Ready to challenge your skills? Getting ready for a CTF or a Cyber Challenge?
Train With CyberQ Skill Pack Challenges
CyberQ Skillpacks are designed to test your skills in a variety of different challenges with limited guidance. Each challenge runs independently as its own “Self-Paced Capture the Flag.” Launching a Skill Pack challenge will reserve your very own space in our CyberQ Data Center, we will raise the Attack Console, as well as the down-range vulnerable targets for you to practice and challenge your skills.

Please note, this is not a learning lab. Skill packs are designed intentionally with challenges, puzzles, and preconfigured targets that will test your ability to identify, analyze, exploit, and own the targets. If you are new to Cyber and have never participated in a cyber challenge or competition, Skill packs may be too advanced. So, feel free to browse our learning products if this describes you, however, if you are ready for a challenge, enjoy solving complex puzzles and testing your limits, CyberQ challenges are a great way to hone your trade craft.
Red Team Architect Techniques Skill Pack
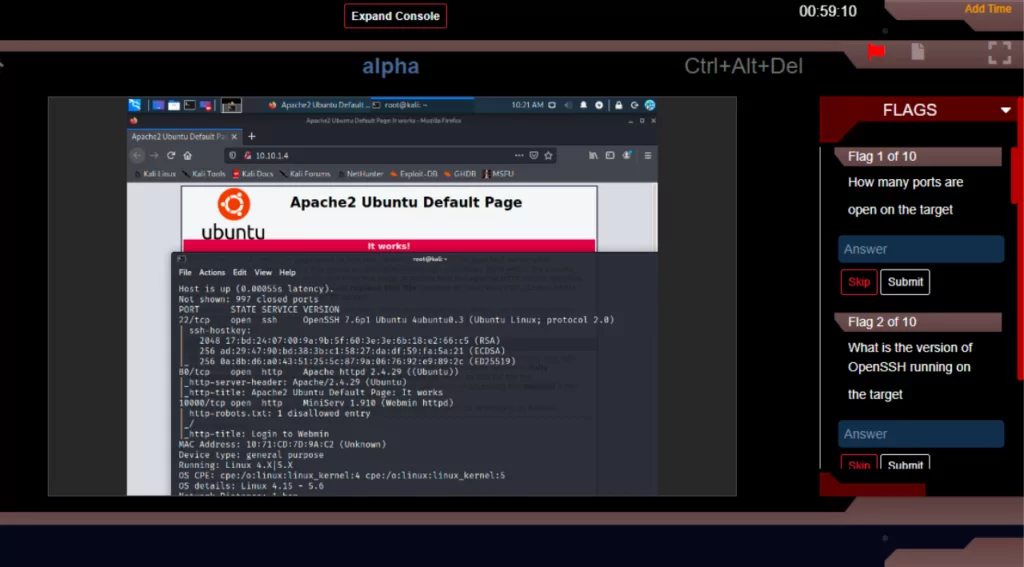
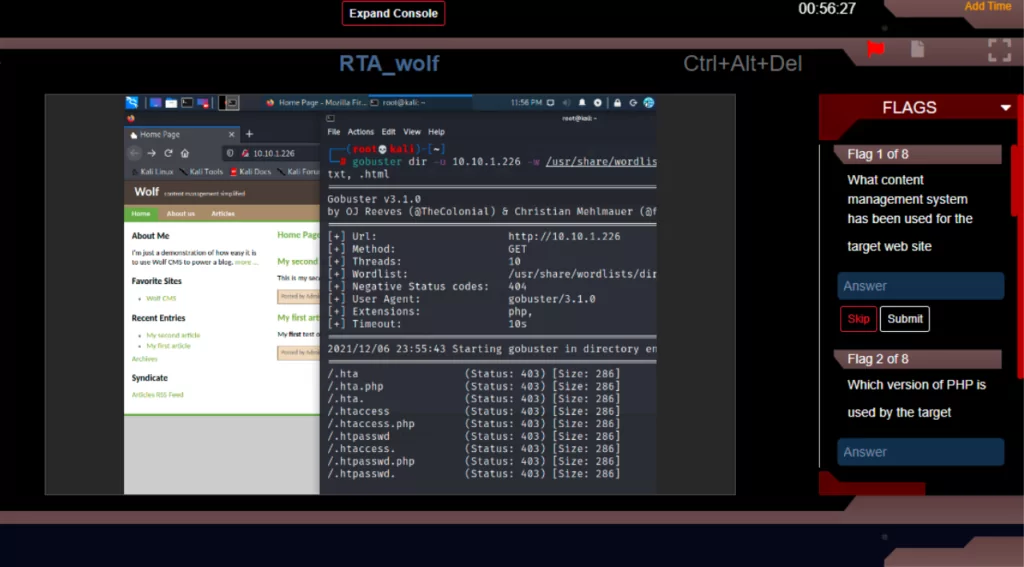
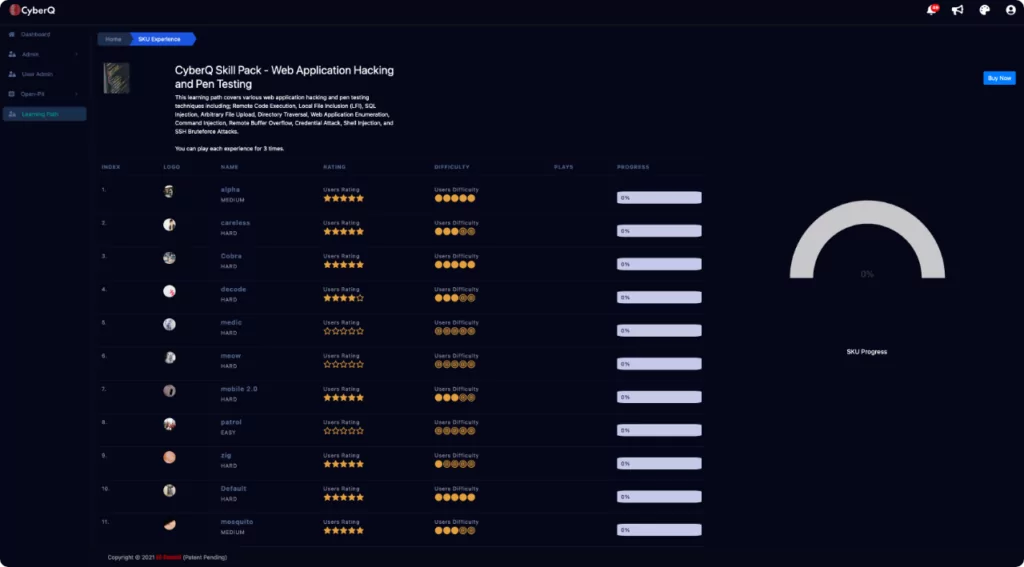
This Skill Pack will challenge your skills in salient web application hacking and penetration testing techniques including; Remote Code Execution, Local File Inclusion (LFI), SQL Injection, Arbitrary File Upload, Directory Traversal, Web Application Enumeration, Command Injection, Remote Buffer Overflow, Credential Attack, Shell Injection, and SSH Bruteforce Attacks.
Each challenge contains a fully designed target network with live virtual machines, servers, web hosts, and vulnerable sites and applications. Launching a challenge will open the CyberQ Console and safely connect you to our live attack environment right through your browser. Depending on the challenge, you will land in your attack machine, either Kali or Parrot, where you will have instant access to the full suite of attack tools required to carry out your challenge. Targets are preconfigured with host and application vulnerabilities which you will uncover as you progress through the challenges. CyberQ is a fully automated Cyber Range platform providing you with a self-driven ‘Capture-the-flag‘ experience in each challenge.
Gain direct hands-on practical experience on Industry’s leading Cyber Range Platform – CyberQ. Successful Completion of this Web Application Hacking and Penetration Testing Skill Pack will gain you Job-ready Cyber skills and execution efficiency against cyber challenges.
- Hands-on Experiences with Immersive Scenarios
- Designed for Deep Learning by Cyber Experts
- Latest Threats, Vulnerabilities and Techniques
- Practical Application of Skills on Cutting-edge Cyber Range
- Skills Feedback with Every Exercise
- Fully Loaded Attack Platform
- Preconfigured Live targets and vulnerable Hosts, Sites, and Applications “down-range”
@ $99.99
About Red Team Architect Skill Pack
Red Team Architect: Techniques, Primary Activities and Responsibilities Covered in the Skill Pack
- Identify and communicate risks to Technology owners to promote a robust cyber risk management program allowing CSX to proactively triage and remediate flaws in Information Technology and Operational Technology systems.
- Conduct active and passive penetration testing on Information Technology and Operational Technology environments.
- Engage with Technology and Engineering teams to explain results and provide guidance on remediation of identified vulnerabilities.
- Lead the Vulnerability Management activities within the Information Security Working Group, a cross functional team of Technology Operations and Applications team members responsible for reducing the cyber-attack surface of CSX systems.
- Coordinate testing efforts of external red teaming and penetration teams engaged by CSX.
- Research, evaluate, design, test, recommend or plan the implementation of new or updated information security hardware or software, and analyze its impact on the existing environment; provide technical and managerial expertise for the administration of security tools.
- Manage production issues and incidents and participate in problem and change management forums.
- Assist with the resolution of negative audit findings reported by internal or external auditors.
Gain related Knowledge and Skills for Red Team Architect
Network penetration testing and manipulation of network infrastructure
Mobile and/or web application assessments
Shell scripting or automation of simple tasks using Python.
Developing, extending, or modifying exploits, shellcode, or exploit tools.
Knowledge of application technology security testing (white box, black box and code review)
Adheres to and improves upon company Information Security policies and procedures; mastery of core technical concepts; supports and assists in response to security events and escalations; may provide disaster recovery support; responsibilities may extend beyond day-time business hours, including on-call rotation.
Technical agility and strong analytical skills.
Knowledge of mainstream operating systems (for example, Microsoft Windows and Linux) and a wide range of security technologies, such as network security appliances, identity and access management systems, anti-malware solutions, automated policy compliance and desktop security tools
Knowledge of network infrastructure, including routers, switches, firewalls and associated network protocols and concepts.
Strong written and verbal communication skills
Strong analytical skills
Continue on your Cyber Proficiency Journey with Skill Packs Designed by Our Cyber Experts
- Web App Hacking and Pen Testing
- Service Exploitation
- Privilege Escalation
- Red Team Architect
- Cryptography
- Vulnerability Research for Hackers and Pen Testers
- Steganography
- SQL Injection
- Password Cracking