
Ready to challenge your skills? Getting ready for a CTF or a Cyber Challenge?
Train With CyberQ Skill Pack Challenges
CyberQ Skillpacks are designed to test your skills in a variety of different challenges with limited guidance. Each challenge runs independently as its own “Self-Paced Capture the Flag.” Launching a Skill Pack challenge will reserve your very own space in our CyberQ Data Center, we will raise the Attack Console, as well as the down-range vulnerable targets for you to practice and challenge your skills.

Please note, this is not a learning lab. Skill packs are designed intentionally with challenges, puzzles, and preconfigured targets that will test your ability to identify, analyze, exploit, and own the targets. If you are new to Cyber and have never participated in a cyber challenge or competition, Skill packs may be too advanced. So, feel free to browse our learning products if this describes you, however, if you are ready for a challenge, enjoy solving complex puzzles and testing your limits, CyberQ challenges are a great way to hone your trade craft.
Password Cracking Techniques Skill Pack
This Skill Pack will challenge your skills in salient web application hacking and penetration testing techniques including; Remote Code Execution, Local File Inclusion (LFI), SQL Injection, Arbitrary File Upload, Directory Traversal, Web Application Enumeration, Command Injection, Remote Buffer Overflow, Credential Attack, Shell Injection, and SSH Bruteforce Attacks.
Each challenge contains a fully designed target network with live virtual machines, servers, web hosts, and vulnerable sites and applications. Launching a challenge will open the CyberQ Console and safely connect you to our live attack environment right through your browser. Depending on the challenge, you will land in your attack machine, either Kali or Parrot, where you will have instant access to the full suite of attack tools required to carry out your challenge. Targets are preconfigured with host and application vulnerabilities which you will uncover as you progress through the challenges. CyberQ is a fully automated Cyber Range platform providing you with a self-driven ‘Capture-the-flag‘ experience in each challenge.
Gain direct hands-on practical experience on Industry’s leading Cyber Range Platform – CyberQ. Successful Completion of this Web Application Hacking and Penetration Testing Skill Pack will gain you Job-ready Cyber skills and execution efficiency against cyber challenges.
- Hands-on Experiences with Immersive Scenarios
- Designed for Deep Learning by Cyber Experts
- Latest Threats, Vulnerabilities and Techniques
- Practical Application of Skills on Cutting-edge Cyber Range
- Skills Feedback with Every Exercise
- Fully Loaded Attack Platform
- Preconfigured Live targets and vulnerable Hosts, Sites, and Applications “down-range”
2 Challenges
No Credit Card Required
10 Challenges
About Password Cracking Skill Pack
Password cracking is the process of recovering passwords from the data transmitted by a computer system or from the data stored in it. The purpose of cracking a password might be to help a user recover a forgotten or lost password, as a preventive measure by system administrators to check for easily breakable passwords, or for use by an attacker to gain unauthorized system access.
Hacking often begins with password-cracking attempts. A password is a key piece of information necessary to access a system. Consequently, most attackers use password-cracking techniques to gain unauthorized access. An attacker may either crack a password manually by guessing it or use automated tools and techniques such as a dictionary or a brute-force method. Most password-cracking techniques are successful because of weak or easily guessable passwords.
Types of Password Attacks
- Dictionary Attack: In this type of attack, a dictionary file is loaded into a cracking application that runs against user accounts. This dictionary is a text file that contains several dictionary words commonly used as passwords. The program uses every word present in the dictionary to find the password.
- Brute-Force Attack: In a brute-force attack, attackers try every combination of characters until the password is broken.
- Rule-based Attack: Attackers use this type of attack when they obtain some information about the password. This is a more powerful attack than dictionary and brute-force attacks because the cracker knows the password type. For example, if the attacker knows that the password contains a two- or three-digit number, he/she can use some specific techniques to extract the password quickly.
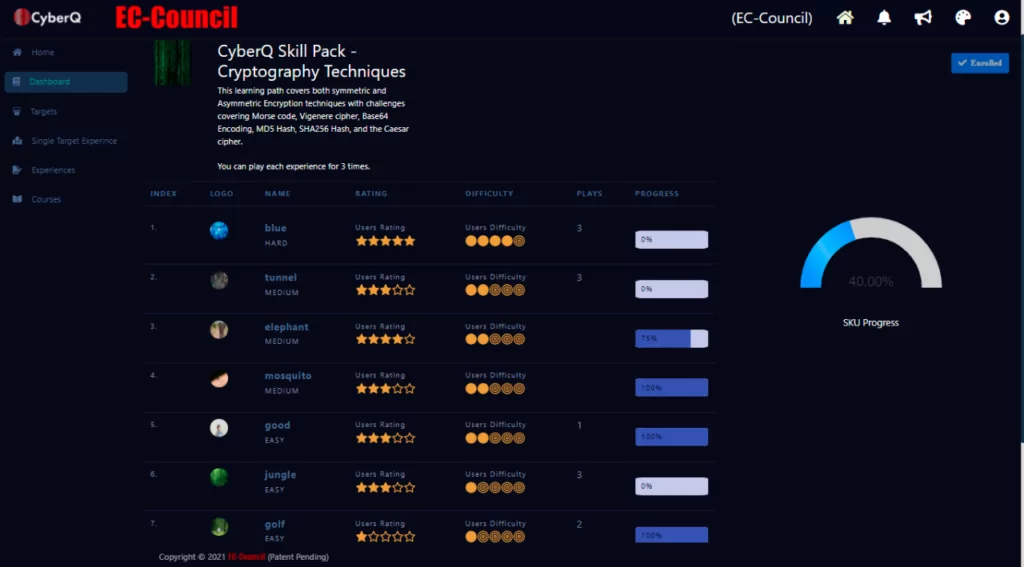
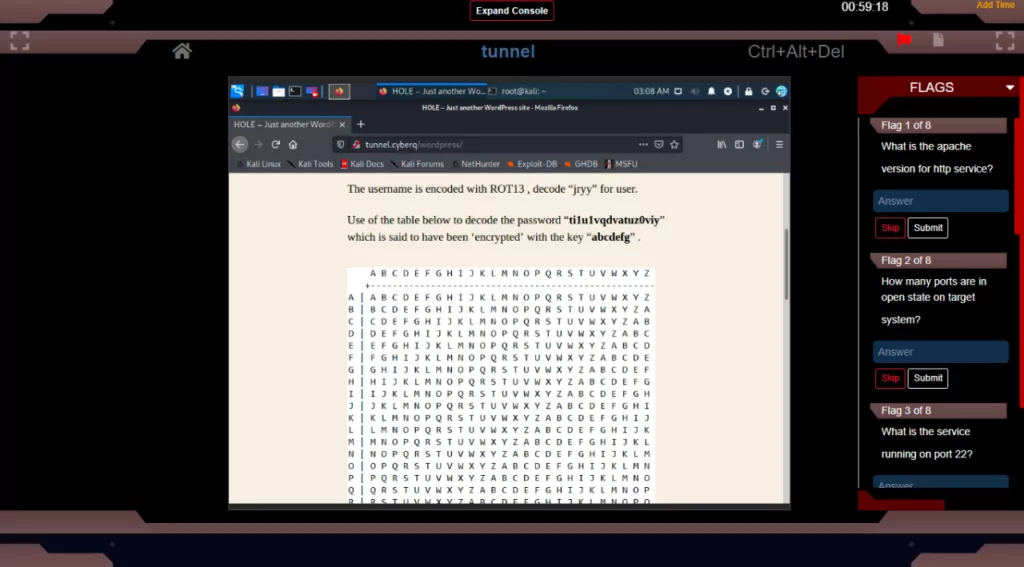
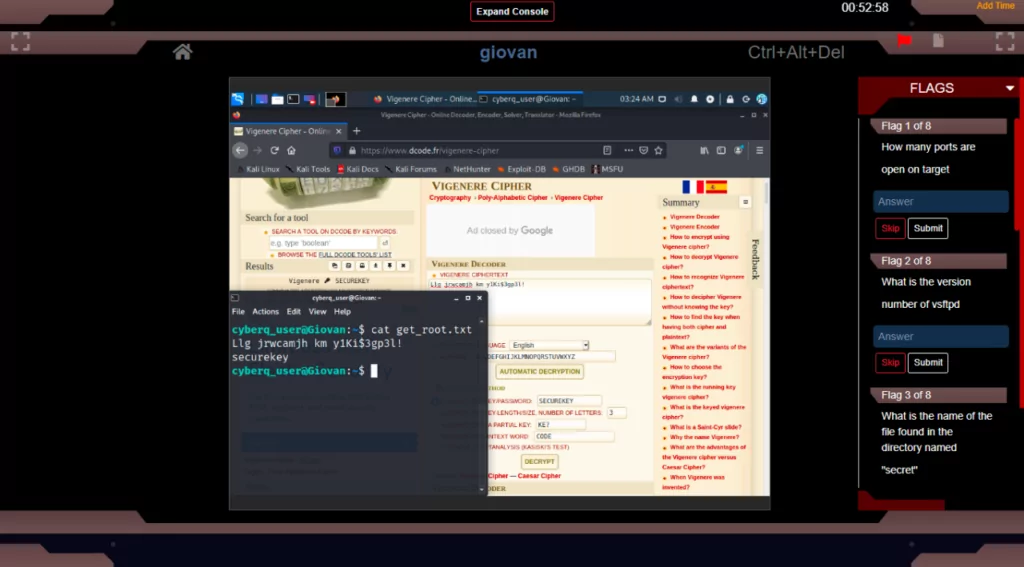
Password Cracking Techniques Covered in the Skill Pack
- SSH Password Cracking
- Telnet password cracking
- RDP Password Cracking
- SMB Password Cracking
- FTP Password Cracking
- ZIP Password Cracking
- Password Hash Cracking
- WinRM Password Cracking
Gain related NICE skills for Steganography
S0001
Skill in conducting vulnerability scans and recognizing vulnerabilities in security systems.
S0009
Skill in assessing the robustness of security systems and designs.
S0044
Skill in mimicking threat behaviors.
S0051
Skill in the use of penetration testing tools and techniques.
S0137
Skill in conducting application vulnerability assessments.
S0364
Skill to develop insights about the context of an organization’s threat environment.
Related Job Roles for Password Cracking
- Blue Team Technician
- Red Team Technician
- Computer Network Defense (CND) Auditor
- Ethical Hacker
- Information Security Engineer
- Internal Enterprise Auditor
- Penetration Tester
- Network Security Engineer
- Technical Surveillance Countermeasures Technician
- Reverse Engineer
- Risk/Vulnerability Analyst
- Vulnerability Manager
Continue on your Cyber Proficiency Journey with Skill Packs Designed by Our Cyber Experts
- Web App Hacking and Pen Testing
- Service Exploitation
- Privilege Escalation
- Red Team Architect
- Cryptography
- Vulnerability Research for Hackers and Pen Testers
- Steganography
- SQL Injection
- Password Cracking

