
Become a Certified Ethical Hacker (C|EH) Compete
"*" indicates required fields
CERTIFIED PROFESSIONALS
IN 145 COUNTRIES







CERTIFIED PROFESSIONALS
IN 145 COUNTRIES






Become a Certified Ethical Hacker (C|EH) Compete
"*" indicates required fields
New Ethical Hacking Challenges Every Month
Windows Citadel Breach: Artifact Alchemy
Scenario:
A user in your organization reported suspicious activity on their workstation shortly after opening an email attachment. Initial automated defenses flagged a potential malware infection.
Your Mission:
You have been tasked with performing a forensic analysis to determine the infection vector, timeline, persistence mechanism, and identify any Command and Control (C2) communication.
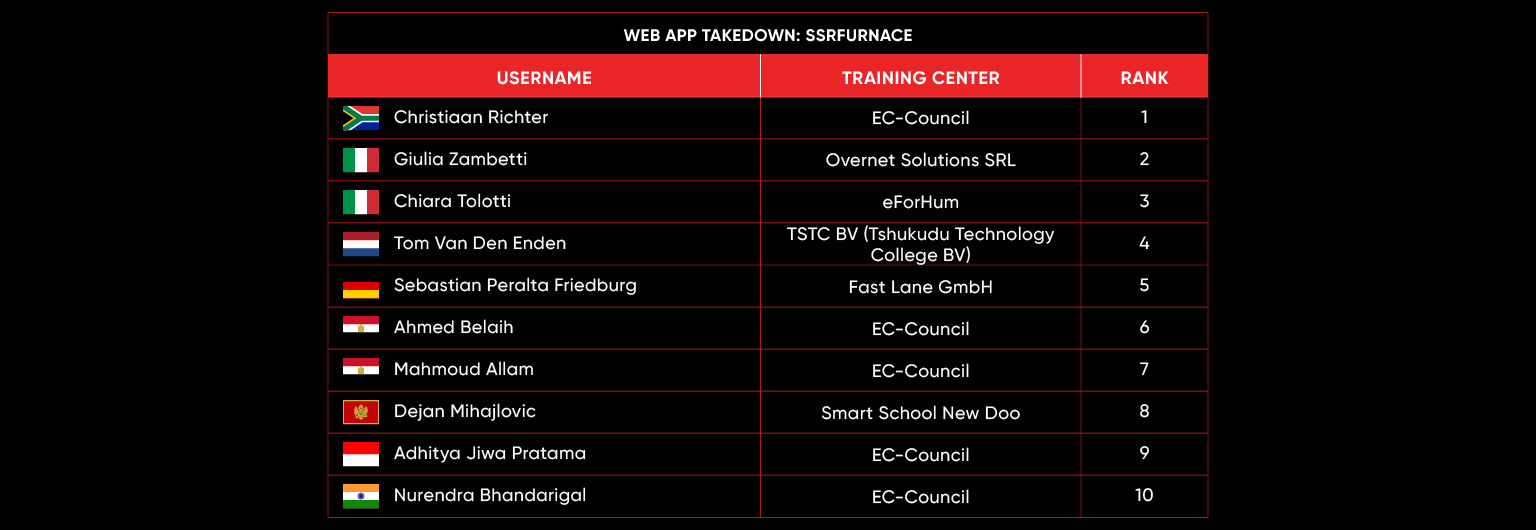
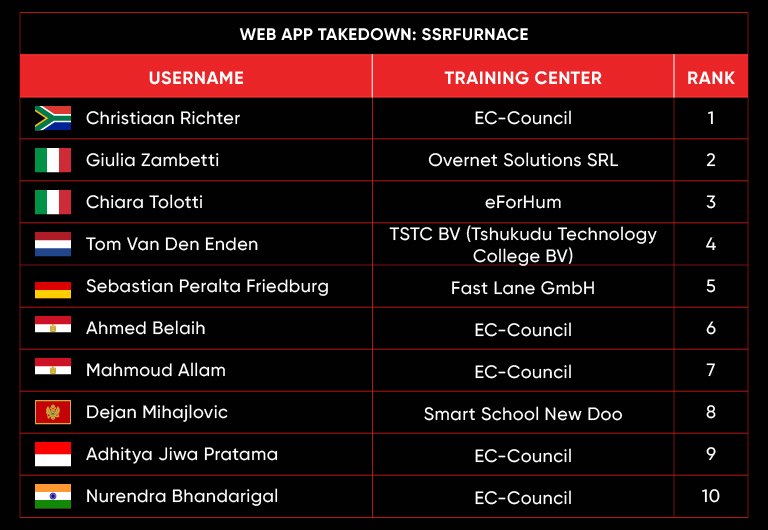
Web App Takedown: SSRFurnace
Scenario:
SSRFurnace, a premier online archive dedicated to the study and preservation of ancient metallurgical techniques and furnace designs, has recently expanded its functionality to dynamically display documents and historical data from various linked archives and partner institutions.
Your Mission:
You are a penetration tester assigned to assess the security of this integration, specifically focusing on how the platform retrieves and presents this interconnected content.
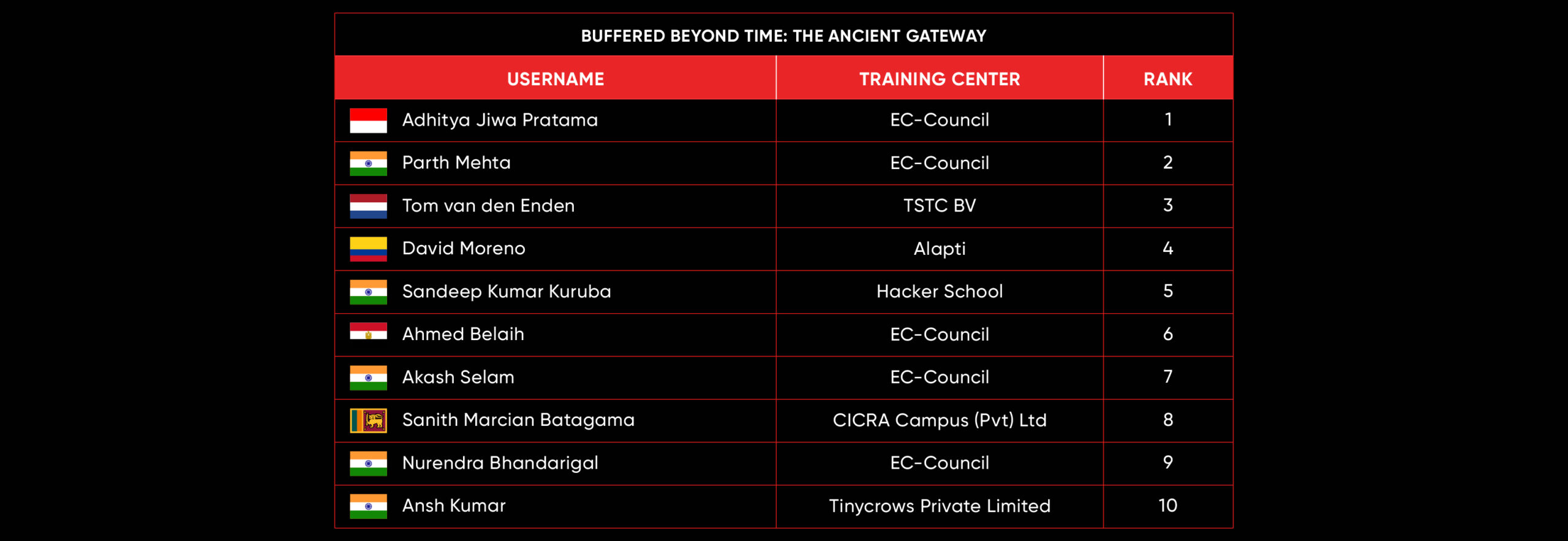
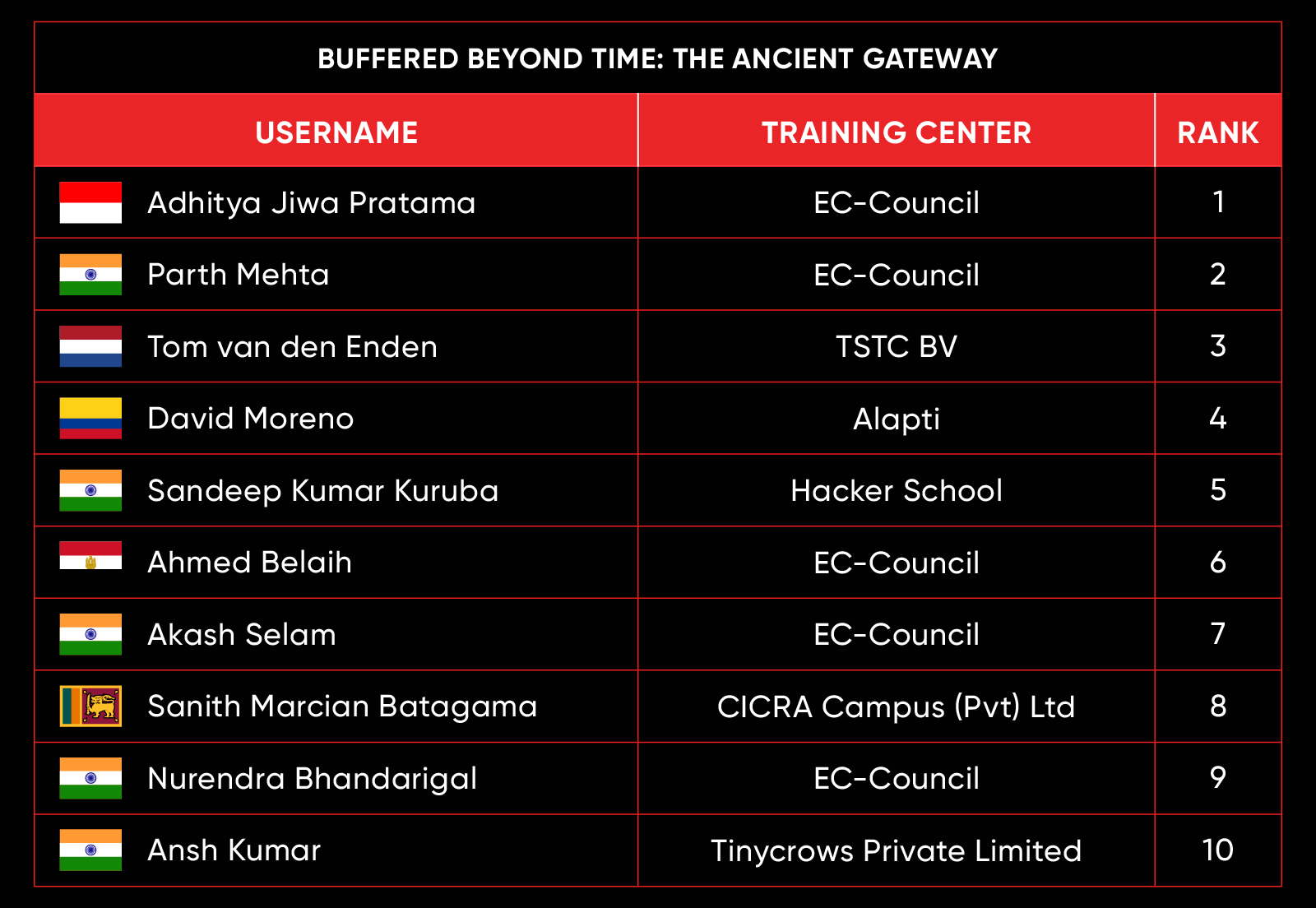
Buffered Beyond Time: The Ancient Gateway
Scenario:
You are presented with a legacy system known as “The Ancient Gateway.” According to ancient legends (and sparse documentation), this gateway guards a valuable secret. The system is old and built on arcane technology, making it a prime candidate for classic vulnerabilities.
Your Mission:
To probe the gateway, uncover its weaknesses, and bypass its defenses to retrieve the secret flag stored within.
Code Red: RansomBreak
Scenario:
You are the lead incident responder for a major metropolitan hospital, which has been crippled by ransomware. Critical files seem to be encrypted, and a ransom demand is displayed. Alongside the ransomware executable, you find network capture files and potentially related log files left on the desktop.
Your Mission:
To analyze the situation, bypass the ransomware’s mechanisms, and recover the original data without paying the ransom.
Artificial Insecurities: Nexus AI
Scenario:
Aperture Cybernetics has launched “Nexus AI,” a new personal assistant designed to help users find products, get insights, and unlock information. This AI is integrated into their main product search page. However, there are suspicions that the AI’s interaction with the backend database may not be as secure as intended.
Your Mission:
You must investigate the AI’s functionality, identify any vulnerabilities, and attempt to gain administrative access to the system.
Gridlock: Traffic Light
Scenario:
You’re a penetration tester hired by FlexoForge Industries, a high-speed automotive parts manufacturer. Their plant runs on a partially automated assembly line, where raw parts are routed by a conveyor belt to various robotic stations. To control the flow of parts and prevent jams, the conveyor relies on traffic light signals (red, yellow, green) at critical junctions.
The signals are controlled by a MODBUS TCP/IP-based PLC (Programmable Logic Controller). Any slight misalignment in the timing of these lights can delay or misroute parts, causing fulfillment issues in just a matter of minutes.
Your Mission:
Recently, the plant reported irregular delays, and your task is to investigate potential vulnerabilities in the traffic light control system. But you’re also tasked with demonstrating a controlled exploit where you must take over the lights and cause a specific conveyor pattern to extract the flag.
AD Compromise: The Distress Signal
Scenario:
You’re a cybersecurity contractor brought in by Ares Interplanetary after they lost contact with ROVER-01, a geological drone exploring the Martian surface. Internal access to critical systems has been lost following a major domain misconfiguration. With administrative credentials locked out and the only remaining access limited to basic network reachability, Ares provides you with leaked internal wordlists and access to a compromised terminal.
Your Mission:
Your objective is to infiltrate the domain, recover the legacy protocol key stored within MARS-DC01, and restore the drone’s communication before it powers down permanently.
Gateway Collapse: Securing the API Frontier
Scenario:
A social media platform, “SquadConnect,” is facing an API security crisis. A flaw in their authentication gateway allows attackers to exploit Broken Object Level Authorization (BOLA) vulnerabilities, giving them unauthorized access to private user data.
Your Mission:
To identify and patch these insecure API endpoints, fix flawed rate limiting, and prevent mass data scraping.
Sanctum Breach: NoSQLNinja
Scenario:
MangoQuest, an emerging tech company, recently upgraded its web infrastructure and integrated a new database system to enhance performance and scalability. To ensure their security measures are robust, they hired you, a database security expert, to evaluate the system for potential vulnerabilities.
Your Mission:
You are tasked with identifying weaknesses, assessing risks, and providing a detailed report on any security flaws discovered.
Red Team Ops: The Corporate Infiltration
Scenario:
You are a red team operator hired by a tech unicorn to simulate an attack from a rival corporation. Your objective is to gain initial access through a misconfigured server, escalate privileges on the host, and then pivot through different network segments.
Your Mission:
Your ultimate goal is to reach the protected R&D network and exfiltrate a target file containing trade secrets.
Neural Firewall: Operation Restore
Scenario:
A critical, next-generation AI firewall responsible for protecting your organization’s network has been sabotaged. A polymorphic malware attack has corrupted the Neural Defense Core by altering its training dataset, rendering all threat classification modules inoperable.
Your Mission:
As the last secure operator with access to the recovery console, your mission is to restore the firewall. You must analyze the corrupted data, craft a new, valid dataset, and upload it to the recovery shell to retrain the AI and bring the firewall back online.
Skyfall: The Cloud–Native Breach
Scenario:
A leading streaming service built on AWS has detected a major breach. Attackers exploited a misconfigured IAM role attached to an EC2 instance, gaining initial access. They are now moving laterally by accessing sensitive data in S3 buckets and RDS databases.
Your Mission:
Your job is to analyze CloudTrail logs, identify the full scope of the compromise, revoke the malicious credentials, and reconfigure the cloud environment to prevent re-entry.
What are the C|EH Global Challenges?
The C|EH Compete Global Challenges part of C|EHv13 Training occurs every month, providing capture-the-flag style competitions that teach students about new technologies and platforms from web applications, OT, IoT, SCADA, and ICS systems to cloud and hybrid environments. Our compete structure lets ethical hackers fight their way to the top of the leaderboard each month in these curated 4-hour CTFs.
C|EH Global Challenge Calendar
| Month | Skill Challenge |
|---|---|
| September 2025 | Cloud Clash: Battle for Infrastructure Security |
| October 2025 | Windows Citadel Breach: Artifact Alchemy |
| November 2025 | Web App Takedown: SSRFurnace |
| December 2025 | Buffered Beyond Time: The Ancient Gateway |
| January 2026 | Code Red: RansomBreak |
| February 2026 | Artificial Insecurities: Nexus AI |
| March 2026 | Gridlock: Traffic Light |
| April 2026 | AD Compromise: The Distress Signal |
| May 2026 | Gateway Collapse: Securing the API Frontier |
| June 2026 | Sanctum Breach: NoSQLNinja |
| July 2026 | Red Team Ops: The Corporate Infiltration |
| August 2026 | Neural Firewall: Operation Restore |
| September 2026 | Skyfall: The Cloud- Native Breach |
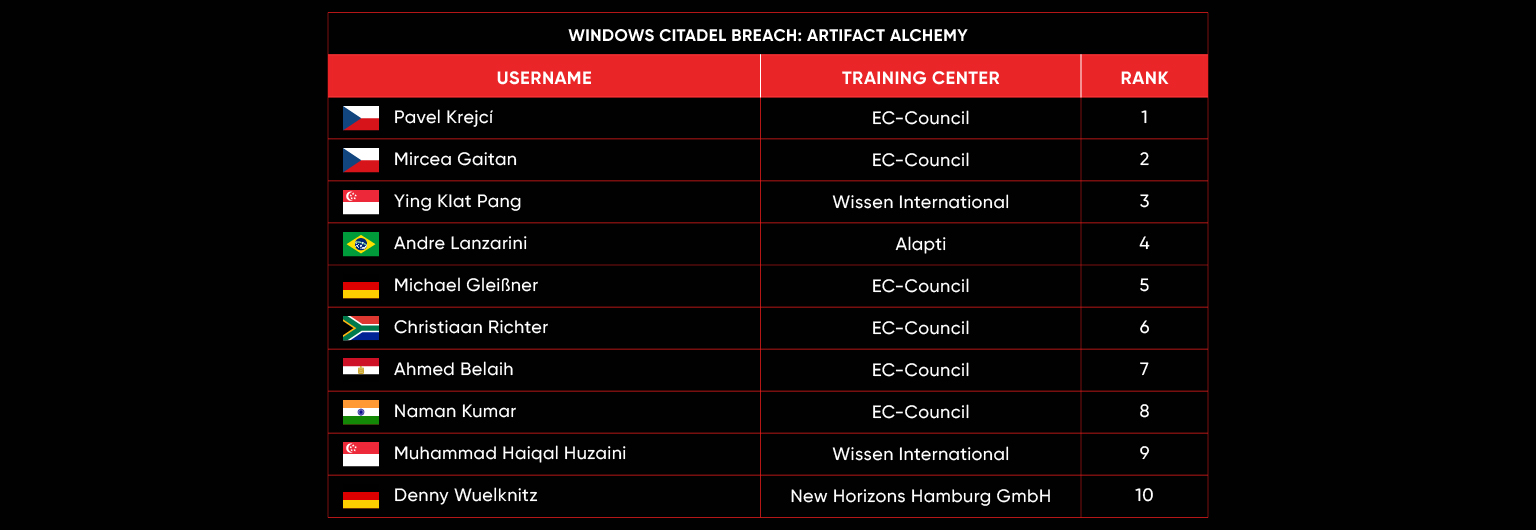
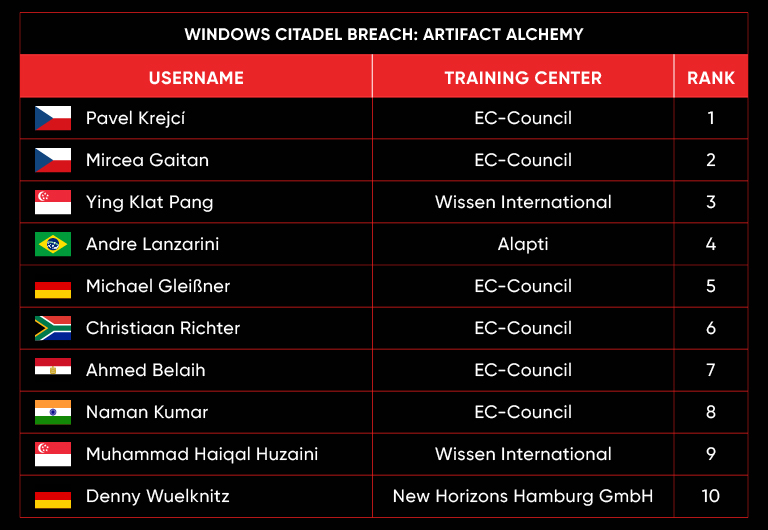
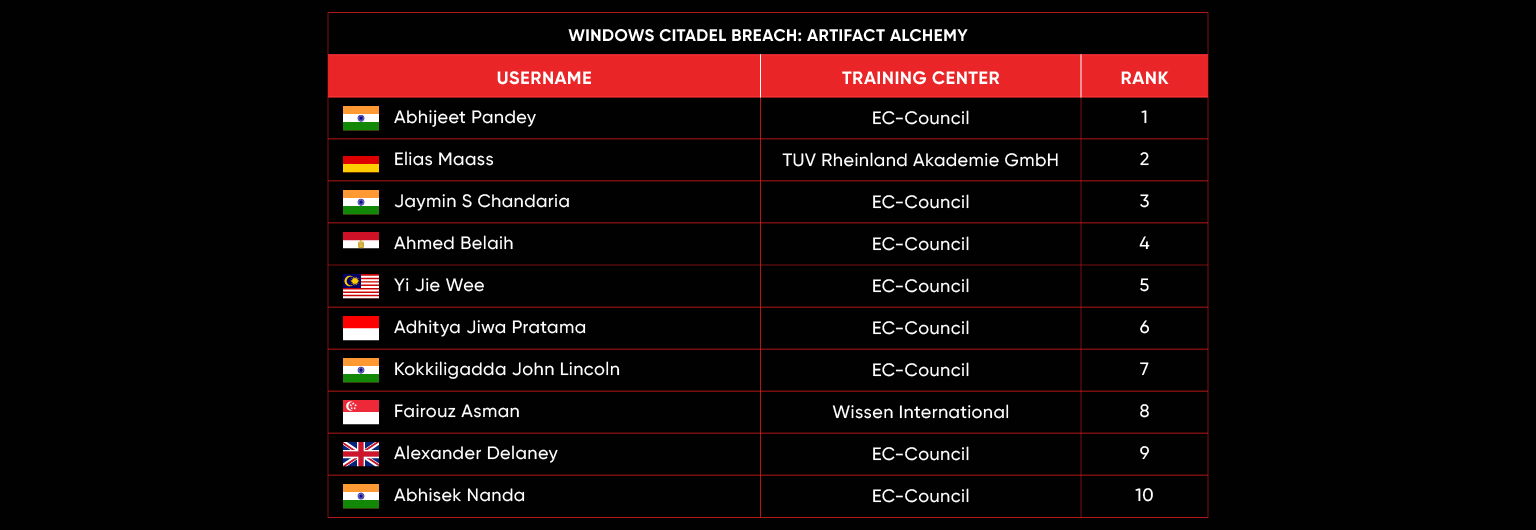
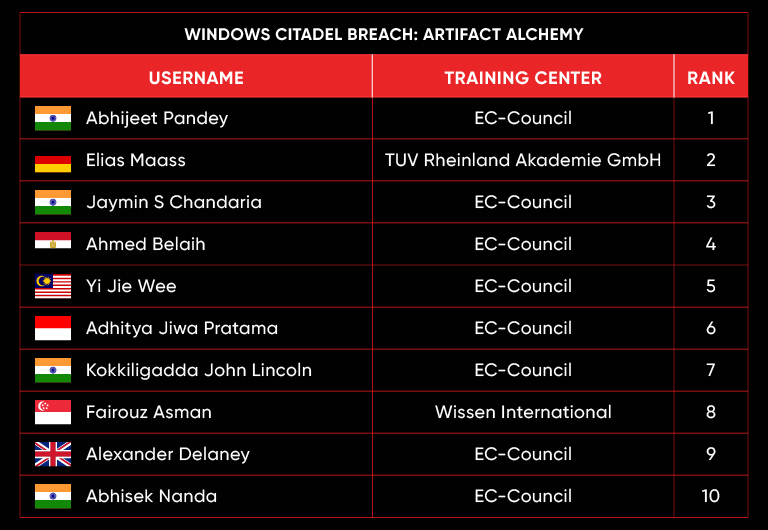
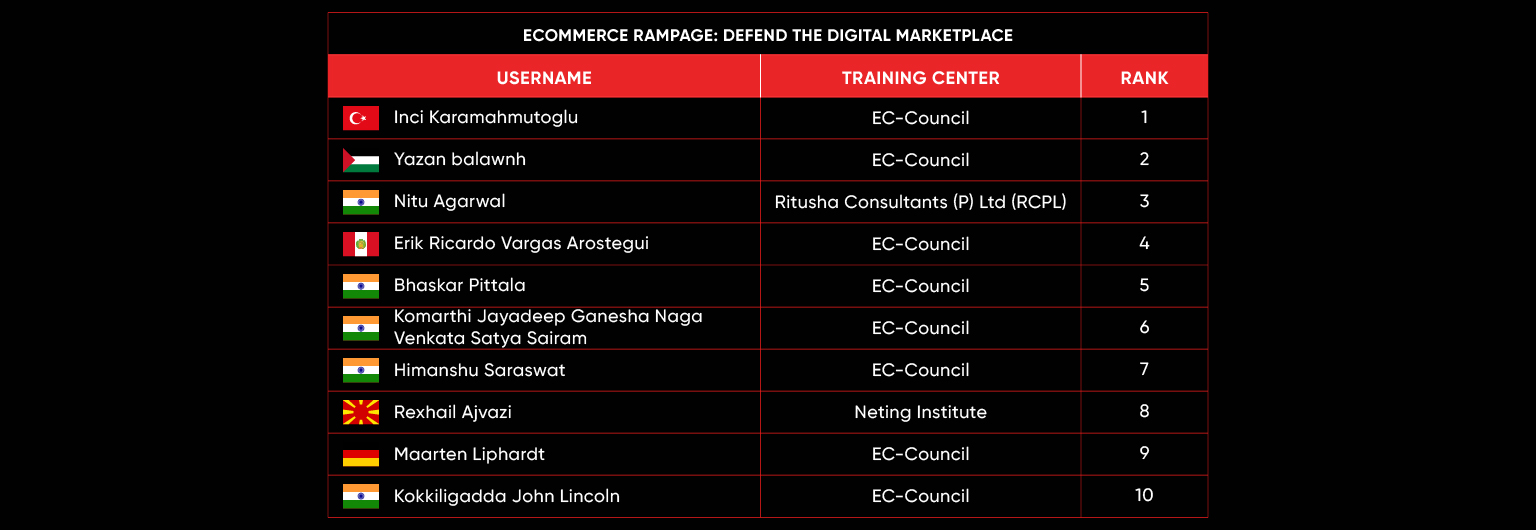
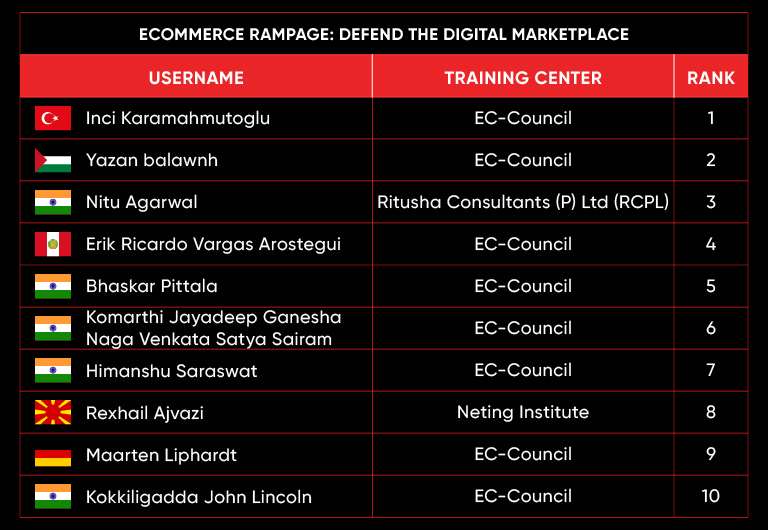
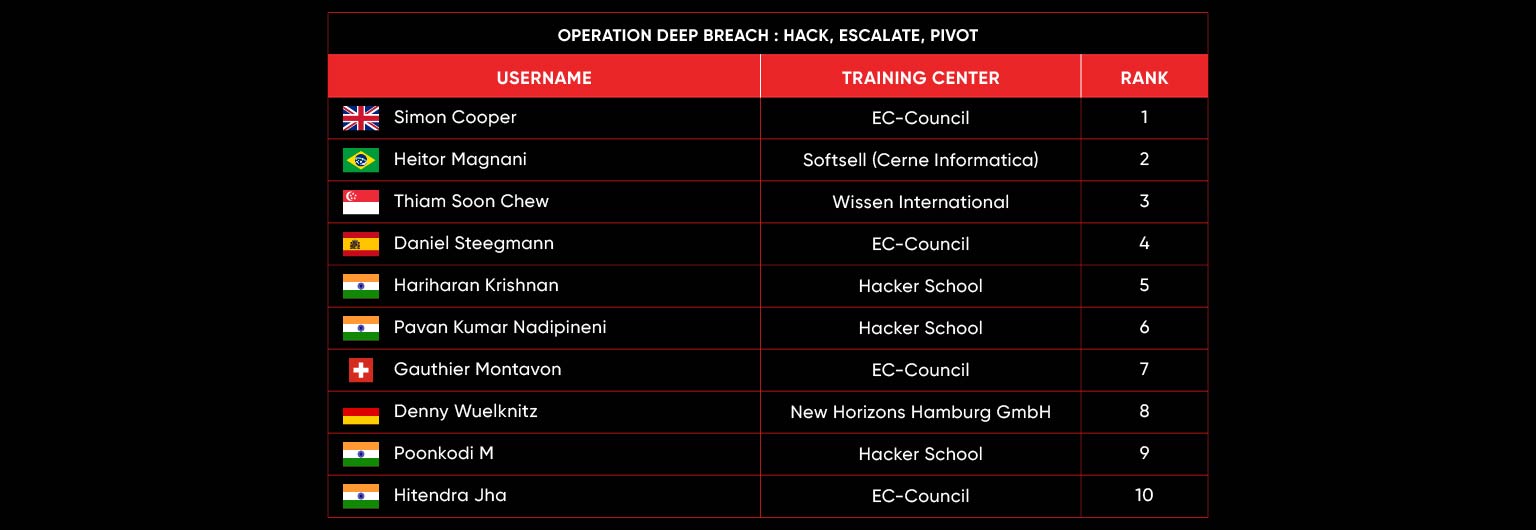
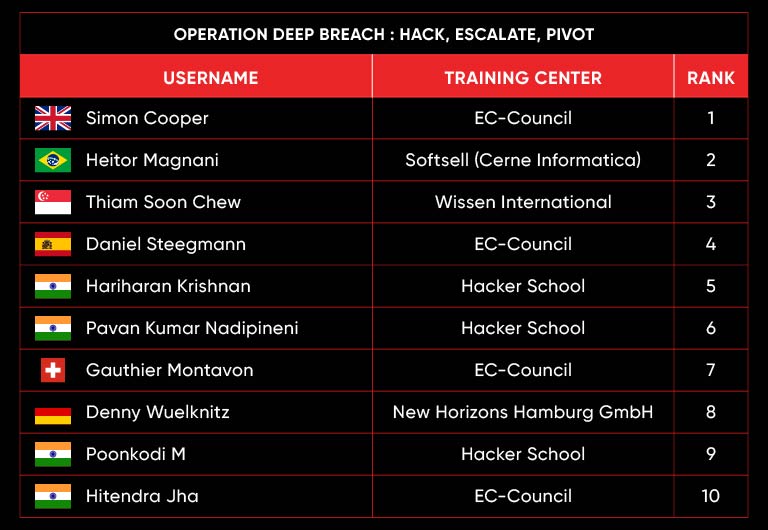
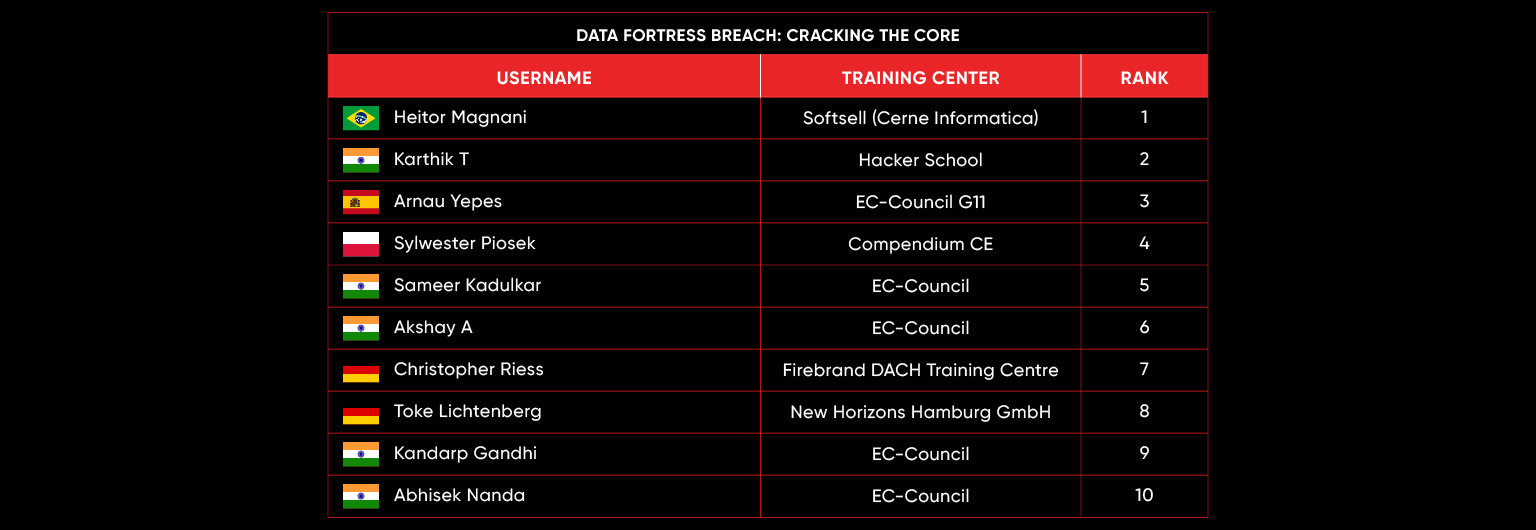
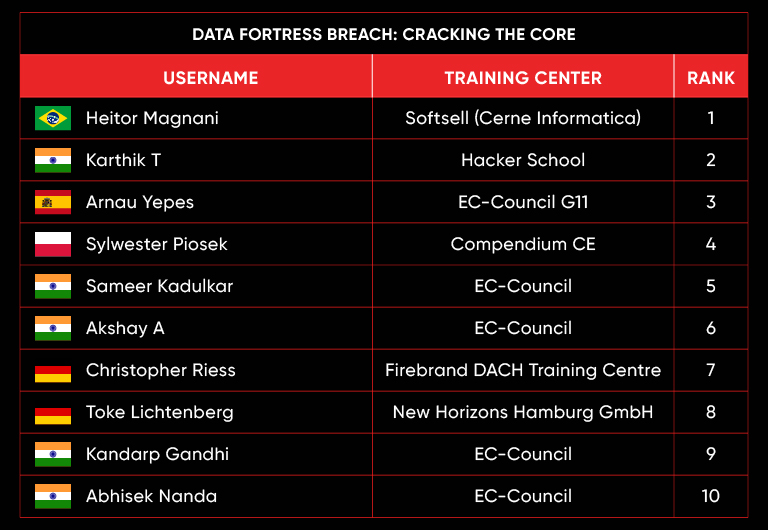
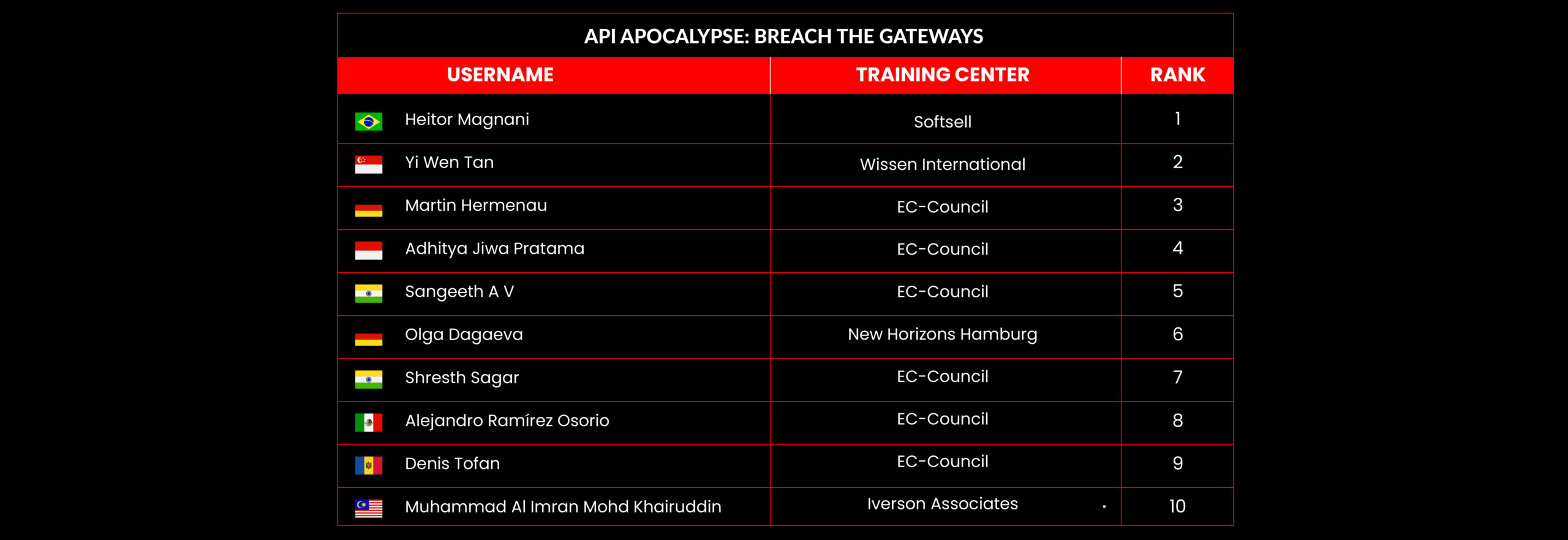
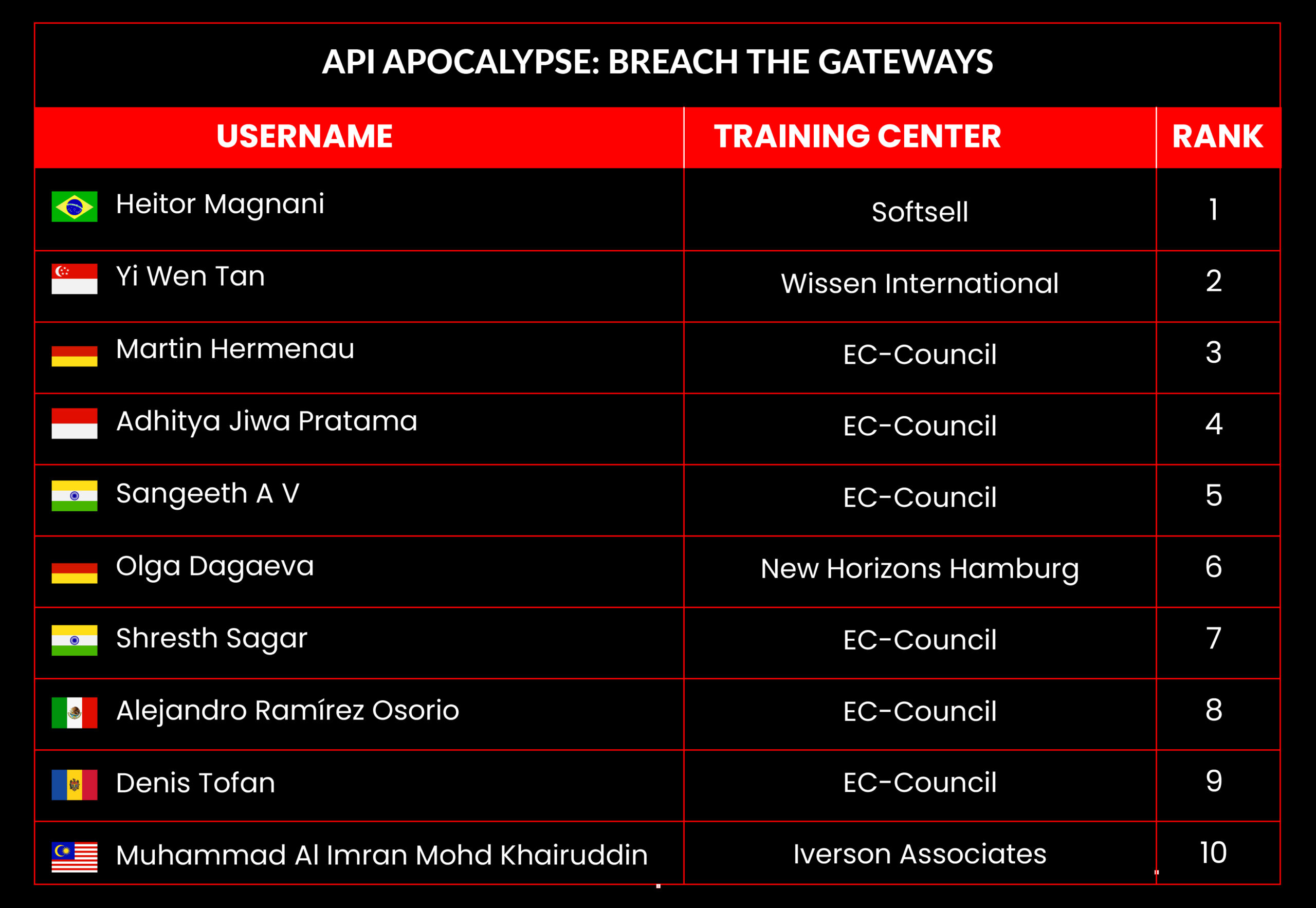
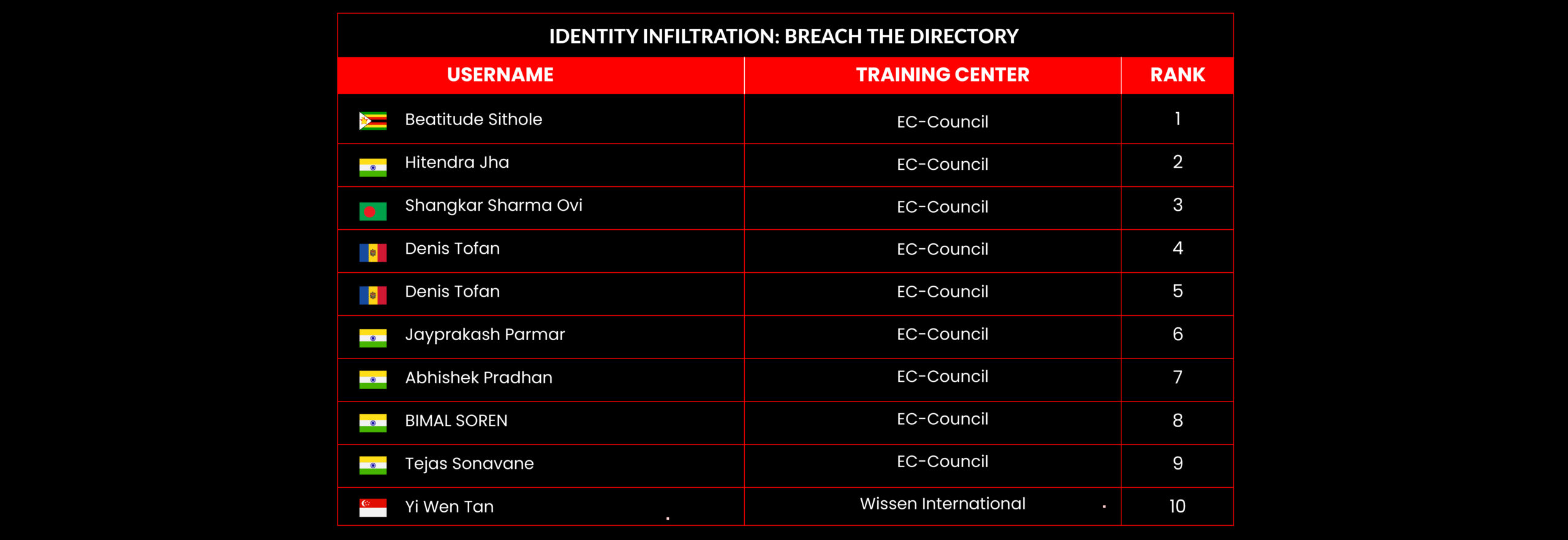
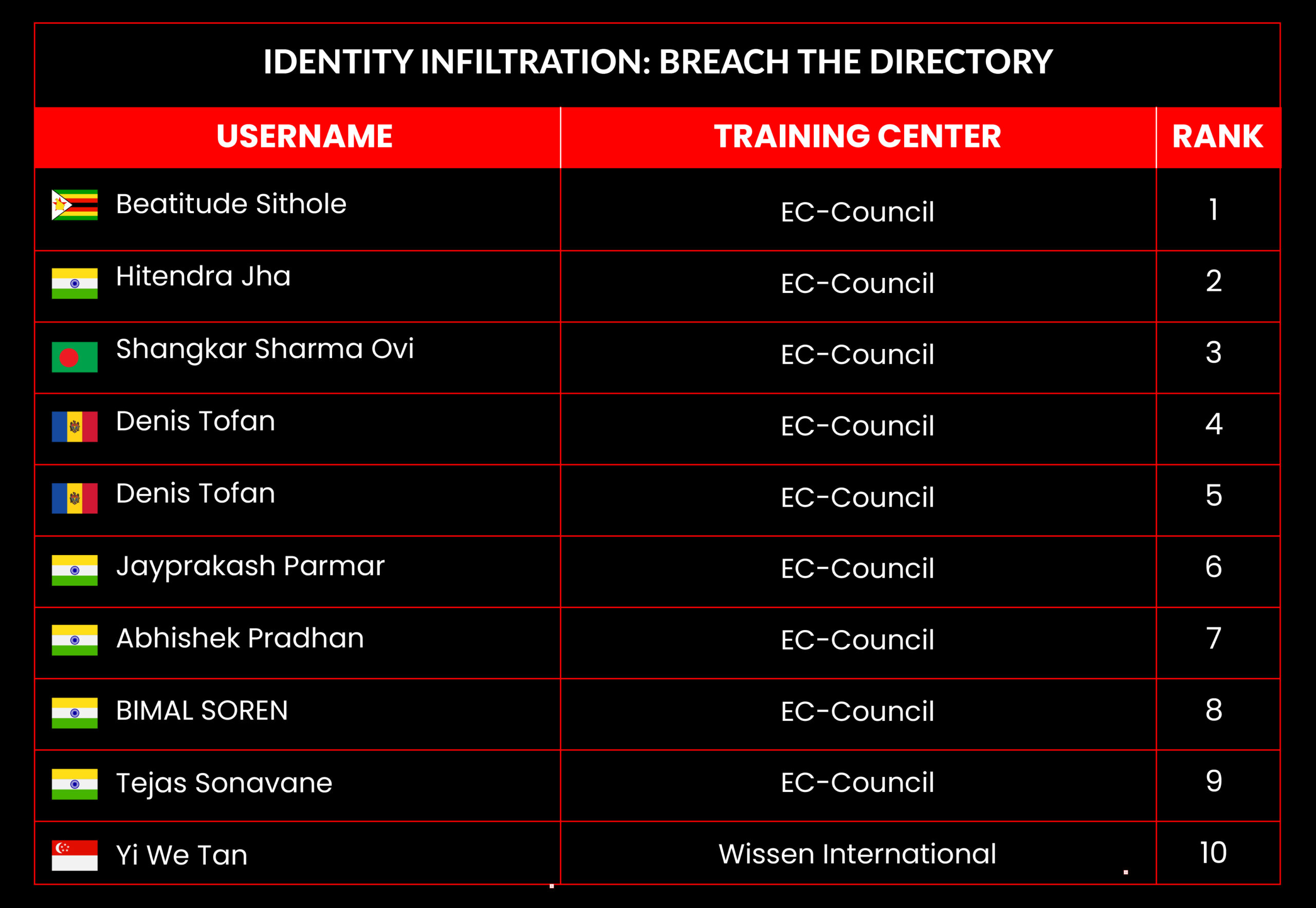
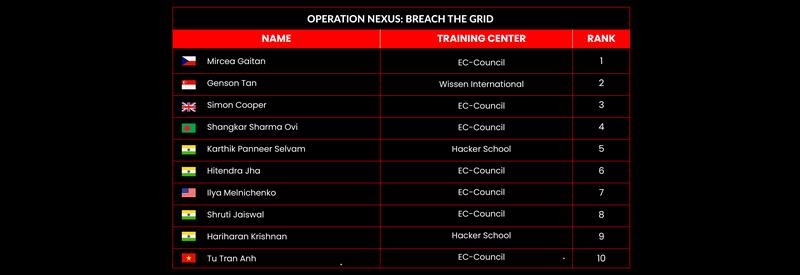
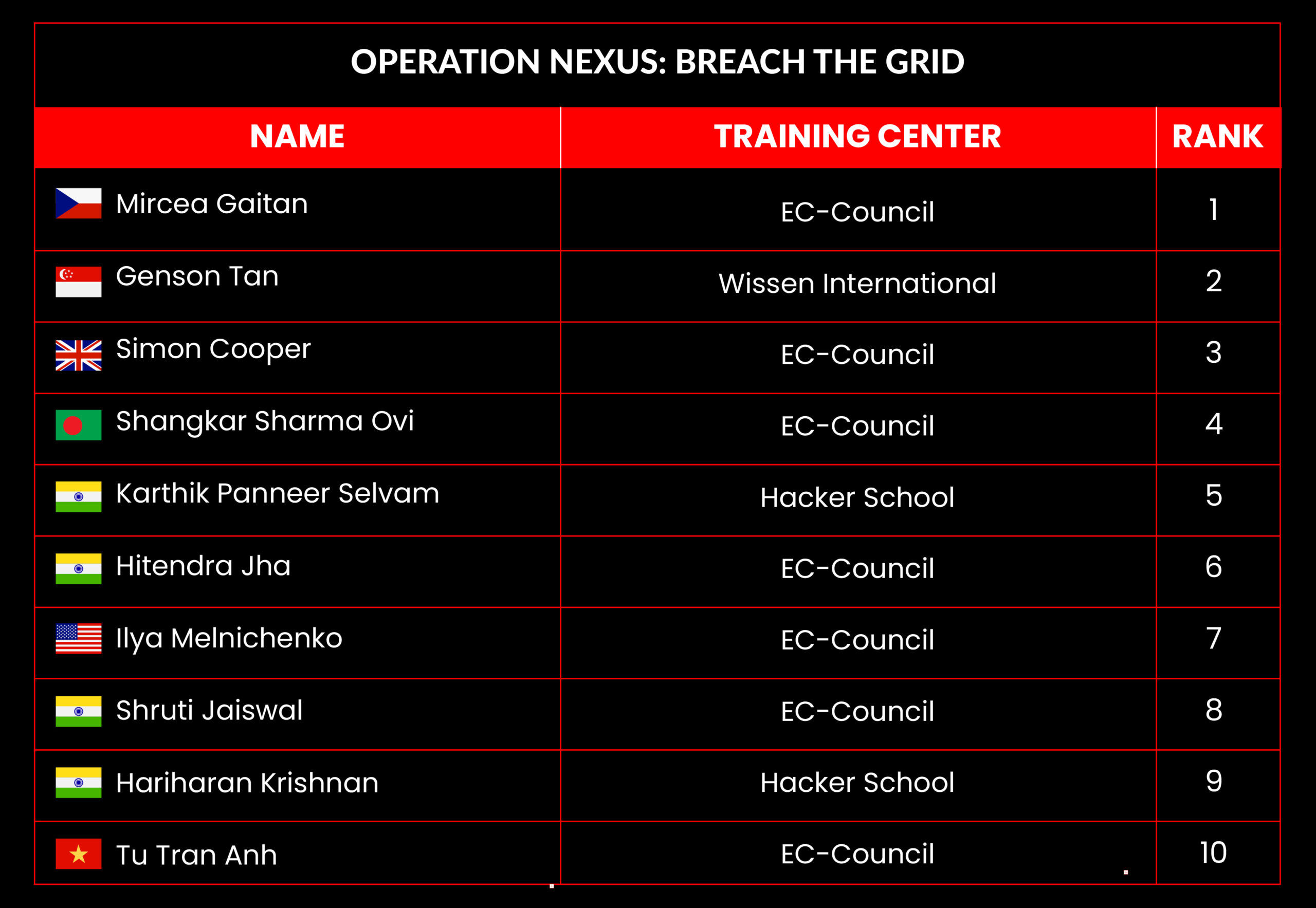
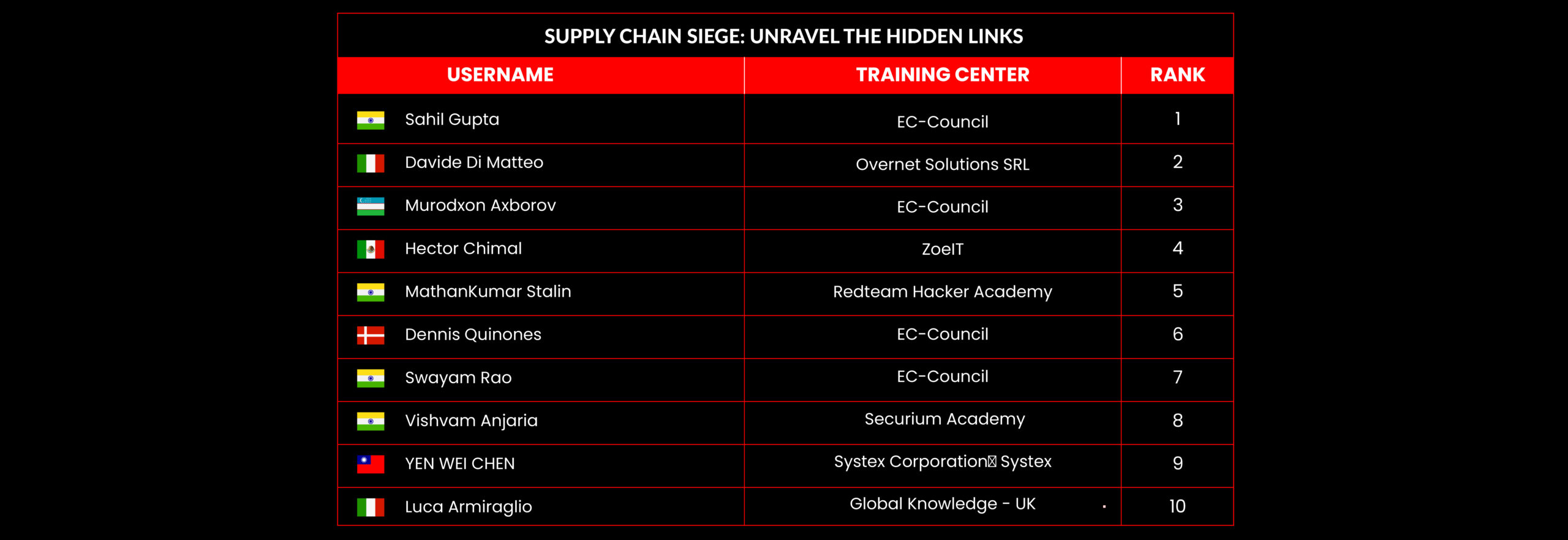
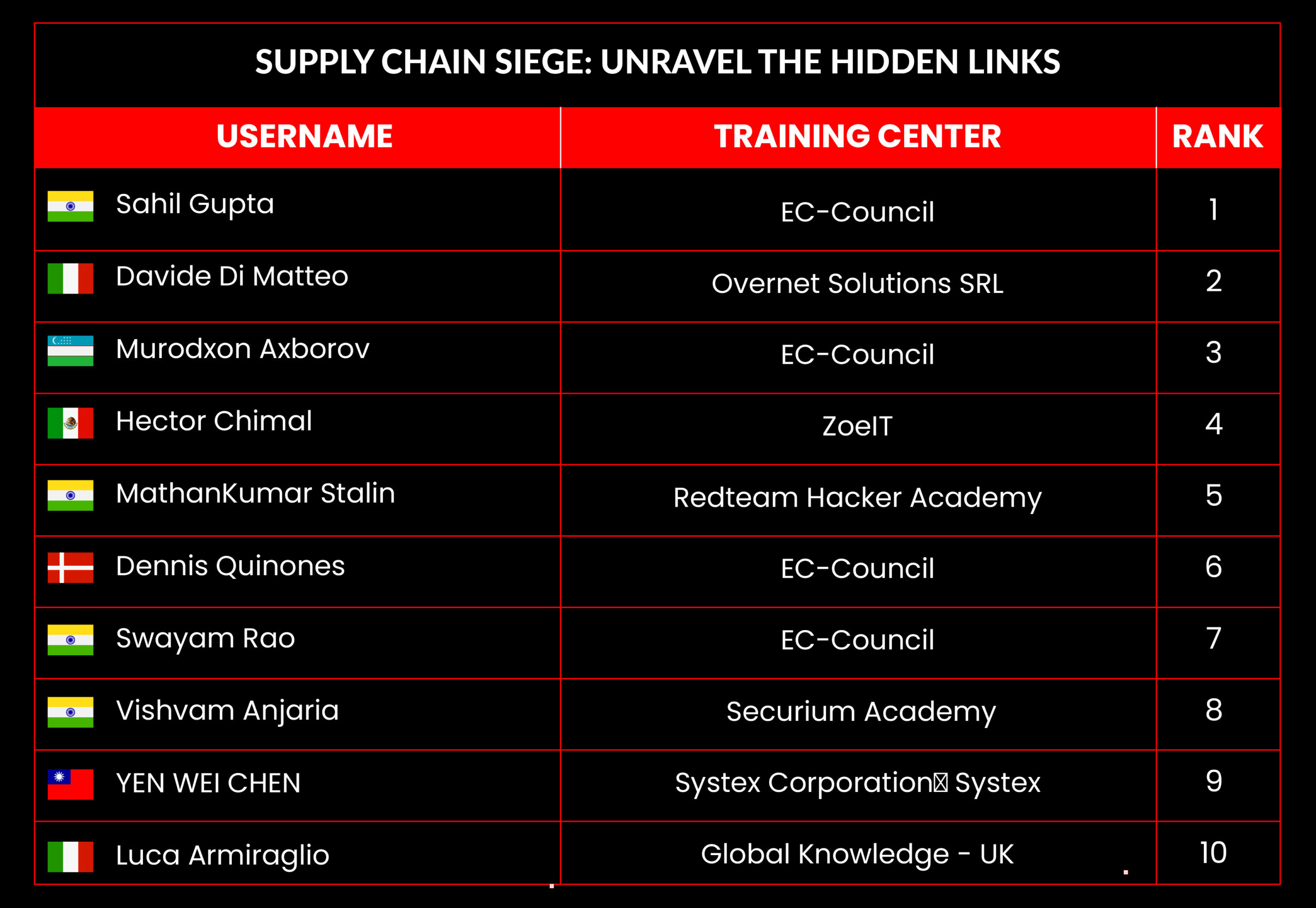
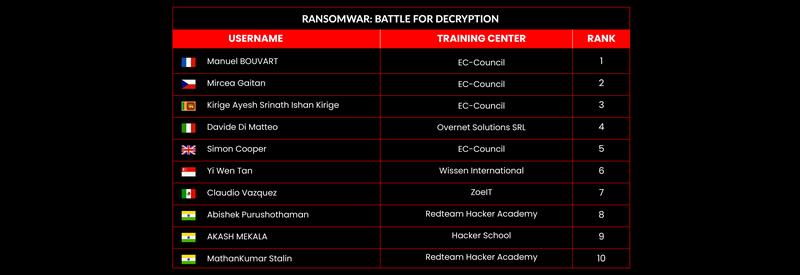
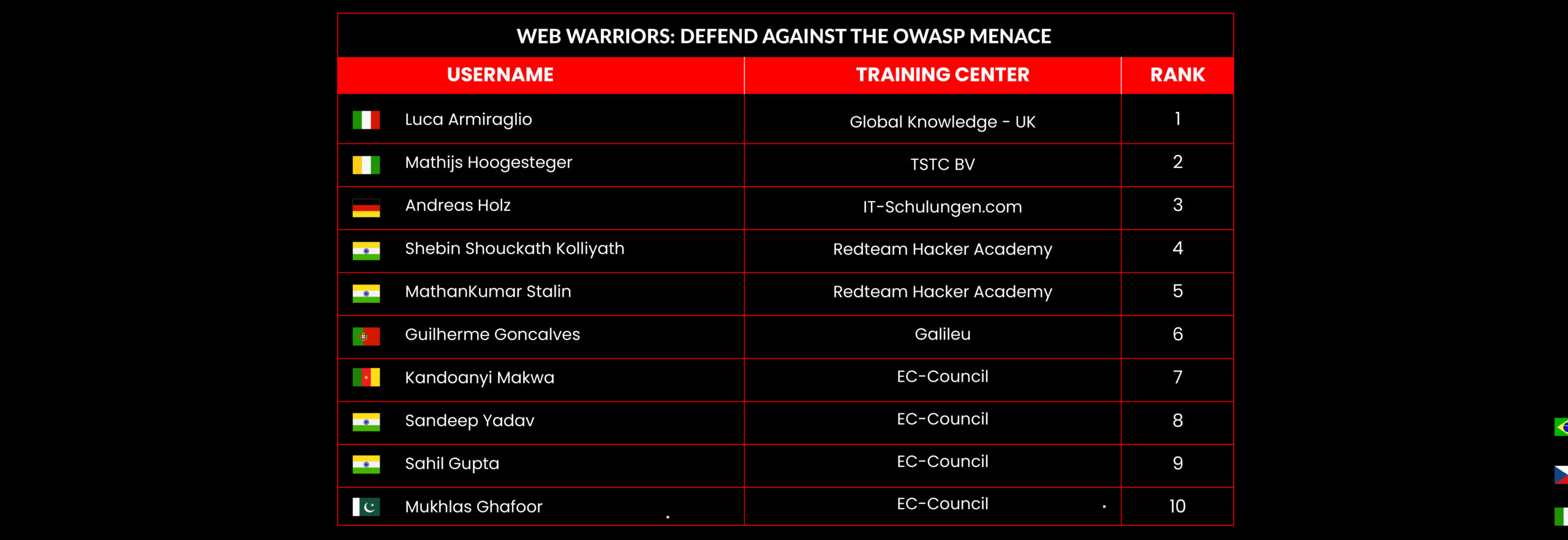
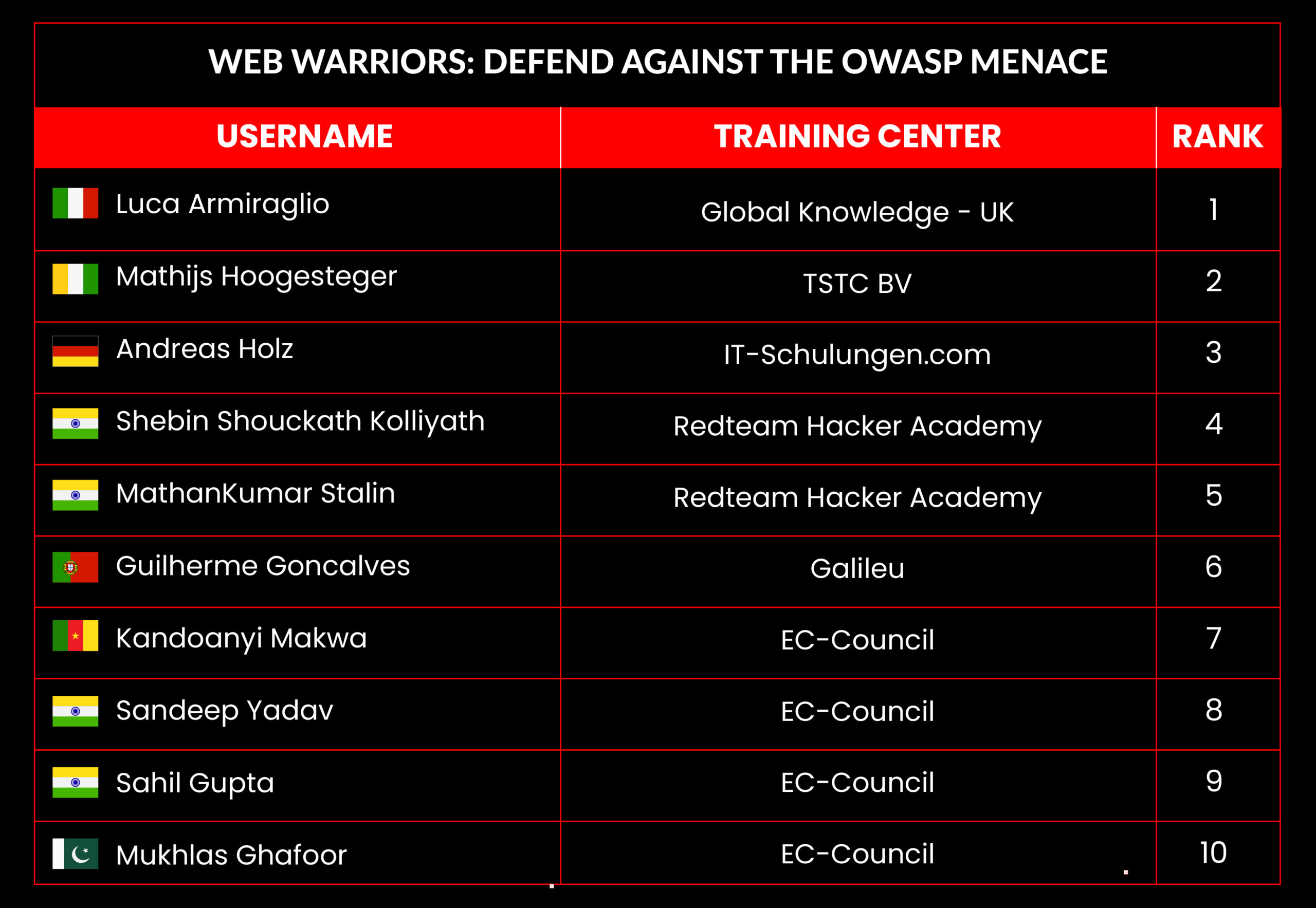
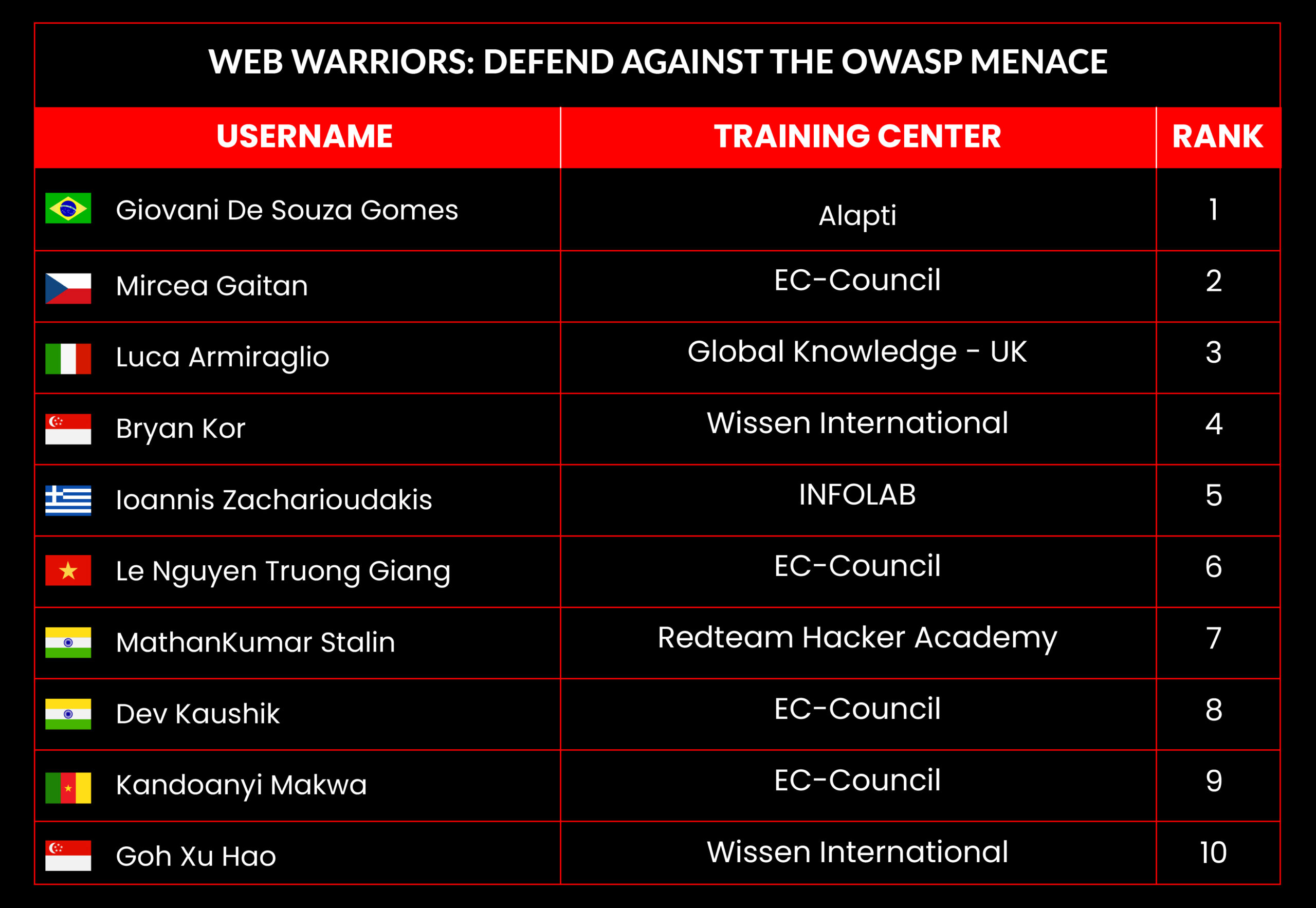
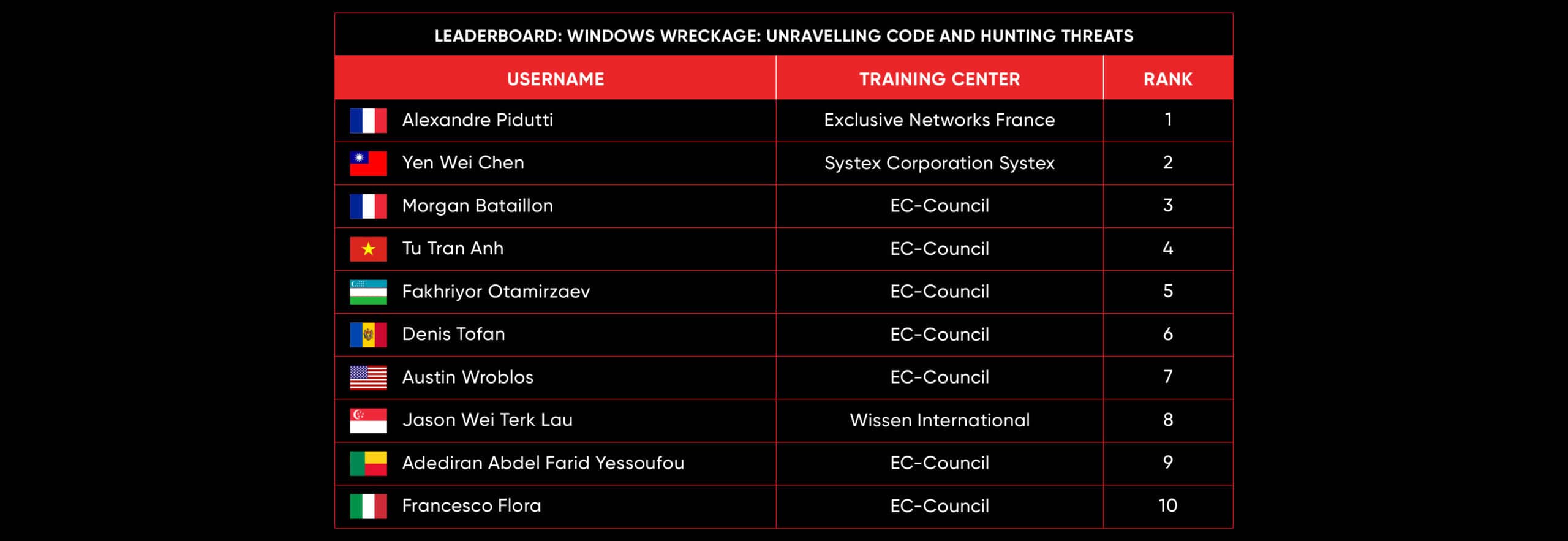
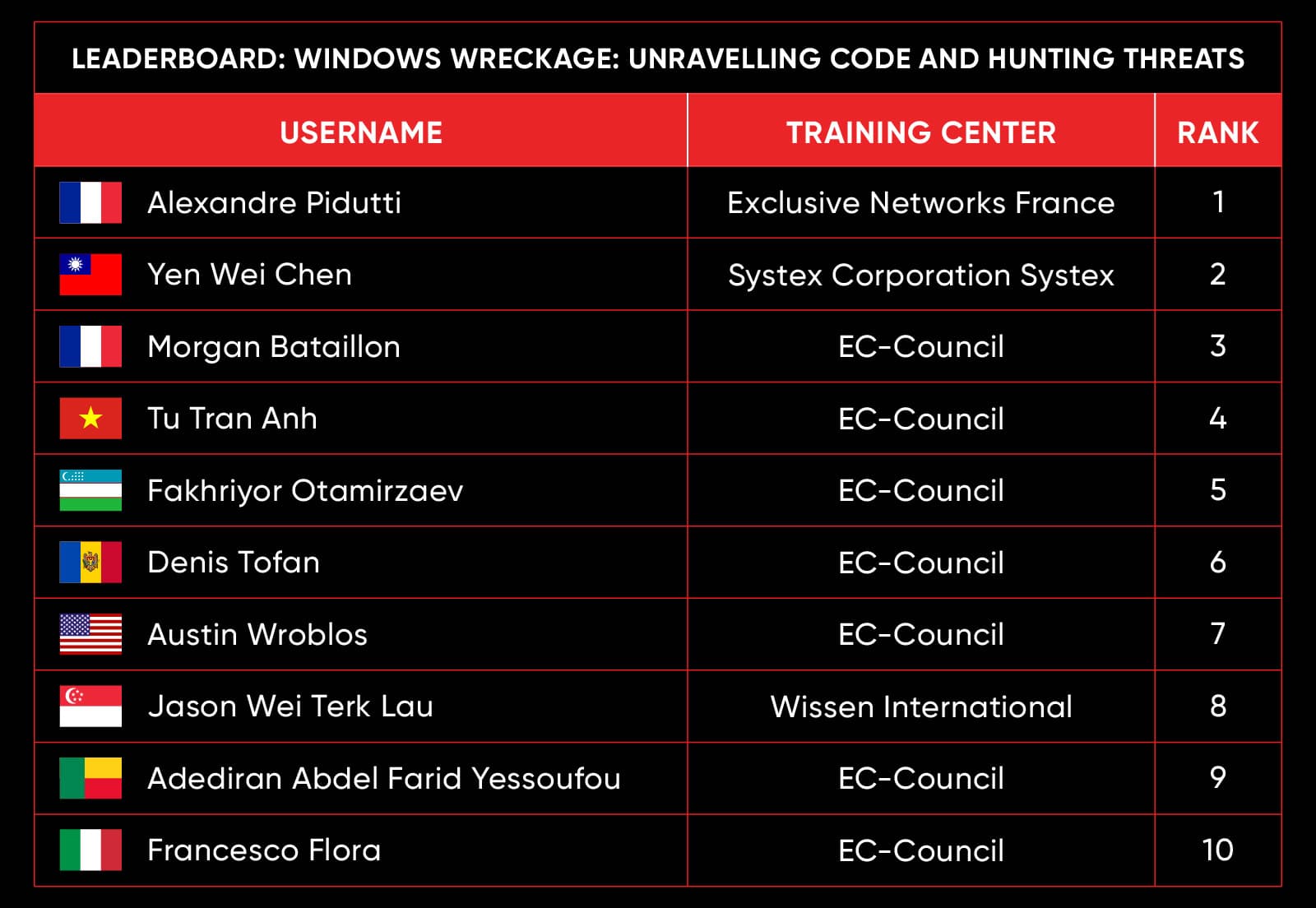
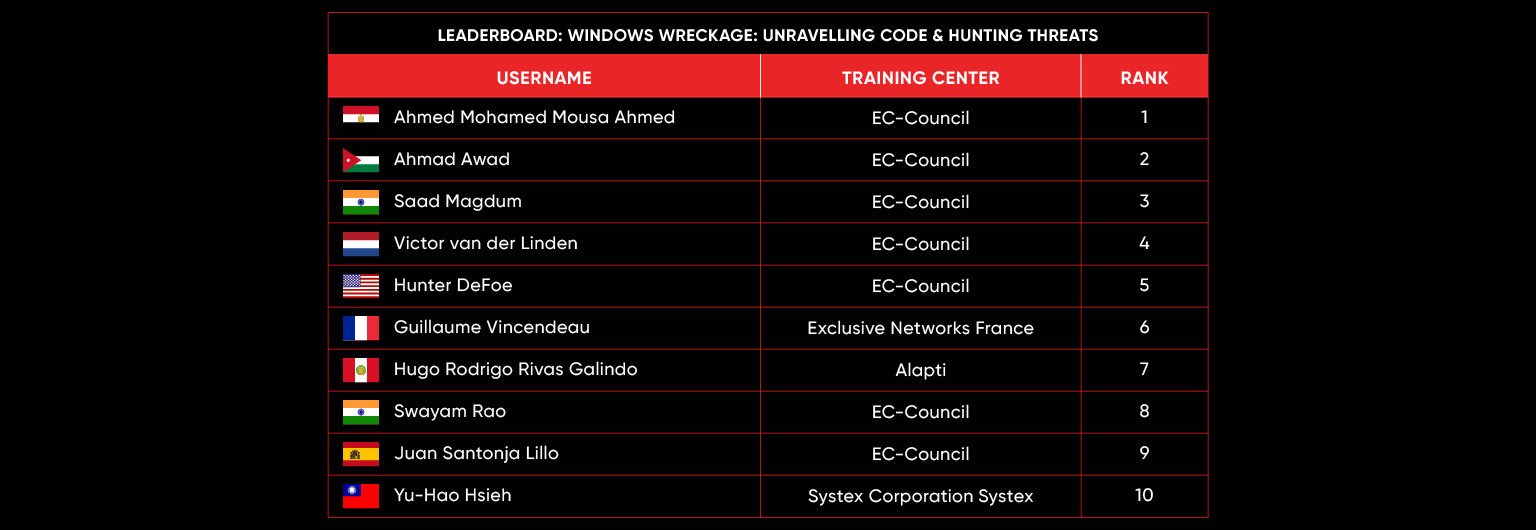
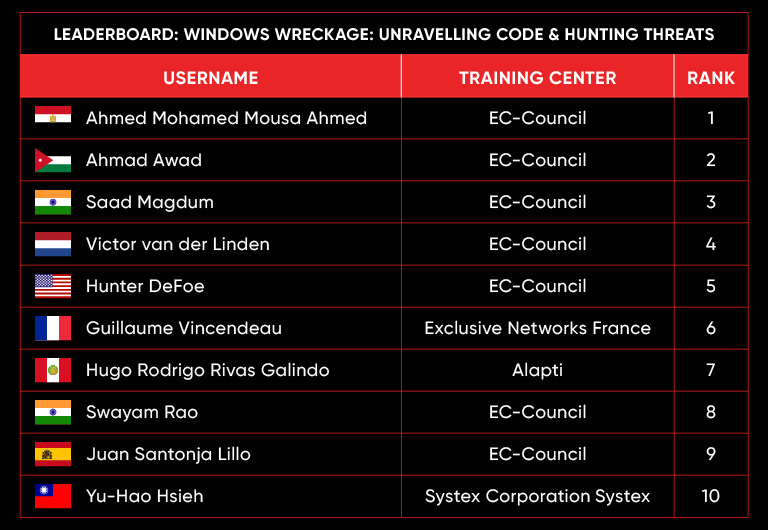
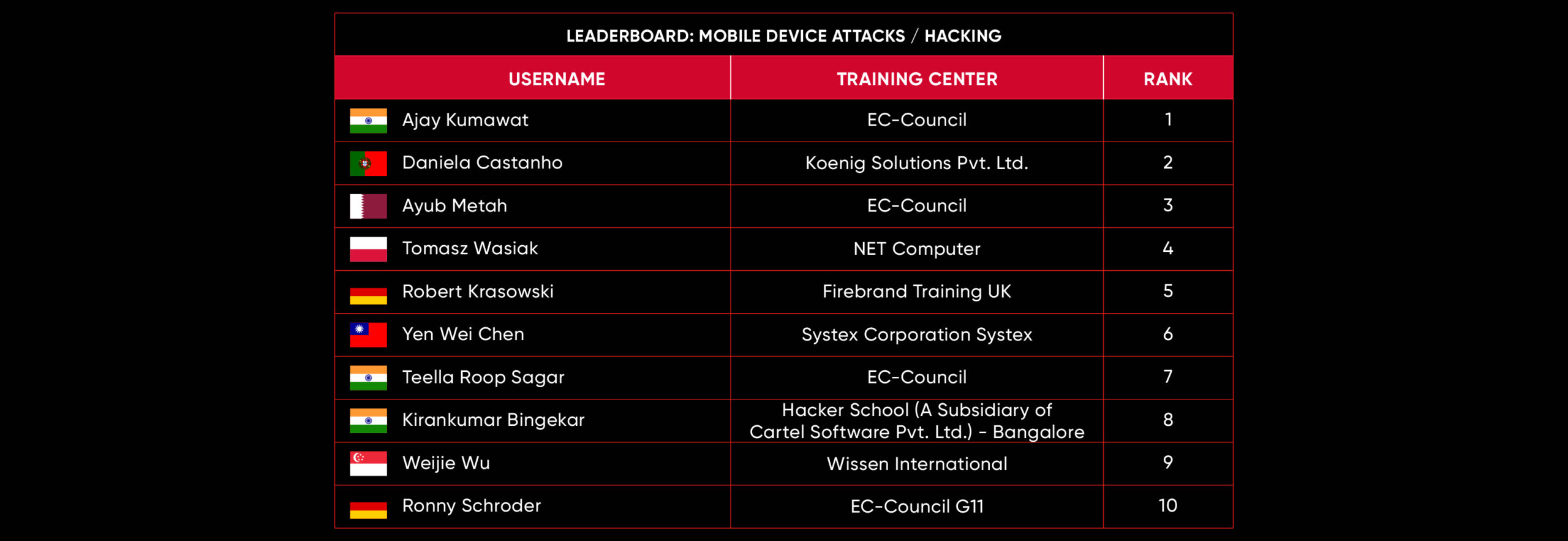
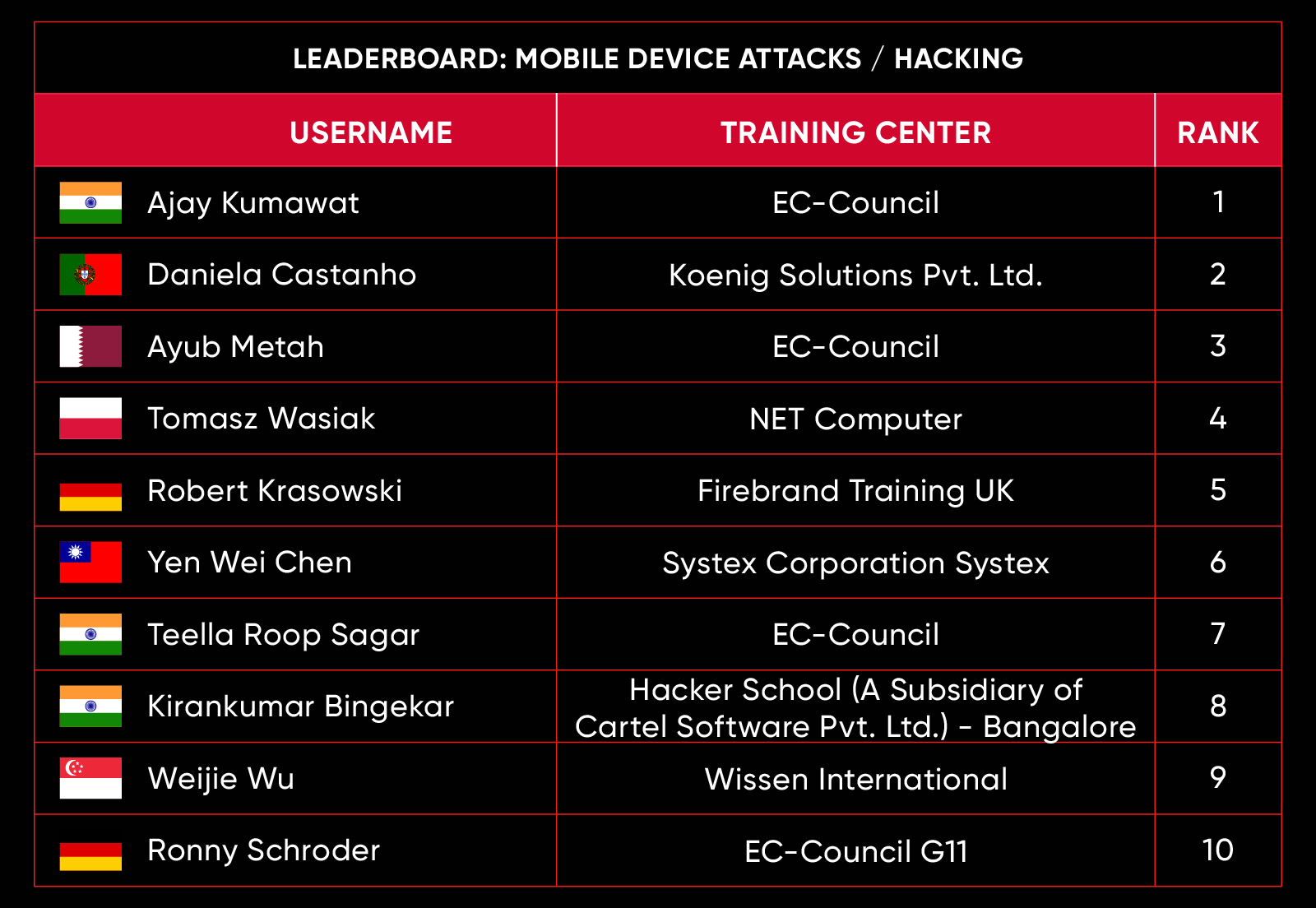
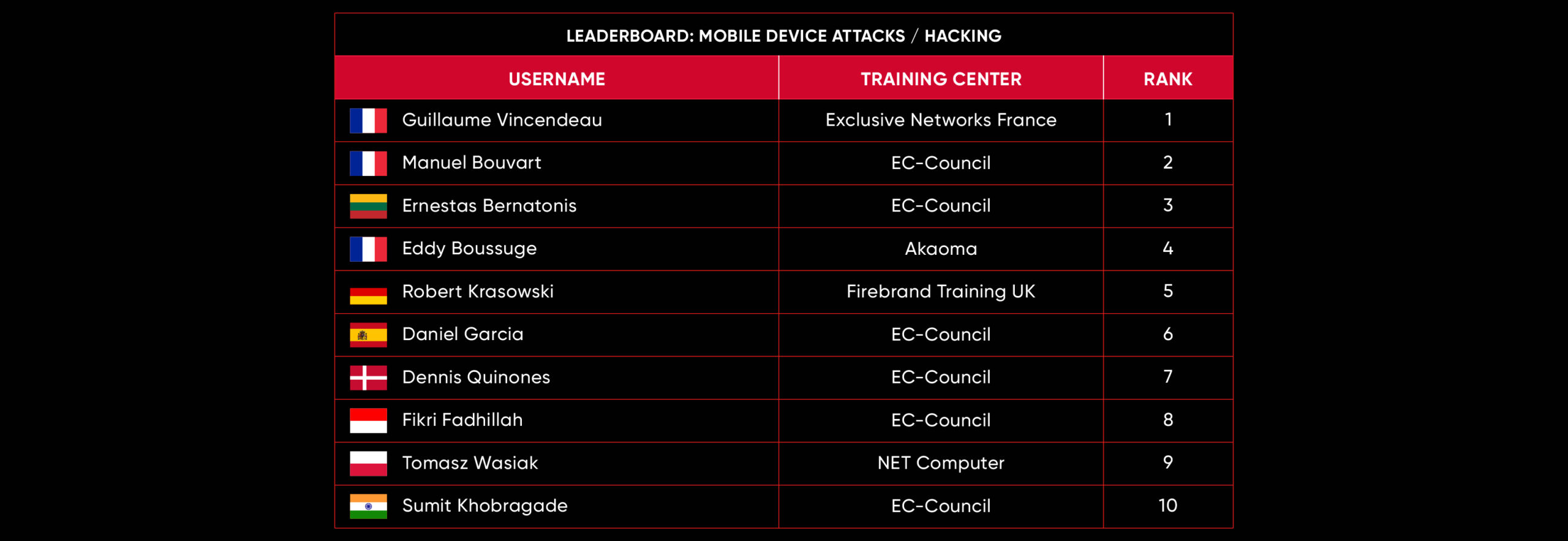
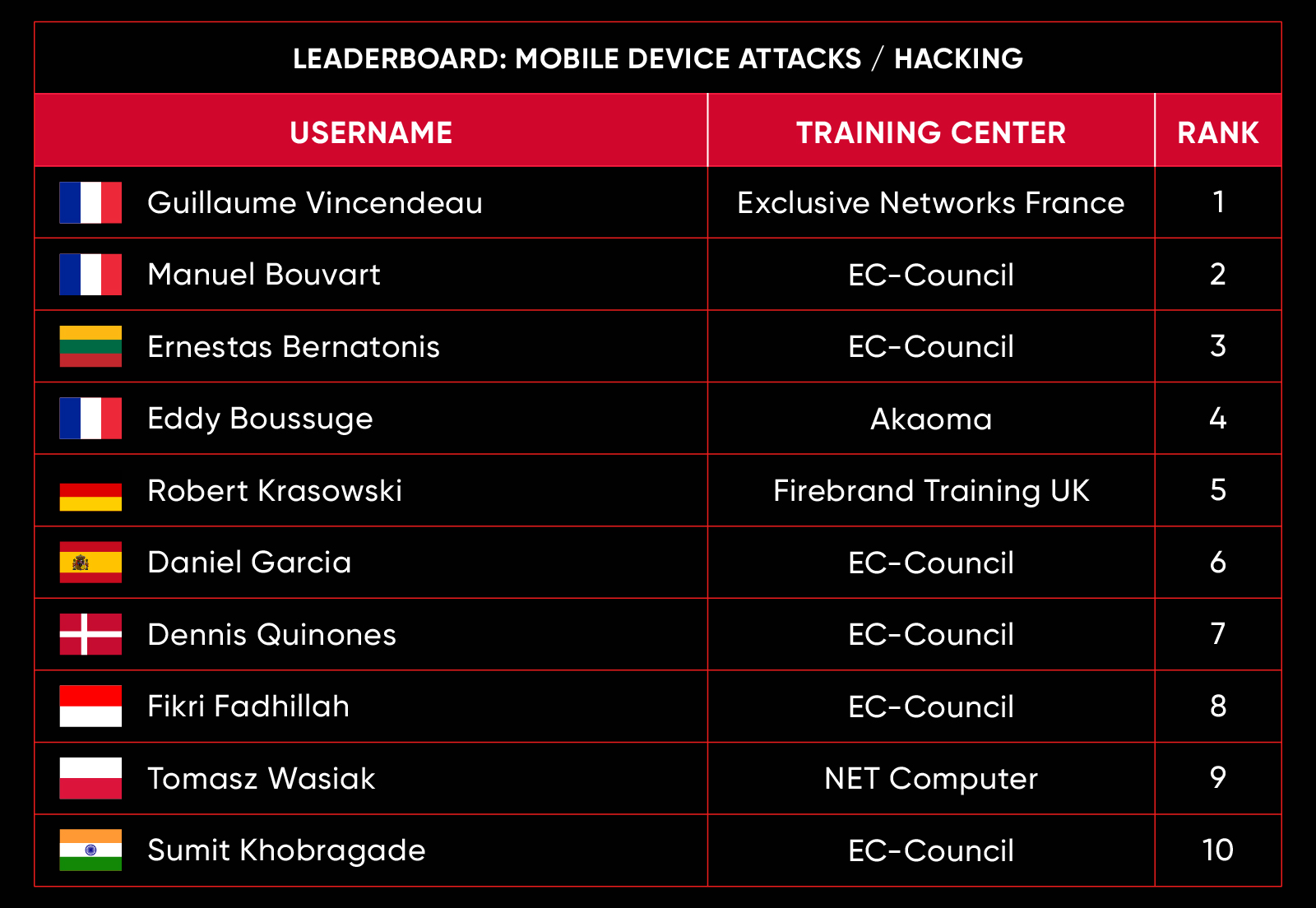
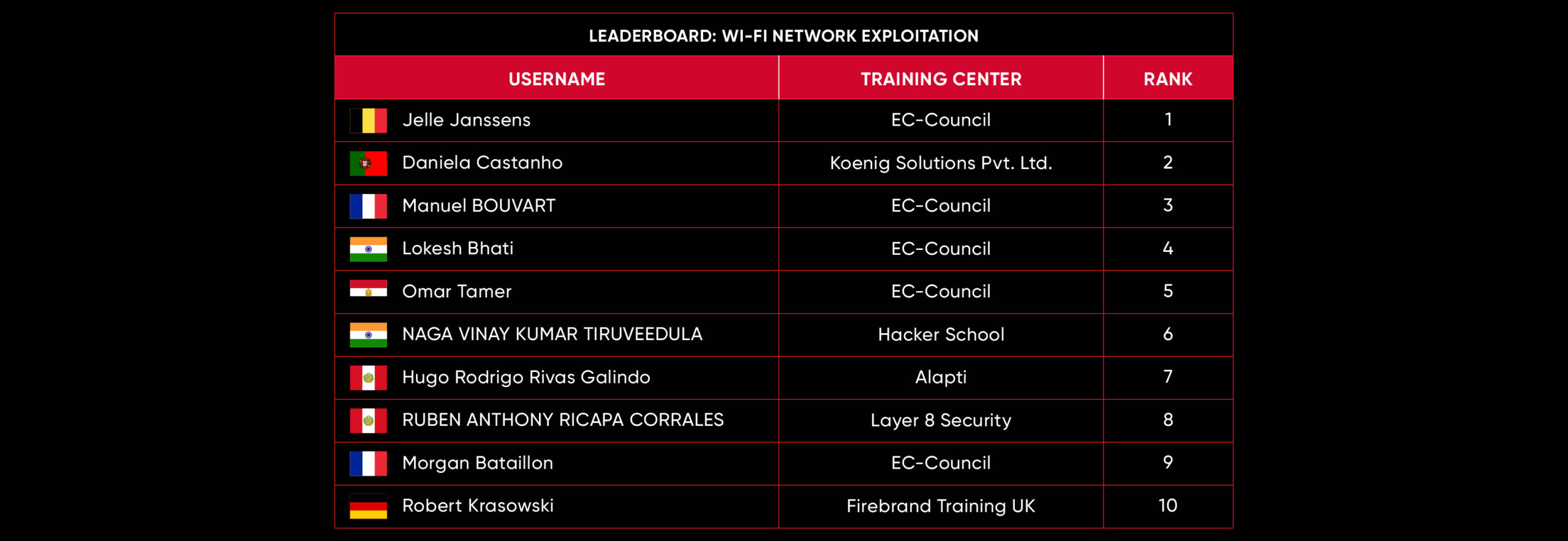
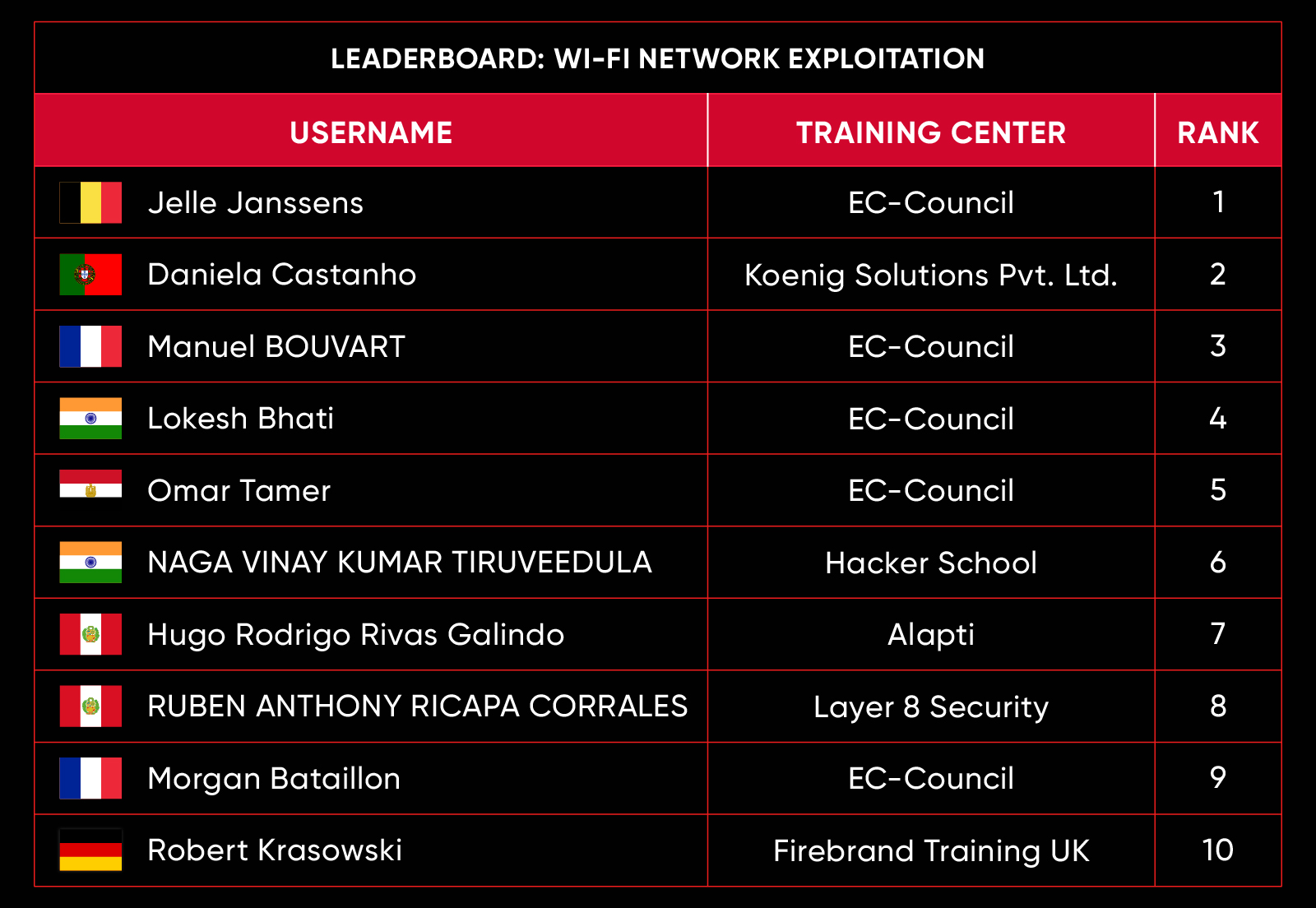
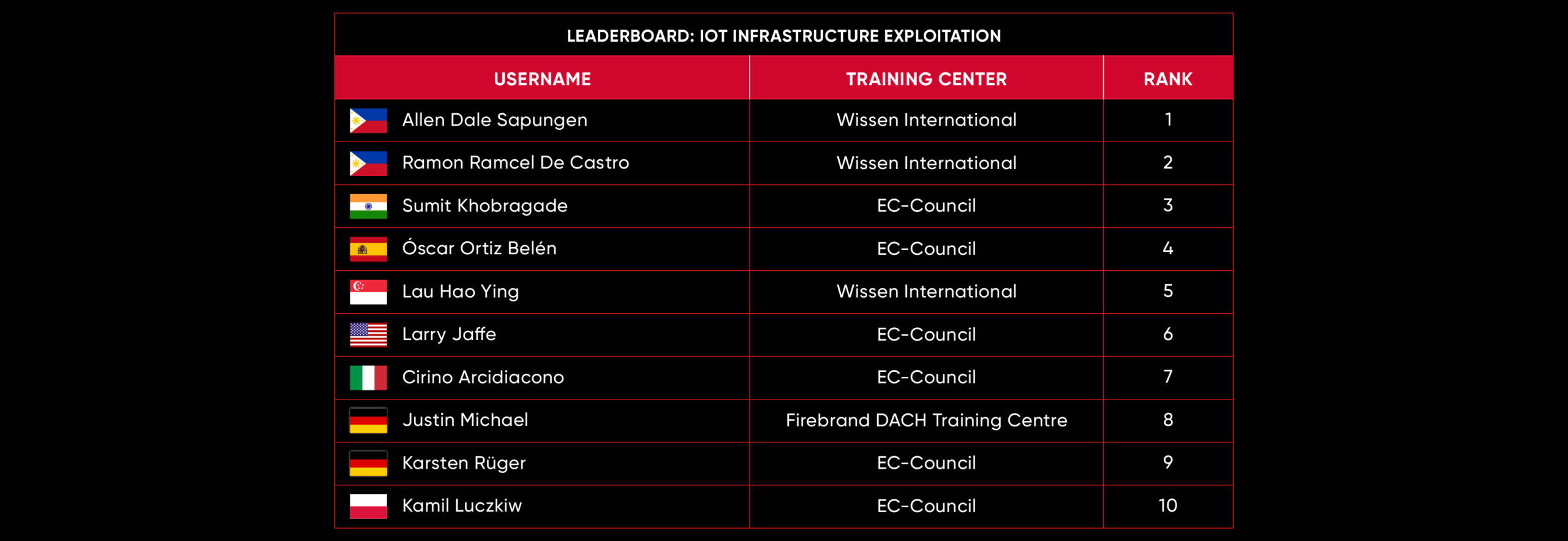
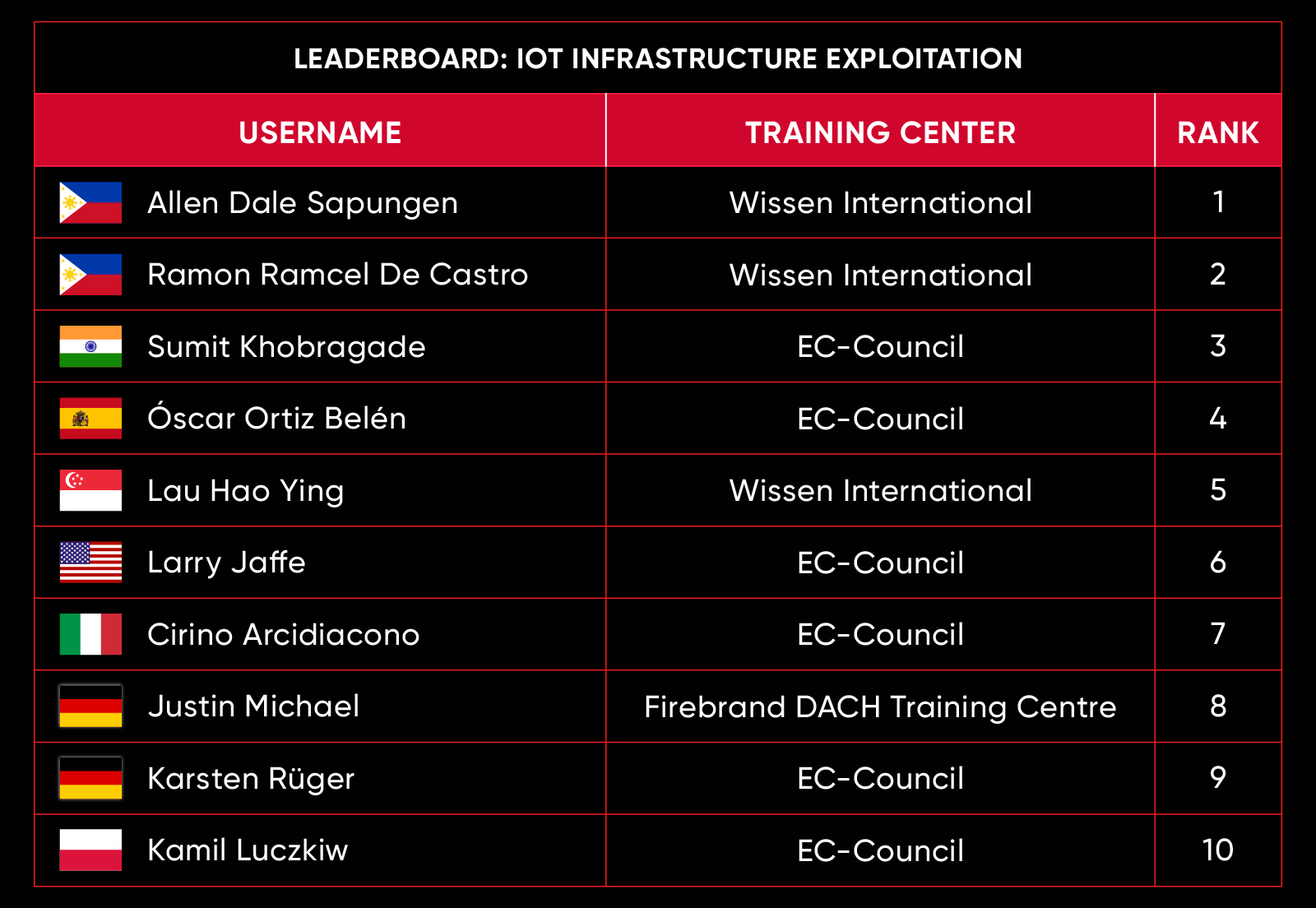
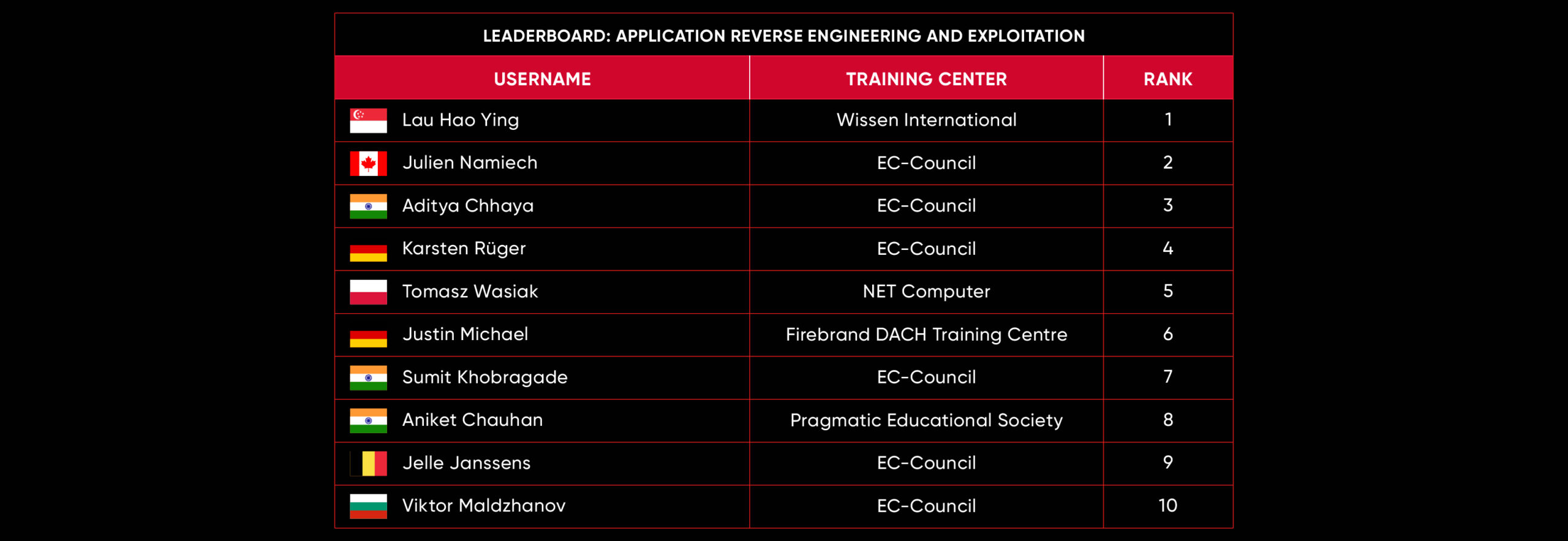
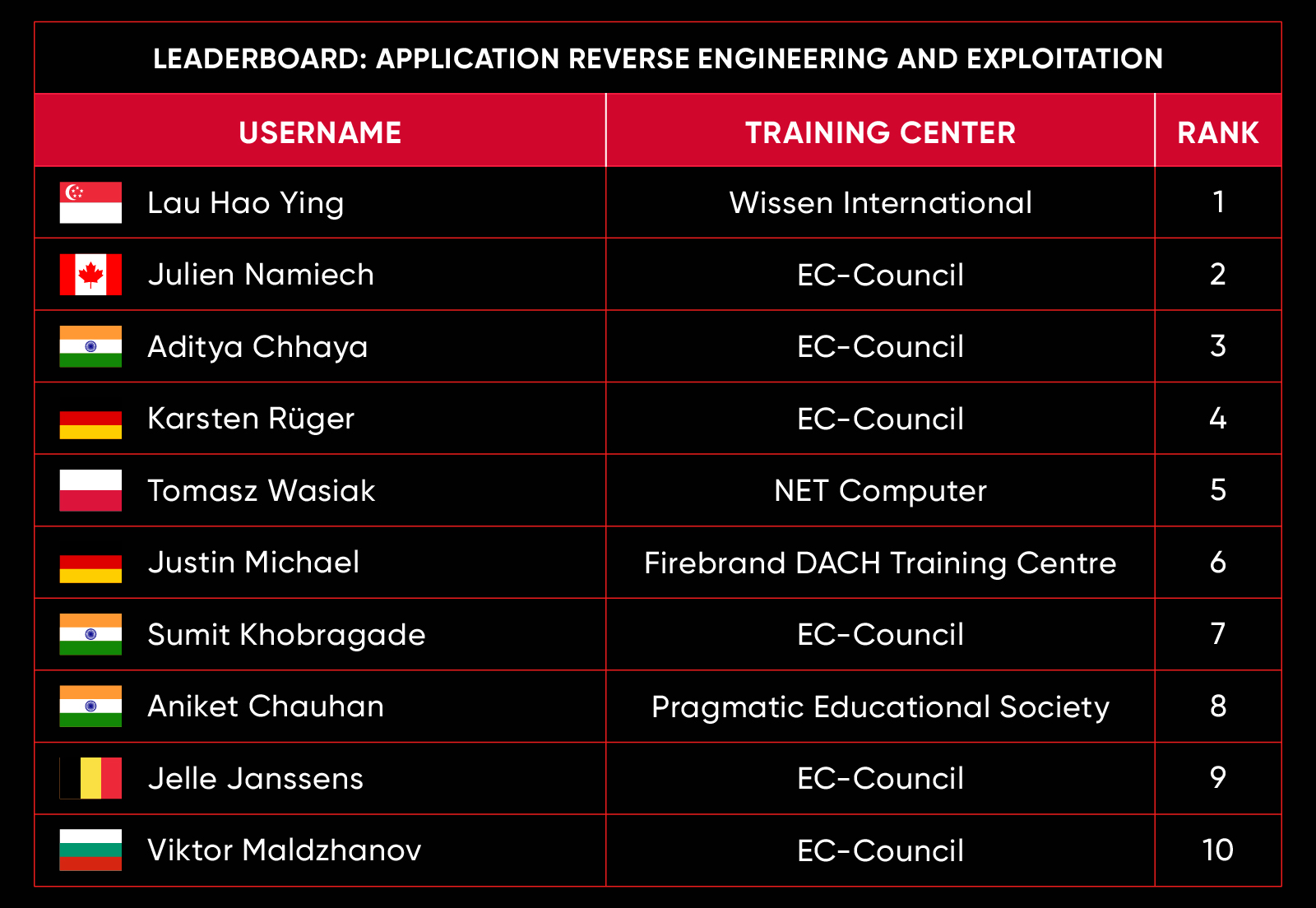
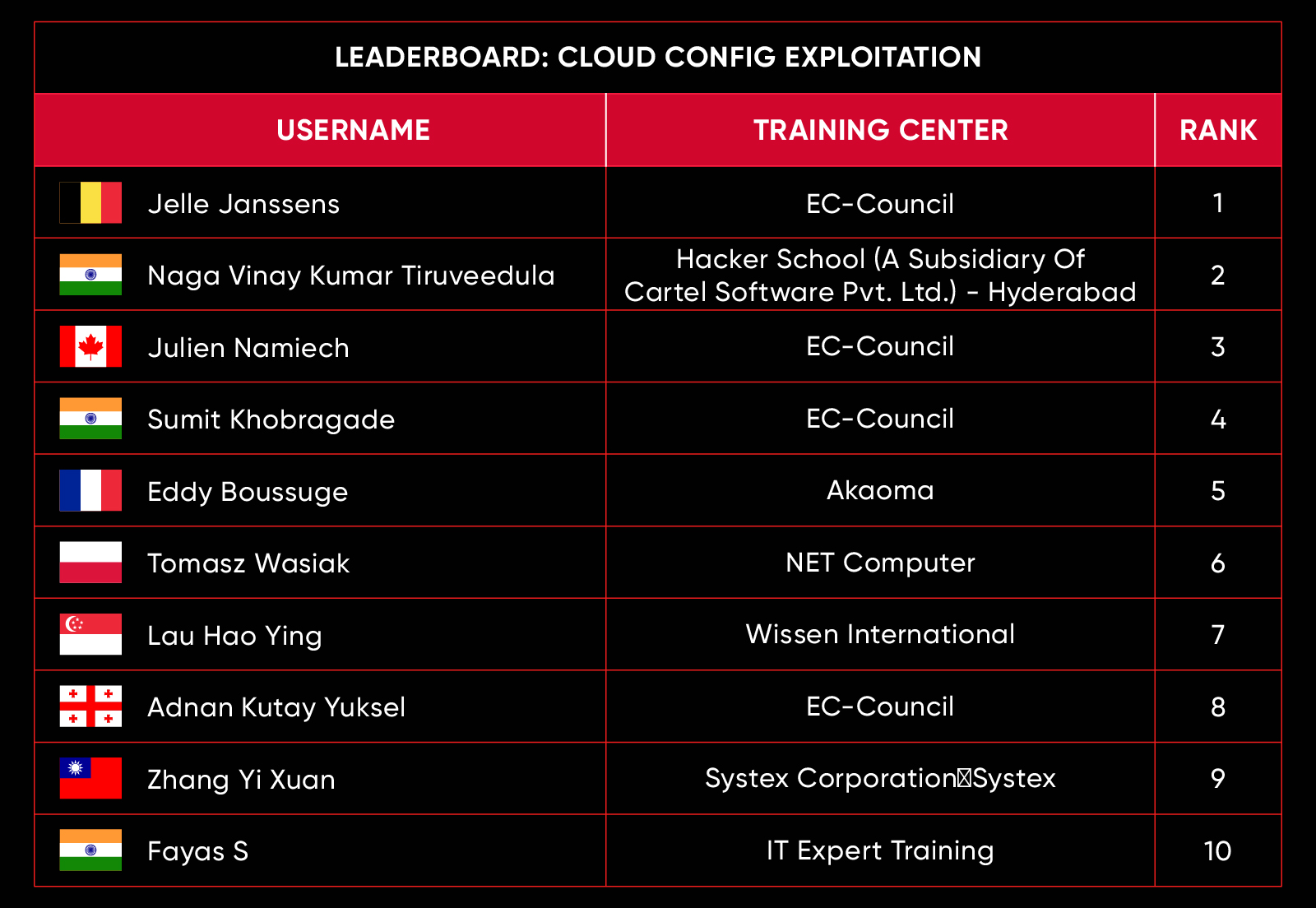
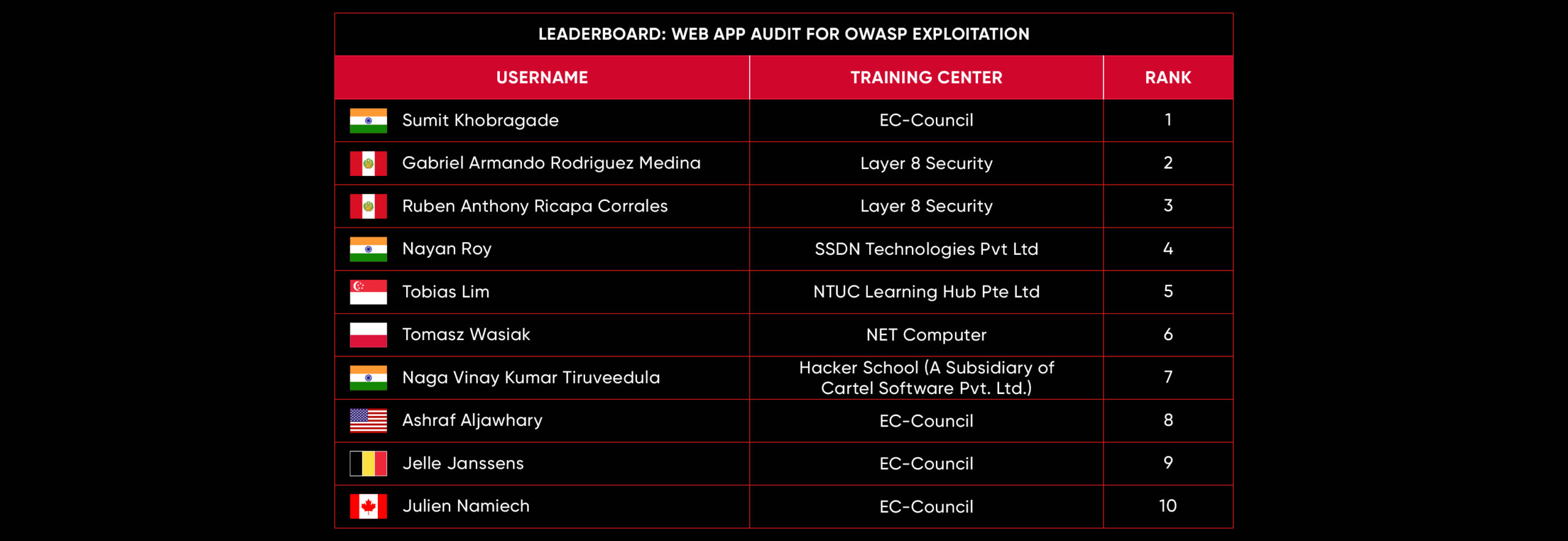
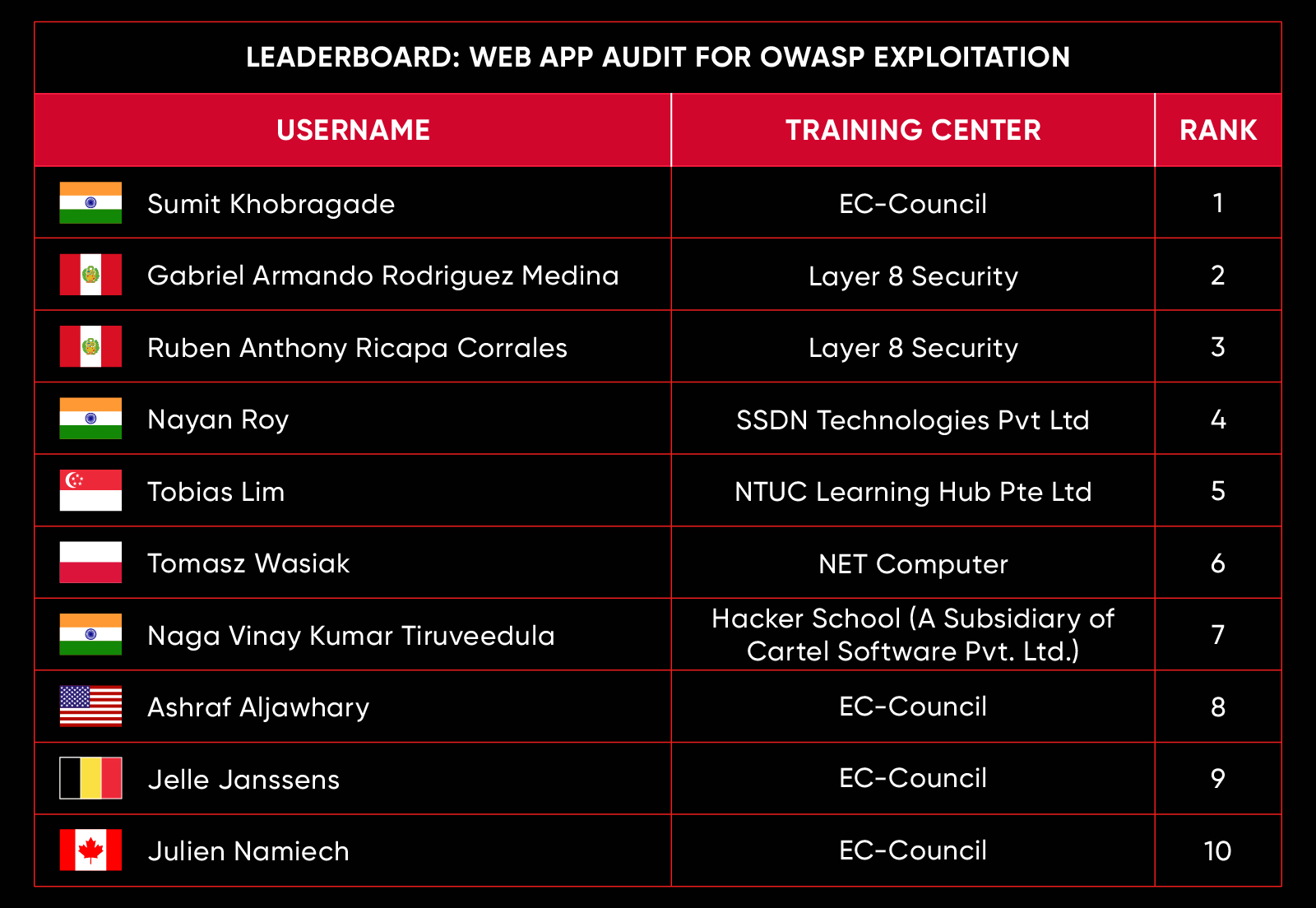
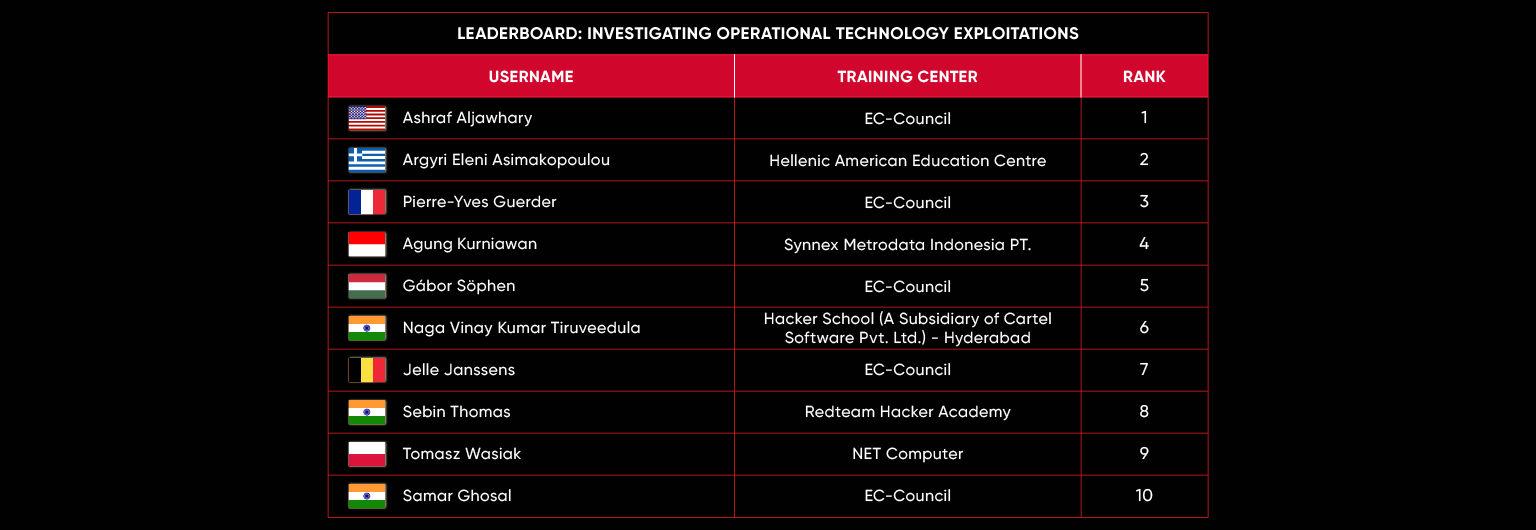
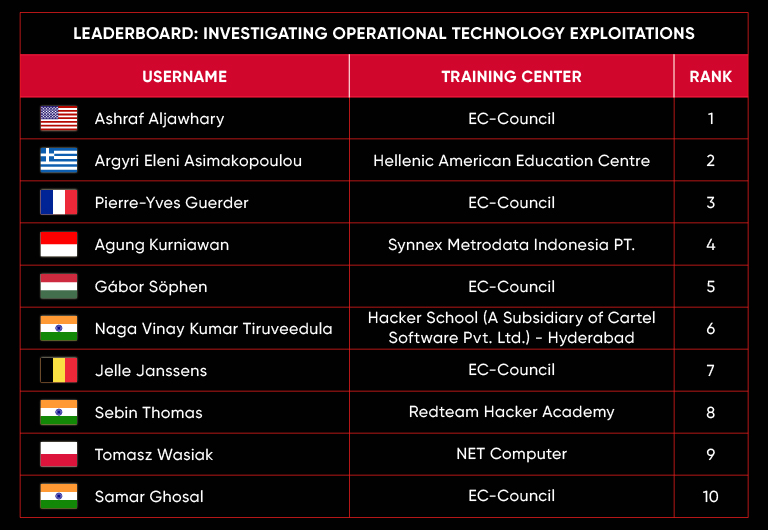
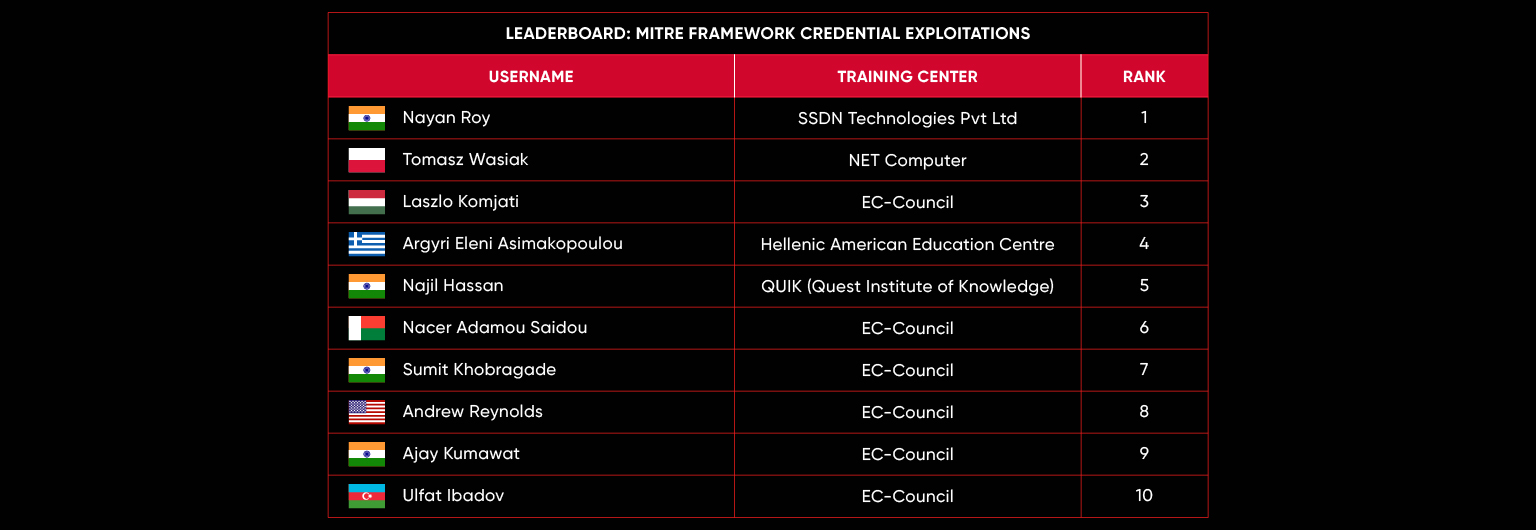
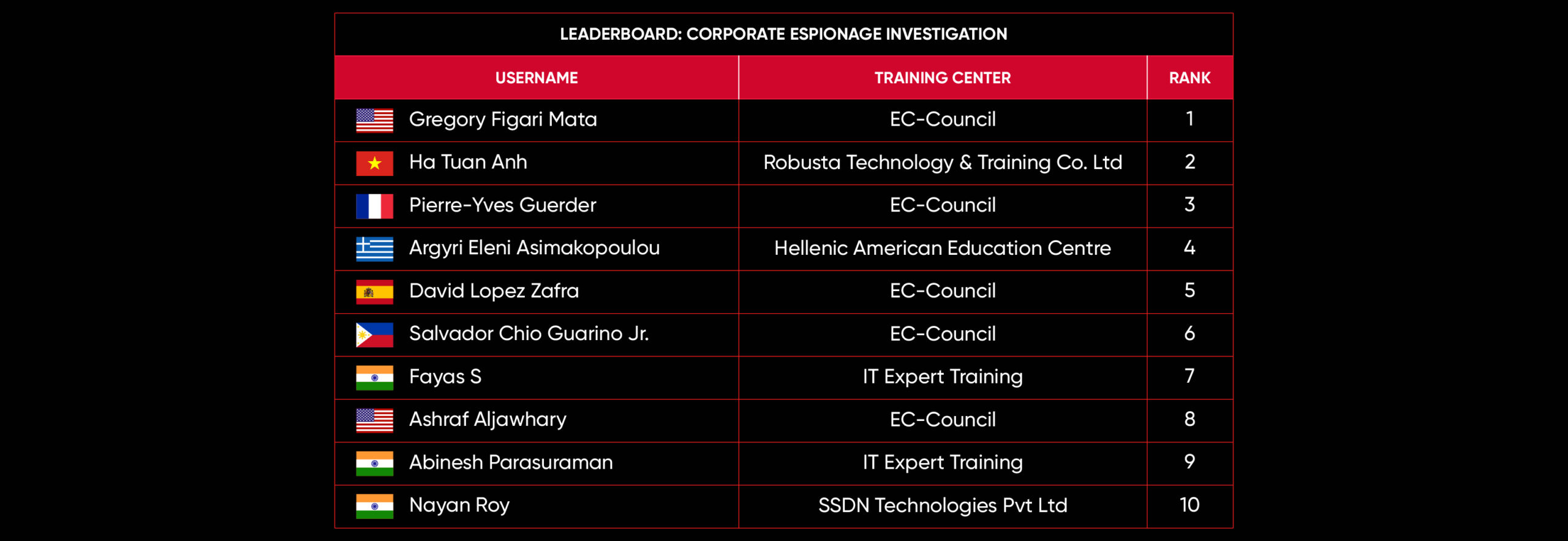
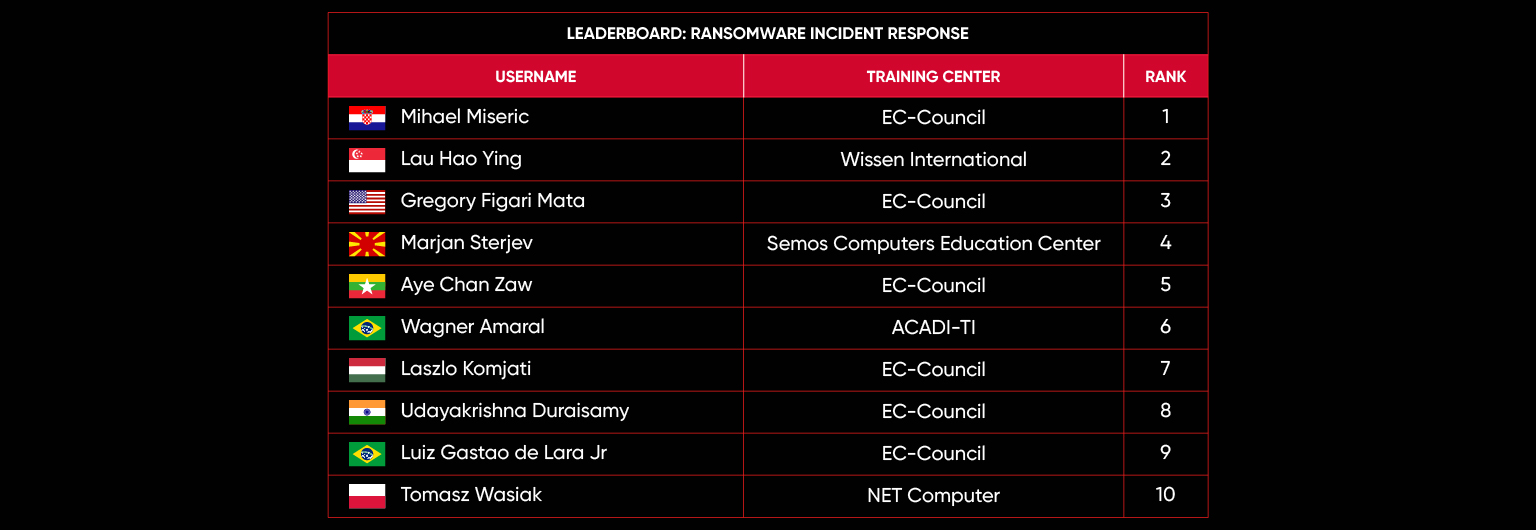
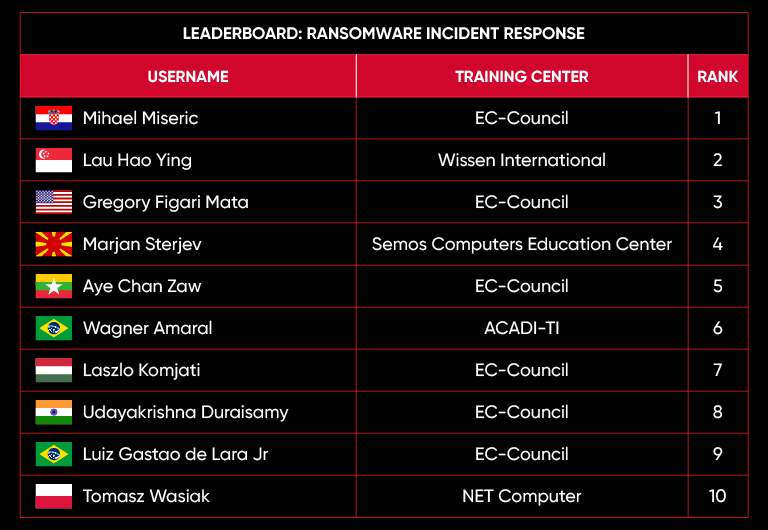
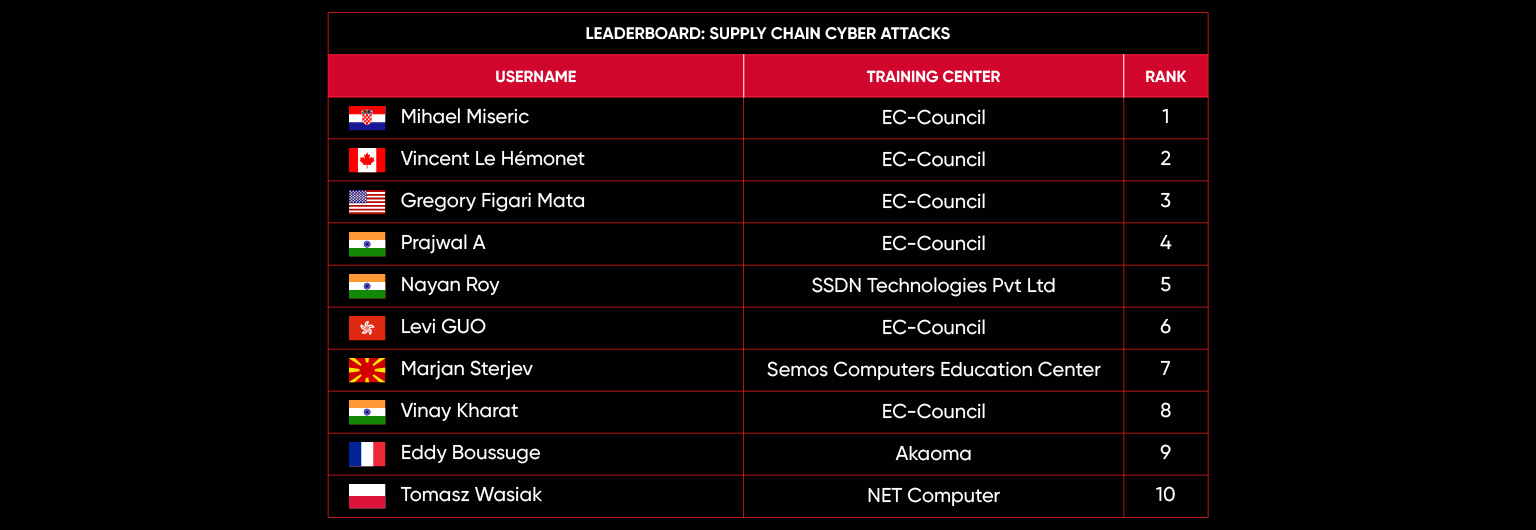
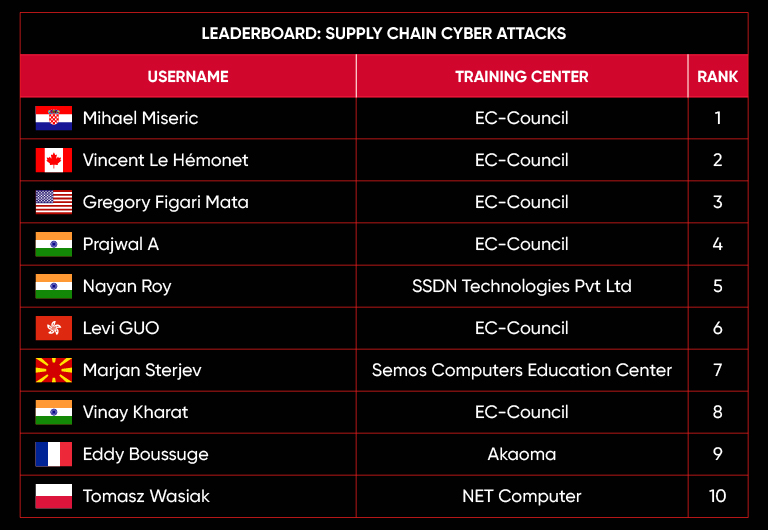
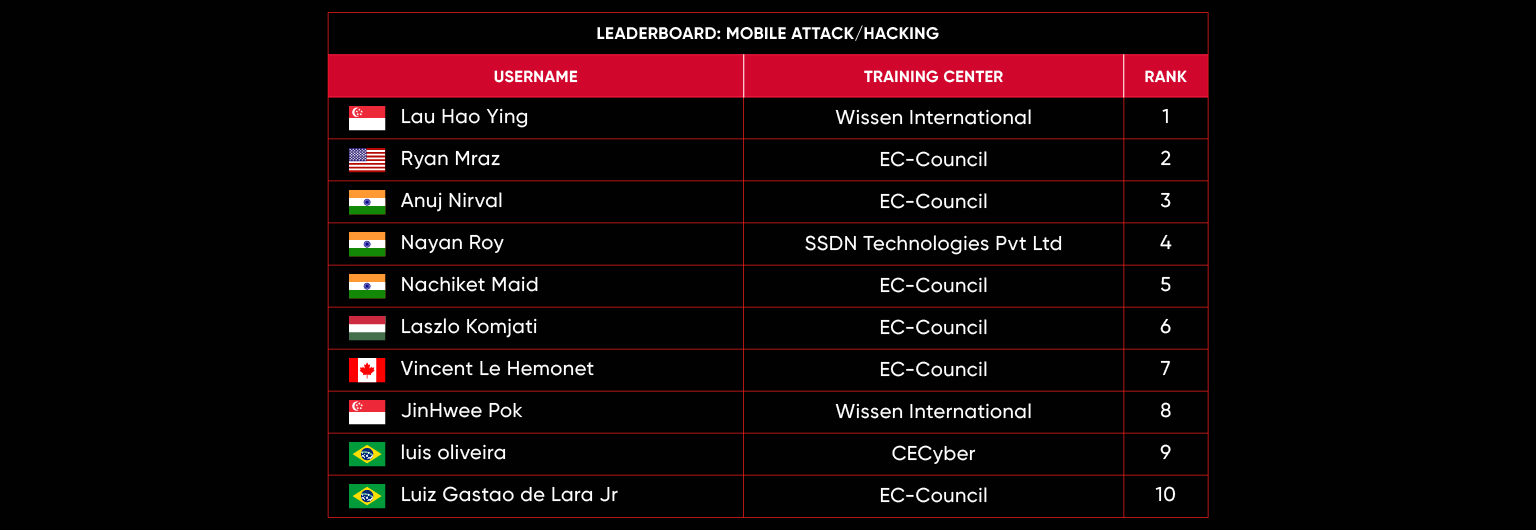
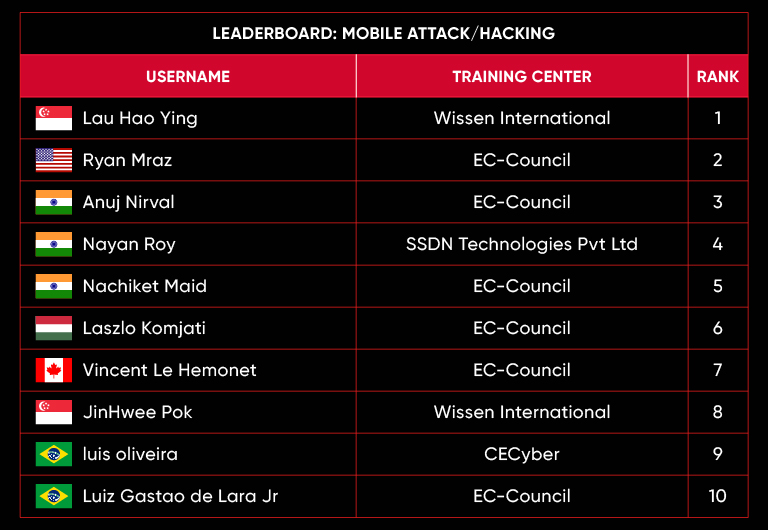
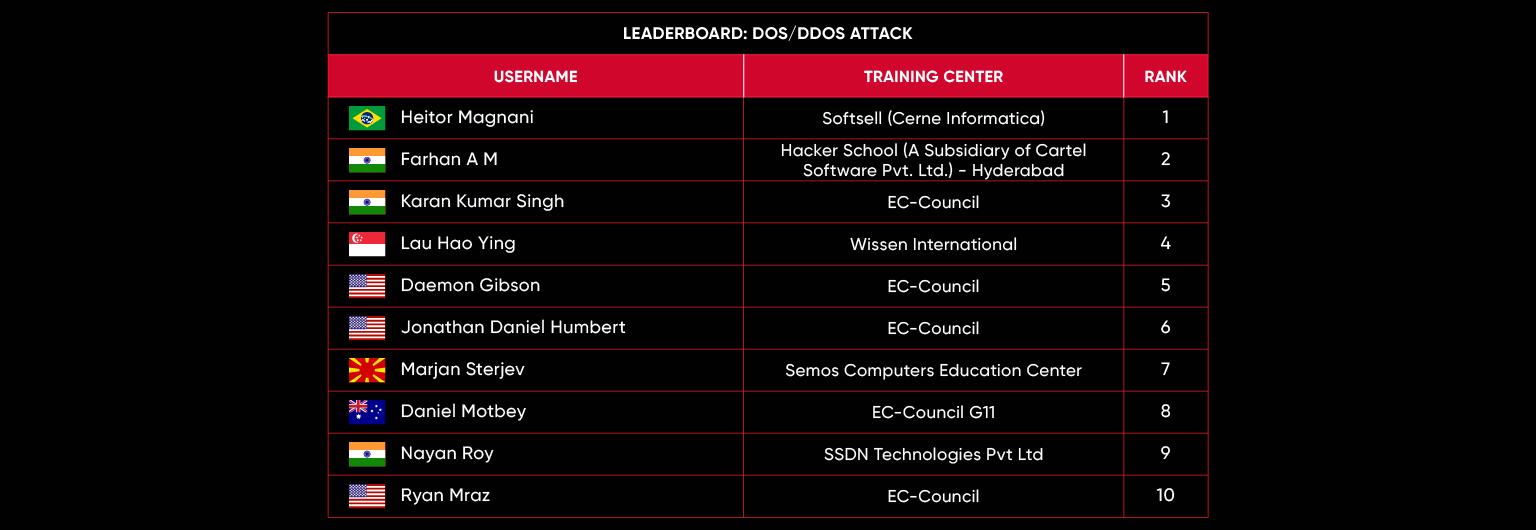
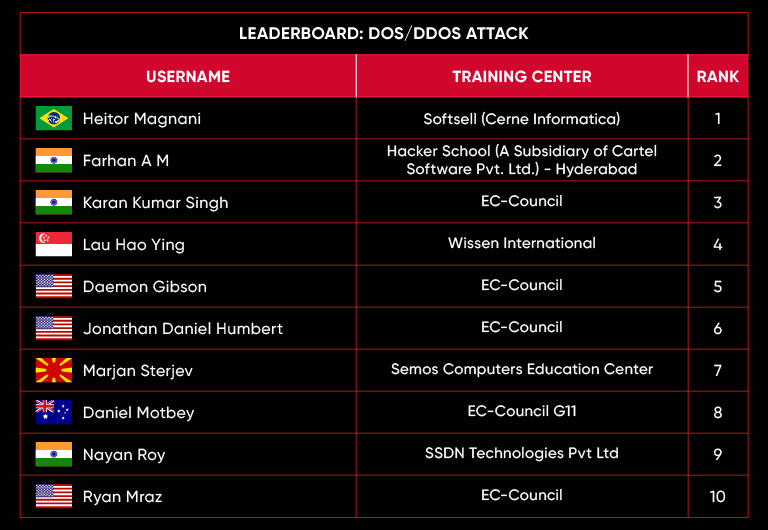
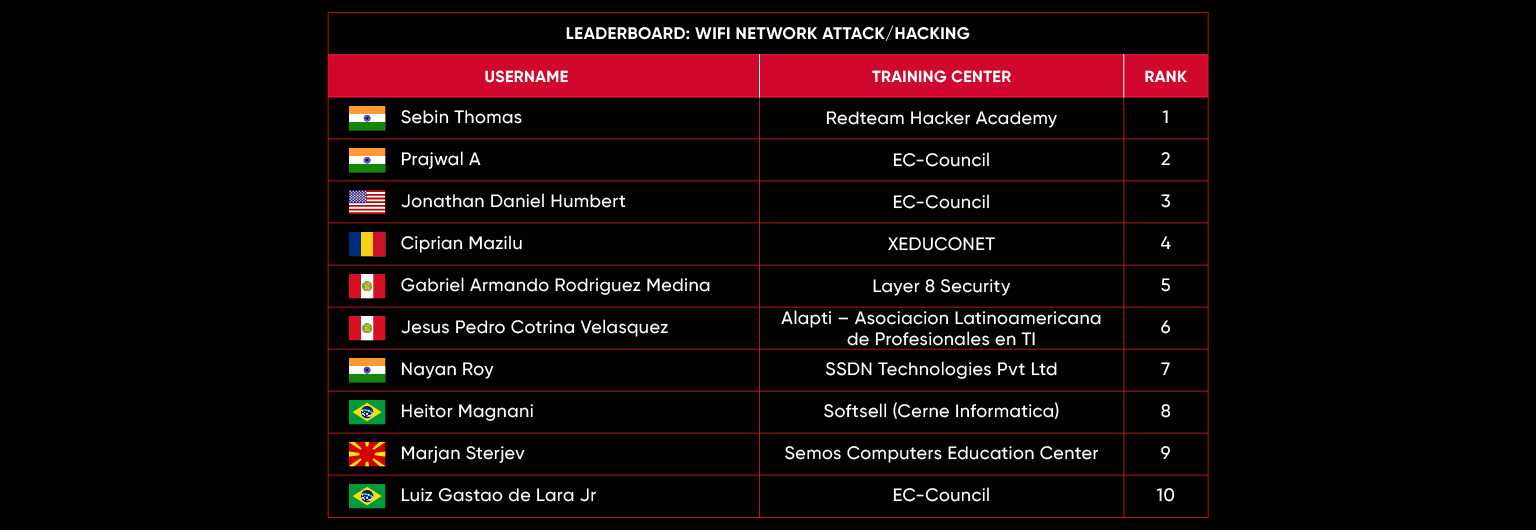
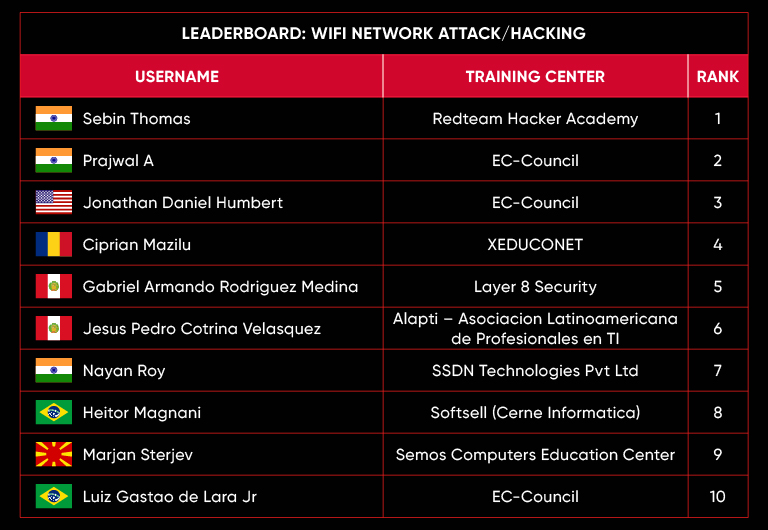
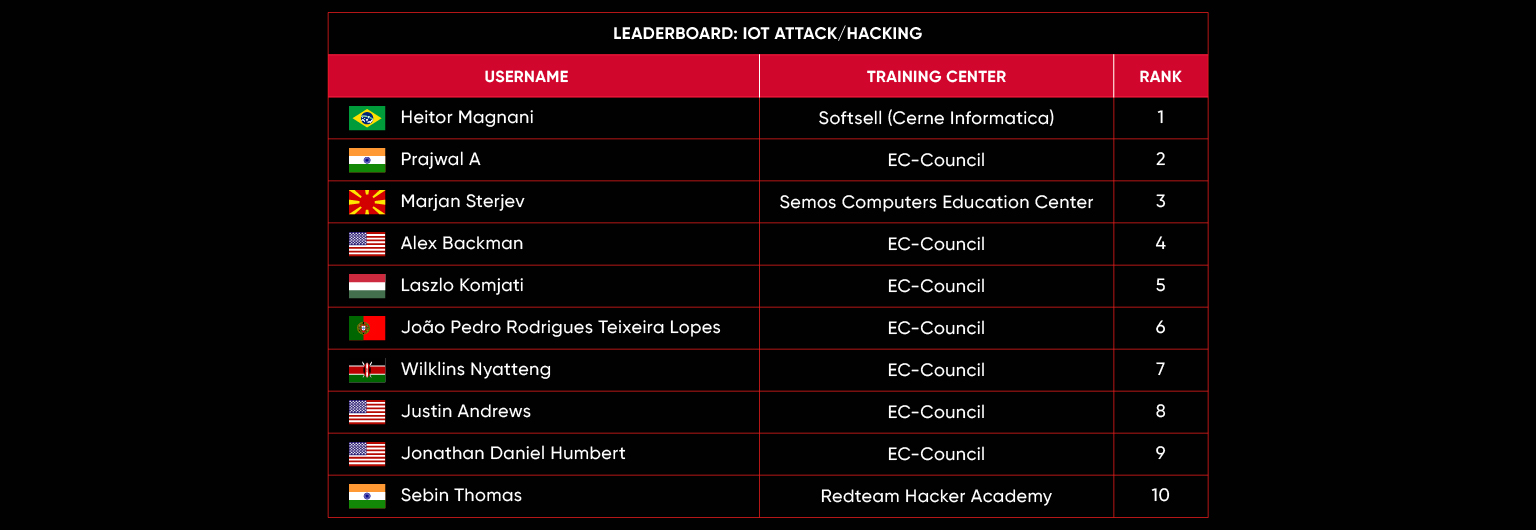
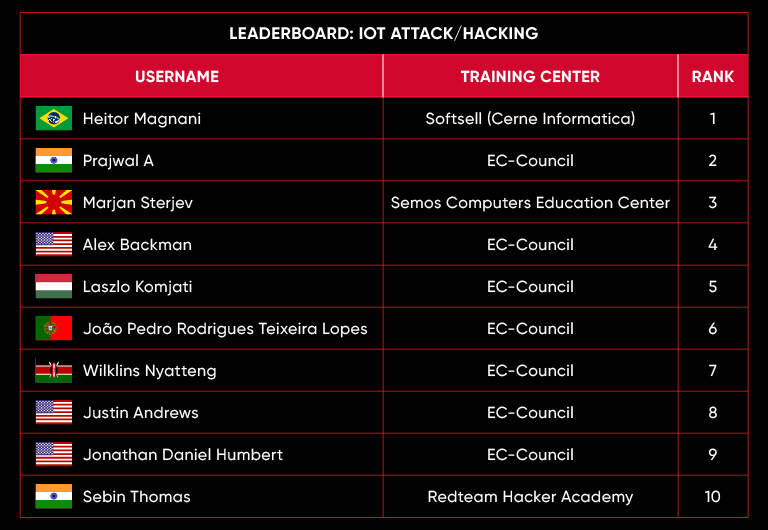
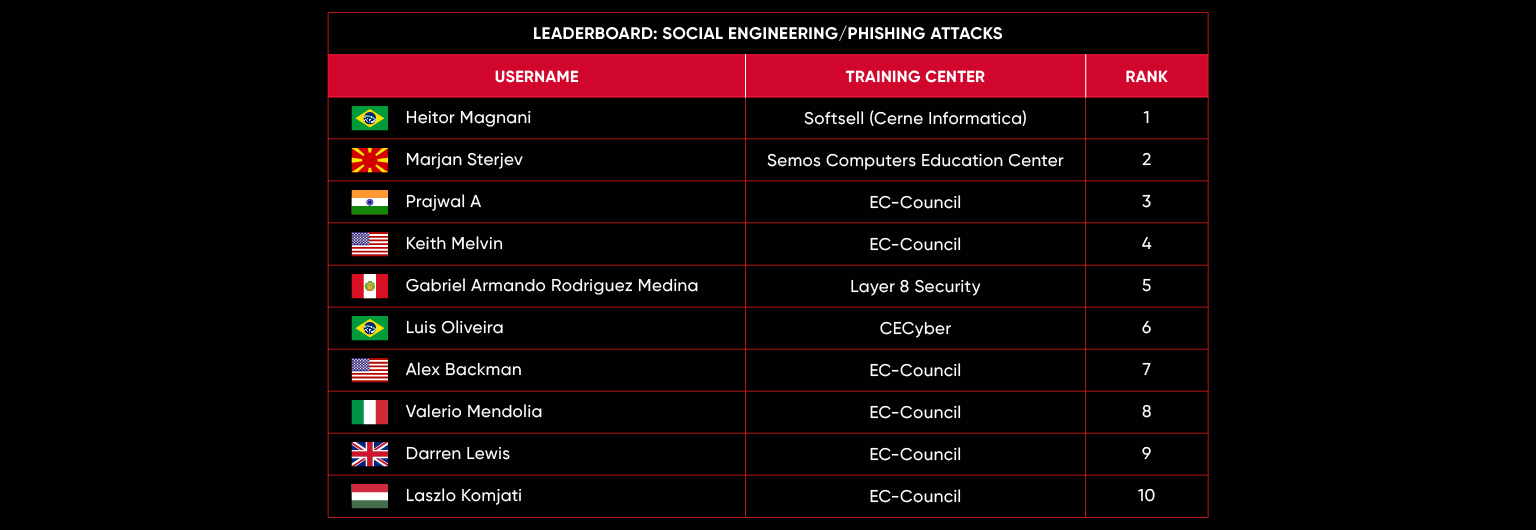
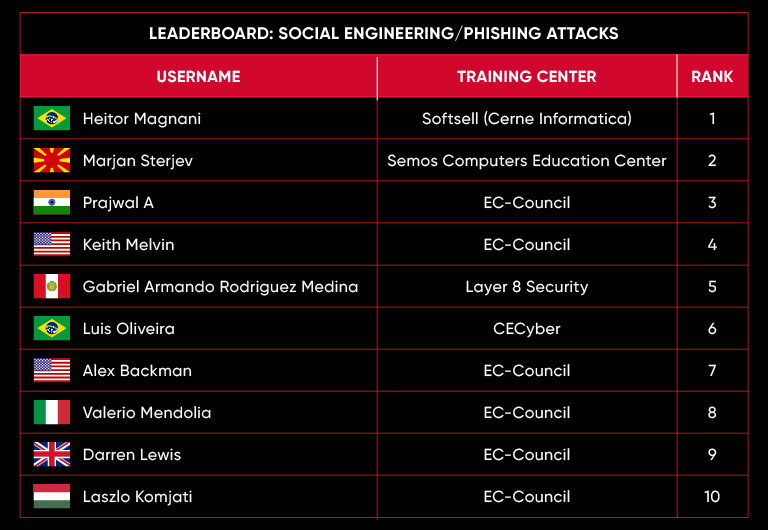
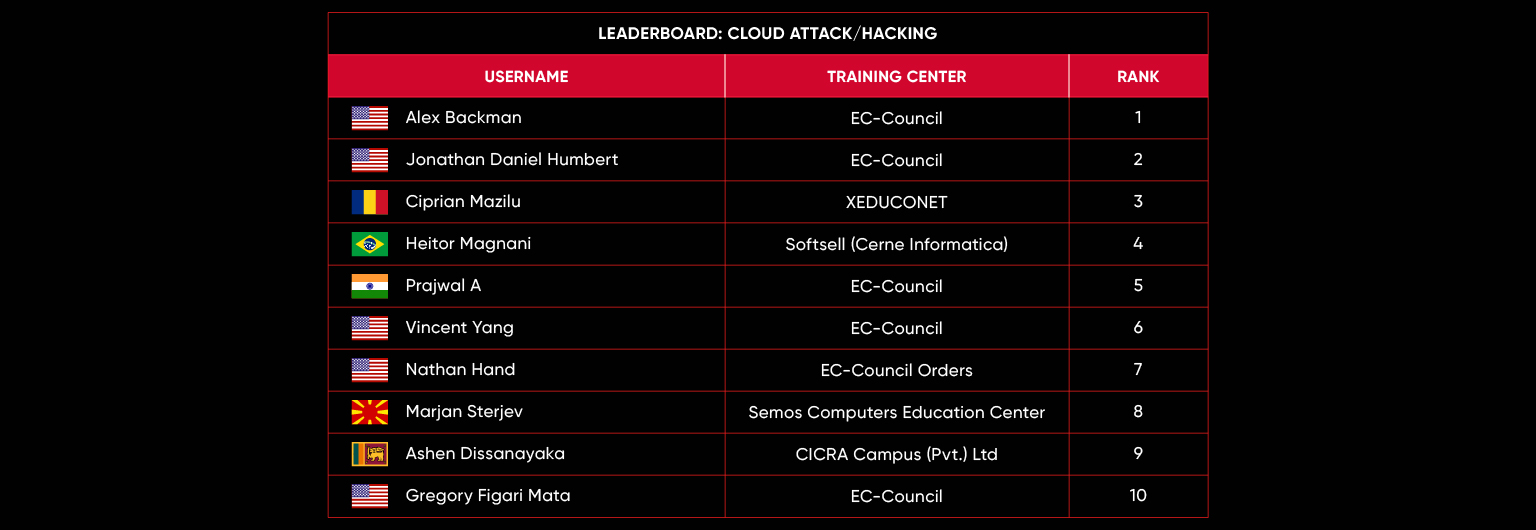
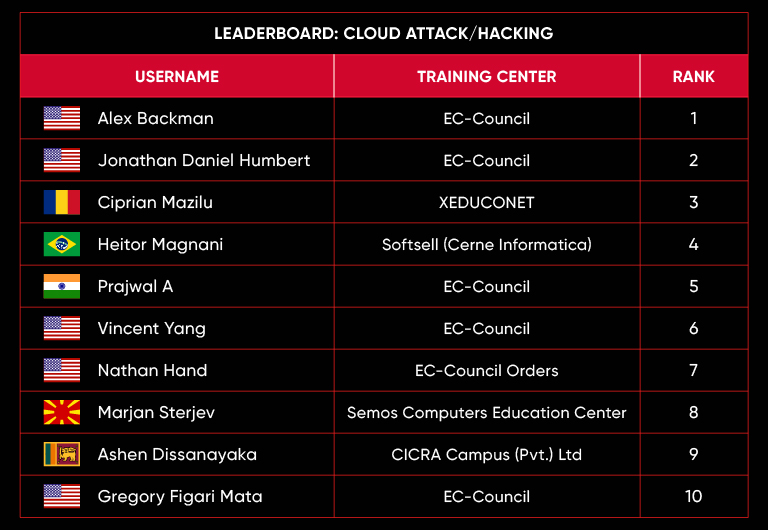
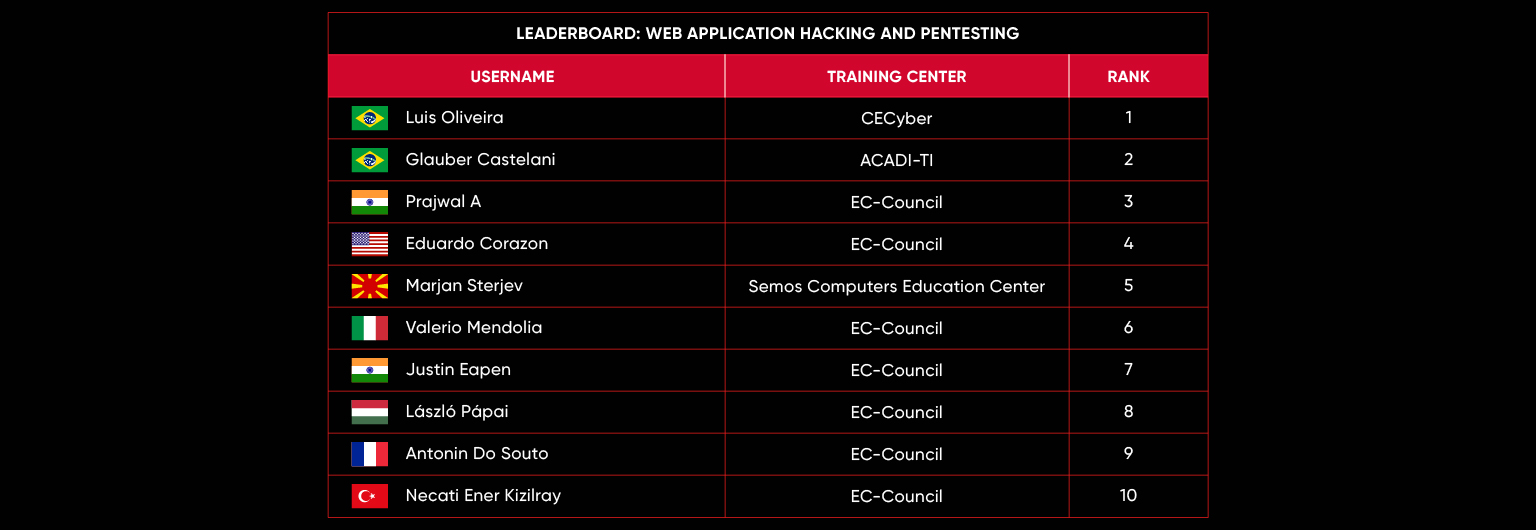
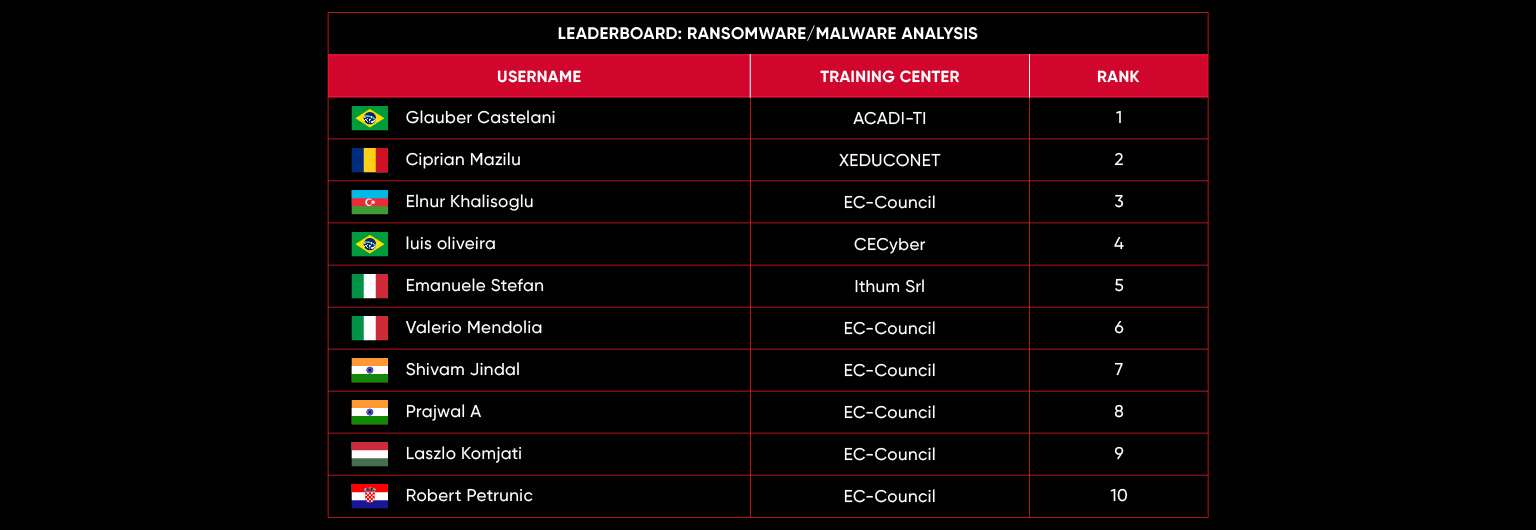
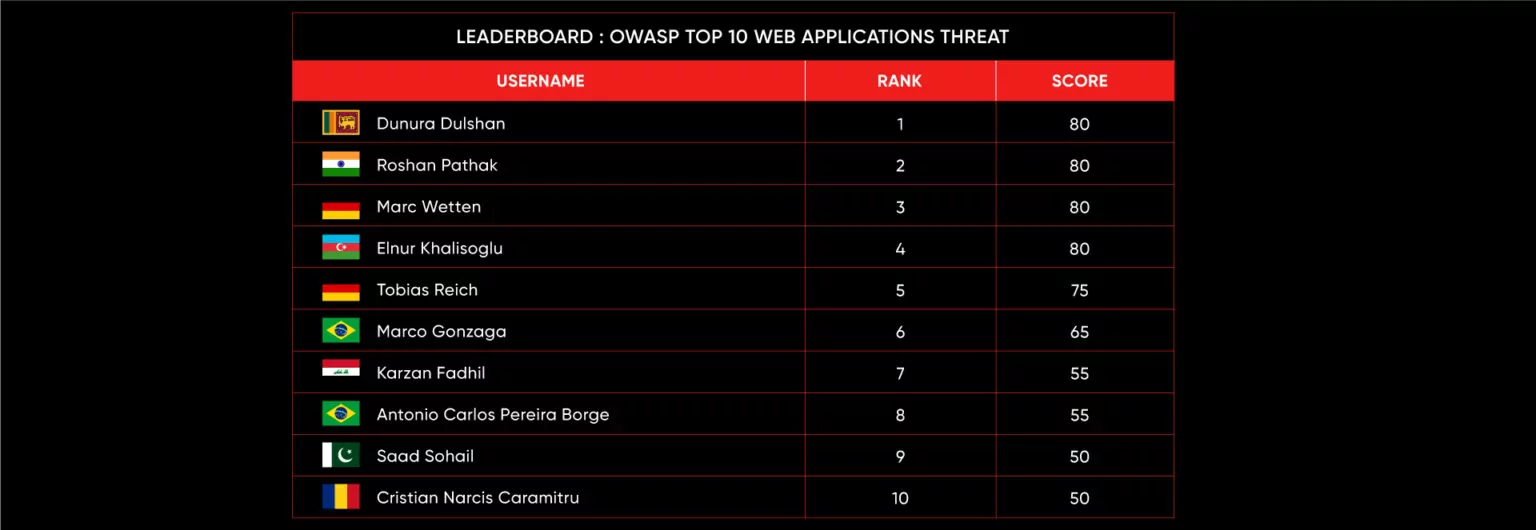
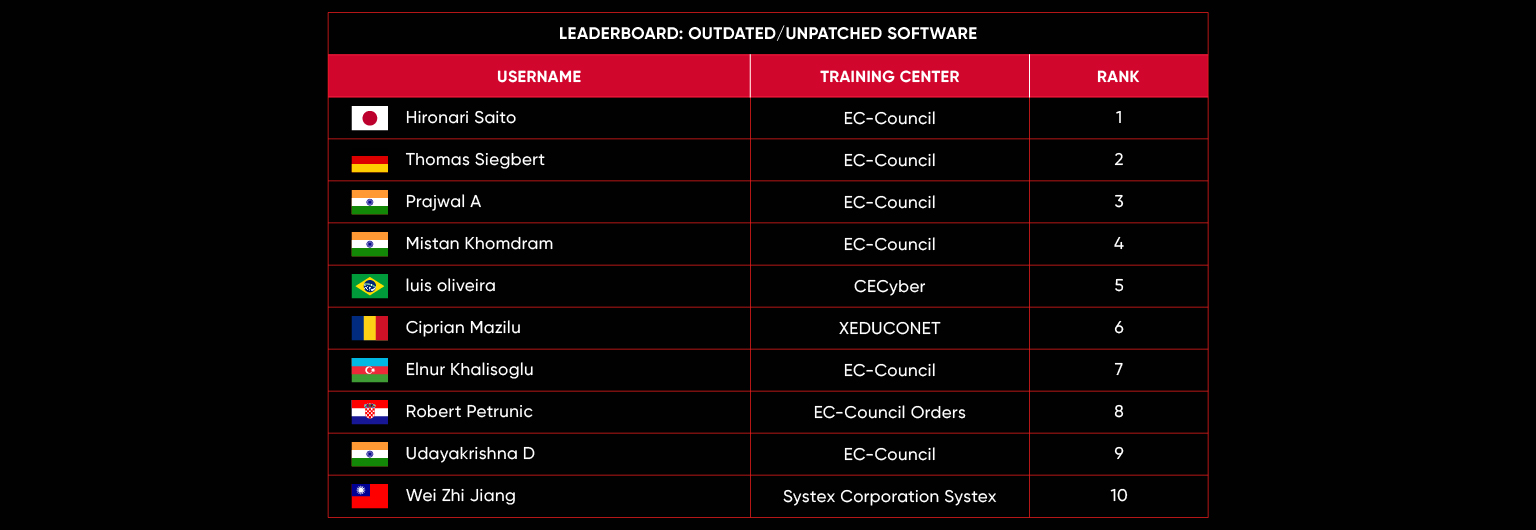
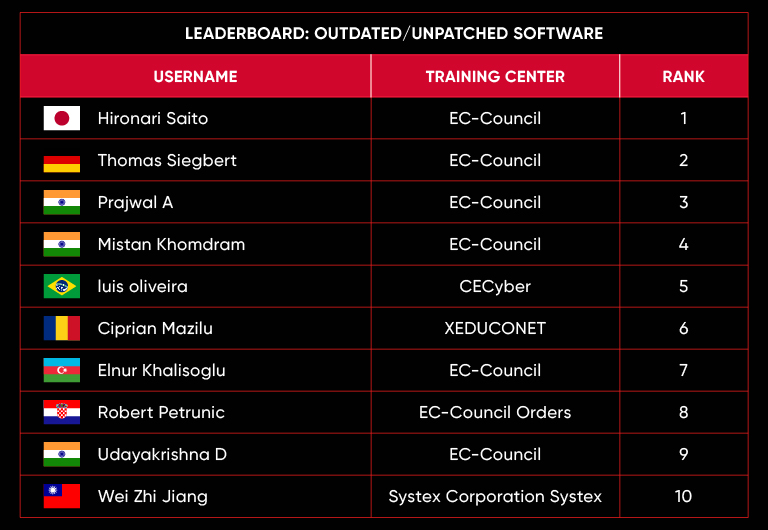
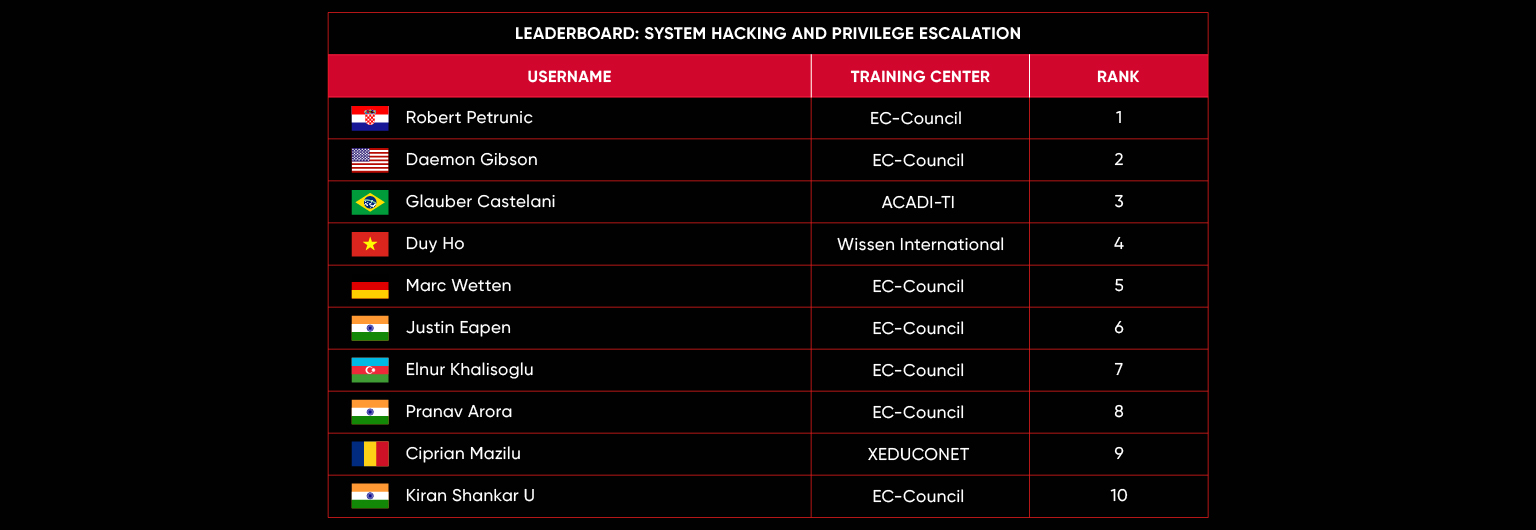
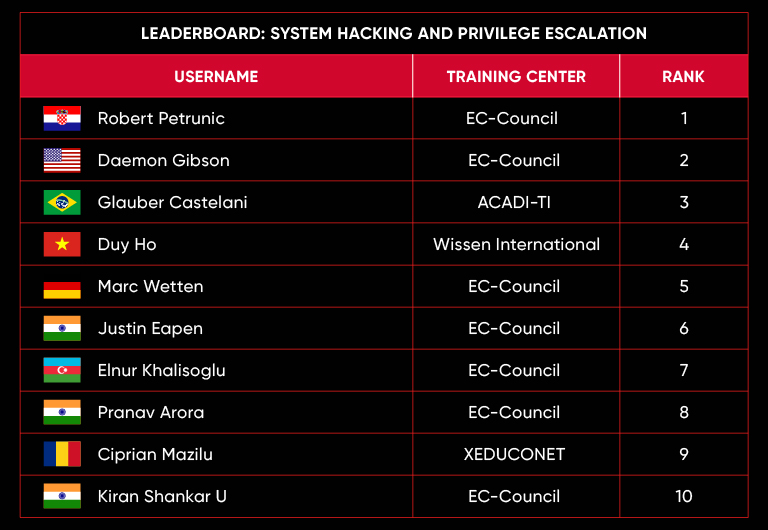
C|EH Compete Leaderboard







Why C|EH Global Challenges?

Gain Skills
- 20 Modules
- Over 221 hands-on labs to practice attack vectors and hacking tools
- 550 attack techniques
- Over 4,000 hacking and security tools
- Labs to Practice AI-driven tools and skills
- AI-integrated skills in the 5 phases of the ethical hacking framework
- Learn how to hack multiple operating systems
- More than 50% of training time is dedicated to labs

Gain Experience
C|EH Knowledge Exam
- 4 hours
- 125 multiple-choice questions
C|EH Practical Exam
- 6-hours
- 20 real scenario-based questions
Both Exams:
ANAB ISO/IEC 17024
US DoD 8140 Accredited

Gain Recognition
- Conduct A Real-World Ethical Hacking Assignment
- Apply The 5 Phases
- Reconnaissance
- Scanning
- Gaining Access
- Maintaining Access
- Covering Your Tracks

Gain Respect
- New Challenges Every Month
- 4-hour CTF competition
- Compete with your peers worldwide
- Hack your way to the top of the leaderboard
- Focus on new attack vectors
- Exploit emerging vulnerabilities
- Continuous learning platform
Learn About the FAQs and the Official Rules of the C|EH Ethical Hacking Global Challenges
FAQ's
Official Rules
FAQ's
- Log in to your ASPEN account. Click here to access ASPEN.
- In the C|EH v13 Competitions pane, you can view Current, Future, and Past competitions by clicking on the arrow (˅) icon.
- To participate in a competition, expand Current Competition and click the + icon.
- Read the competition scenario and click Compete. Note: By participating in the C|EH competitions, you agree to the challenges’ rules.
- Ensure that the Console toggle button is turned on and your nearest lab launch location is selected. Click Play.
- Wait while your lab range is being built.
- Read the about the competition and scenario carefully, then click Launch to participate in the competition.
- In the C|EH Competition console, click Red Flags. This will open competition flags in the right pane.
- Use the console machine to find the answers to the flags, enter the answer in the Answer field, and click Submit.
- Once you have found and submitted answers to all the flags, click Finish to close the cyber range.
C|EH Global Challenges are an exclusive benefit for students of C|EH Version 13. Included with C|EH Elite access, our students and certified members have access to each monthly competition through their student dashboard.
As a student of C|EH v13, you’ve already prepared to compete! Going through C|EH has taught you the tactics, techniques, and procedures necessary to be successful in the C|EH Global Challenges. Though the flags will be challenging, you will apply what you learned during C|EH to solve each flag. Between the coursework, labs, practice time, and Engage range, you can be confident in your skills as an ethical hacker. Trust your training and use it to compete!
You will be connected live to real machines in the EC-Council Cyber Range. This is not a simulation. However, you are flying solo. Each time you connect to the C|EH Global Challenges, you will be in an isolated competition environment. Your machines are yours, and there are no other players in your boxes. The scoring system works by comparing the results of each individual player, but you will not be playing head-to-head in your environment.
Each time you compete, you will have a series of flags (questions that require answers). To solve the flags, you must perform activities in the live target environment. Submitting each answer will award you the points associated with that flag. Time matters and so do hints. Not all competition flags provide hints, but for the ones that do, each use of a hint will deduct points from your flag score. Arriving at a correct answer will lock in your score during the 4-hour competition period. Leaderboards are calculated based on total points earned and overall time spent completing the challenge. To claim your spot at the top, you must be correct, proficient, and precise on the range.
Equipment requirements are basic for our competitions because all targets are located in our cloud infrastructure, including your attack platform. You will need a stable internet connection and an HTML5 capable browser to connect to our environment. All the tools required to compete are provided in the platform that launches when you click Compete.
Competitions are hosted in our cloud-based Cyber Range. Clicking Play will initiate our launch process. It typically takes 1 to 2 minutes to generate your attack console and all target machines required for the event. As you connect to the console view, you will see the desktop of your attack console and a set of flags on the right side of the screen. As you work in the remote view of the machines, you will arrive at solutions to each flag challenge, which you will enter in the answer box to achieve your score.
CTF stands for Capture-the-Flag. This gamified style of challenges provides you with objective-based flags. To get the answer for a flag, you must perform hands-on activities in the target network. Each flag is tracked and has a point value. Our flags are mapped to cyber competencies that you would use in your regular day as an ethical hacker.
Leaderboards and performance metrics are available to you in the C|EH v13 dashboard in ASPEN, EC-Council’s student management system. You can select current or previous month’s challenges and see how you placed overall. You can also see individual flag performance with benchmark comparisons to the total possible points and average points earned by other participants.
Yes! Support is only a click away throughout your competition. When you launch into the competition, a small “Chat with us” support option is available on the screen. It will connect you directly to our customer support team. While they are trained not to give you hints or answers on the content, they are able to support you with any platform-related challenges. Our professional support team is always standing by 24/7 to support whatever challenges you face.
For over 20 years, EC-Council has trained and certified information security professionals as Certified Ethical Hackers. For the past few years, we have been working to provide the best in hands-on experiences with labs and challenges to ensure our classroom experience mimics the real, day-to-day experiences of our Certified Ethical Hacker alumni and certification holders. One common piece of feedback we have received from over 80% of our certification holders is that they dedicate time each week to learning new skills and staying ahead of the curve. Competition drives that research, practice, curiosity, and discipline. With our new CyberQ Cyber Range, we wanted to provide a place to drive our Ethical Hackers to be the best they can be through challenges, applied knowledge, new topics, and changing conditions and standards while bringing in the spirit of fun competition. Our goal with the C|EH Global Challenges is to inspire the continuous development of our professional certified audience and give them an accessible, safe place to test out new tactics as well as expose them to live threats and vulnerabilities as they continuously improve.
There is no prize better than knowledge and experience. Our competitions are not sponsored, and there are no sales gimmicks. The C|EH Global Challenges are provided by EC-Council as a benefit to C|EH Elite students and certified members exclusively for the sole purpose of continuous education, skill development, and pushing our Ethical Hackers to be the best they can be.
Official Rules
The C|EH Global Challenges are open to all C|EH Certified Members with active access to C|EH Version 13 or higher.
The C|EH Global Challenges consist of one (1) cyber challenge each month. Challenges will be available at 00:00:01 UTC on the first calendar day of the month, and each challenge will conclude at 23:59:59 UTC on the last calendar day of the month. Players will be responsible for determining the translation to their respective time zones, given that all start and end times are calculated on the UTC basis as noted above.
Each challenge will have a maximum time of 4 hours. Challengers will not have the ability to pause or restart challenges. Each challenge attempt must be completed from start to finish in one 4-hour session. Once the 4-hour time limit is up, the challenge will automatically end, at which point scores are considered final regardless of the challenger’s progress.
Each challenge will allow one (1) attempt only. Challengers may activate their attempt at any point during the month. Initiating a challenge attempt during an active challenge month will consume the single attempt allotment, and challengers will not be able to initiate their next challenge until the following calendar month when the next challenge becomes available.
Challenge scoring is calculated through the submission of flags. Challenges are hosted in EC-Council’s CyberQ Platform, which generates the live challenge environment with the required tools and targets as well as a flag submission engine. Questions are posed to challengers, and they must find the correct answer to the question by evaluating the target systems and carrying out tactical cyber activities to determine the correct response. In some cases, hints are provided but may reduce the overall points issued for capturing the flag, thereby reducing the candidate’s overall score.
All C|EH Global Challenge scoring metrics are available through the C|EH v13 ASPEN dashboard tile. Near the top of the screen is a section titled “C|EH Competition Dashboard.” Each Challenge you participate in has available metrics centered around your performance. You may use the select boxes to filter by challenge, month, and year. Once you have selected the appropriate challenge, the scenario will be displayed, explaining the context of the challenge as well as your performance metrics as specified below.
Leaderboard – The Leaderboard provides a view of the top 10 challengers by rank and score, as well as your position either in the Top 10 or in a lower rank based on your performance in the challenge.
Rank –Rank is the relative position of your score in the challenge to other Certified Ethical Hackers who have completed the same challenge. Scores combined with time to complete provide a speed and accuracy variable to determine your overall rank against other challenges.
Score –Score is a number calculated by adding the value of each flag submission you completed correctly or partially correct during your challenge attempt. Each question has a numerical value. In order to earn points on a flag submission, you must answer the question correctly. Some flag values are higher than others, depending on the complexity of the question or task required to determine your response. Once all flags are submitted, your total score is calculated by adding each individual submitted flag’s value together.
My Rank
Rank Position – Your current rank or position is a sequential numerical value that specifies where you stand in relation to other players who have attempted the same challenge.
Change in Rank Position – Throughout the duration of the challenge, your rank is subject to change should another Certified Ethical Hacker score higher than you or complete the entire challenge in a shorter time with as many or more points.
My Score vs. Total Possible
My Score – This is the same metric described above under “Leaderboard.”
Possible Score – This value represents the highest possible score you can earn in a given challenge. It is the maximum available point value from all flags in the challenge.
Overall Percentage Calculated as (My Score/Possible Score)*100, the result is shown as a % value.
My Flag Performance vs. Benchmark
This chart represents your performance for individual flags in the challenge. The graph provides a simple benchmark comparison of your score on a flag-by-flag basis to the total possible score, and the average score achieved by all players in the challenge.
My Score –This is the number of points you earned on each individual flag.
Possible Score –This is the total possible points available for each individual flag.
Average Score –This is the average score earned by all players in the challenge.
All challengers are required to utilize a system with an HTML5 (or newer) capable browser. Challengers must also have a stable, preferably high-speed internet connection. All activities will be carried out in a controlled, virtualized environment. Though challengers are evaluating live target systems and utilizing live attacks, scanners, and tools, all traffic is contained to the challenge environment. No processes are run on challenger machines aside from their active connection to the CyberQ Console via a web site.
EC-Council reserves the right to disqualify a participant at its own discretion. Examples of events leading to disqualification can include but are not limited to: cheating, violating the terms and conditions of use, violating the End User License Agreement in any way, sharing flag answers with others, broadcasting or streaming their attempt, and/or abusing other participants in the challenge in any way, shape, or form.
If a player is disqualified from the C|EH Global Challenges, their score and rank data will be removed from the event in which they were disqualified, and participation in future global challenges will be prohibited. Candidates will be notified in writing at the official email address used to register for their account in ASPEN.
Accreditations, Recognitions & Endorsements




