Cybersecurity is of utmost importance, especially in today’s world. Our world is connected through a fragile network that deals with internet banking and government infrastructure as DoS attacks, website defacement, and other cyber-attacks are on the rise.
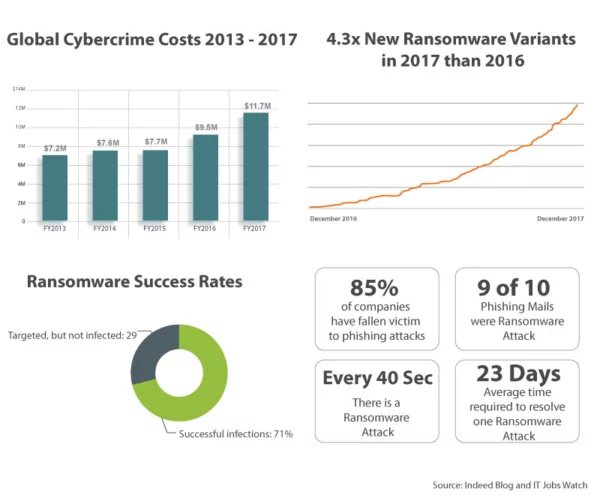
Global cybercrime costs saw an increase of approximately 27.4% in the last year alone. Of late, 85% of the companies in the UK and the U.S. have fallen victim to phishing attacks (9 out of 10 phishing emails carried malicious ransomware). The number of newly evolved ransomware attacks in 2017 is over 4 times more than in 2016. An organization is hit with a ransomware attack every 40 seconds; at least 71% of these attacks are successful. The time taken, on an average, for a company to resolve even one of these attacks is 23 days.
Penetration Testing (or Pen Testing) is a method of evaluating the security of an information system by simulating an attack from a malicious source. In simple terms, it is an authorized test to establish how weak your organization’s cybersecurity is and what you can do to strengthen it. Sadly, not many companies are comfortable with the idea of reassessing their security budgets.
It is time for organizations to re-think the security of their cyberspace with the help of penetration testers. Here are a few reasons why you should hire a penetration tester:
1. Security Tools vs. Penetration Testers
Every company has their own set of cybersecurity tools––like encryption codes, anti-virus software, and vulnerability scanning––but how sure are you that these tools will be able to protect you in a live attack?
Penetration testers are trained to think beyond the normal and navigate their way through even the toughest of barriers using a base of open-source methodologies like Open Web Application Security Project (OWASP), PTES, NIST800-115, PCI DSS, Information Systems Security Assessment Framework (ISSAF), Open Source Security Testing Methodology Manual (OSSTMM), etc. as basic road-map.
They go one step beyond a vulnerability assessment by providing defense in depth; this also includes exploiting the vulnerabilities identified during Perimeter Testing, Database Penetration Testing, Log-Management Penetration Testing, Cloud Penetration Assessment, Network Security Assessment, Wireless/ RAS Assessment, Telephony Security Assessment, File Integrity Checking, and other assessments.
2. A Fresh and Advanced Opinion
Often, a person falls into a set pattern of performing tasks when completed on a day-to-day basis. This is also the case with ethical hackers employed in a company. While following a schedule is generally a great advantage for an organization, it is not the case with penetration testing.
A penetration tester is trained to identify the threats through a new approach, as well as determine the probability of an attack on information assets, ensuring a better Return on Investment (RoI) for IT Security. They provide assurance that the company is operating with an acceptable limit of information security risks, and are to do so in compliance with the regulations and industry standards.
3. Attacks a Single Target as a Whole
You have just learned the various tools and techniques of ethical hacking, but is that enough to carry you through a full-scale penetration test?
It is in a moment like this that the penetration tester’s skills and hands-on experience to stimulate a real-life cyber-attack is important. By using various methodologies to perform advanced attacks they can identify Structured Query Language (SQL) injections, Cross-Site Scripting (XSS), LFI, and RFI vulnerabilities in the organization’s web applications and infrastructure.
It is through hands-on experience and hours of implementing knowledge and skill into practice that a penetration tester is able to expose several vulnerabilities for a single target by aiming a combination of methodologies at the organization’s cybersecurity.
Very often, a single attack will not show the penetration tester any vulnerabilities in the organization’s cybersecurity. However, when a single target is obtained and attacked by various simultaneous attacks, it could lead to a breach in an organization’s cybersecurity; thus, exposing a vulnerability.
4. Penetration-Testing Report Writing
Every penetration tester is trained to provide in-detail, industry-level approved documentation of their findings. This report generally includes a detailed usage of methodologies: an attack narrative, evidence and corroboration of any successful penetration findings, and documentation of any security flaws. Apart from the findings, the report also includes remediation details to prevent any possible future malicious attacks on the organization.
The penetration tester will also be able to advise you on what risks must be addressed first based on the amount of risk exposure it involves.
This report will enable the organization to make decisions on implementing security controls in the organization and patch any flaws. This also enables the organization and the penetration testers to keep track of the exploits performed and the information accumulated.
5. White-Box vs. Black-Box Testing
White-box testing is the method in which the penetration tester has an authorized view of the internal structure of the organization; black-box testing provides the penetration tester with little-to-no information about the organization’s infrastructure.
While white-box testing is certainly a cheaper option, it may not be the best option for your company––where security is concerned––as it is highly possible that many threats can go unnoticed.
Black-box testing gives the company the perfect “real-life” perspective from an unauthorized hacker’s point of view. This enables the penetration tester to conduct an unbiased test, as they will be working independently. It also tests the environment the program is running in and is perfect for large applications. Test cases can also be designed immediately, as the tester does not have to wait for the development to be completed. The penetration testers who follow black-box methodology use various application scanners––such as Boundary Value Analysis (BVA), equivalence partitioning, error guessing, domain analysis, and many more techniques––to find and exploit vulnerabilities.
Only 38% of global organizations claim they are prepared to handle a sophisticated cyber-attack––while the estimated average cost of a data breach in 2020 is said to exceed $150 million. This makes penetration testing a boardroom agenda. Apart from the aforementioned reasons, a trained penetration tester is considered one of the finest solutions to discovering vulnerabilities in your organization, as they also help train the organization’s developers to make fewer mistakes.
However, keep in mind that while penetration testing can expose a weak link––giving you an idea of where to tighten security––tests must be conducted on a regular basis to ensure that the company remains secure at all times.
EC-Council is ready to play their role in helping secure organizations and businesses around the world on 14 March, as they reveal their biggest announcement yet. Book your seats now to be a part of this event!
Sources:
https://www.accenture.com/t20170926T072837Z__w__/us-en/_acnmedia/PDF-61/Accenture-2017-CostCyberCrimeStudy.pdf
https://www.proofpoint.com/sites/default/files/pfpt-us-tr-q117-threat-report.pdf
https://securelist.com/kaspersky-security-bulletin-2016-story-of-the-year/76757/
https://info.wombatsecurity.com/state-of-the-phish
http://phishme.com/phishing-ransomware-threats-soared-q1-2016/
https://www.cybintsolutions.com/cyber-security-facts-stats/








