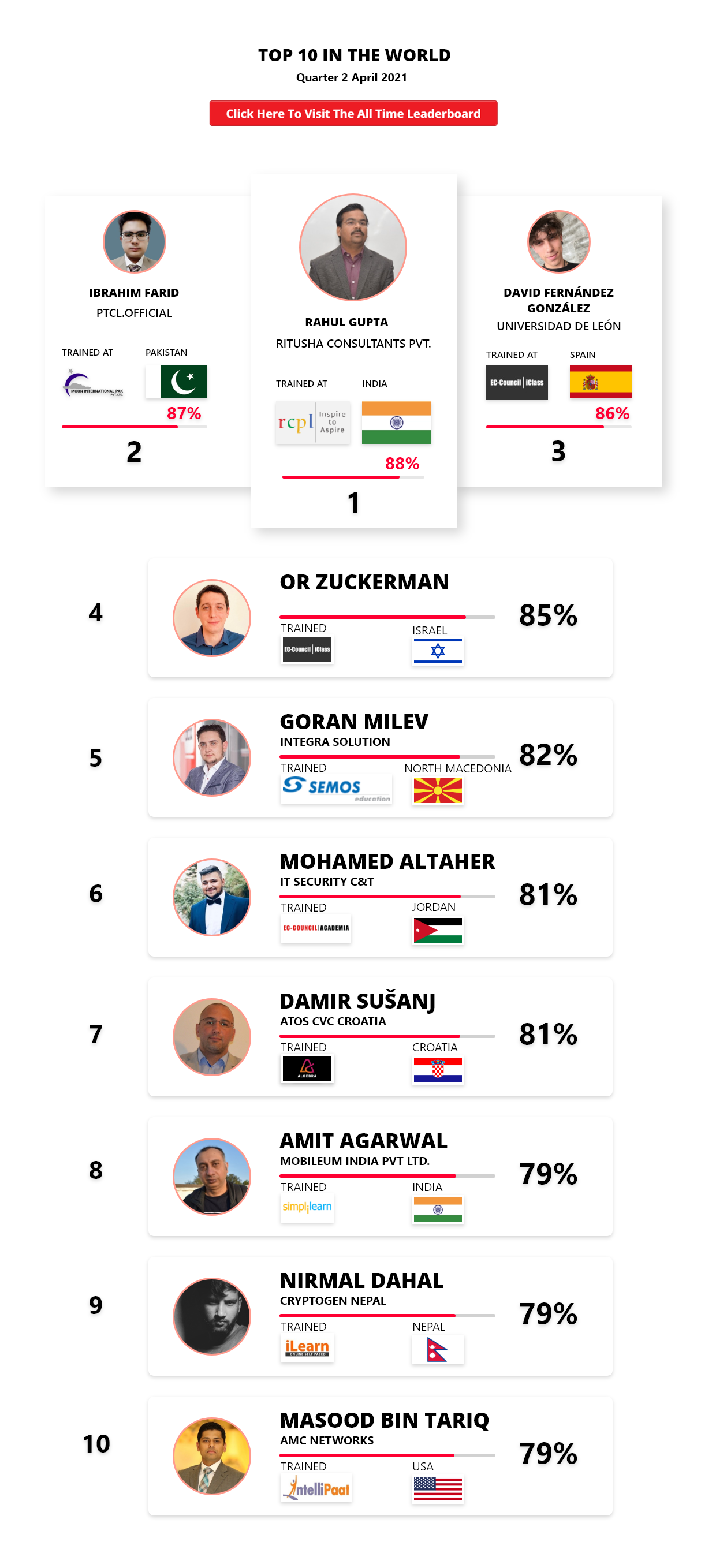
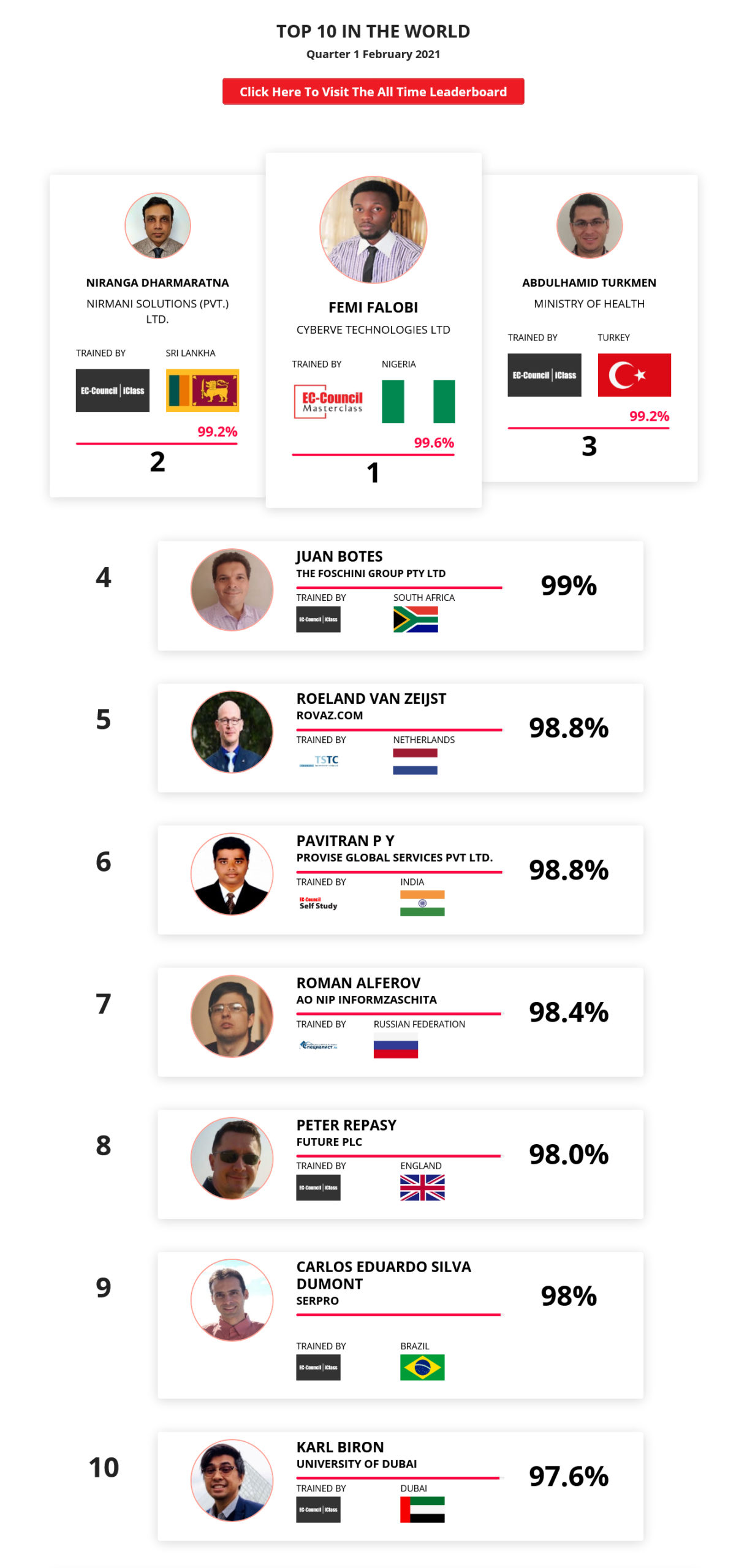
1

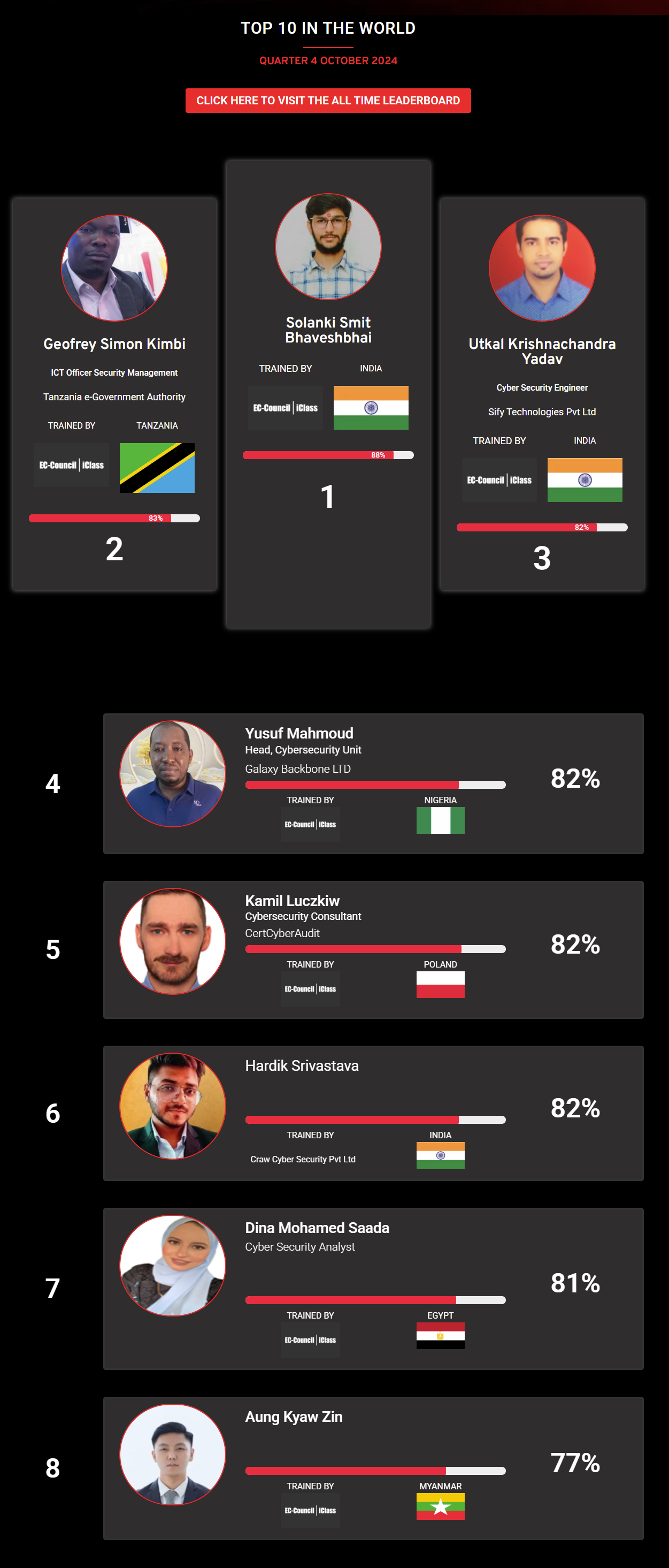
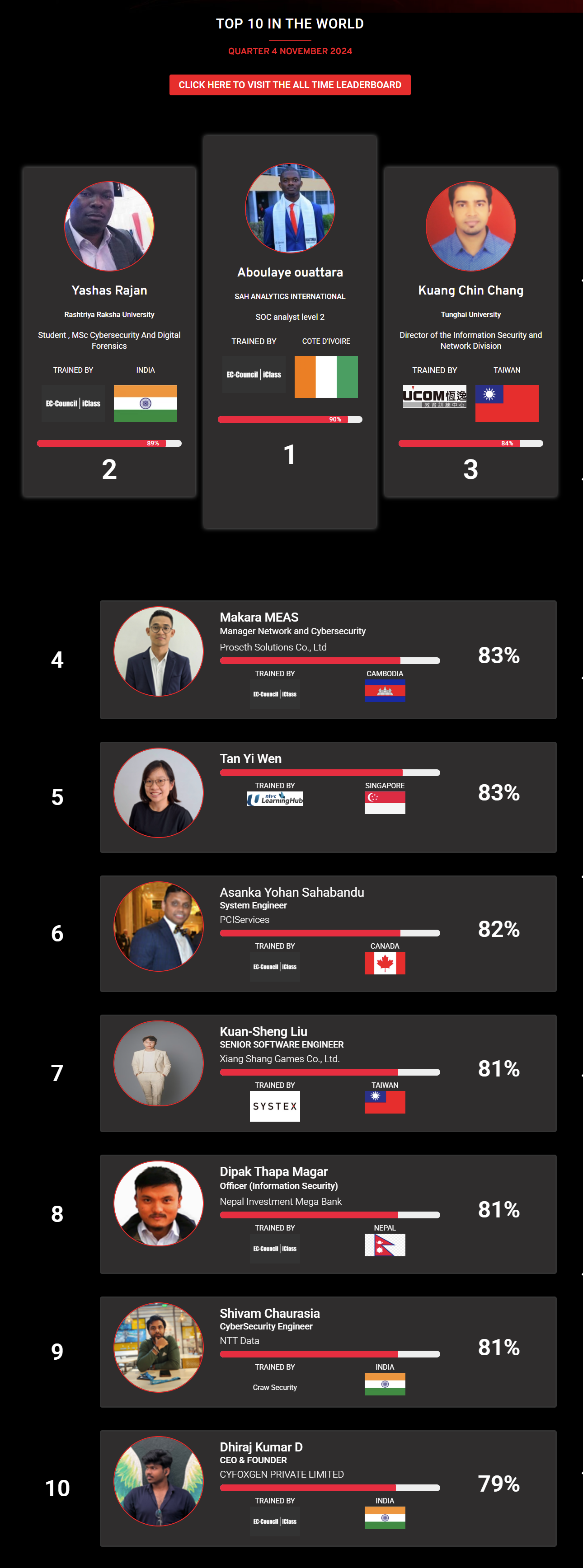
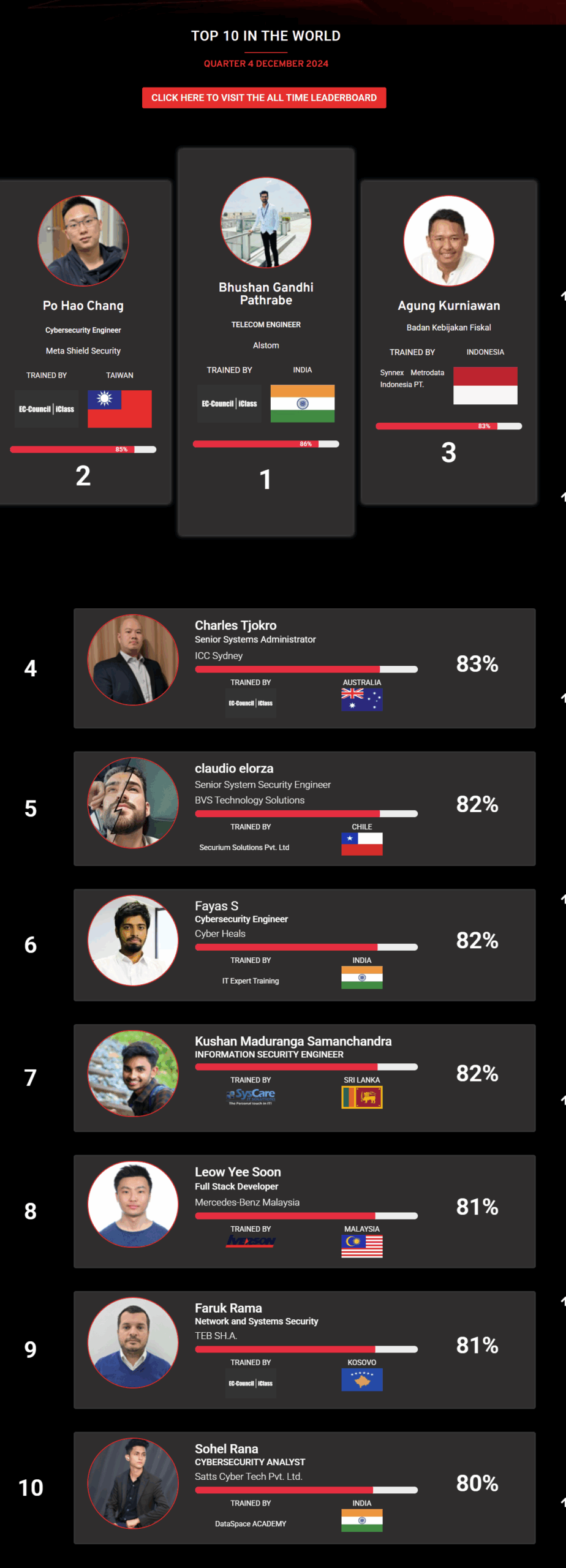
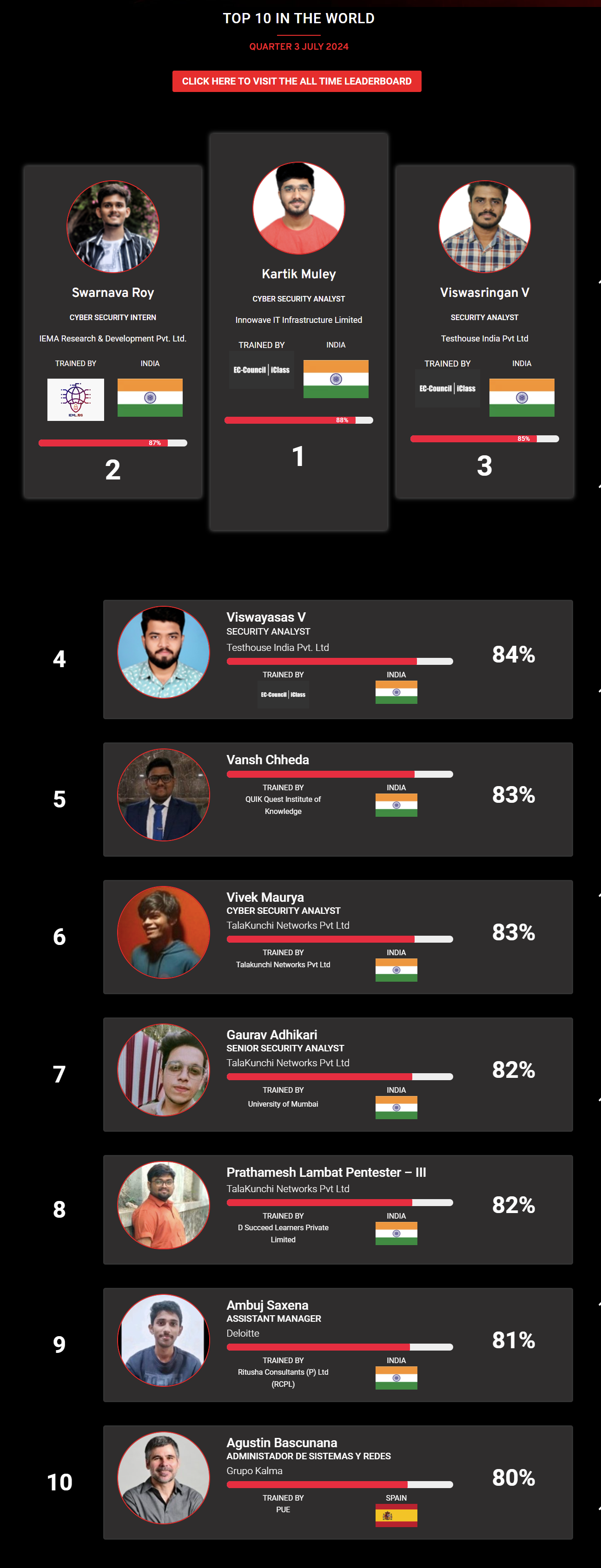
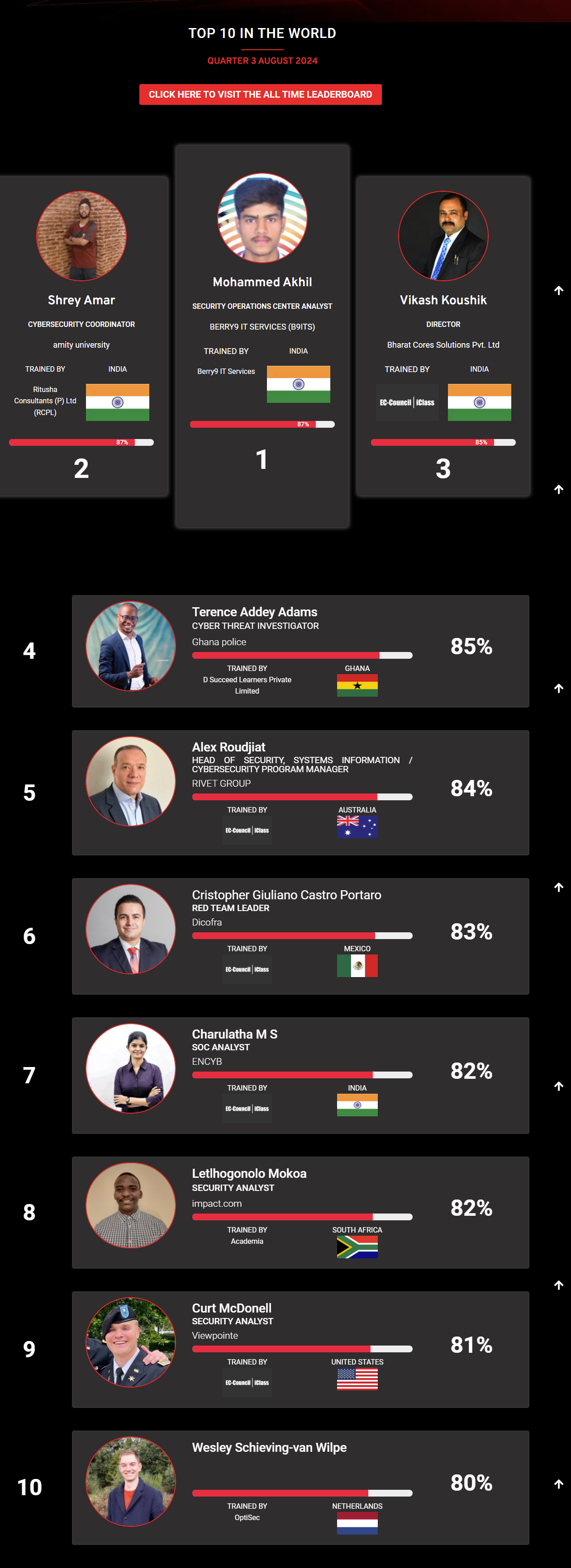
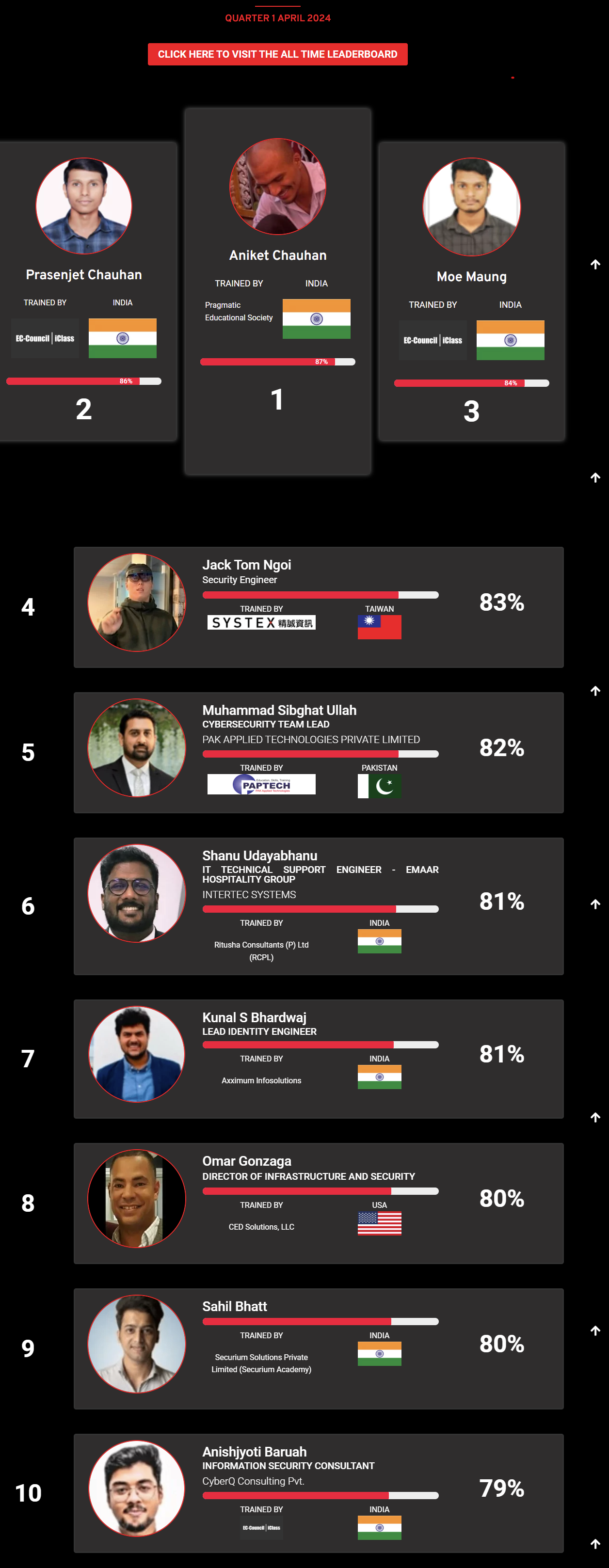
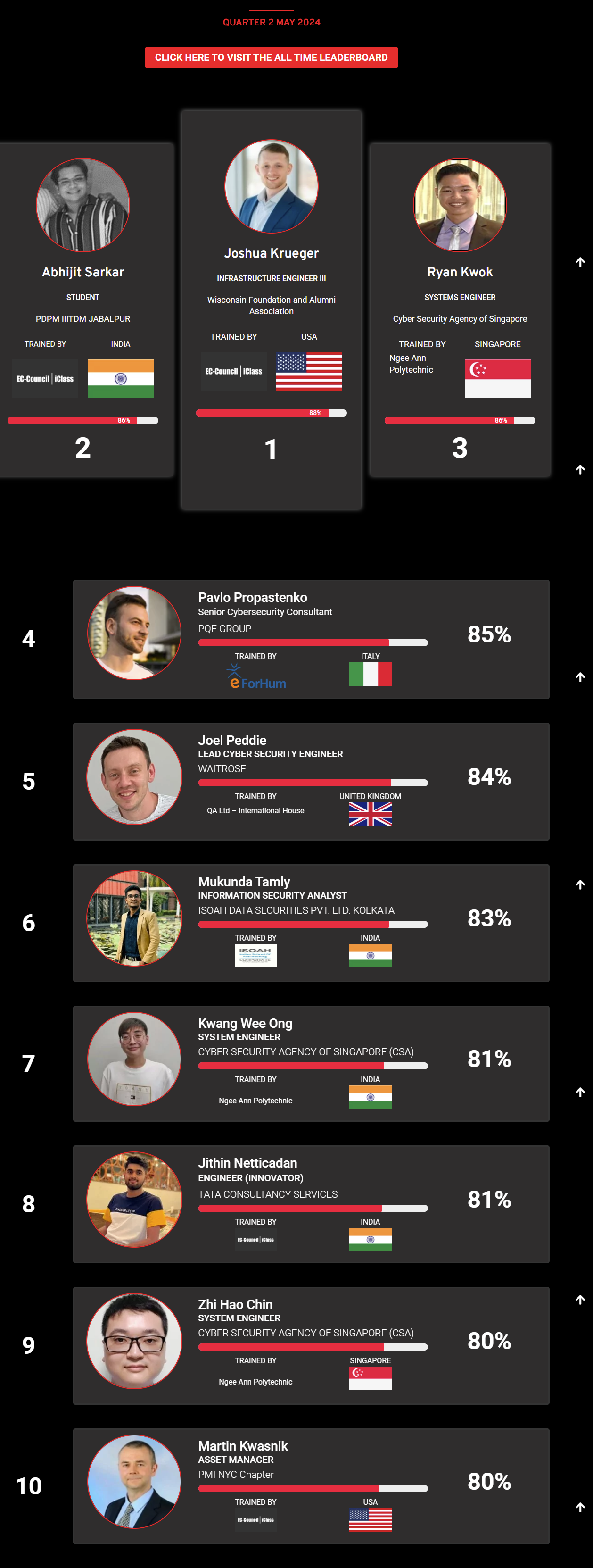
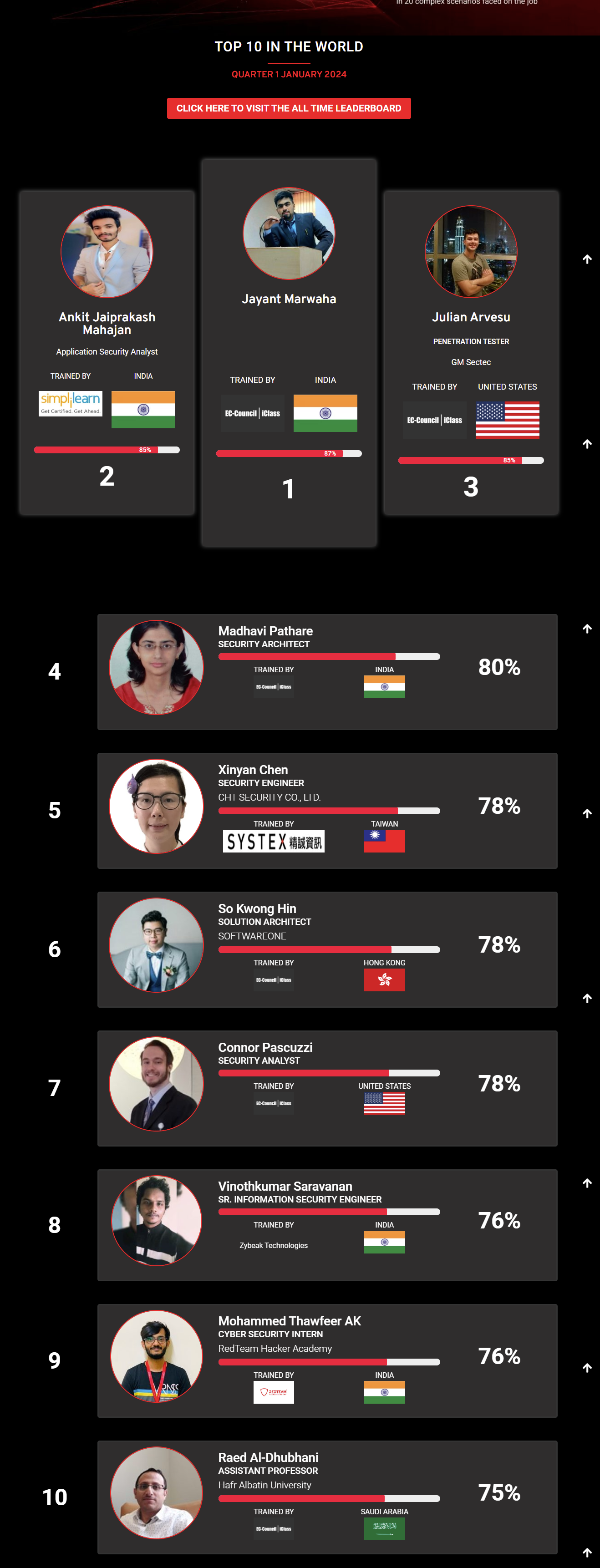
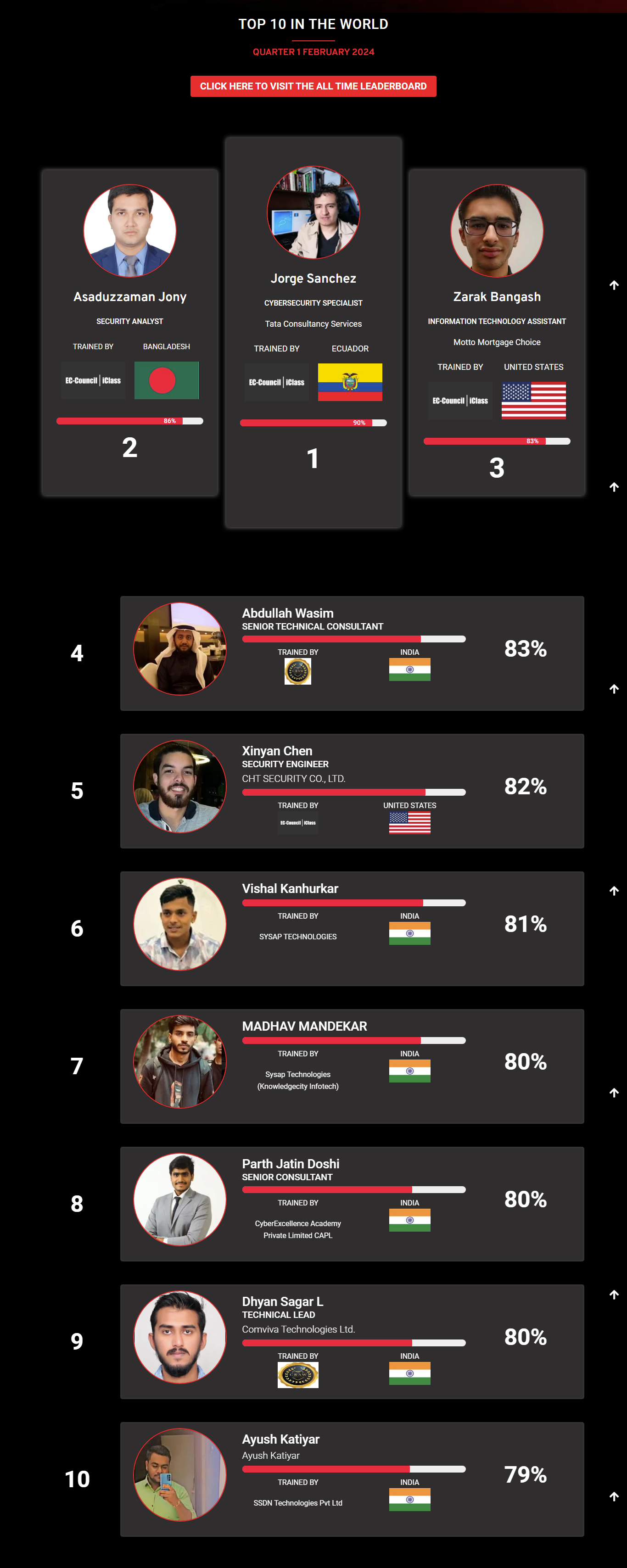
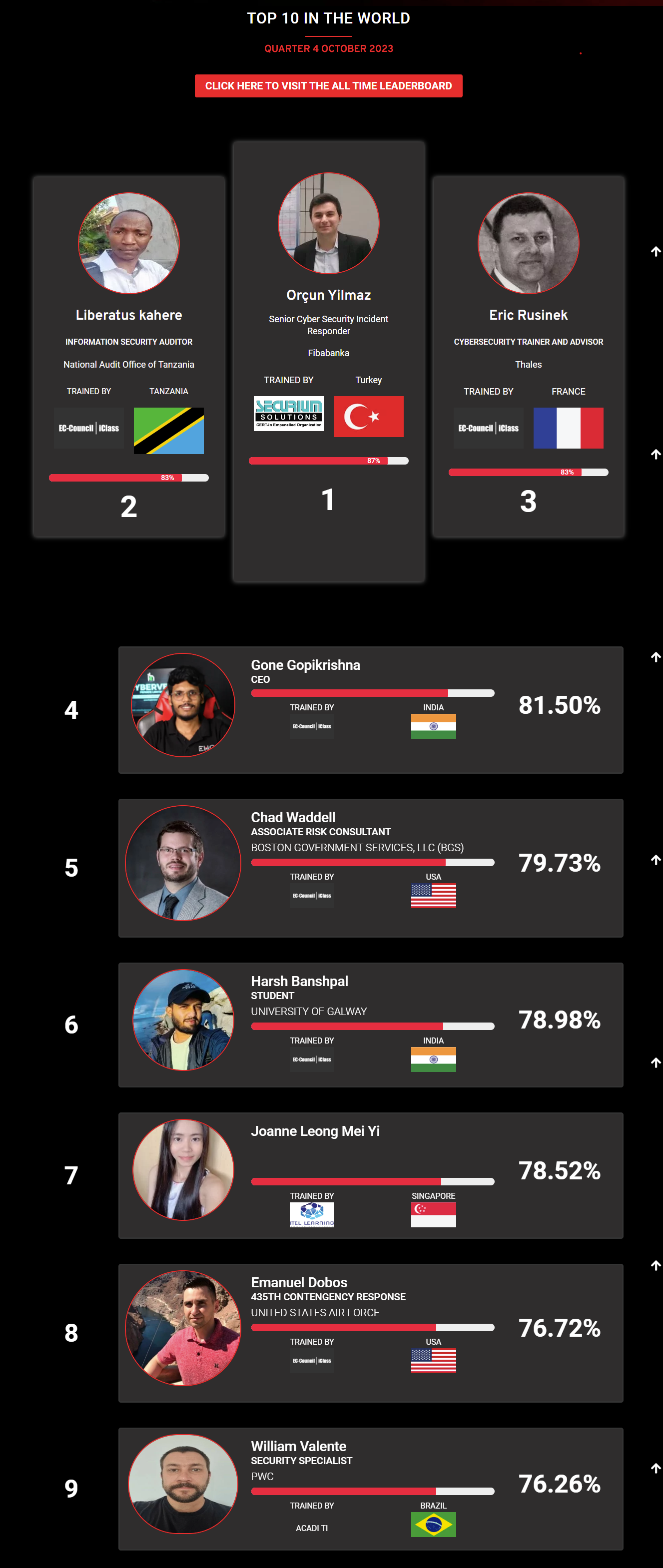
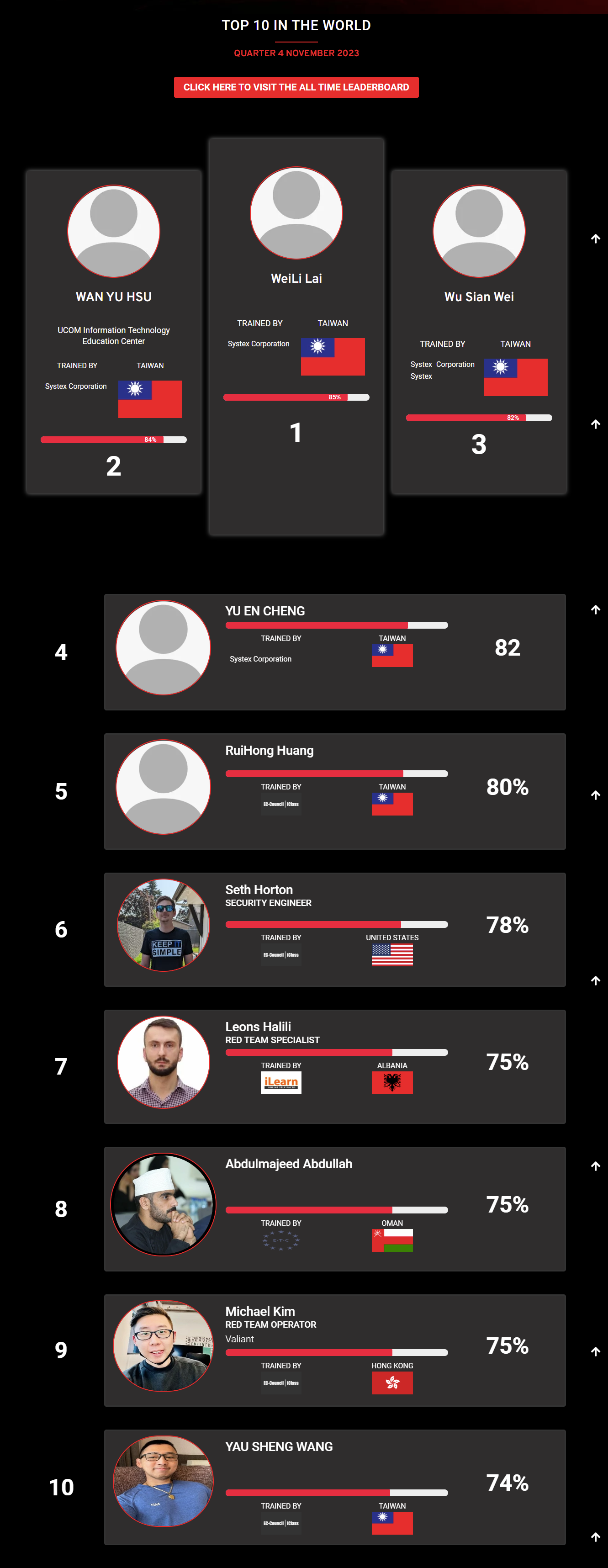
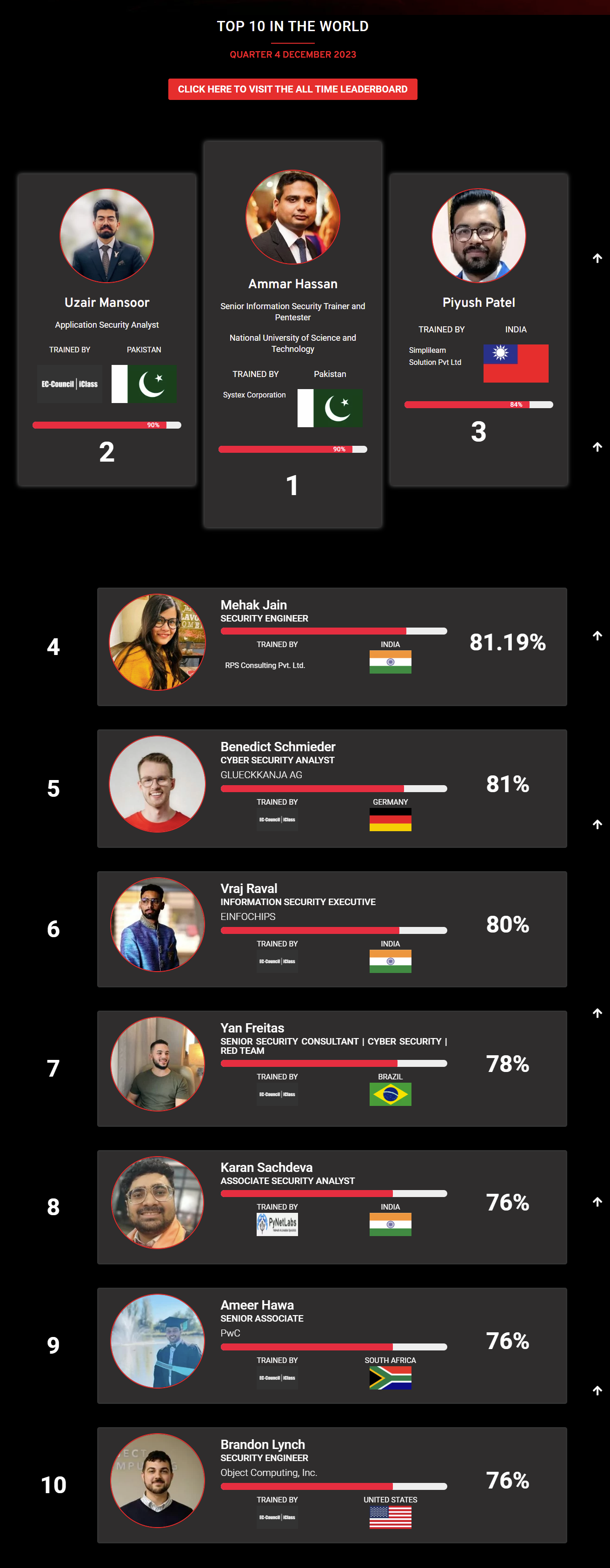
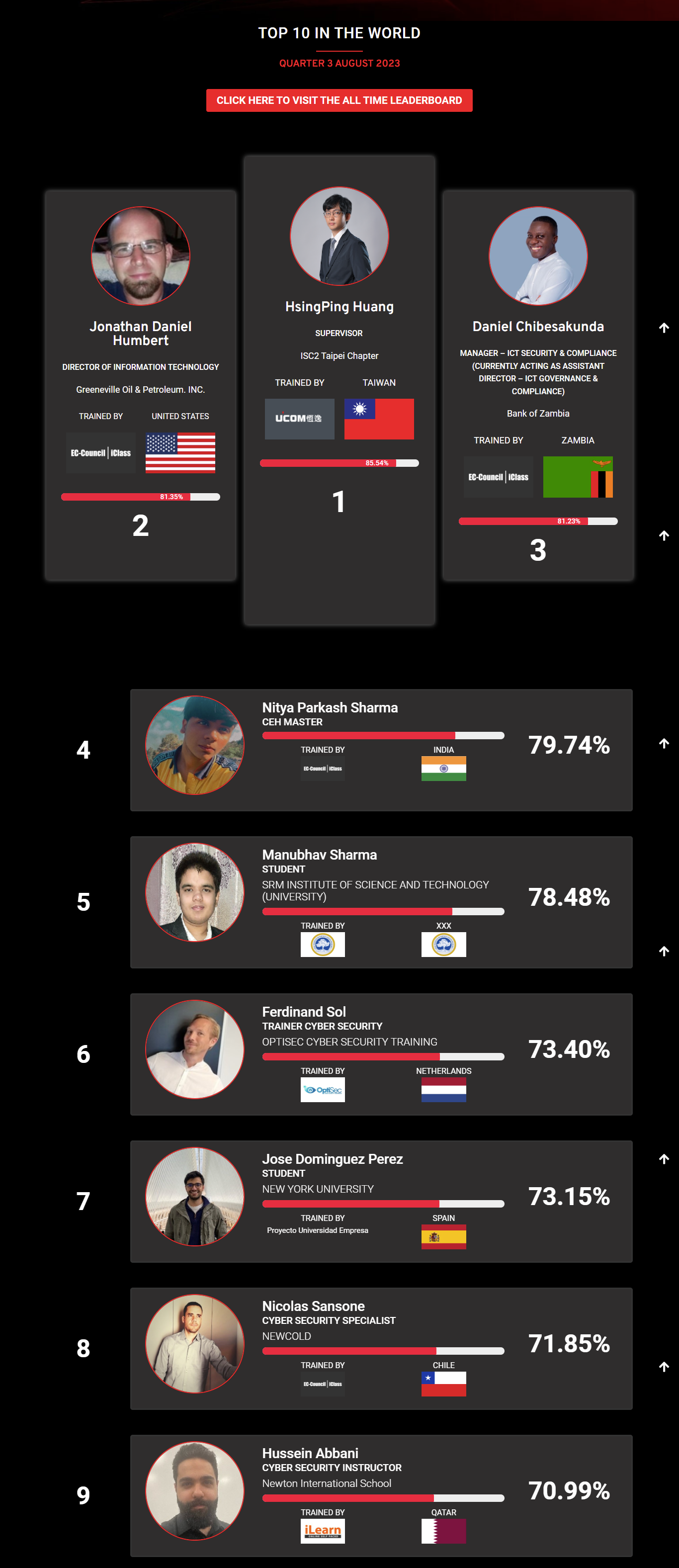
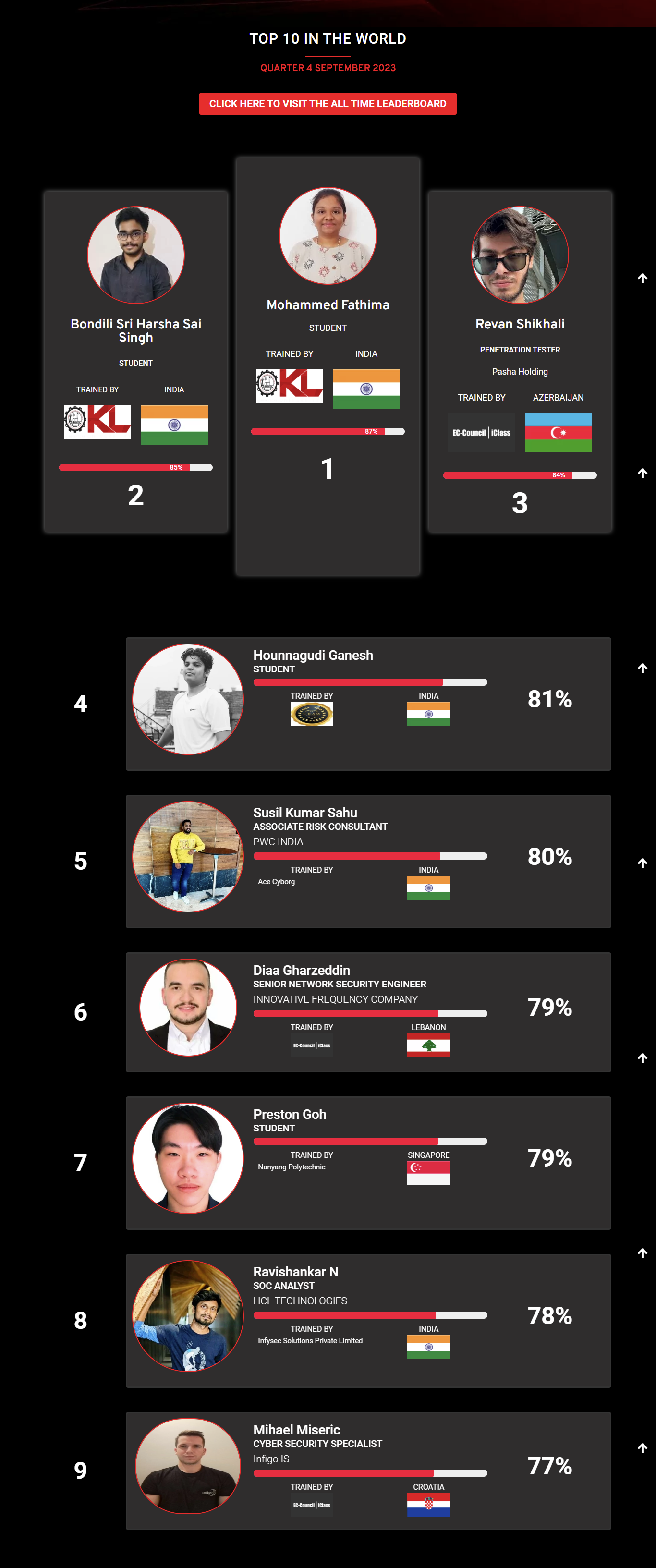
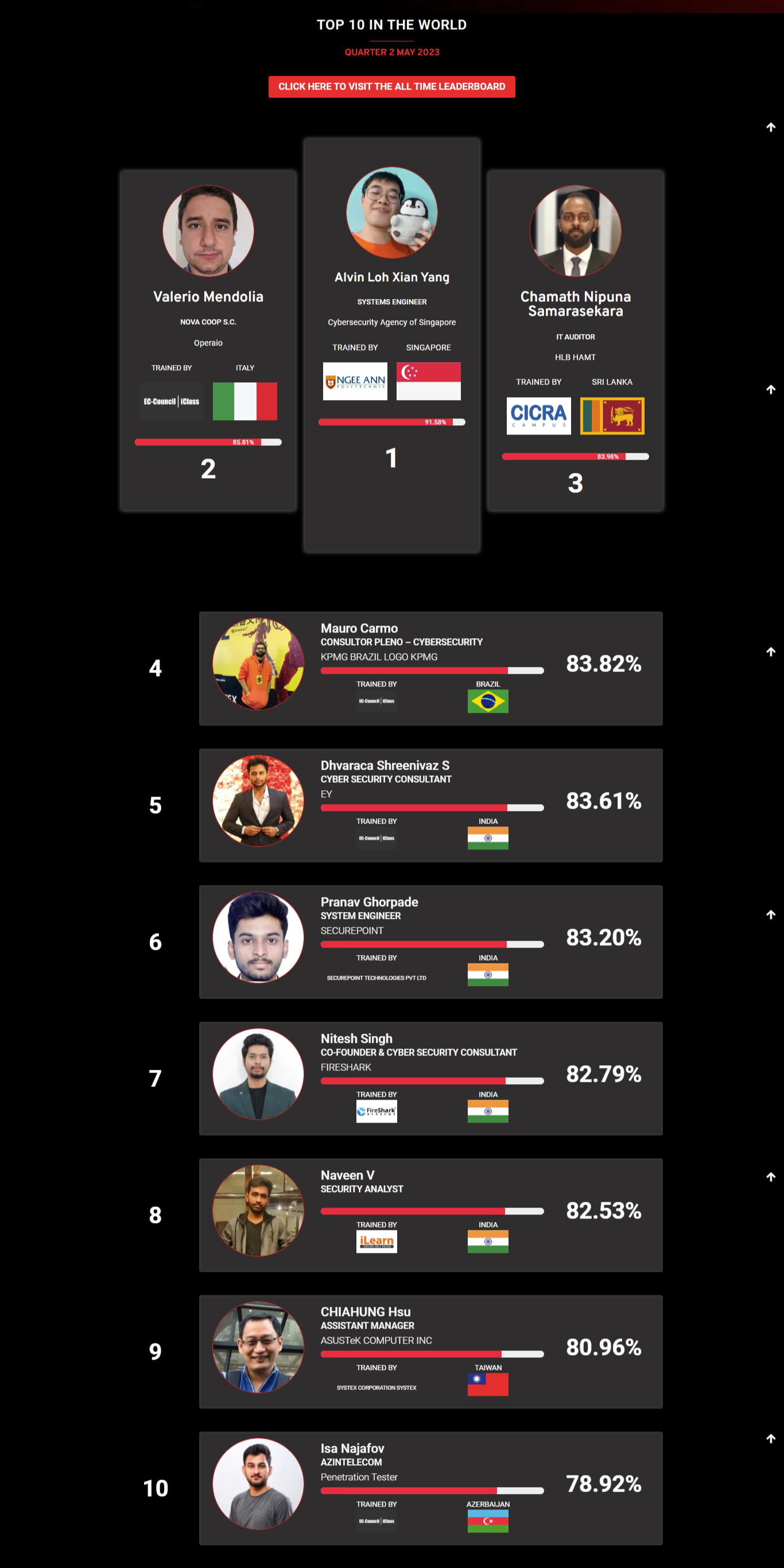
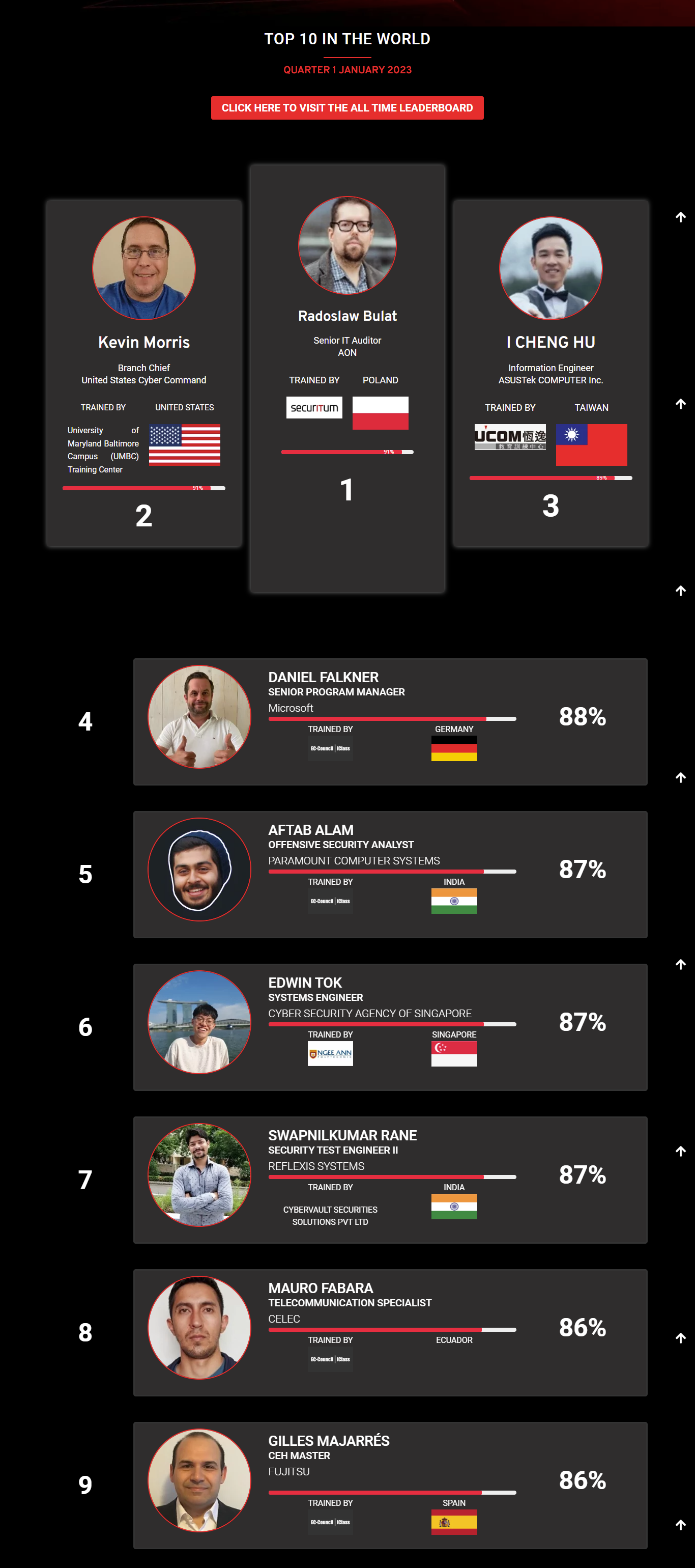
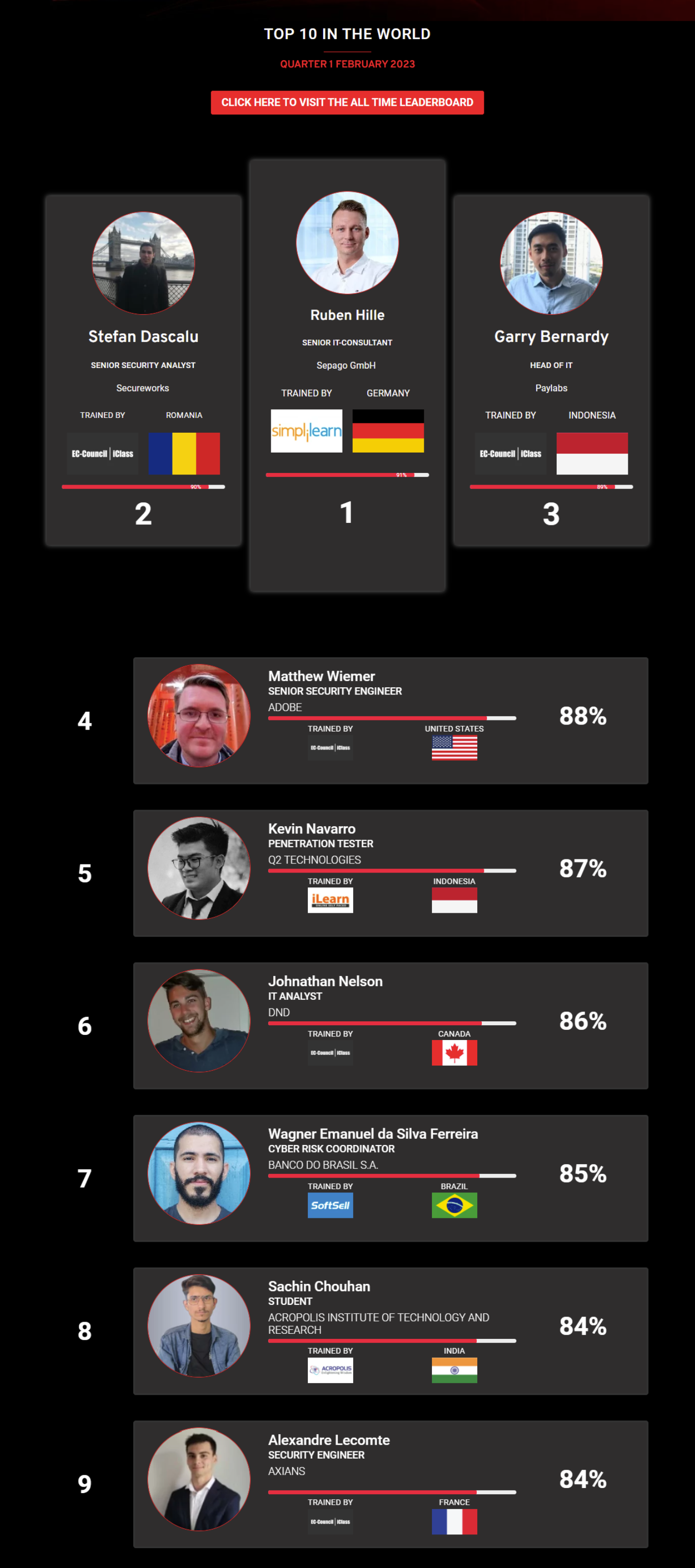
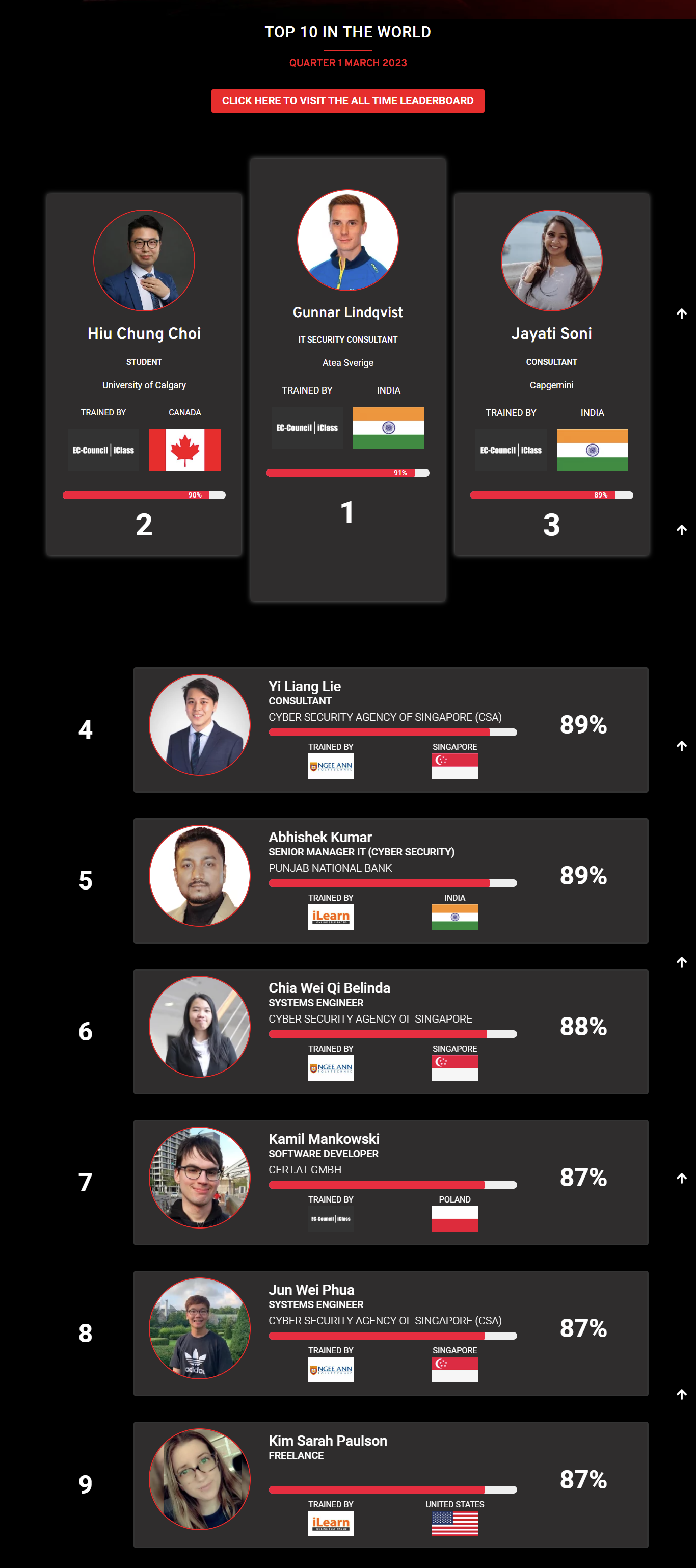
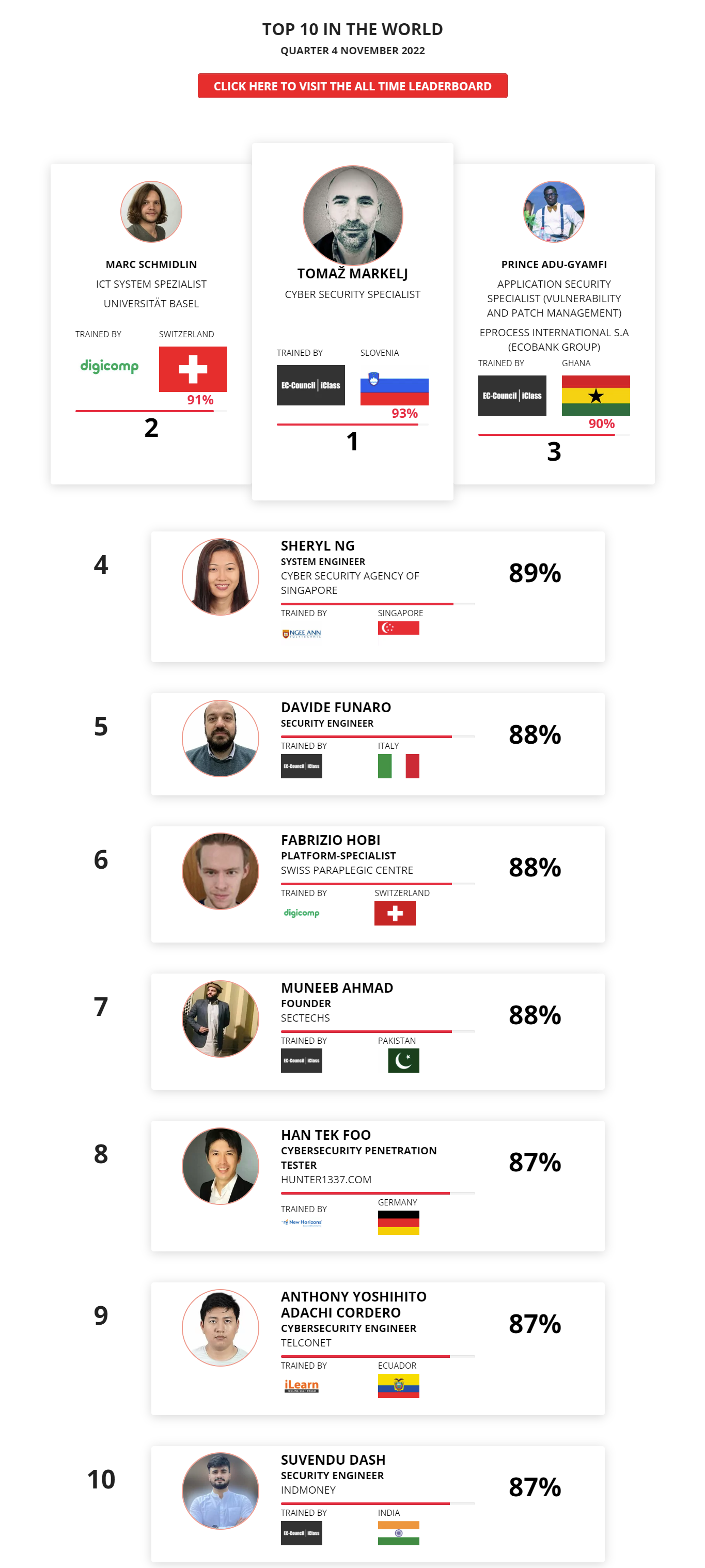
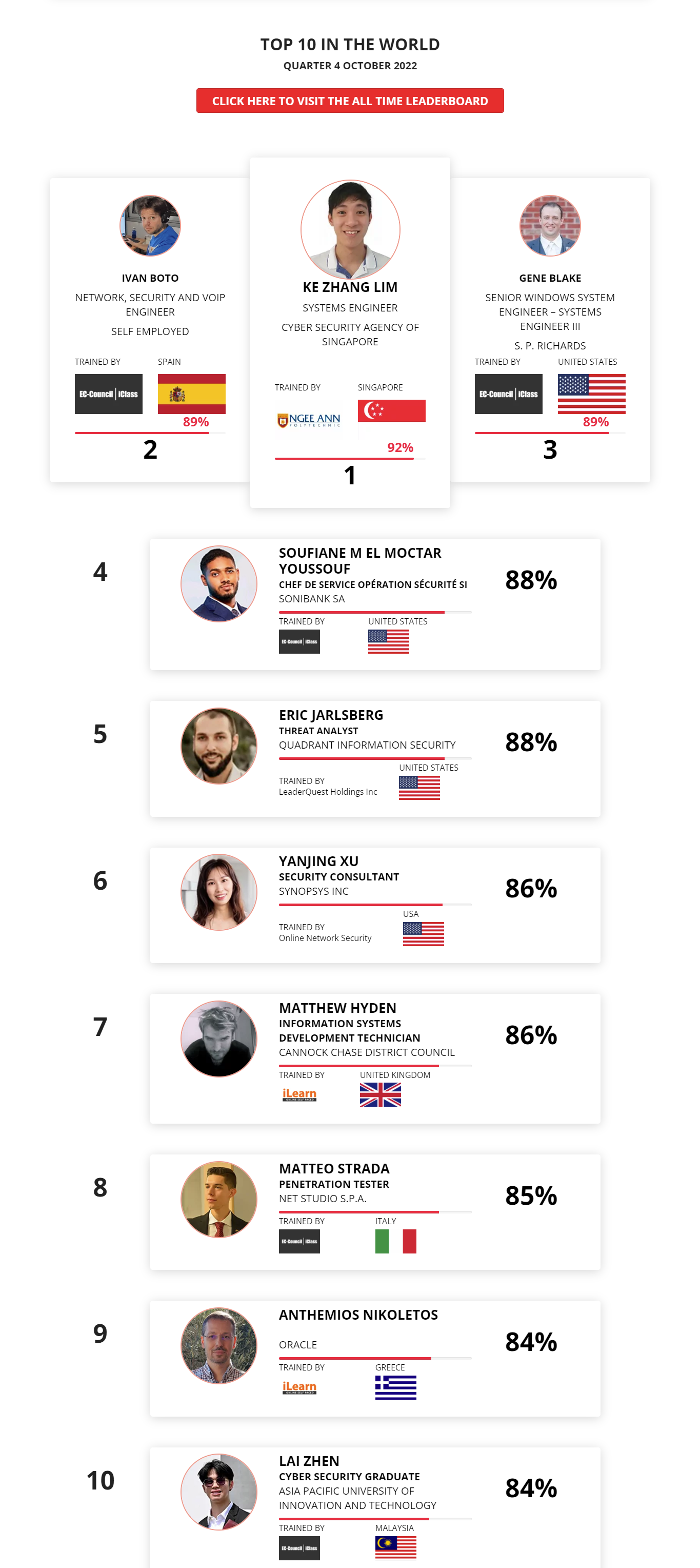
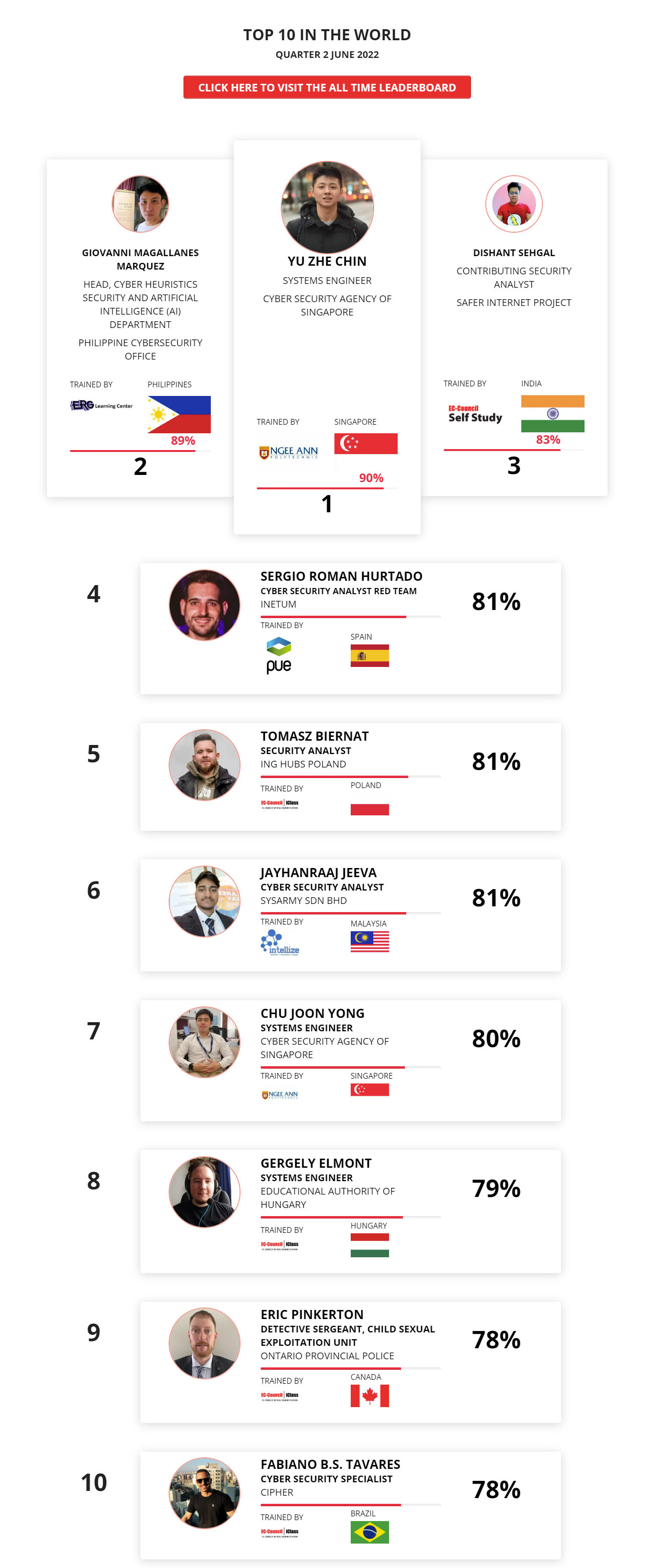
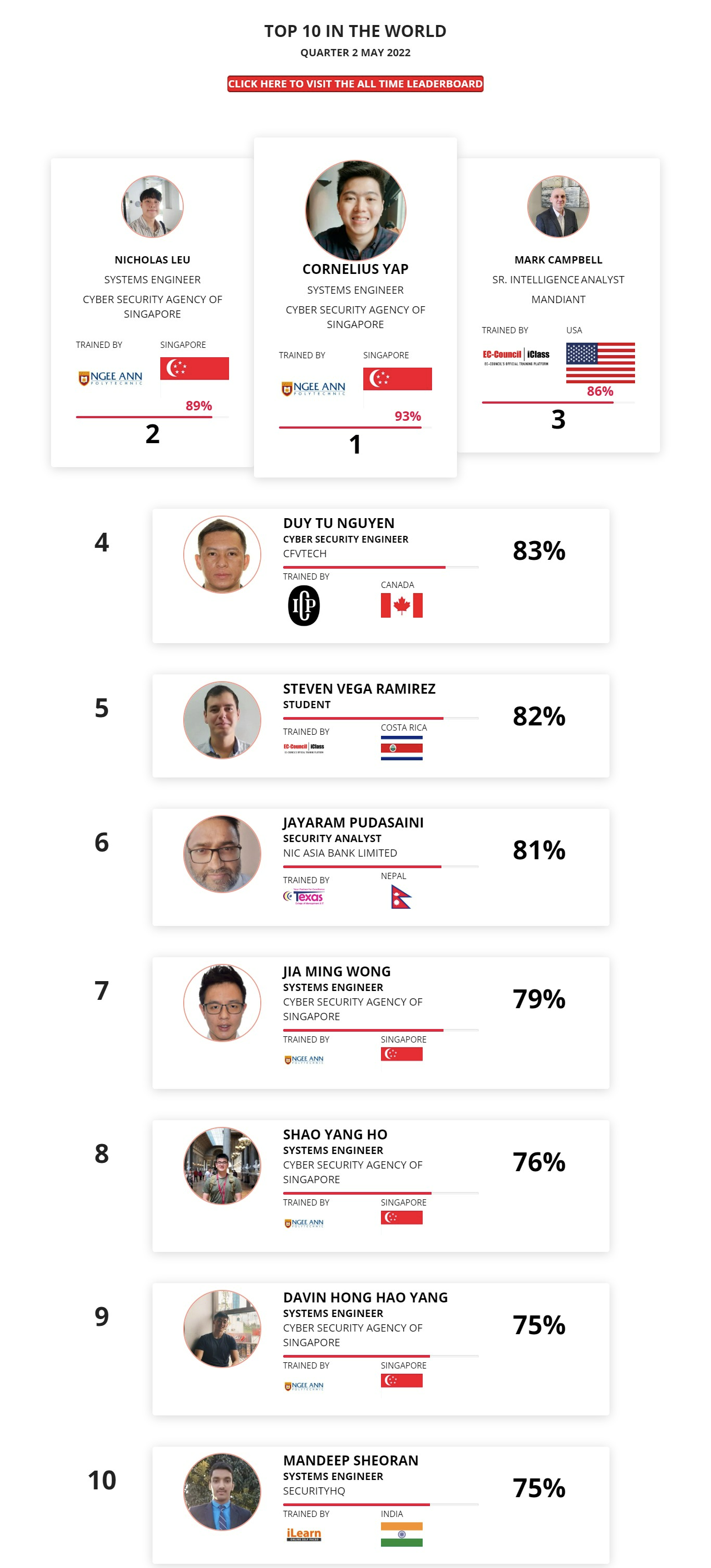
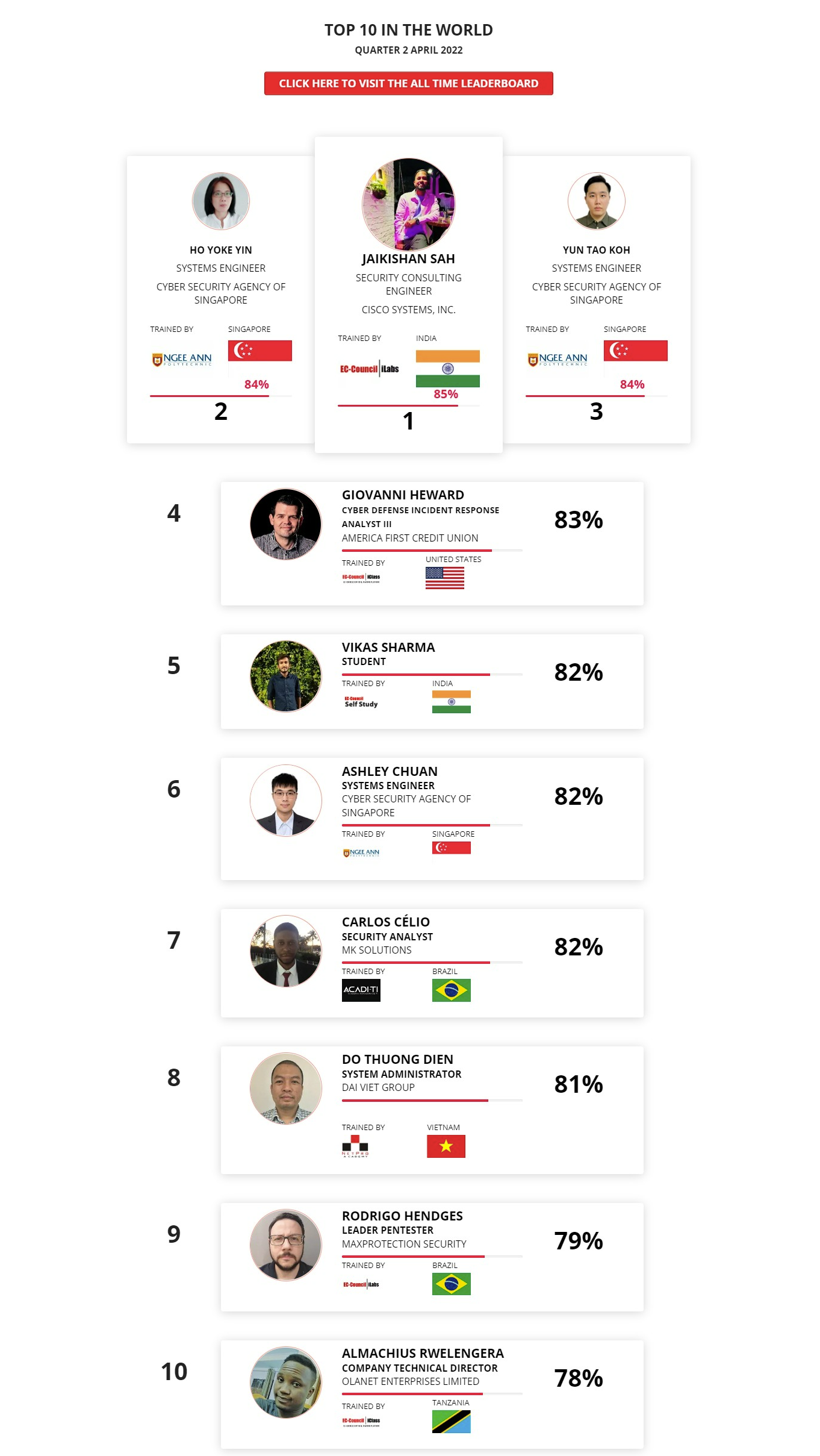
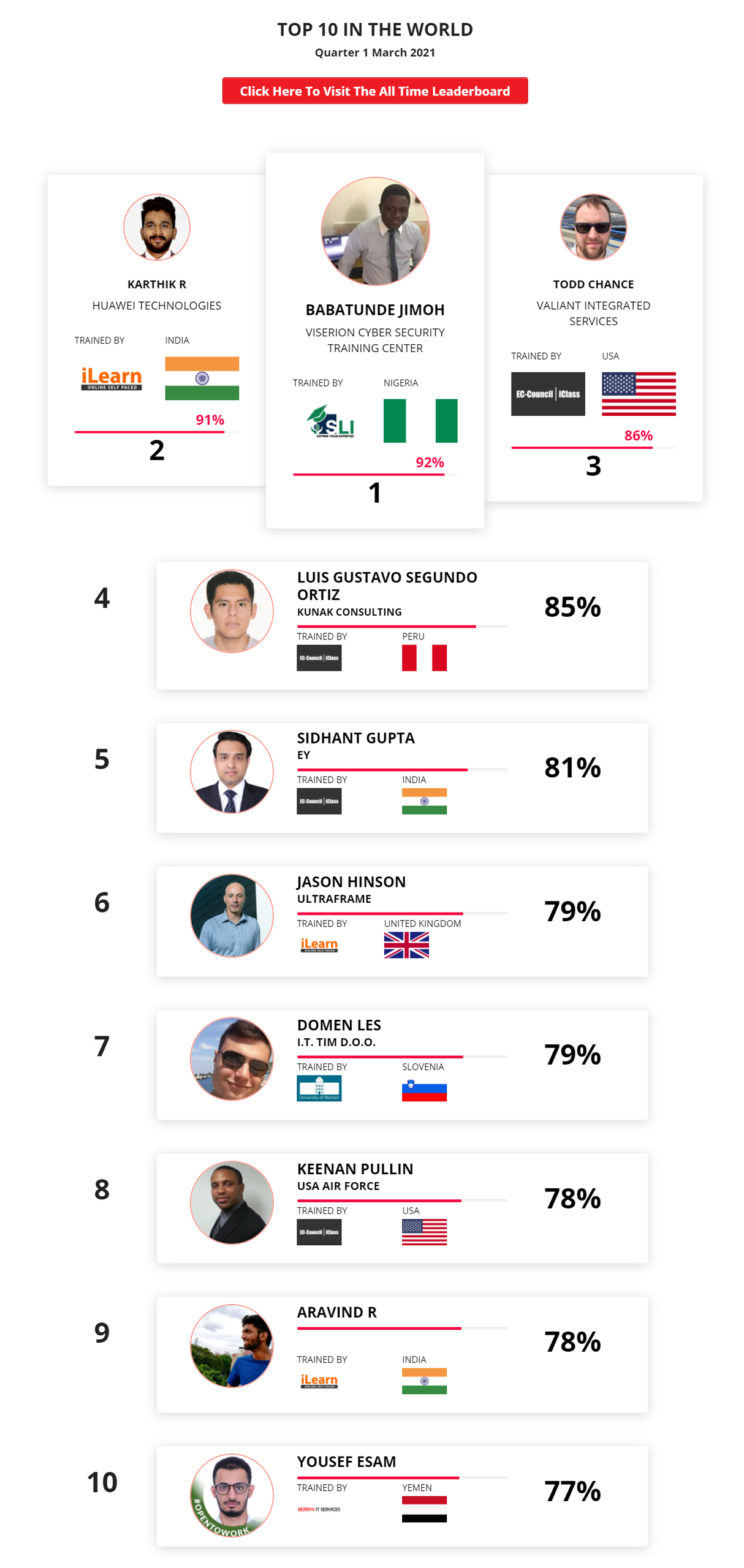
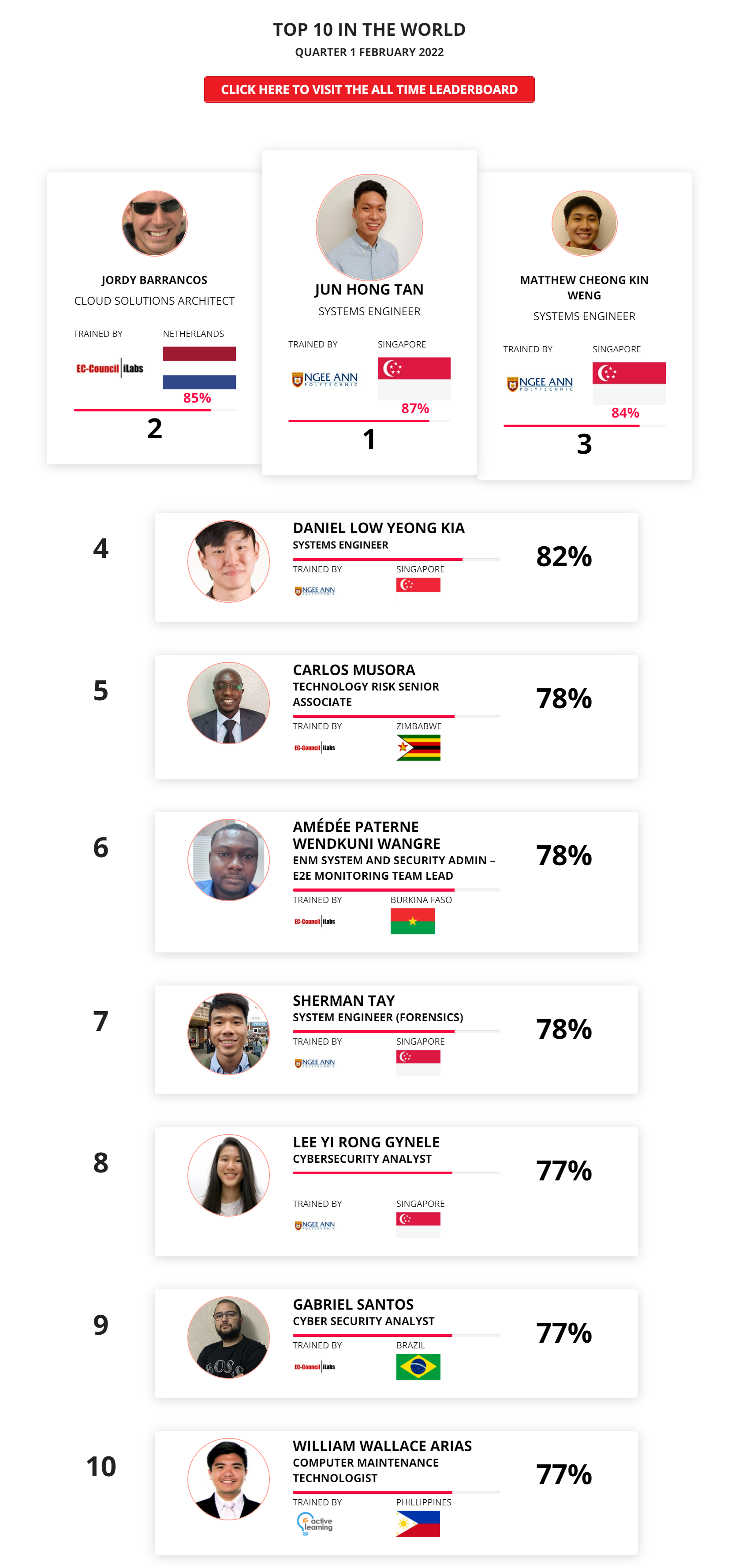
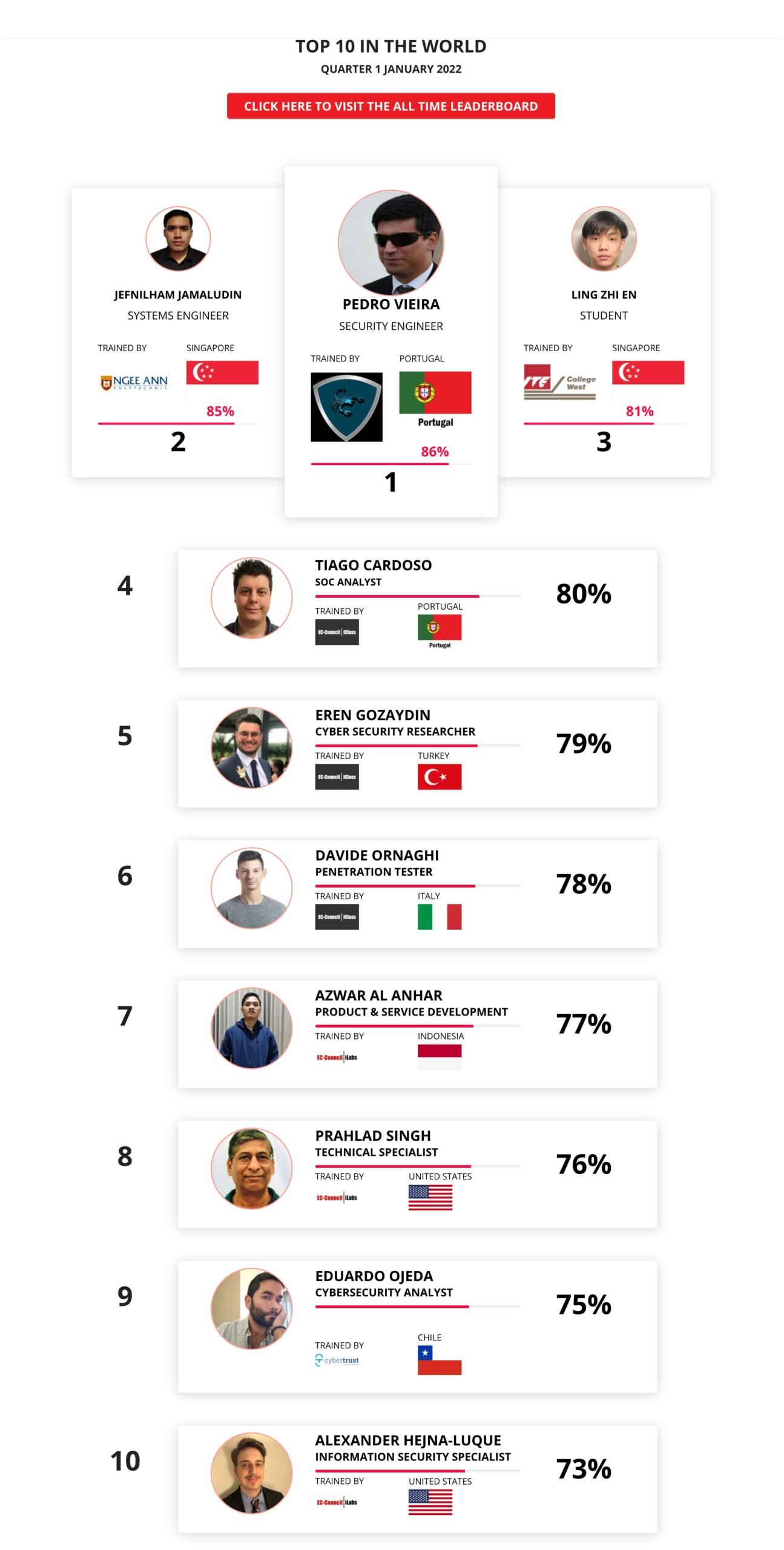
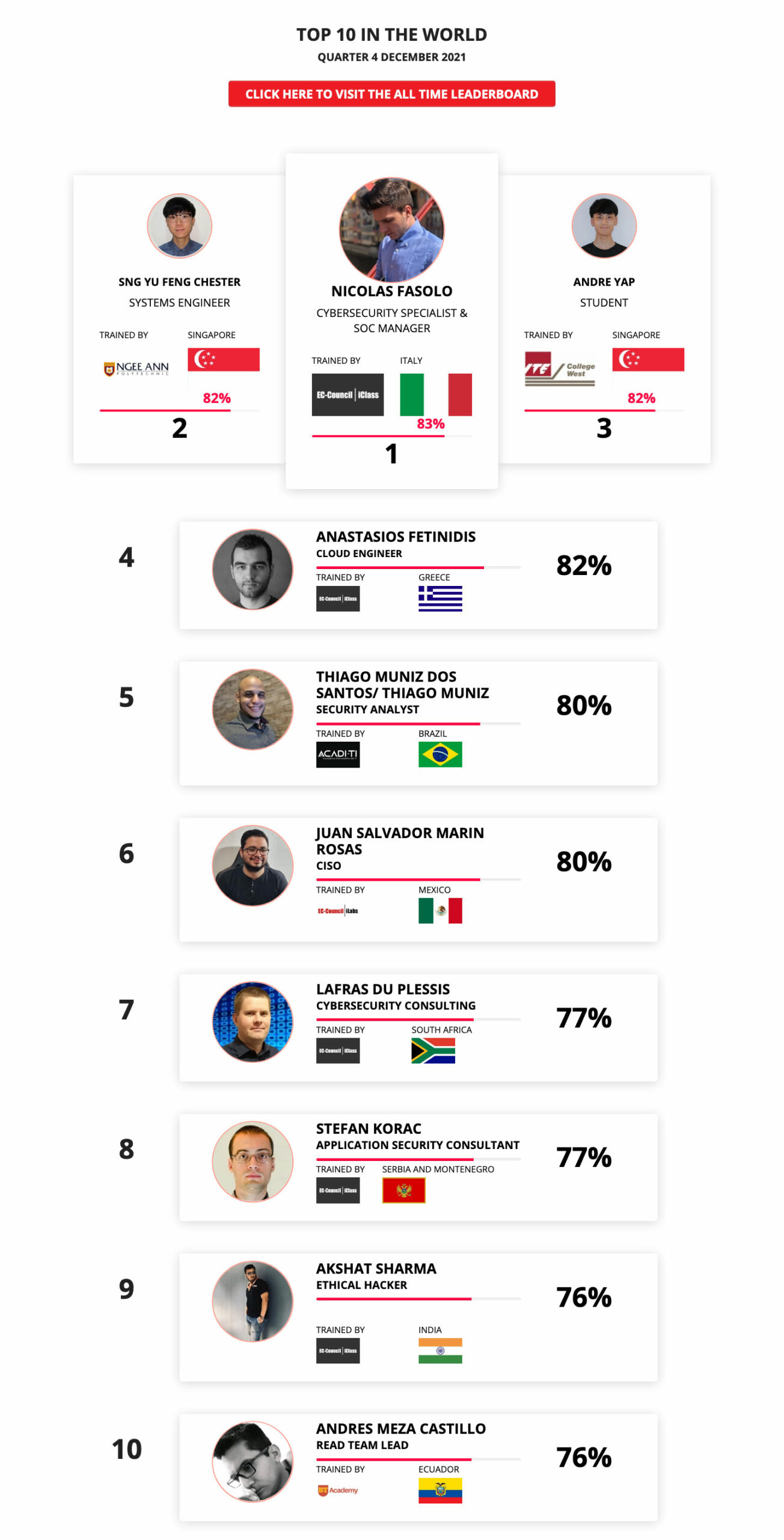
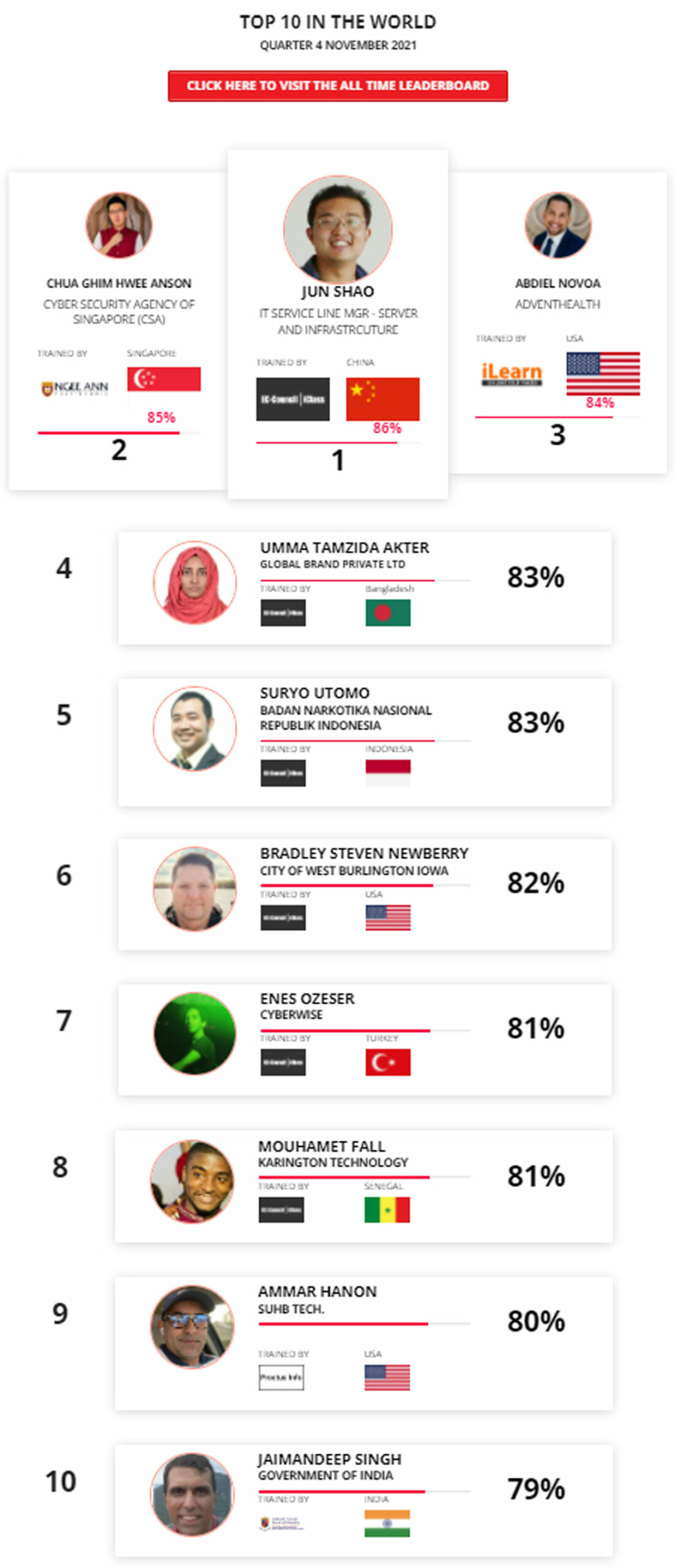
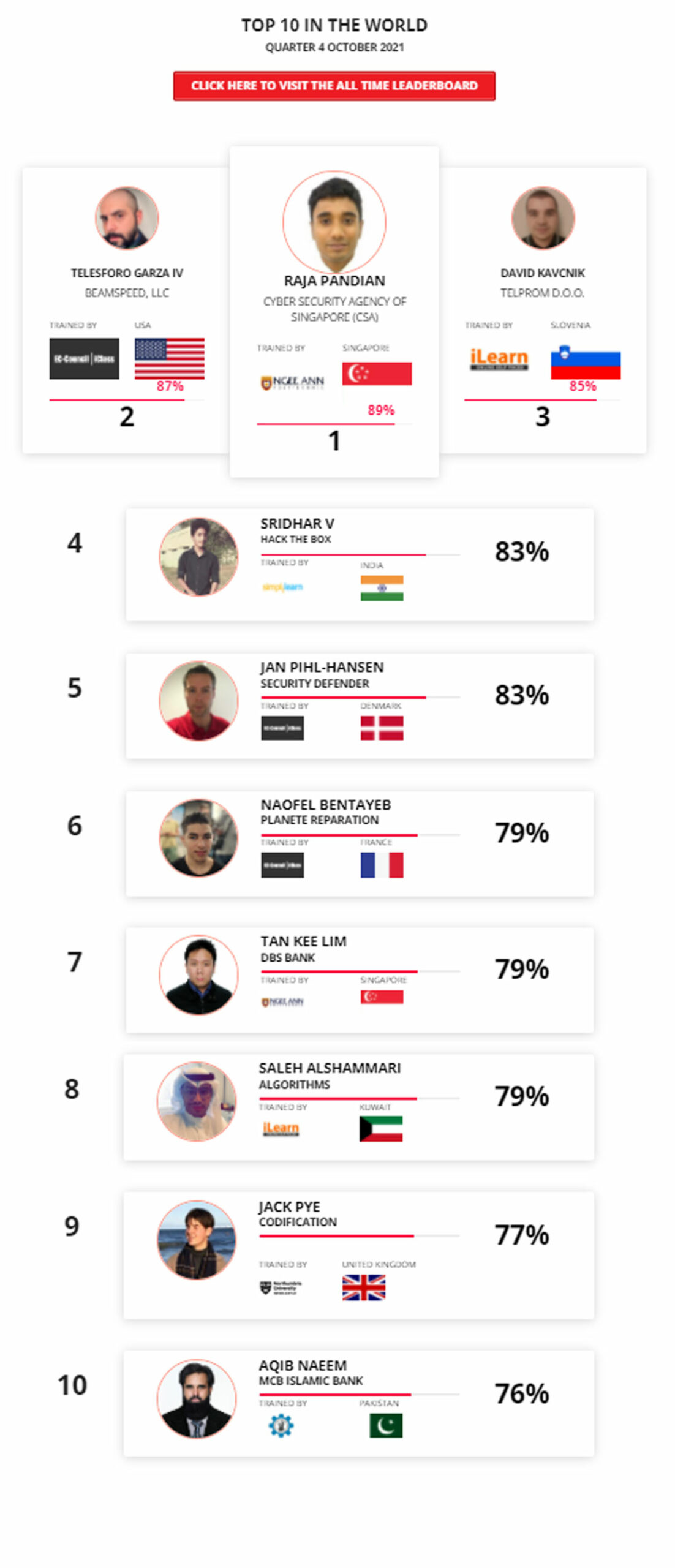
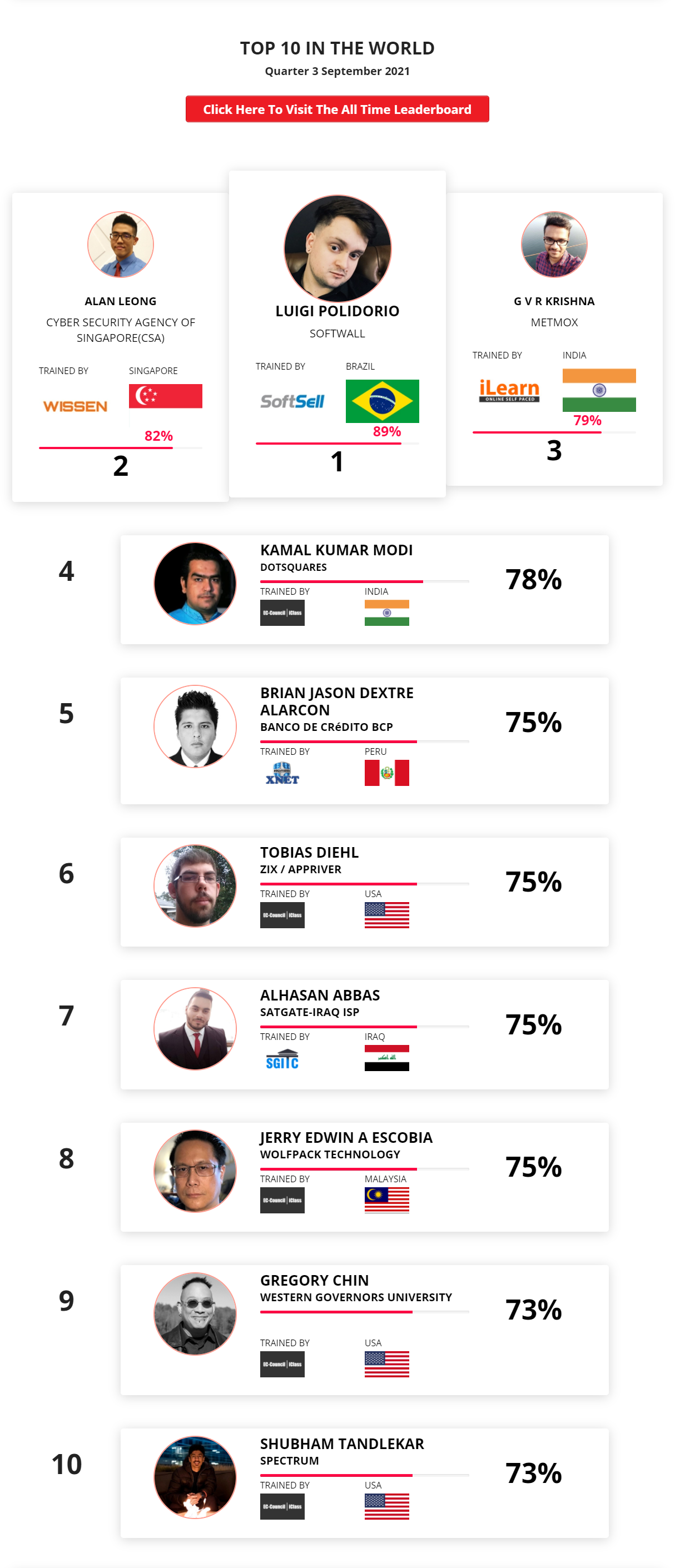
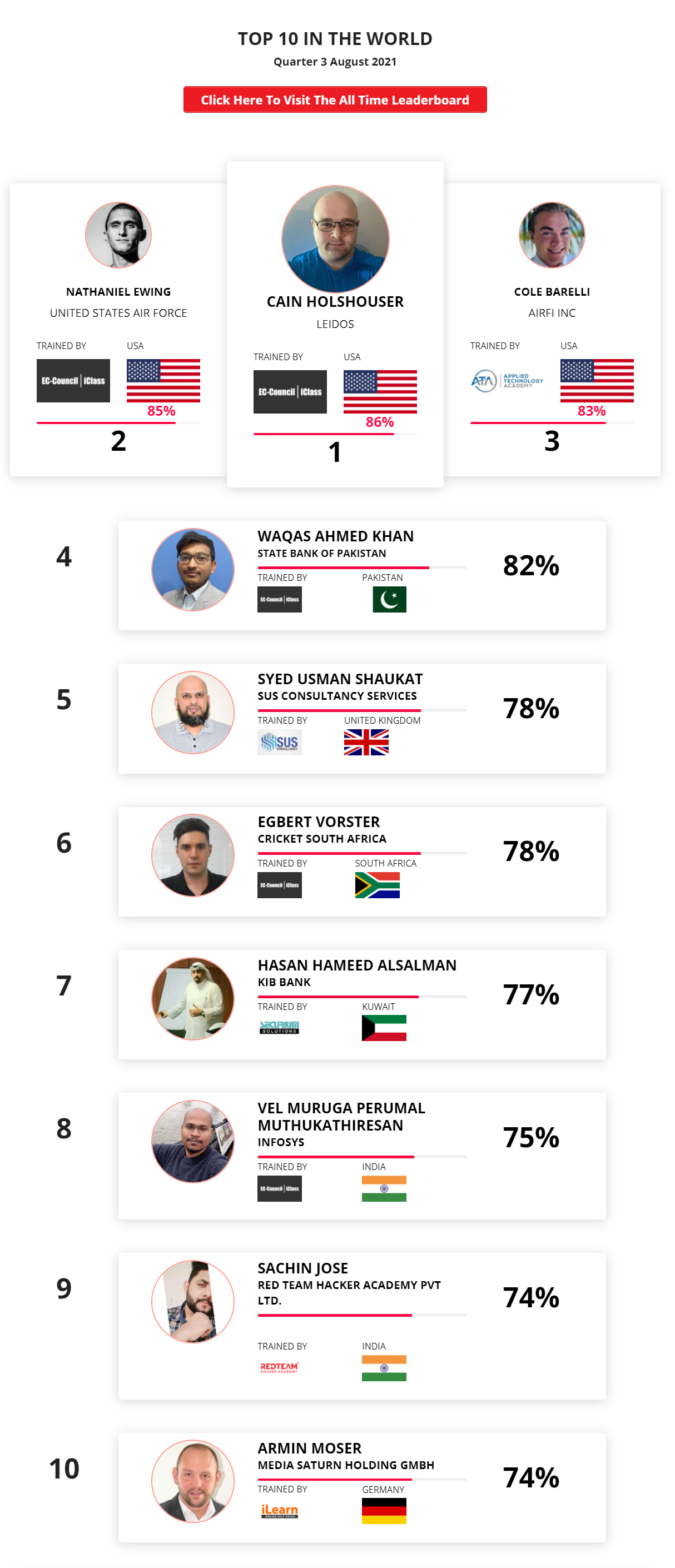
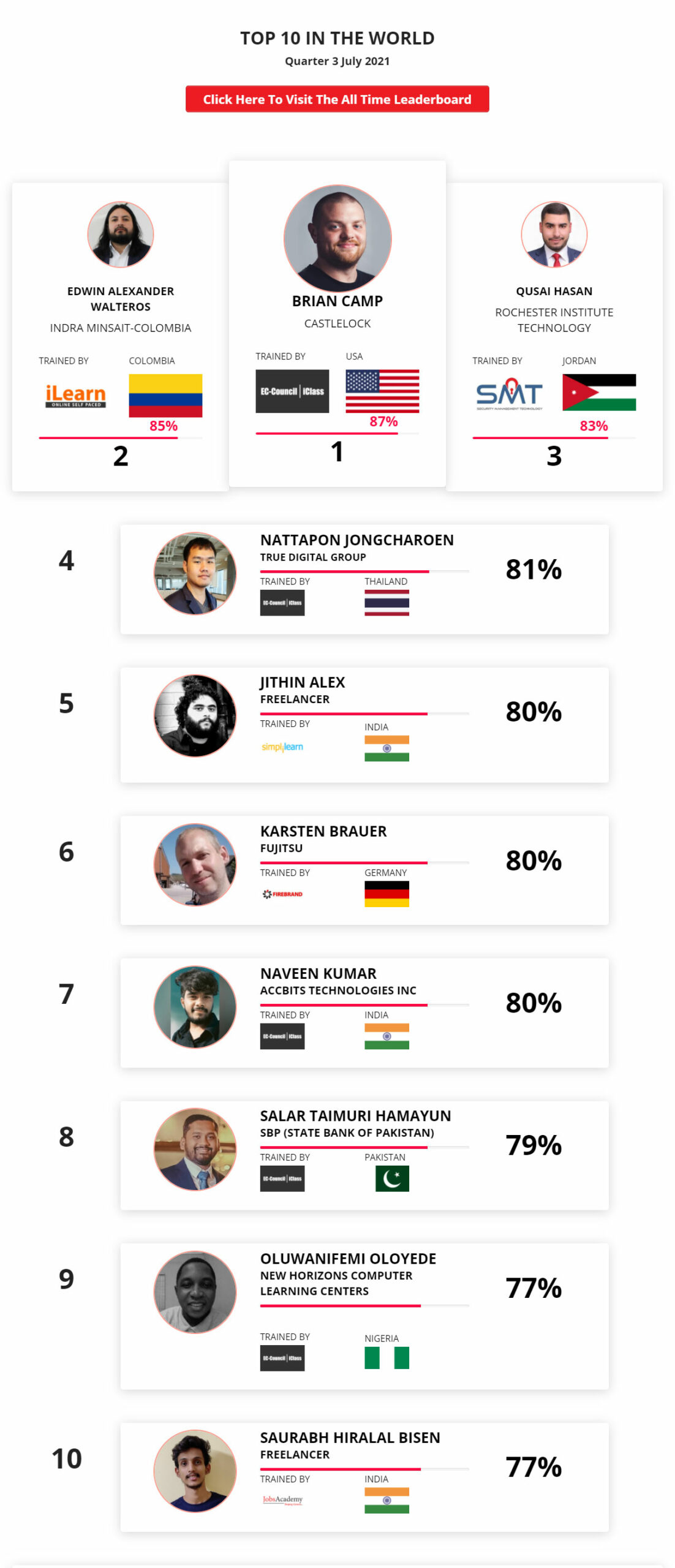
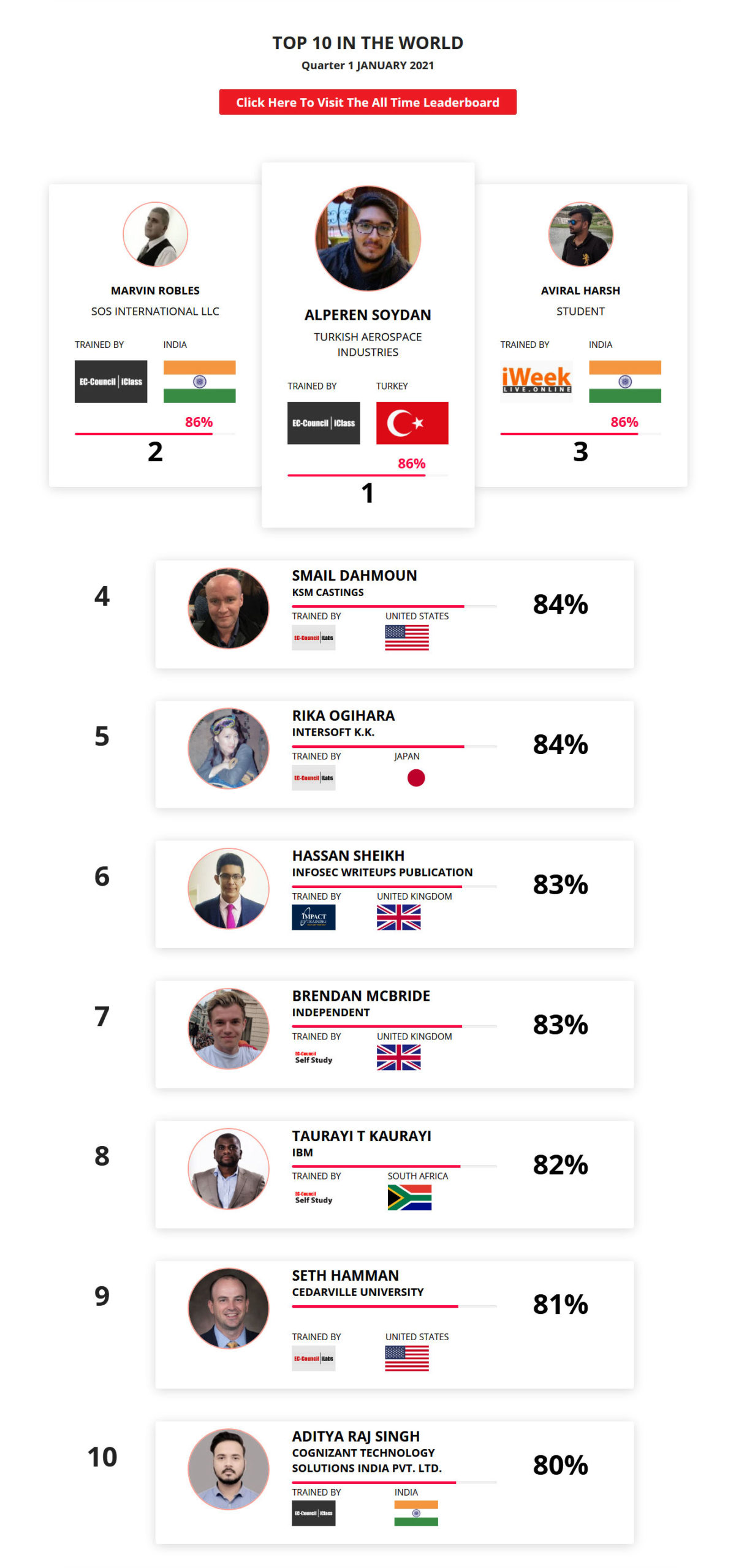
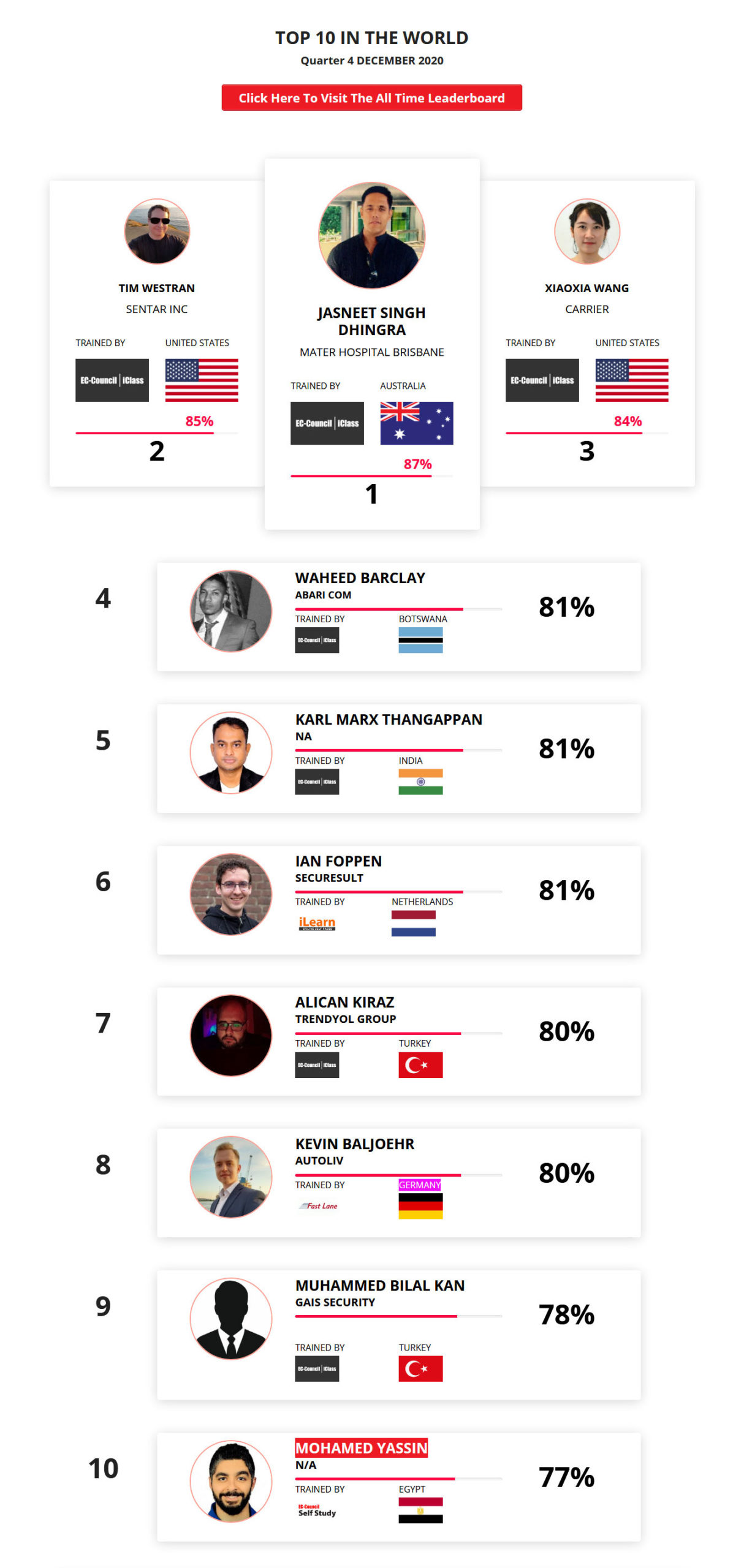
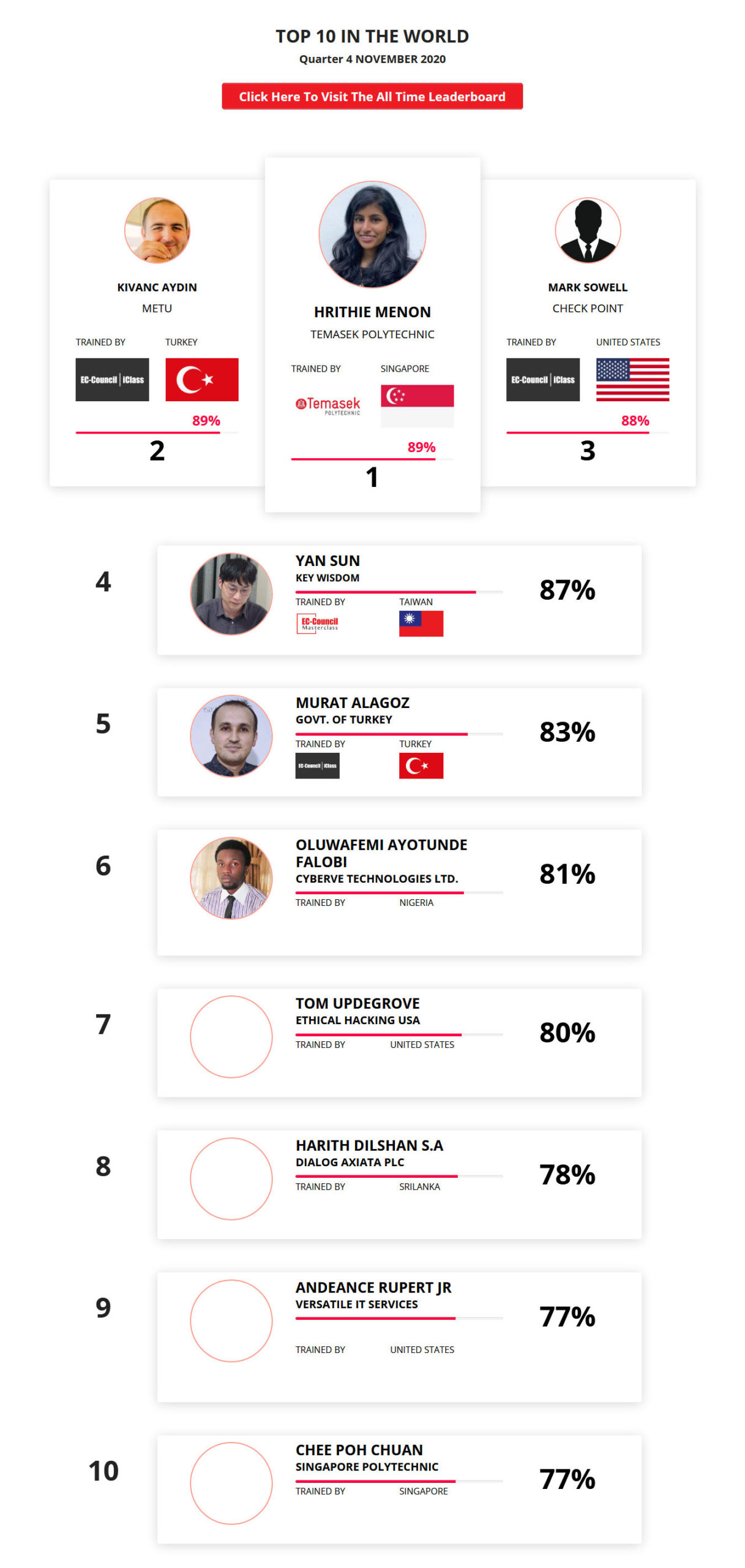
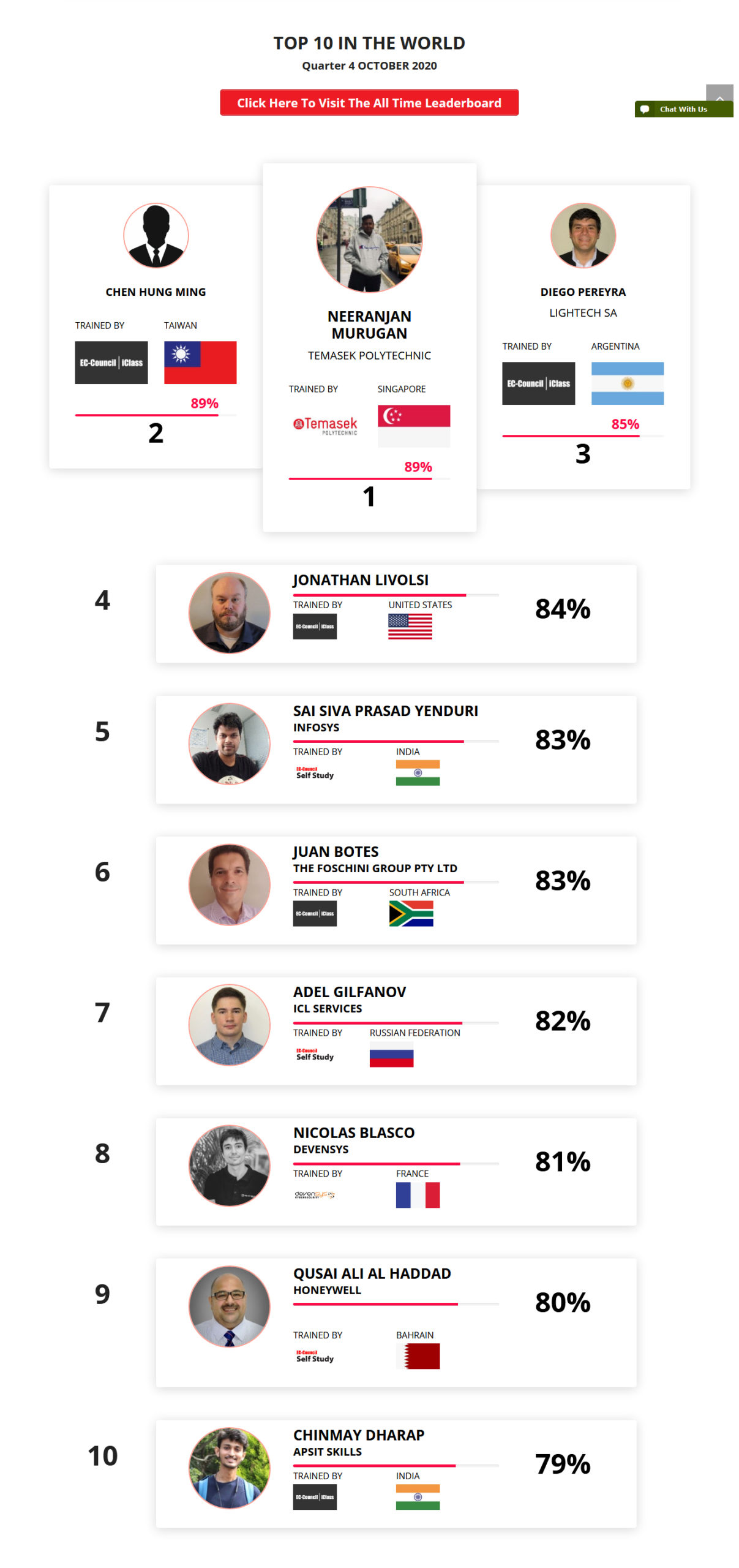
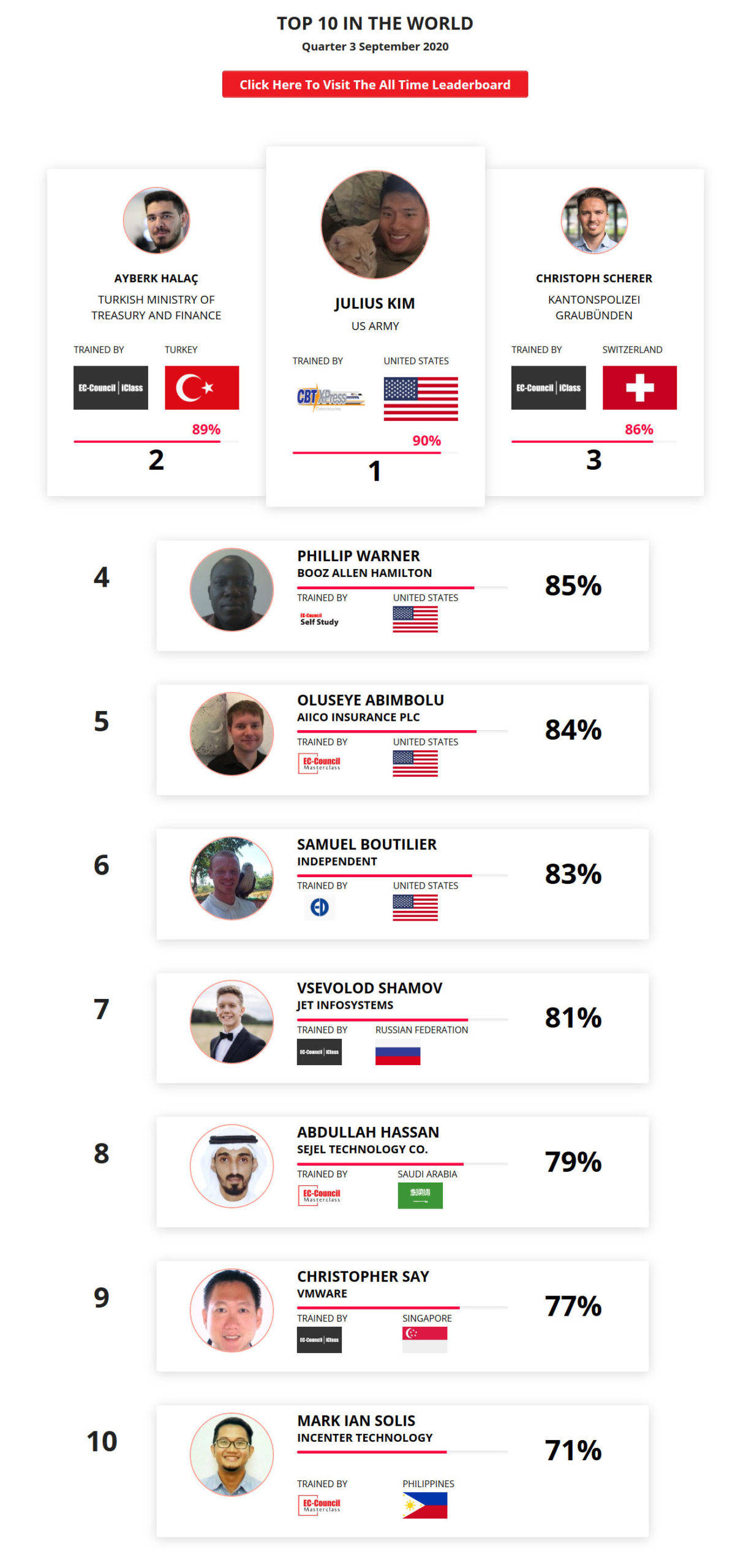
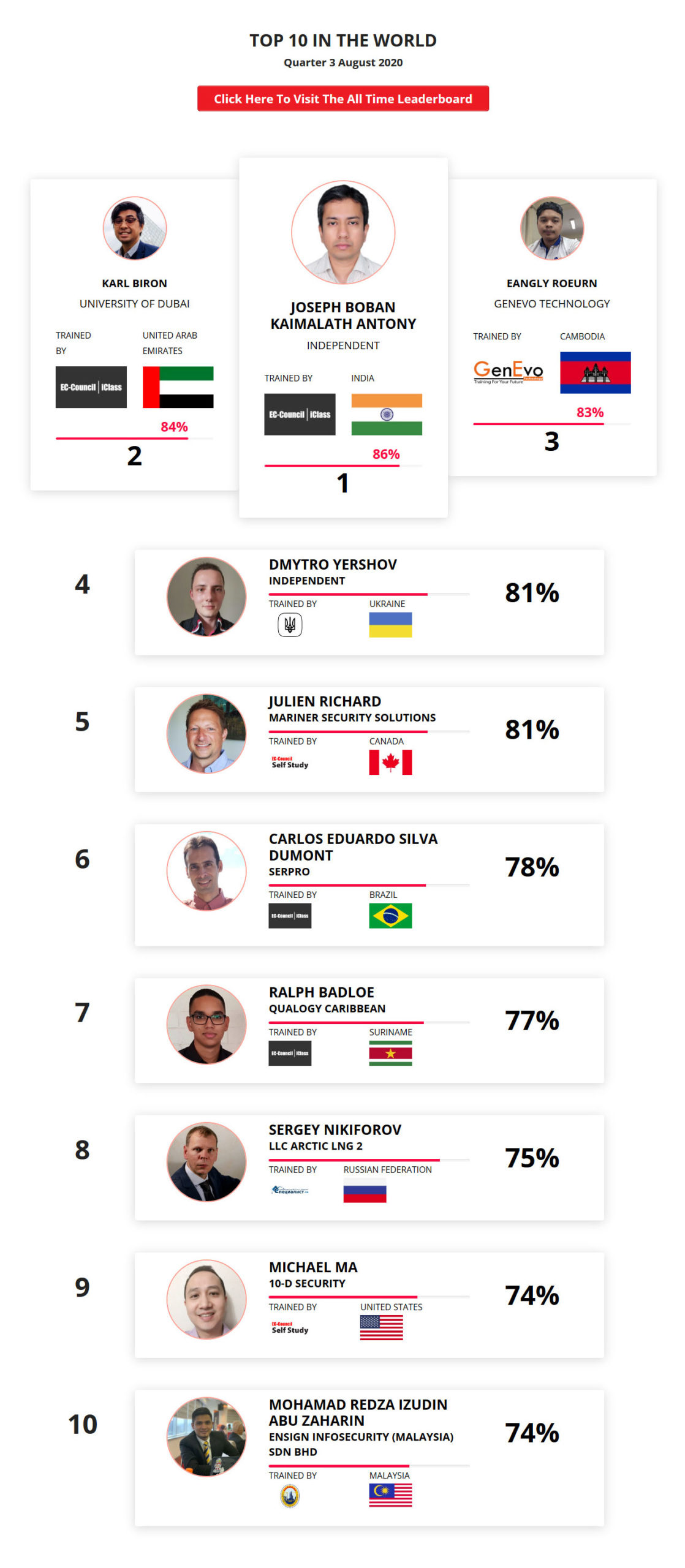
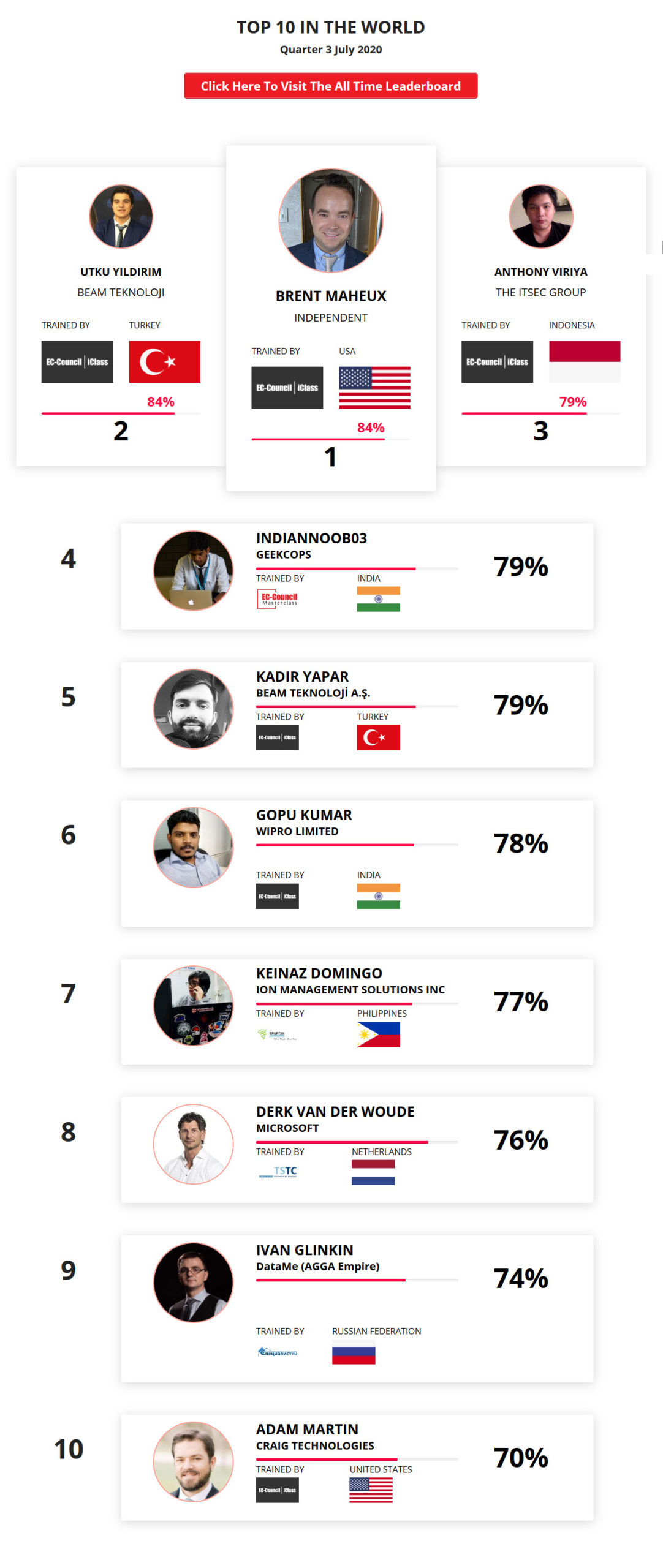
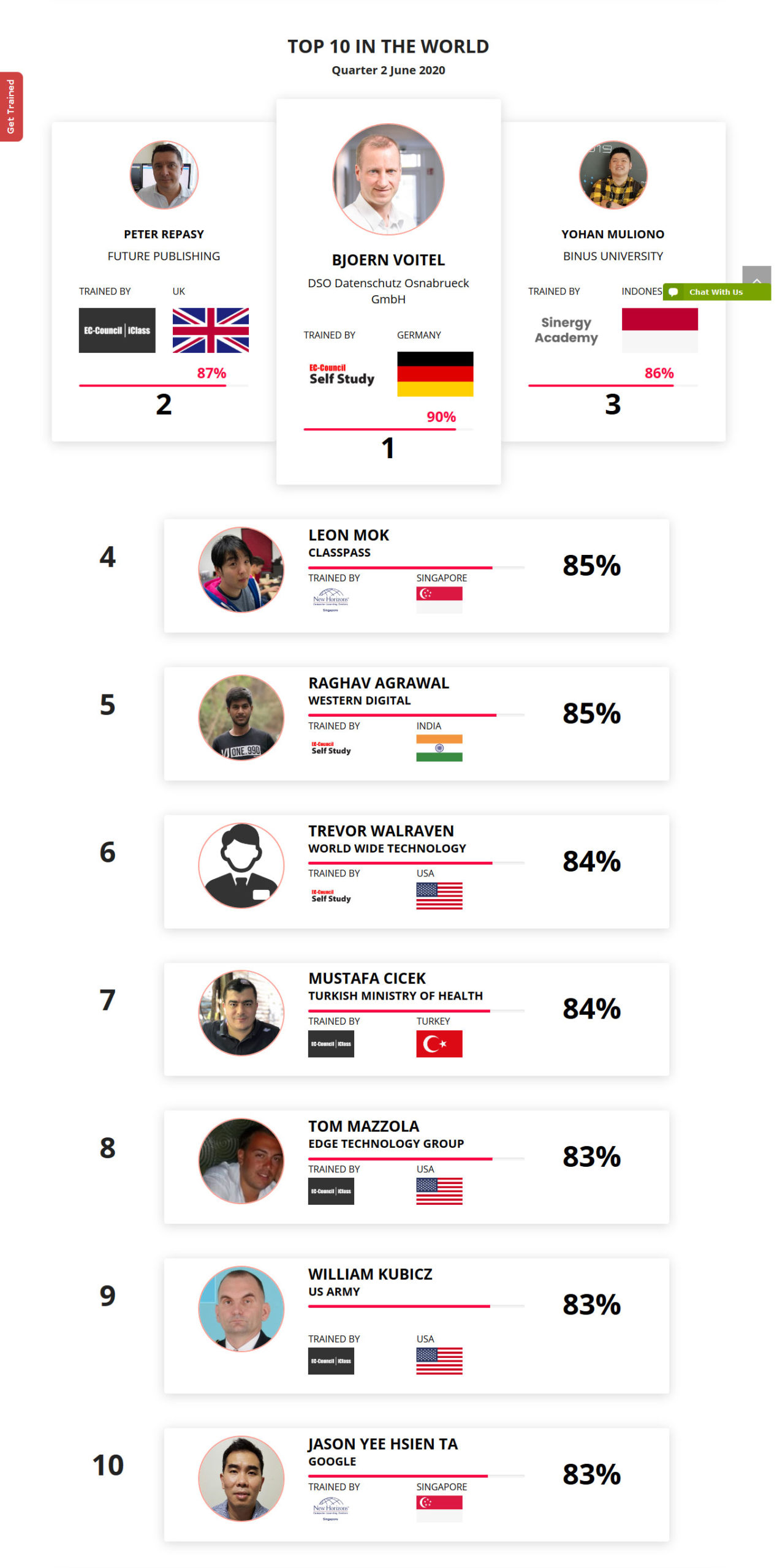
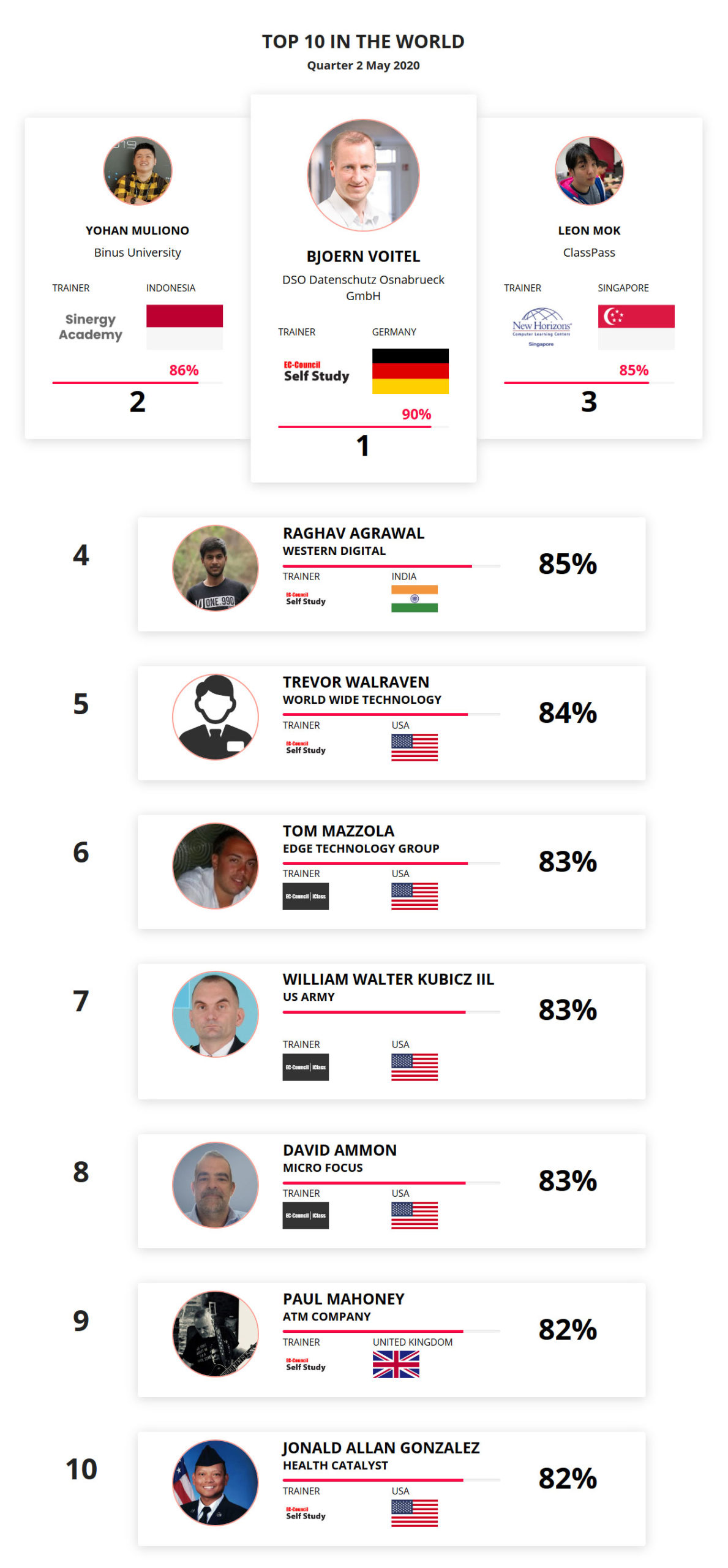
Mohamed Mounir Boudjema
Penetration Tester / Cyber Security Instructor
Trained by


89%
2

Wen Jie Tan
Ministry of Manpower

87%
3

AJAY KUMAWAT


84%

Wen Jie Tan

2

Mohamed Mounir Boudjema
Penetration Tester / Cyber Security Instructor
Trained by

ALGERIA

1

AJAY KUMAWAT
Trained by


3
4

DJIBRILLA BOUKARY Yacine


82%
5

Sujeet Kale
Jr. IT Systems Administrator

81%
6

Mayank Jasuja
Cyber Security Analyst


81%
7

Kush Jasrapuria
Information Security Consultant

80%
8

Chinmay Arora
Cybersecurity Consultant


80%
9

Vansh kumar
Intern

INDIA

80%
10

Mudunuri Naveen Varma
VAPT Analyst


80%
How To Feature On The Leader Board
To feature on the leaderboard, you will have to pass both, the CEH knowledge-based MCQ (v8 and above) and the CEH Practical exam, thereby attaining the CEH (Master) credential. Scoring is based on the marks obtained and time taken to pass the exam. EFFICIENCY IS THE KEY.
Simply put, the faster and more accurate you are, the better your CEH (Master) score is bound to be. Since the CEH (Master) credential is a validation of ethical hacking prowess of a candidate, more weightage is given to the practical exam, due to its 6 hour rigorous challenge, which actually puts a candidate through a live security audit challenge, as if they were an ethical hacker on the job.
We have incorporated weighted scoring components comprised of both score and time to complete to derive our scoreboard leaders.
Our leaderboard algorithm calculates 4 elements, Scores earned in both the CEH knowledge exam and the CEH Practical, as well as time to complete on both exams. Because this is the CEH Master Leaderboard, we hold a higher weightage on the Practical Score than on the Knowledge exam score. Actual leaderboard algorithm weightage is as follows.
MCQ Score =28.6%
MCQ Time = 14.29%
Practical Score = 42.86%
Practical Time = 14.29%
(Note: Placement on the CEH Master Leaderboard has no bearing on certification status, pass or fail, candidates appearing on the leaderboard achieved a combination of the highest scores possible in the fastest time possible in comparison to other CEH Masters appearing on the Leaderboard)
Being featured on the Global Ethical Hacking leaderboard is a privilege. Members receive wide coverage and cognizance from the cybersecurity community. You have now set the bar and it just got higher!
To speak to our specialized career consultant on how to feature on the leaderboard
LEADERBOARD MEMBER INTERVIEWS

Interview With Alessandro Rizzolini
I work for a smart-metering company. We produce electricity meters and develop firm- and software. In Switzerland, we have a new law that all intelligent meters must meet. It is about the security and integrity of the devices. This was when I decided that I should pursue cybersecurity as a career.
As the CEH is a more theoretical exam, it was clear to me that I also want to achieve the more practical master’s exam. The CEH is the first step that I made for my long-term goal: the LPT. I am now training for the ECSA and ECSA Practical exams.
I learned tons of things! A lot of essential tools for security testing. This included the whole chain of information gathering, scanning, enumeration, exploitation, and so forth. It was amusing.
It was nice to see that the iLabs had more to provide. It is an excellent platform for exercising with the tools. Also, the technical support from the EC-Councils support team was exceptional.
I would not exclude that I will go for some other certification when I have achieved the LPT. But for the moment, the EC-Council provides step-by-step certification. I have time. I can do everything at my pace. And it fits perfectly into my working- and family life.

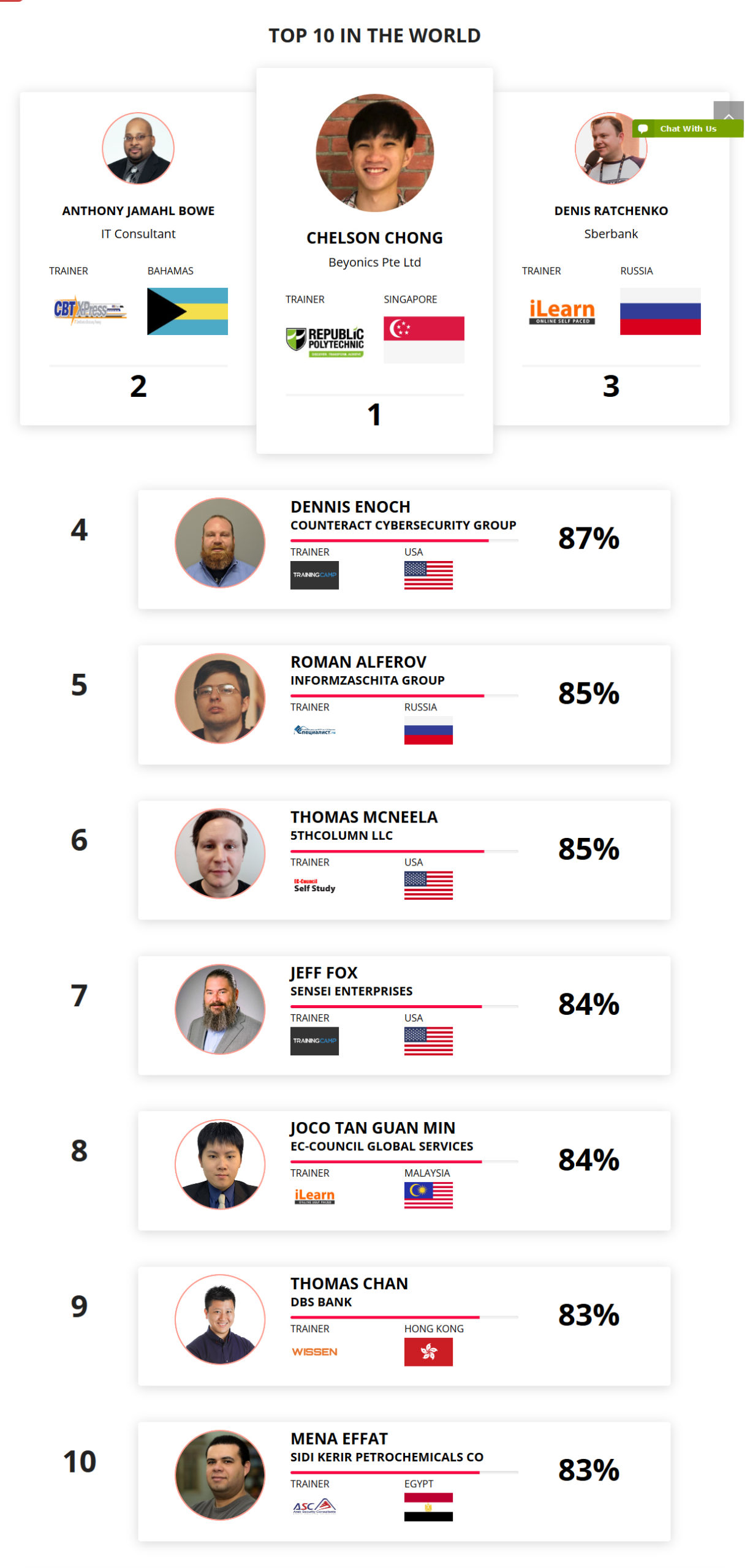
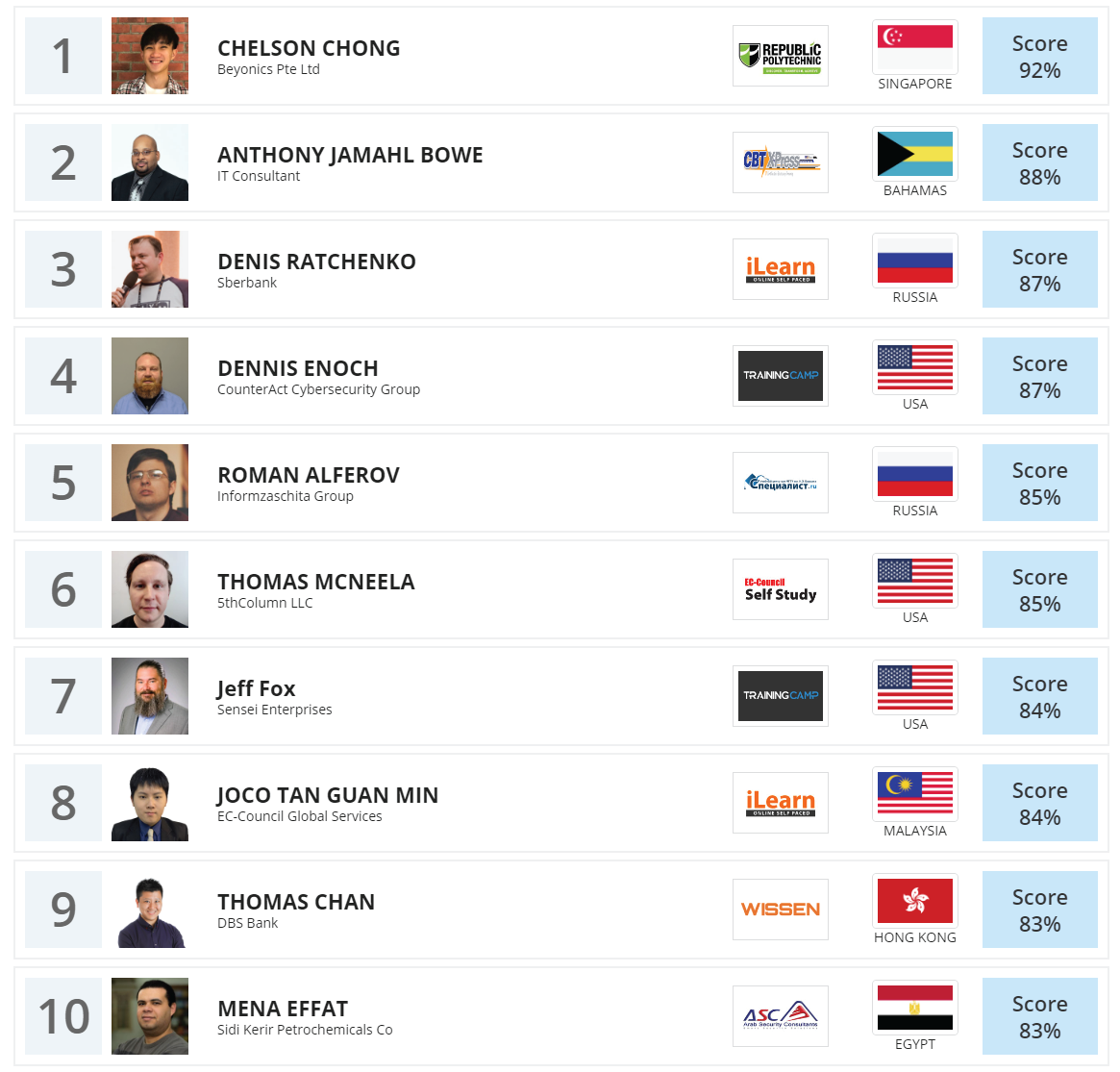
Interview With Chelson Chong
I got into cybersecurity as a career due to sheer curiosity and passion for Digital Forensics. I have been interested in digital forensics and was looking through various courses when cybersecurity appeared, which sparked my curiosity and pushed me to pursue it further.
Attaining CEH (Master) certification is a steppingstone for me to build confidence in the technical skills I possess. I will now slowly pursue more advanced certifications.
One of the most important skill that the CEH (Master) program has provided me is the cyber kill chain methodology, which provides an understanding of the stages of a cyberattack from reconnaissance to exfiltration of data. This aids an Ethical Hacker to identify, prepare to attack, engage, and destroy the target.
One of the most important skill that the CEH (Master) program has provided me is the cyber kill chain methodology, which provides an understanding of the stages of a cyberattack from reconnaissance to exfiltration of data. This aids an Ethical Hacker to identify, prepare to attack, engage, and destroy the target.
My experience was great! EC-Council has given a lot of courseware and training material for us to practice.
Some of the tools and techniques that I use are scanning, Nmap, Sparta, Wireshark. These are used primarily to scan networks and find abnormalities. The other tools that I use, like Acronis and Ease US, are handy for backups.
My advice for people would be not to be daunted by cybersecurity. Yes, it is a big topic and one with lots of responsibilities. But with hard work and perseverance, I am sure you can do it!
I always believe that everyone starts off crawling, and slowly learn to walk and run. Hence, I felt that the EC-Council certification path was a more structured way for me to start my certification routes, from learning the theory (CEH theory) to then slowly advancing to practical skills CEH (Master).
Getting CEH (Master) was an accomplishment for me! It has boosted my confidence as I pursue further into the field of cybersecurity! Without a doubt, there is more to learn in the world of cybersecurity.

Interview With Boštjan Špehonja
Achieving the CEH (Master) certificate was additional confirmation that I was headed in the right direction and that my work was excellent. Also, I am proud to be the first in Slovenia to receive the CEH (Master) certificate. While studying for the certification, I learned some techniques that we have additionally introduced in the daily implementation of penetration tests.
Certainly! I am halfway to achieving an ECSA certificate, and I wish to obtain an LPT certificate as well. I often give lectures on ethical hacking and would one day like to be a Certified EC-Council Instructor.
Definitely! I already do so ever since I got CEH certified. I help a lot of aspiring students learn about information security; some of them decide to get certified as well.
The CEH certificate is well known in the economy and business in Slovenia. It is considered as a mandatory qualification in various tenders due to its recognition and accreditations. With the CEH (Master) certificate, I can now climb a step higher.
"*" indicates required fields