
Ready to challenge your skills? Getting ready for a CTF or a Cyber Challenge?
Train With CyberQ Skill Pack Challenges
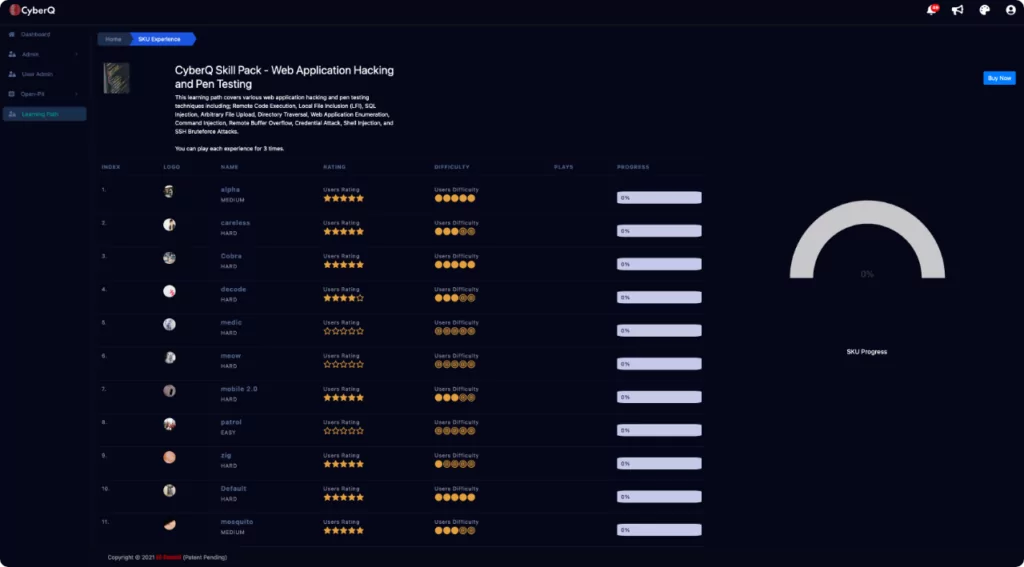
CyberQ Skillpacks are designed to test your skills in a variety of different challenges with limited guidance. Each challenge runs independently as its own “Self-Paced Capture the Flag.” Launching a Skill Pack challenge will reserve your very own space in our CyberQ Data Center, we will raise the Attack Console, as well as the down-range vulnerable targets for you to practice and challenge your skills.

Web Application Hacking and Penetration Testing Techniques Skill Pack
Network Security Engineer Salary
This Skill Pack will challenge your skills in salient web application hacking and penetration testing techniques including; Remote Code Execution, Local File Inclusion (LFI), SQL Injection, Arbitrary File Upload, Directory Traversal, Web Application Enumeration, Command Injection, Remote Buffer Overflow, Credential Attack, Shell Injection, and SSH Bruteforce Attacks.
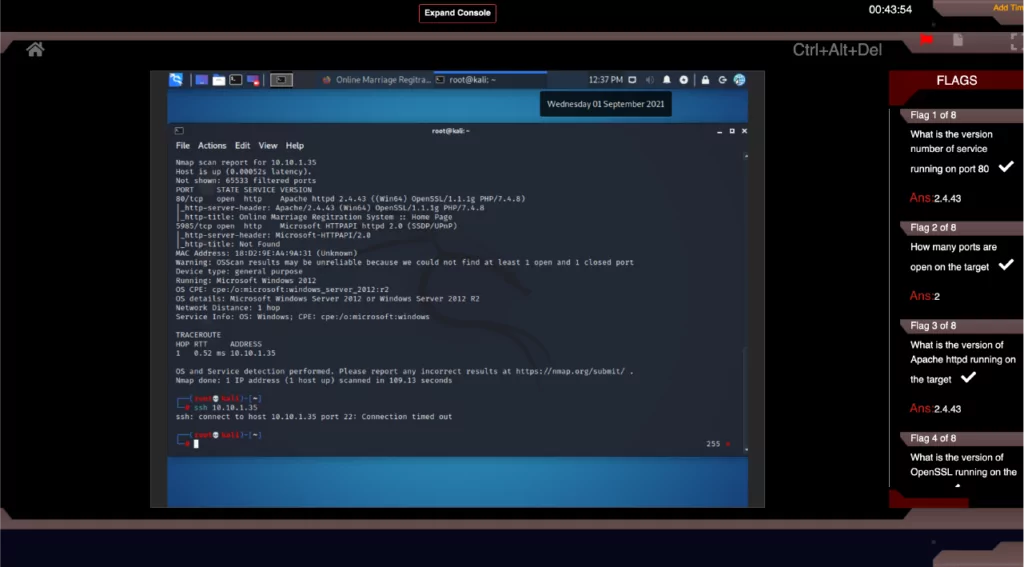
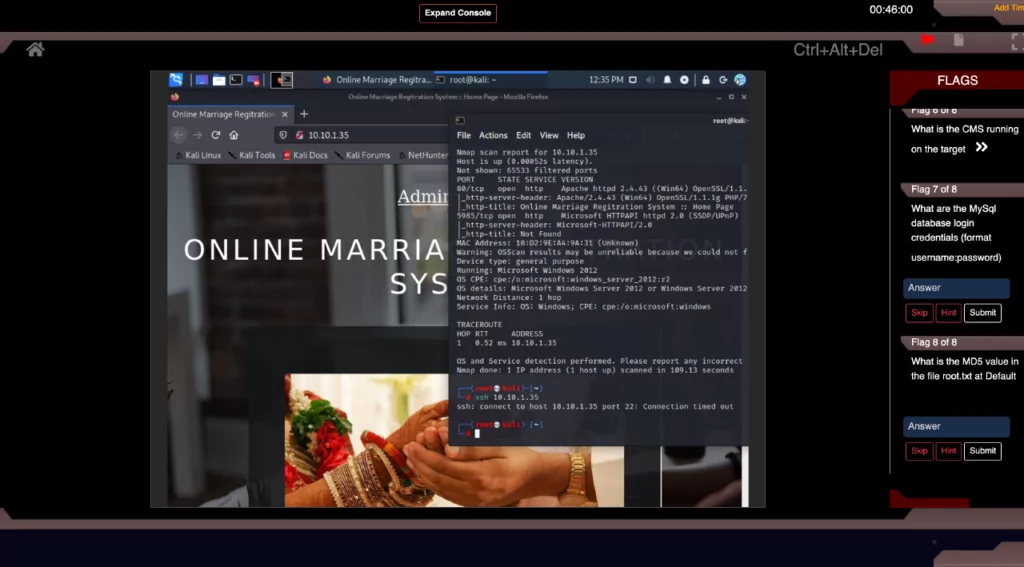
Each challenge contains a fully designed target network with live virtual machines, servers, web hosts, and vulnerable sites and applications. Launching a challenge will open the CyberQ Console and safely connect you to our live attack environment right through your browser. Depending on the challenge, you will land in your attack machine, either Kali or Parrot, where you will have instant access to the full suite of attack tools required to carry out your challenge. Targets are preconfigured with host and application vulnerabilities which you will uncover as you progress through the challenges. CyberQ is a fully automated Cyber Range platform providing you with a self-driven ‘Capture-the-flag‘ experience in each challenge.
Gain direct hands-on practical experience on Industry’s leading Cyber Range Platform – CyberQ. Successful Completion of this Web Application Hacking and Penetration Testing Skill Pack will gain you Job-ready Cyber skills and execution efficiency against cyber challenges.
- Hands-on Experiences with Immersive Scenarios
- Designed for Deep Learning by Cyber Experts
- Latest Threats, Vulnerabilities and Techniques
- Practical Application of Skills on Cutting-edge Cyber Range
- Skills Feedback with Every Exercise
- Fully Loaded Attack Platform
- Preconfigured Live targets and vulnerable Hosts, Sites, and Applications “down-range”
3 Challenges
No Credit Card Required
11 Challenges
About Web Application Hacking and Penetration Testing Skill Pack
The evolution of the Internet and web technologies, combined with rapidly increasing Internet connectivity, has led to the emergence of a new business landscape. Web applications are an integral component of online businesses. Everyone connected via the Internet is using various web applications for different purposes, including online shopping, email, chats, and social networking.
Web applications are becoming increasingly vulnerable to more sophisticated threats and attack vectors. Attackers attempt various application-level attacks to compromise the security of web applications to commit fraud or steal sensitive information.
Pen testers and attackers use the web application hacking methodology to gain knowledge of a particular web application to compromise it successfully. This methodology allows them to plan each step to increase their chances of successfully hacking the application. Under this methodology, they do the following to collect detailed information about various resources needed to run or access the web application:
- Footprint web infrastructure
- Analyze web applications
- Bypass client-side controls
- Attack authentication mechanisms
- Attack authorization schemes
- Attack access controls
- Attack session management mechanisms
- Perform injection attacks
- Attack application logic flaws
- Attack shared environments
- Attack database connectivity
- Attack web application clients
- Attack web services
Web Application Hacking and Penetration Testing Techniques Covered in the Skill Pack
- Remote Code Execution
- Local File Inclusion (LFI)
- SQL Injection
- Arbitrary File Upload
- Directory Traversal
- Web Application Enumeration
- Command Injection
- Remote Buffer Overflow
- Credential Attack
- Shell Injection
- SSH Bruteforce
Gain related NICE skills for Web Application Hacking and Penetration Testing
S0001
Skill in conducting vulnerability scans and recognizing vulnerabilities in security systems.
S0009
Skill in assessing the robustness of security systems and designs.
S0044
Skill in mimicking threat behaviors.
S0051
Skill in the use of penetration testing tools and techniques.
S0137
Skill in conducting application vulnerability assessments.
S0364
Skill to develop insights about the context of an organization’s threat environment.
Related Job Roles for Web Application Hacking and Penetration Testing
- Remote Code Execution
- Red Team Technician
- Computer Network Defense (CND) Auditor
- Ethical Hacker
- Information Security Engineer
- Internal Enterprise Auditor
- Penetration Tester
- Network Security Engineer
- Technical Surveillance Countermeasures Technician
- Reverse Engineer
- Risk/Vulnerability Analyst
- Vulnerability Manager
Continue on your Cyber Proficiency Journey with Skill Packs Designed by Our Cyber Experts
- Web App Hacking and Pen Testing
- Service Exploitation
- Privilege Escalation
- Red Team Architect
- Cryptography
- Vulnerability Research for Hackers and Pen Testers
- Steganography
- SQL Injection
- Password Cracking

