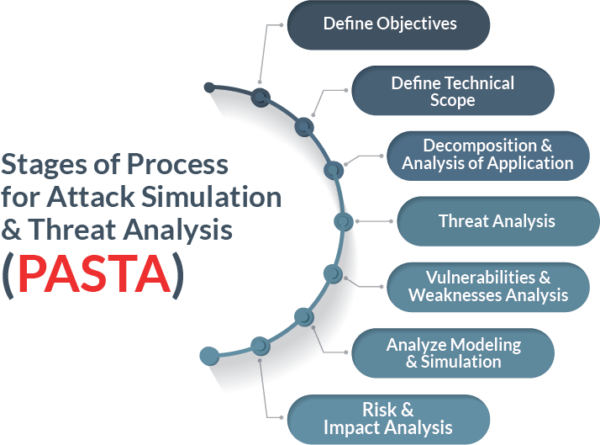
CYBER THREAT Modeling
Become a
Cyber Threat Intelligence Analyst (CTIA)
"*" indicates required fields
"*" indicates required fields
Threat modeling is a structured process to identify and enumerate potential threats such as vulnerabilities or lack of defense mechanisms and prioritize security mitigations. Threat modeling intends to equip defenders and the security team with an analysis of what security controls are required based on the current information systems and the threat landscape, the most likely attacks, their methodology, motive, and target system.
The threat modeling process requires collaboration between Security Architects, Security Operations, Network Defenders, SOC, and the Threat Intelligence team to understand each other’s roles, responsibilities, purpose, and challenges.
Threat modeling helps threat intelligence analysts identify, classify, and prioritize threats to ensure effective documentation and reporting, which is the overall objective of a threat intelligence program. An effective threat intelligence report helps the security defense and the security operations team protect IT assets from threats and vulnerabilities.
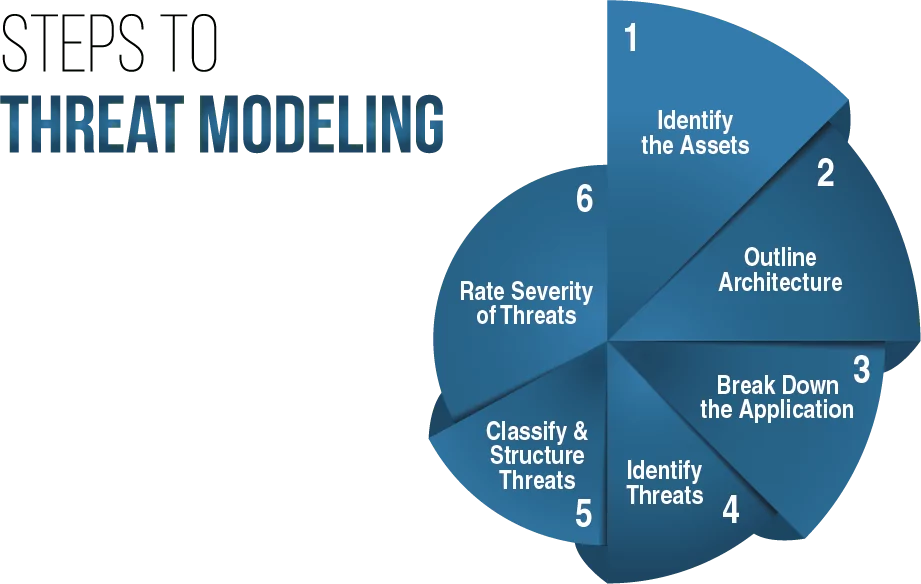
While adopting a threat modeling methodology, it is equally important to understand the difference in the approach, process, and objectives. There are several cyber threat modeling methodologies used to improve cybersecurity and threat intelligence practices. To ensure that the threat intelligence is actionable, information security professionals or cyber threat intelligence analysts must decipher which method aligns with their specific business goals and objectives.
Here are some of the six most common threat modeling methodologies that are used to access and prioritize threats to your IT assets:
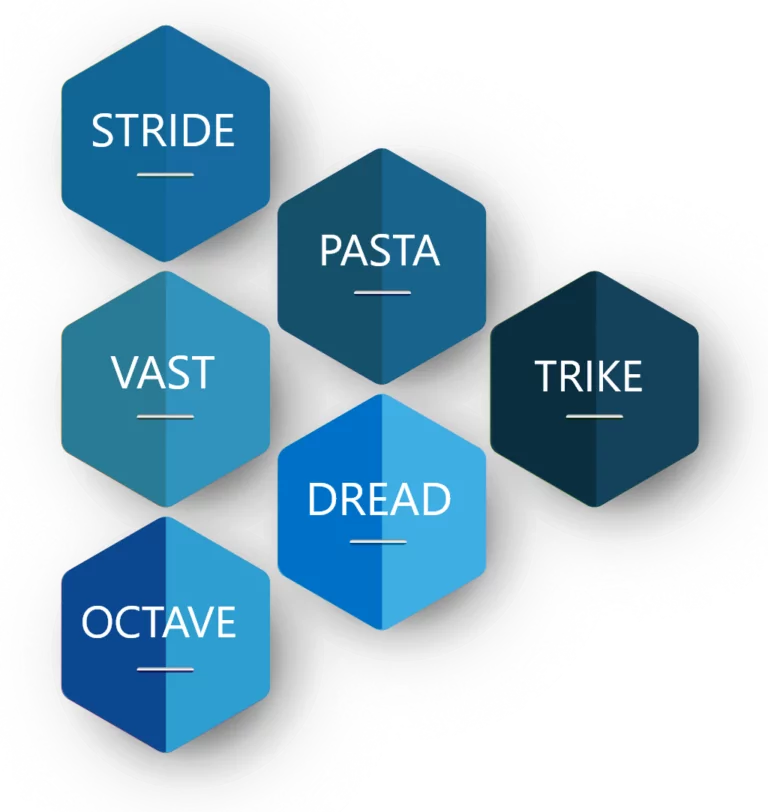
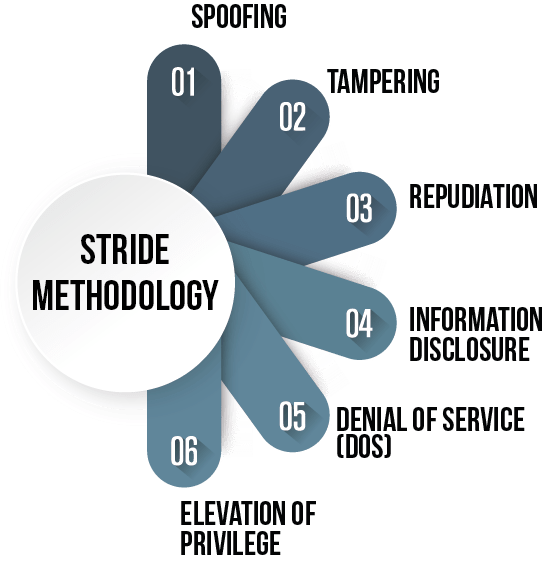
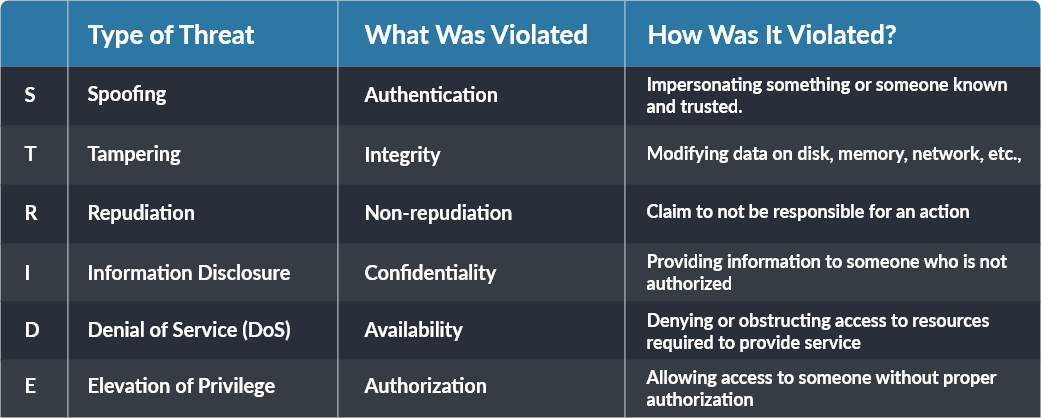
STRIDE is an approach to threat modeling developed by Loren Kohnfelder and Praerit Garg in 1999 to identify potential vulnerabilities and threats to your products.
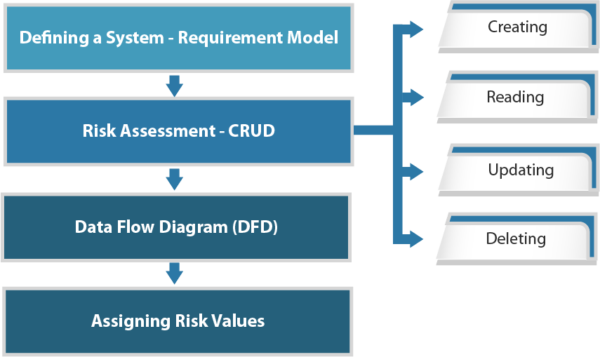
TRIKE is an open-source threat modeling methodology that is used when security auditing from a risk management perspective. TRIKE threat modeling is a fusion of two models namely – Requirement Model and Implementations Model. The requirement model is the base of TRIKE modeling that explains the security characteristics of an IT system and assigns acceptable levels of risk to each asset. This model also enables coordination among different security teams and stakeholders by providing a conceptual framework. After this comes the implementation model. In this model, a Data Flow Diagram (DFD) is created to illustrate the flow of data and the user performed actions within a system. In this model, threats are analyzed to enumerate and assign a risk value. Based on this, security controls or preventive measures defined to address the threats as per the priority and assigned risks.
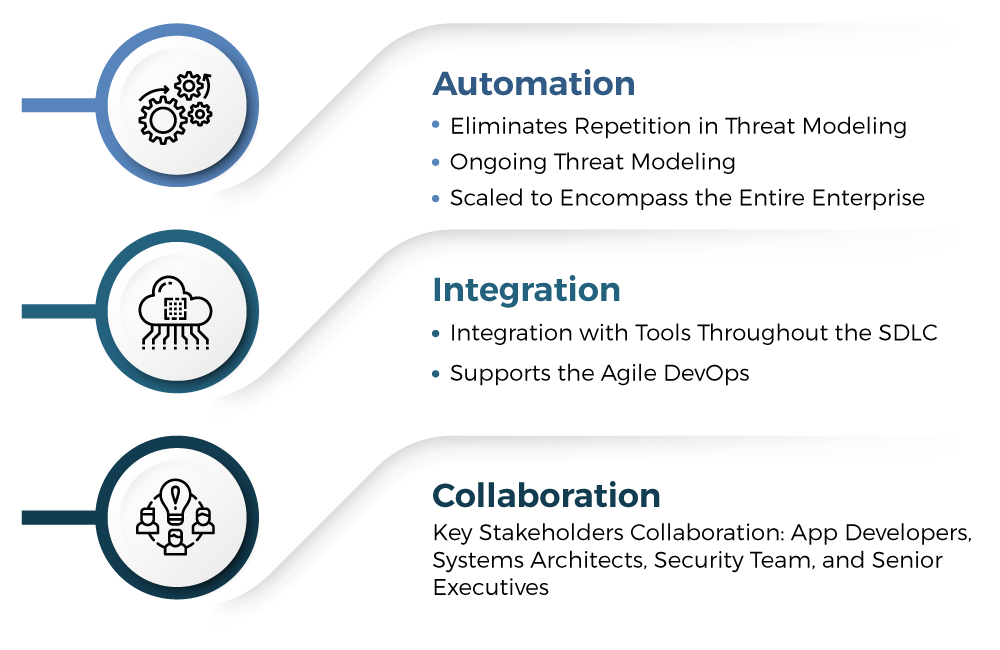
VAST (Visual, Agile, and Simple Threat) methodology is based on automated threat modeling that covers the software development life cycle across the organization with proper integration with tools and collaboration with all key stakeholders like developers, architects, security professionals, and leaders across the organization.
DREAD methodology is used to assess, analyze, and find the probability of risk by rating the threats as described in the image below.

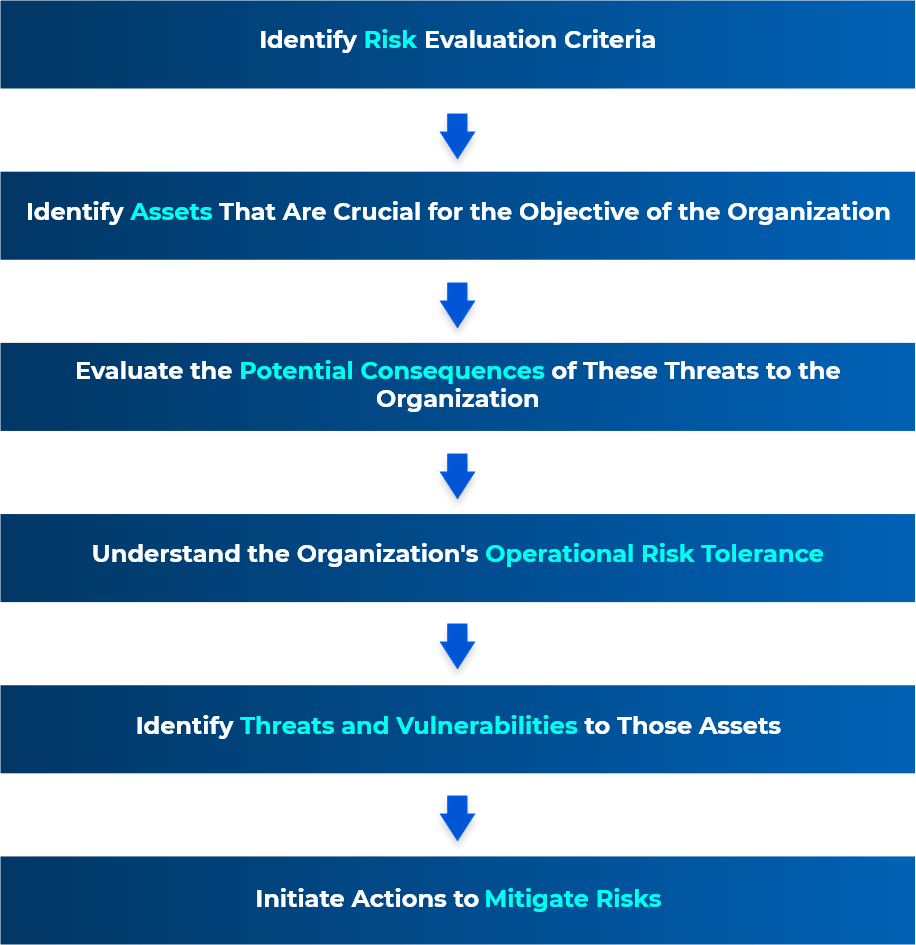
OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation) is an approach to identify, assess, and manage risks to IT assets. This process identifies the critical components of information security and the threats that could affect their confidentiality, integrity, and availability. This helps them understand what information is at risk and design a protection strategy to reduce or eliminate the risks to IT assets.
Microsoft’s Threat Modelling Tool is free and allows software architects to identify and mitigate most likely security issues at an early stage when they are comparatively easy and cost-effective to fix. Thus, reducing the total cost of development.
ThreatModeler is an automated threat modeling tool that secures and scales the enterprise software development life cycle (SDLC). It helps identify, predict, and define threats on the attack surface to make proactive security measures and reduce the overall risk.
securiCAD Professional helps create virtual models of existing and future IT environments. The attack simulations on a virtual model provides detailed insights about the security posture of the organization. This facilitates prioritizing security mitigations and compare different design alternatives. securiCAD works with intruder’s mindset and to find the most likely attack paths in your IT systems.
Iriusrisk is a threat modeling tool with architectural design and questionnaires defined by an expert system that explains the technical architecture, the features, and the security context of the application. The model has major components and a list of the potential security risks and vulnerabilities and provides specific recommended preventive measures.
SD Elements is a software security requirement management platform that allows automation of the security process. It reduces the risks and its cost by following the best practices, easily tracking the status security part of the project and fast security and compliance processes in line with Agile and DevOps methods.
The Tutamen Threat Modeling tool is designed to enable security during architecture, to minimize the cost of resolving flaws. The automation reduces human error and inconsistencies with a single input of variables. Tutamen is a living threat model that changes accordingly with the design.
OWASP Threat Dragon is an open-source threat modeling tool (both web application and desktop) that is used to create threat model diagrams, record the most likely threats, and decide the action to mitigate said threats. Threat Dragon is both an online threat modeling web application and a desktop application. It includes system diagramming as well as a rule engine to auto-generate threats and their mitigations.
Thus, threat modeling delivers more value if executed more frequently and consistently. When threat modeling is conducted on a consistent basis throughout an organization, secure architecture patterns start emerging that can be documented and leveraged by security and development teams.
"*" indicates required fields
"*" indicates required fields