
Become a Certified Ethical Hacker (C|EH) Compete
"*" indicates required fields
CERTIFIED PROFESSIONALS
IN 145 COUNTRIES







CERTIFIED PROFESSIONALS
IN 145 COUNTRIES






Become a Certified Ethical Hacker (C|EH) Compete
"*" indicates required fields
New Ethical Hacking Challenges Every Month
Windows Wreckage: Unraveling Code & Hunting Threats
Scenario:
You are a security analyst for a leading cybersecurity firm investigating a critical incident involving a large financial corporation. The corporation recently suffered a sophisticated cyberattack that exploited vulnerabilities in one of its custom-built Windows applications. The attack has led to unauthorized data exfiltration, and the company’s systems are showing signs of compromise from unknown malware variants.
Your Mission:
An encrypted Windows application suspected of containing malicious code has been recovered from a compromised machine. Your first task is to reverse-engineer the application to identify the malware, understand its functionality, and uncover any backdoors or embedded payloads used to exfiltrate sensitive data.
While analyzing the reverse-engineered application, your team must also perform threat hunting across the company’s Windows-based infrastructure. The attackers have left traces in system logs, hidden processes, registry keys, and artifacts buried deep in memory. Your objective is to track the attacker’s movements, identify persistence mechanisms, and neutralize the threat.
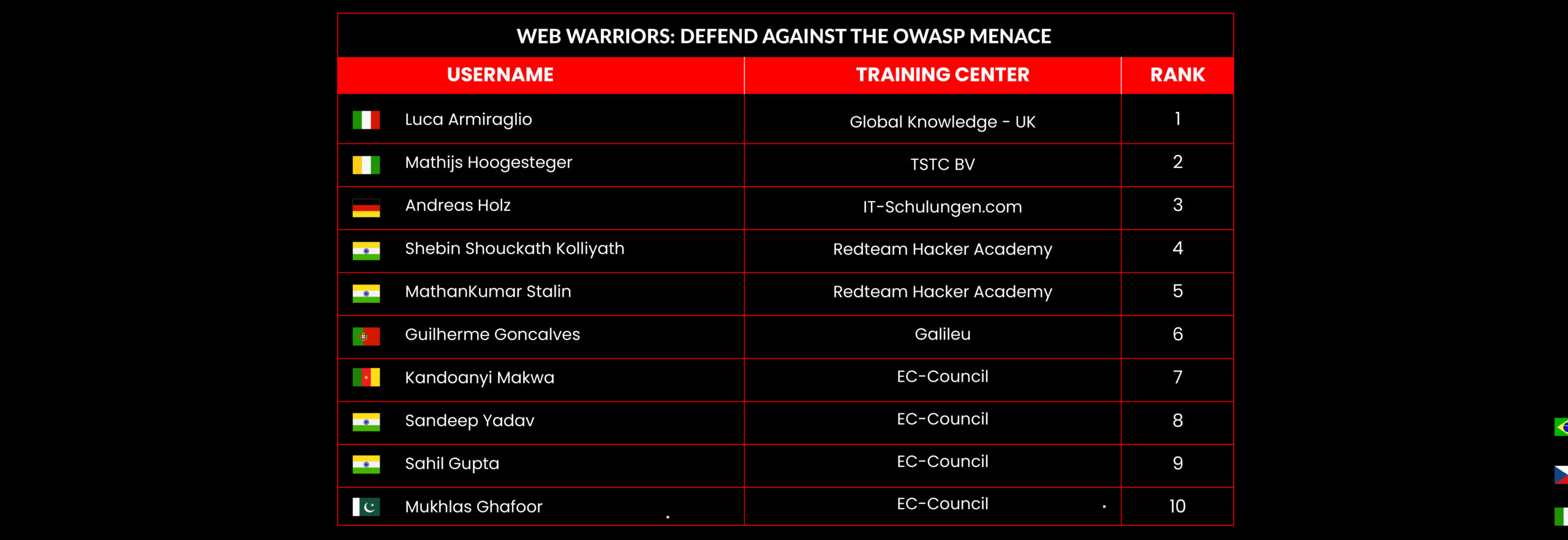
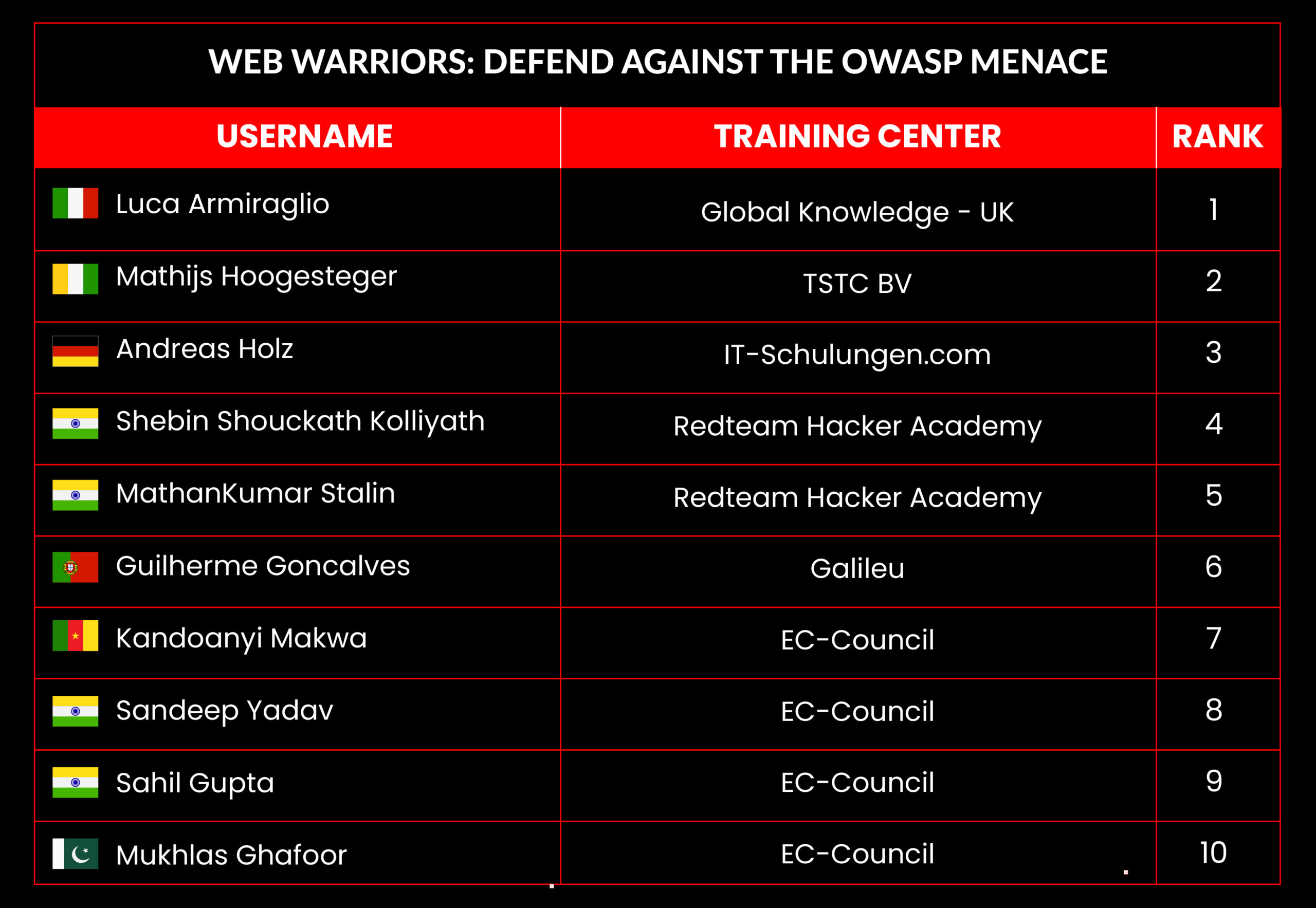
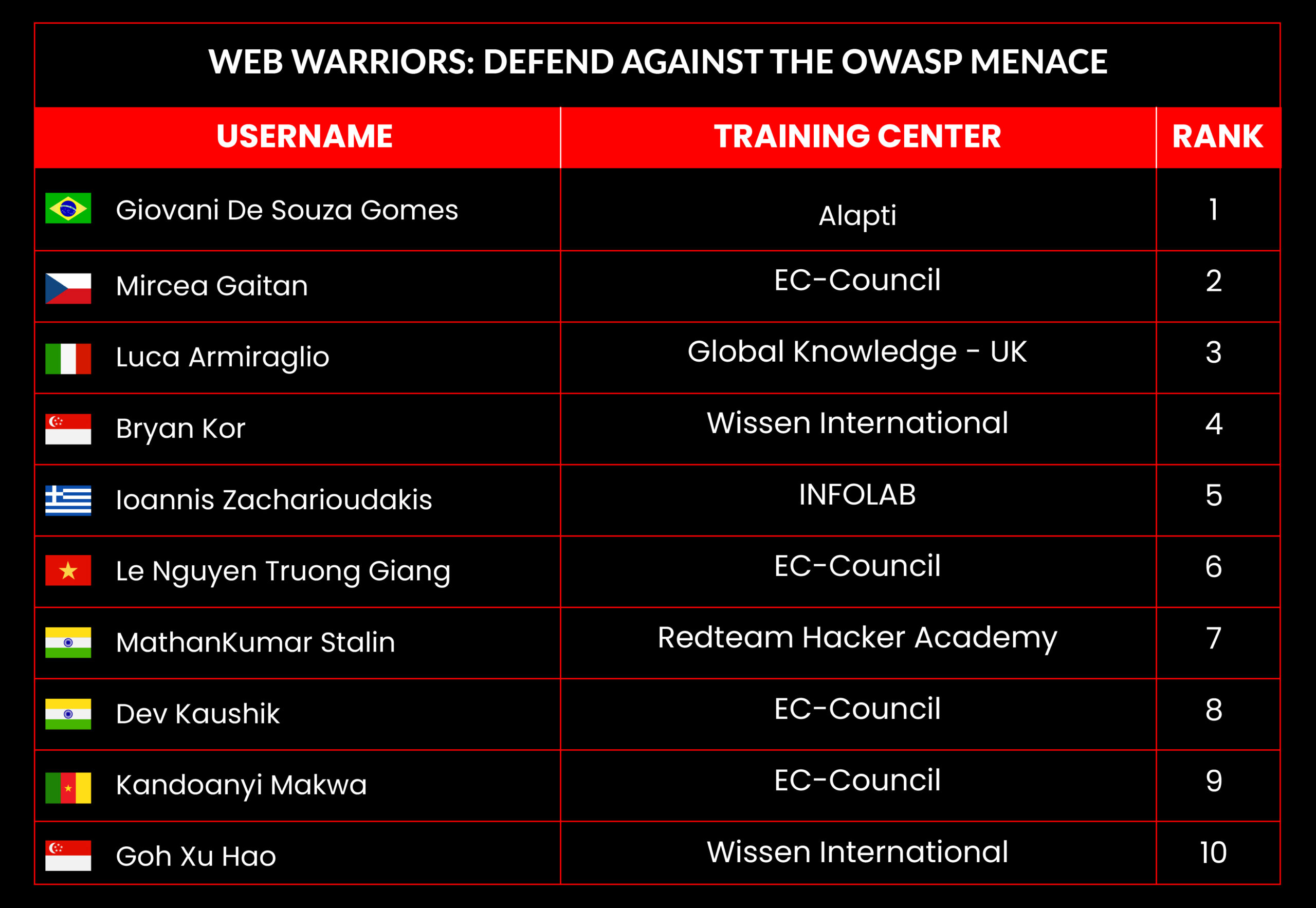
Web Warriors: Defend Against the OWASP Menace
Scenario:
You are a security analyst hired by a tech company, WebSec Solutions, which specializes in e-commerce platforms. Recently, they have suffered multiple security breaches due to various web application vulnerabilities, which have impacted their customer data and financial transactions.
Your Mission:
The company suspects that attackers are exploiting several vulnerabilities within their web applications and configurations. Your task is to assess their web infrastructure and uncover these vulnerabilities before malicious actors exploit them further.
You will investigate vulnerabilities aligned with the OWASP Top 10 Web Application Threats, including SQL injection, security misconfigurations, broken authentication, cross-site scripting, etc. Each challenge will simulate real-world attacks, and you’ll need to identify, exploit, and mitigate these vulnerabilities to strengthen WebSec Solutions’ defenses.
Operation ATT&CK Unveil: Decoding Cyber Tactics
Scenario:
As a member of an elite cybersecurity defense team, you’ve been called to investigate a sophisticated breach within a critical infrastructure network. Intelligence points to a notorious APT (Advanced Persistent Threat) group known for leveraging tactics from the MITRE ATT&CK framework to target global organizations.
Your Mission:
In this challenge, you must track the adversary’s movements, detect breaches, and remediate attacks by identifying and mitigating various stages of their kill chain. The attackers have already infiltrated the network using phishing tactics, but their end goal remains unclear.
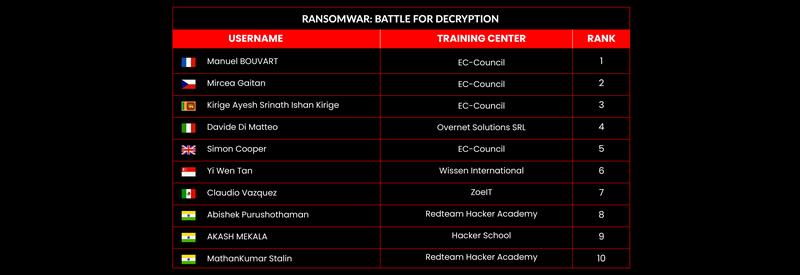
RansomWar: Battle for Decryption
Scenario:
In this challenge, participants take on the role of cybersecurity experts hired by a large multinational company, Xenovate Corp, which has been hit by a devastating ransomware attack. The ransomware, known as IronCrypt, has encrypted critical servers and databases, halting all operations and putting sensitive customer and financial data at risk.
Your Mission:
The attacker has demanded a hefty ransom in cryptocurrency, threatening to leak sensitive information if the demand is not met within 72 hours. However, the company refuses to pay and seeks your expertise to investigate, mitigate, and recover from the attack.
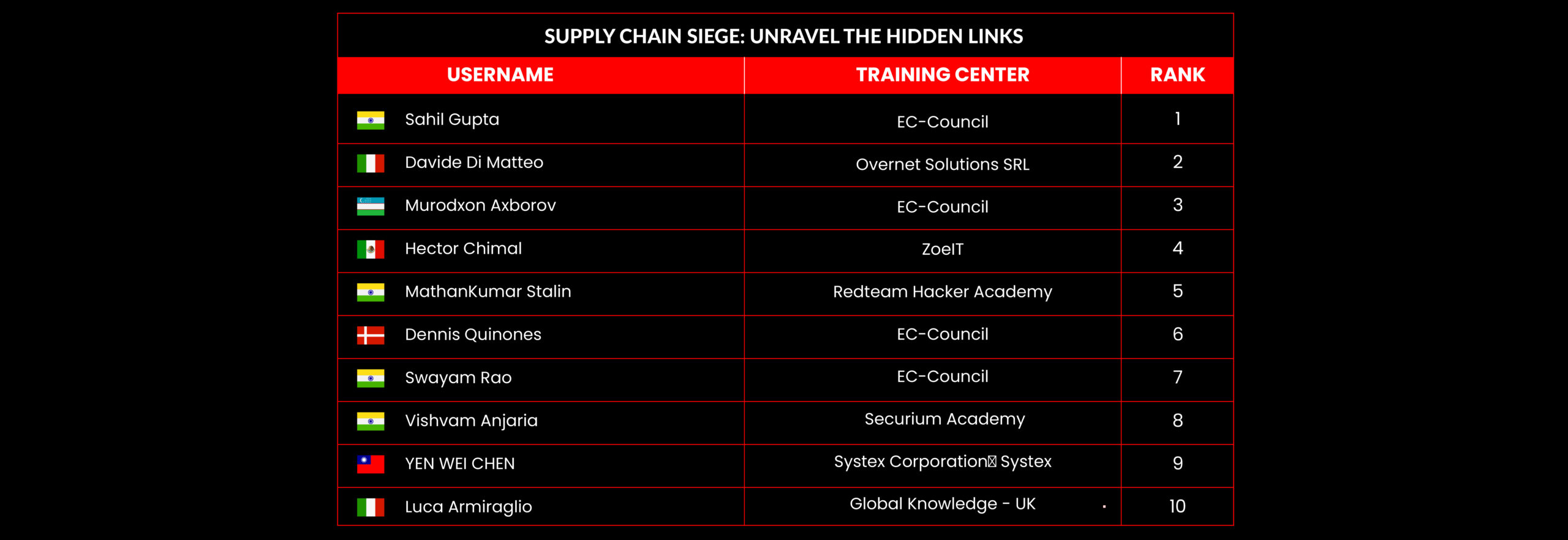
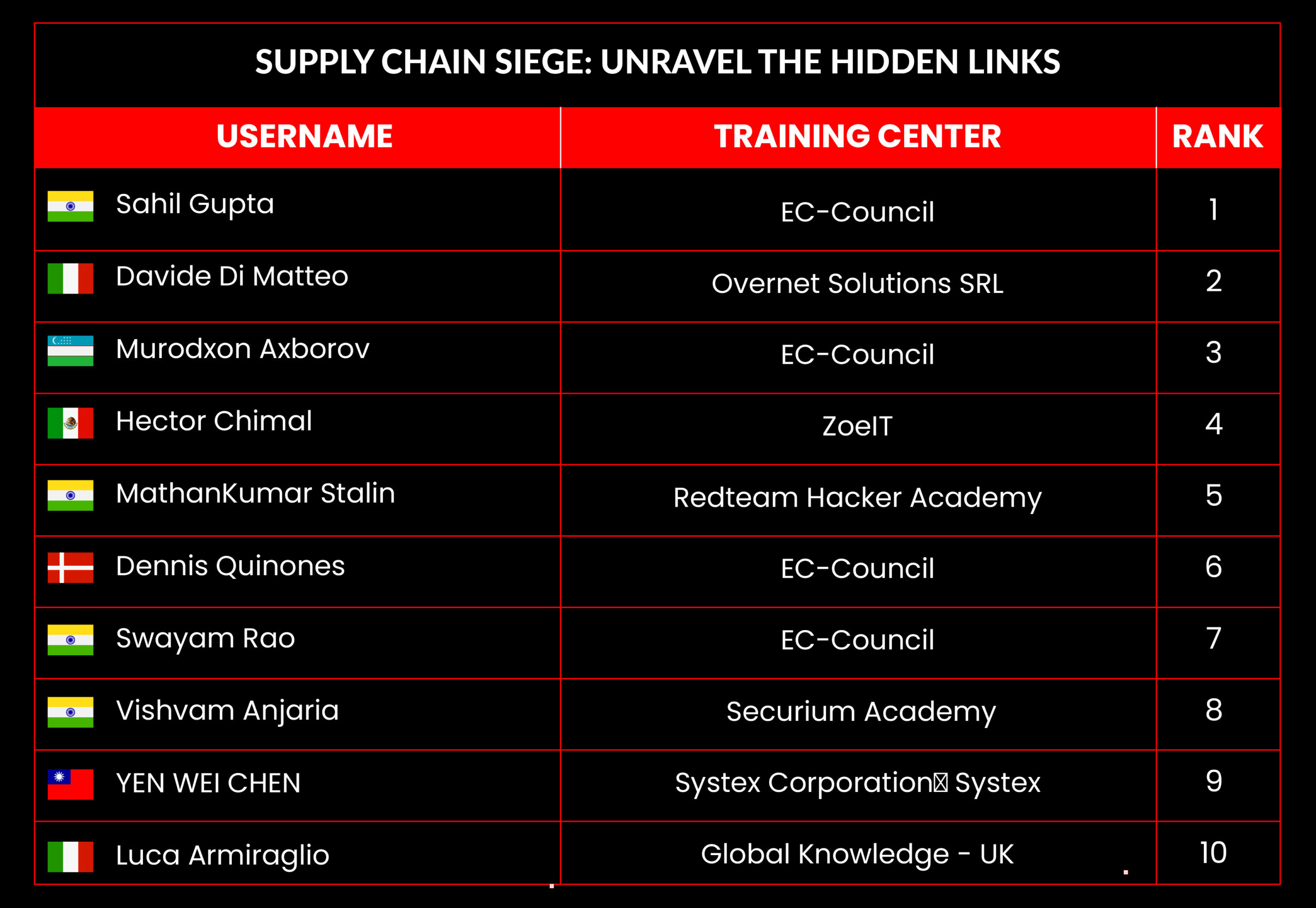
Supply Chain Siege: Unravel the Hidden Links
Scenario:
A major tech company, TechChain Inc., has recently experienced a mysterious breach affecting its production systems. Critical software updates sent to thousands of customers have been compromised, causing widespread disruptions and potential data leaks. Initial investigations reveal that the attack originated from a vulnerable third-party supplier within their software supply chain.
Your Mission:
As a cybersecurity expert, you have been recruited to uncover the full extent of the breach. Your mission is to investigate the supply chain vulnerabilities, trace the origin of the malicious code, and neutralize any remaining threats. Along the way, you will encounter various challenges involving reverse engineering, secure code analysis, exploiting weak dependencies, and identifying compromised components.
The fate of TechChain Inc. and its customers rests on your ability to expose the hidden links of the supply chain attack and prevent future threats. Time is running out—can you stop the siege before it’s too late?
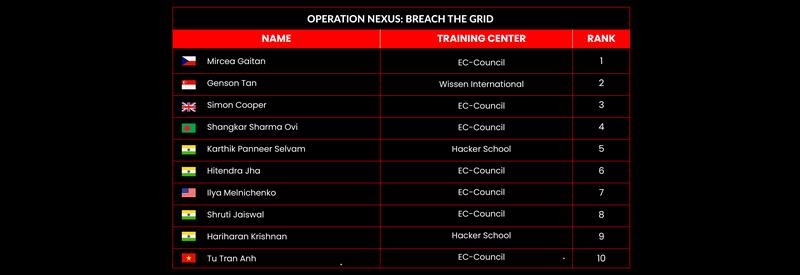
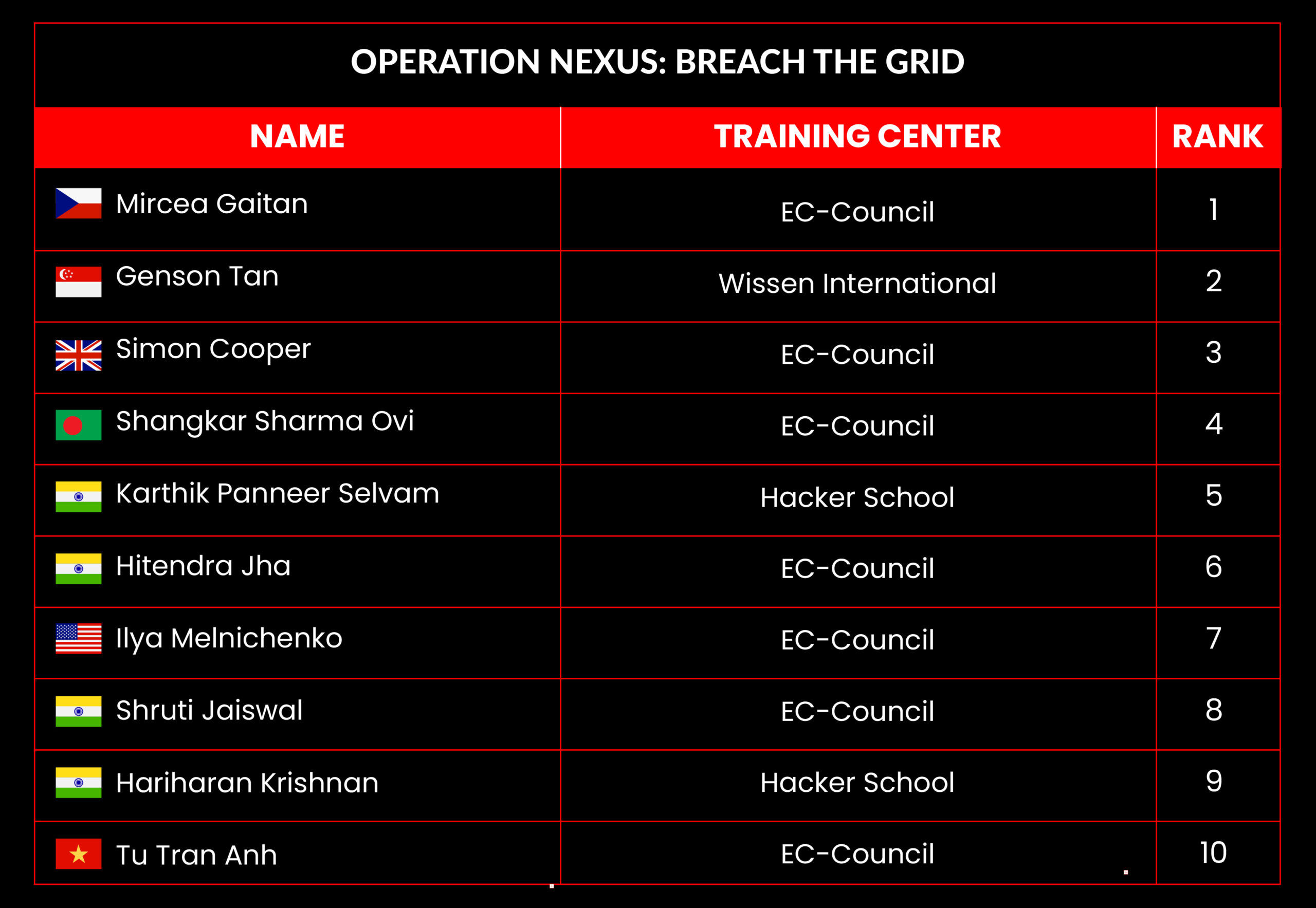
Operation Nexus: Breach the Grid
Scenario:
A powerful cybercriminal syndicate known as DarkCircuit has launched a series of coordinated attacks on critical infrastructure across the nation. Their primary target is Nexus PowerGrid, an energy company that controls the electricity and water supply for millions of people. DarkCircuit has exploited vulnerabilities in Nexus’s IoT devices and Operational Technology (OT) systems, causing rolling blackouts, disrupting water supply, and threatening national security.
Your Mission:
As an elite cybersecurity specialist, you’ve been recruited by a government task force to stop the attacks before they escalate further. Your mission is to infiltrate the compromised IoT and OT networks, identify the weak points in Nexus PowerGrid’s infrastructure, neutralize the malicious code, and bring DarkCircuit’s operations to a halt.
Throughout the challenge, you will face tasks that test your ability to hack, defend, and secure critical IoT and OT systems. These will range from identifying weak IoT protocols to exploiting industrial control system (ICS) vulnerabilities and performing real-time incident response.
The nation’s critical infrastructure is under siege, and time is running out. Can you breach DarkCircuit’s defenses and save Nexus PowerGrid before the system collapses?
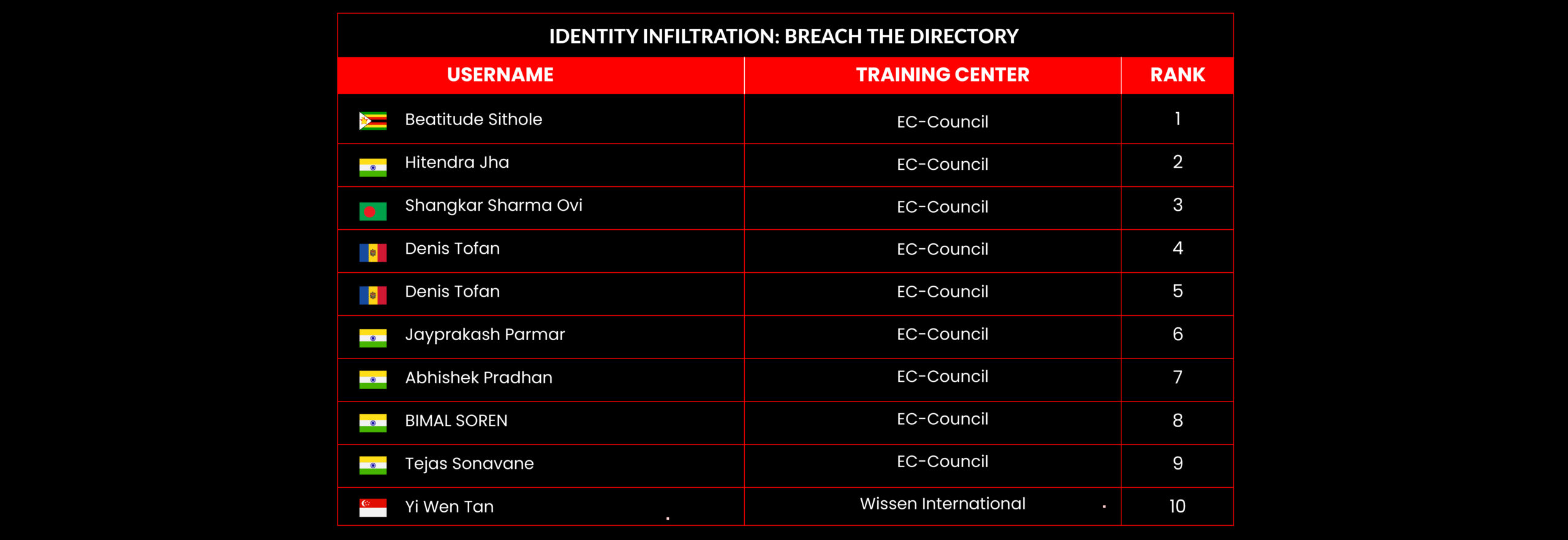
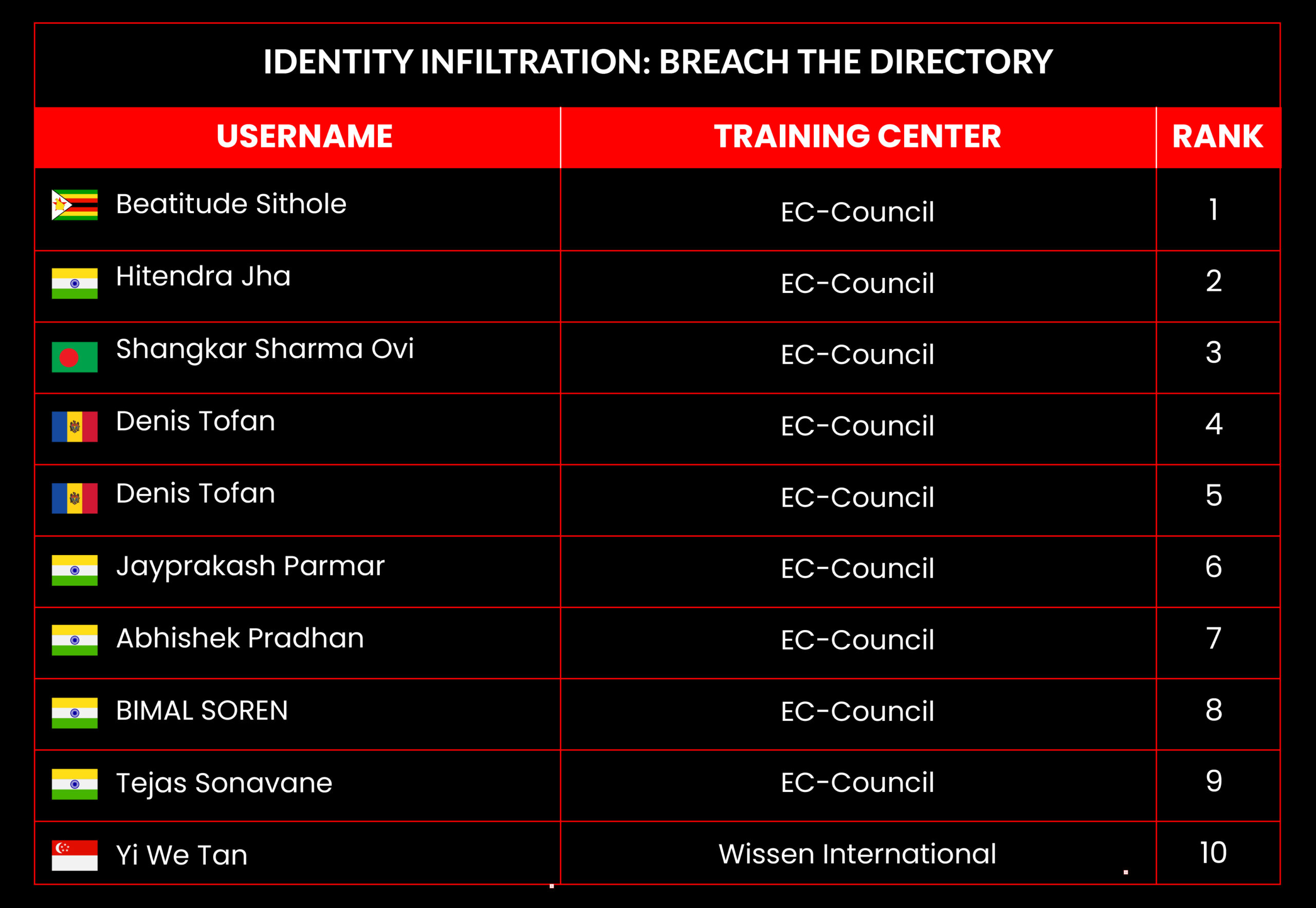
Identity Infiltration: Breach the Directory
Scenario:
A global financial institution, SecureBank, has reported unusual activity within its network. Several high-level user accounts behave suspiciously, accessing sensitive areas and exfiltrating critical data. The internal security team suspects that attackers have breached the Active Directory (AD) infrastructure, compromising key accounts and leveraging identity-driven attacks to move laterally through the network undetected.
Your Mission:
As a top cybersecurity analyst, you’ve been called to investigate and neutralize the threat. To maintain persistence, the attackers use sophisticated tactics, including credential theft, Pass-the-Hash, Golden Ticket attacks, and AD misconfigurations. They have already created multiple backdoor accounts to ensure continuous access.
Your task is to identify how the attackers gained initial access, uncover their foothold in the AD infrastructure, and shut down their lateral movement across the network. You must understand identity attacks, analyze AD logs, and reverse unauthorized privileges to prevent further damage.
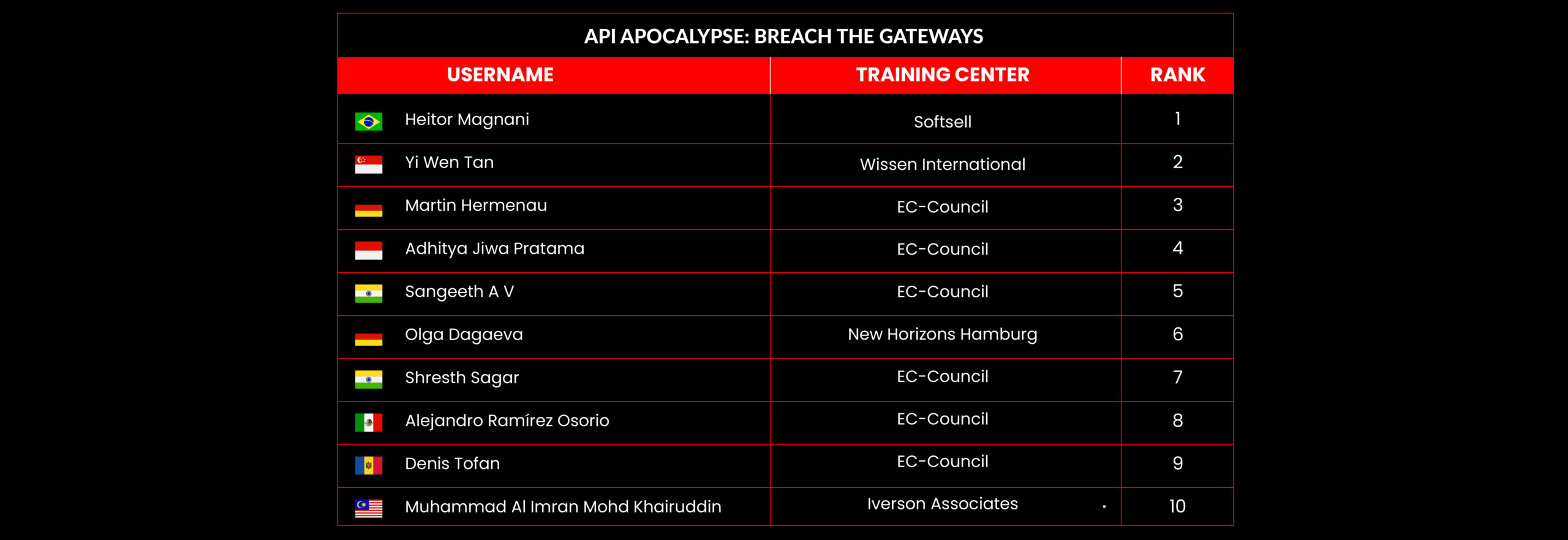
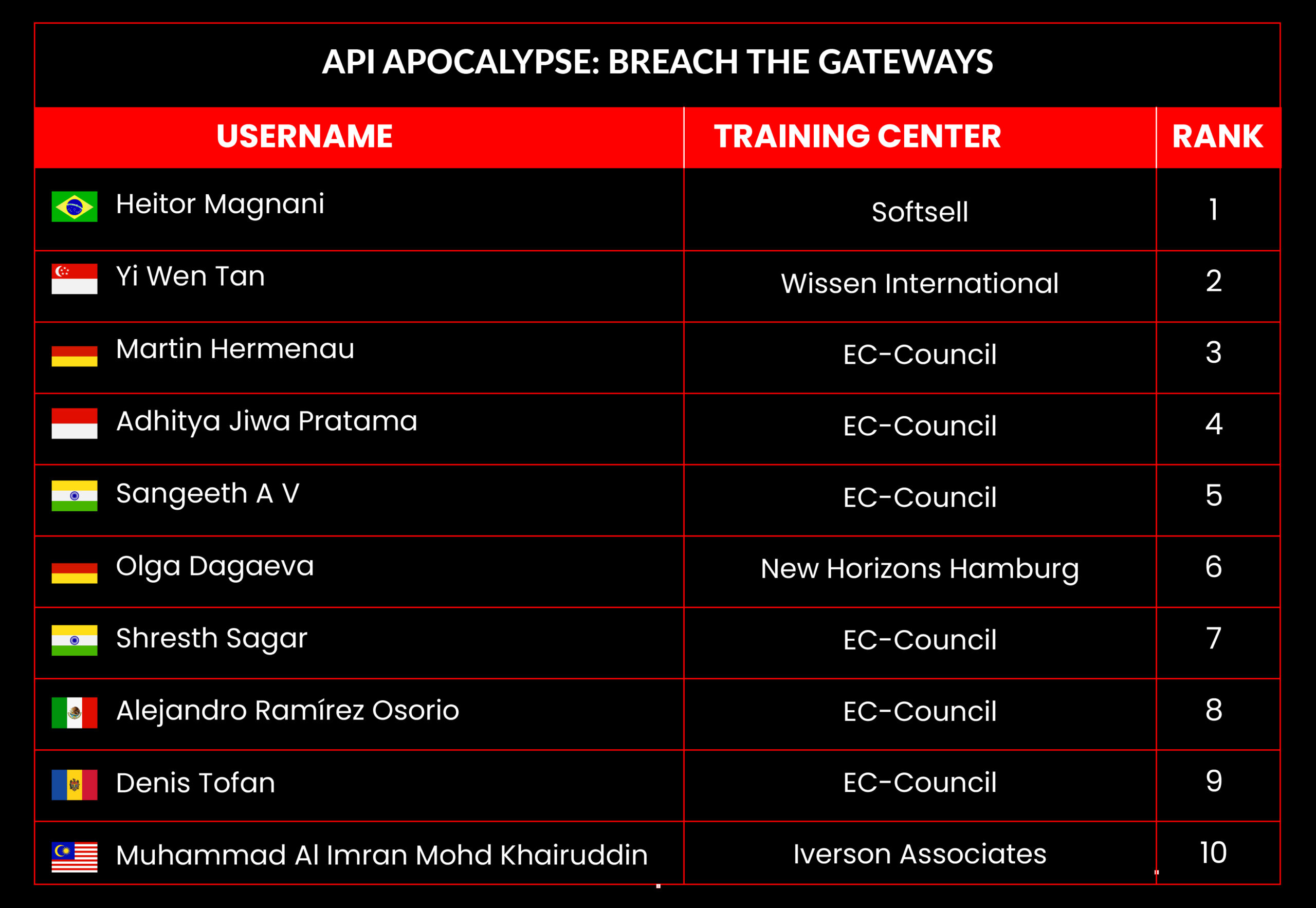
API Apocalypse: Breach the Gateways
Scenario:
In a world where interconnected systems rely heavily on APIs for communication, a leading fintech company, SecurePay, has become the target of a devastating cyber-attack. Hackers have discovered vulnerabilities in the company’s API infrastructure, allowing them to bypass authentication, access sensitive customer data, and disrupt critical financial services.
Your Mission:
As a skilled cybersecurity professional, you are tasked with investigating the breach, securing the exposed APIs, and tracking the attackers before they cause further damage. Throughout the challenge, you will encounter real-world API security issues such as broken authentication, excessive data exposure, rate-limiting bypass, and injection attacks.
The integrity of SecurePay’s customer data and the company’s reputation now rests on your ability to identify and exploit the flaws within their API architecture. Time is of the essence; can you stop the ‘API Apocalypse’ and restore order before the hackers fully compromise the system?
Data Fortress Breach: Cracking the Core
Scenario:
FortifyBank, a global financial institution, prides itself on having one of the most secure database infrastructures in the industry. However, a recent intrusion attempt has raised alarms within its cybersecurity team. An unknown group of attackers is actively targeting the bank’s critical database servers to exfiltrate sensitive customer data, including financial transactions and personal information.
Your Mission:
As part of a specialized cyber incident response team, you have been tasked with investigating the vulnerabilities in FortifyBank’s database infrastructure. The attackers have already exploited weak configurations, obscure injection points, and privilege escalation paths to establish a foothold in the system. Your mission is to track down the attackers, patch the exploited vulnerabilities, and recover stolen data.
Throughout this mission, you will face challenges that involve SQL injection, improper database permissions, misconfigured backups, and auditing security weaknesses in the database architecture.
Operation Deep Breach: Hack, Escalate, Pivot
Scenario:
A covert hacker collective known as DarkPulse has infiltrated the network of a high-security government agency. They’ve gained initial access to a low-level server, but their ultimate goal is to breach the agency’s most classified systems. To stop them, a team of elite cybersecurity professionals has been assembled to retrace DarkPulse’s steps, understand their tactics, and neutralize the threat.
Your Mission:
As one of the top cybersecurity experts on the team, your mission is to hack into the network, escalate privileges, and pivot through various layers of security—just as DarkPulse did. You’ll need to uncover hidden backdoors, bypass advanced firewalls, and use lateral movement techniques to gain deeper access. Along the way, you will encounter double-pivot scenarios that require you to chain multiple exploits and move through isolated network segments.
The future of national security depends on your ability to hack, escalate, and pivot more deeply into the network to uncover DarkPulse’s hidden tracks and secure the system before it completes its mission.
eCommerce Rampage: Defend the Digital Marketplace
Scenario:
The world’s largest online retail platform, ShopSphere, has undergone a massive cyberattack just before the holiday season. Hackers have infiltrated its e-commerce ecosystem, targeting customer payment systems, inventory management, and order-processing pipelines. Sensitive customer data, including credit card information and personal details, is at risk of being stolen and sold on the dark web.
Your Mission:
As part of an elite cybersecurity response team, your task is to investigate the vulnerabilities exploited by the attackers, mitigate ongoing threats, and recover compromised systems. You’ll need to tackle various challenges, such as identifying fraudulent payment injections, reversing ransomware affecting inventory systems, patching vulnerabilities in APIs, and recovering stolen customer data from the dark web.
Cloud Clash: Battle for Infrastructure Security
Scenario:
A global enterprise, CloudCorp, has recently migrated its entire infrastructure to the cloud, hoping to leverage the flexibility and scalability of cloud technologies. However, just weeks after the transition, they experience a massive cyberattack targeting their cloud environment. Critical services are disrupted, sensitive data is at risk, and attackers exploit misconfigurations, API vulnerabilities, and privilege escalations within the cloud infrastructure.
Your Mission:
As a member of an elite cybersecurity team, you are tasked with defending CloudCorp’s infrastructure. The attackers have left traces of their methods behind; your mission is to uncover these indicators of compromise, neutralize the attack, and secure the environment from further breaches. You will also face challenges involving cloud misconfigurations, IAM vulnerabilities, data exfiltration detection, API abuse, and lateral movement through cloud resources.
What are the C|EH Global Challenges?
The C|EH Compete Global Challenges part of C|EHv13 Training occurs every month, providing capture-the-flag style competitions that teach students about new technologies and platforms from web applications, OT, IoT, SCADA, and ICS systems to cloud and hybrid environments. Our compete structure lets ethical hackers fight their way to the top of the leaderboard each month in these curated 4-hour CTFs.
C|EH Global Challenge Calendar
| Month | Skill Challenge |
|---|---|
| September 2024 | Off-The-Shelf CMS Exploitation |
| October 2024 | Windows Wreckage: Unravelling Code & Hunting Threats |
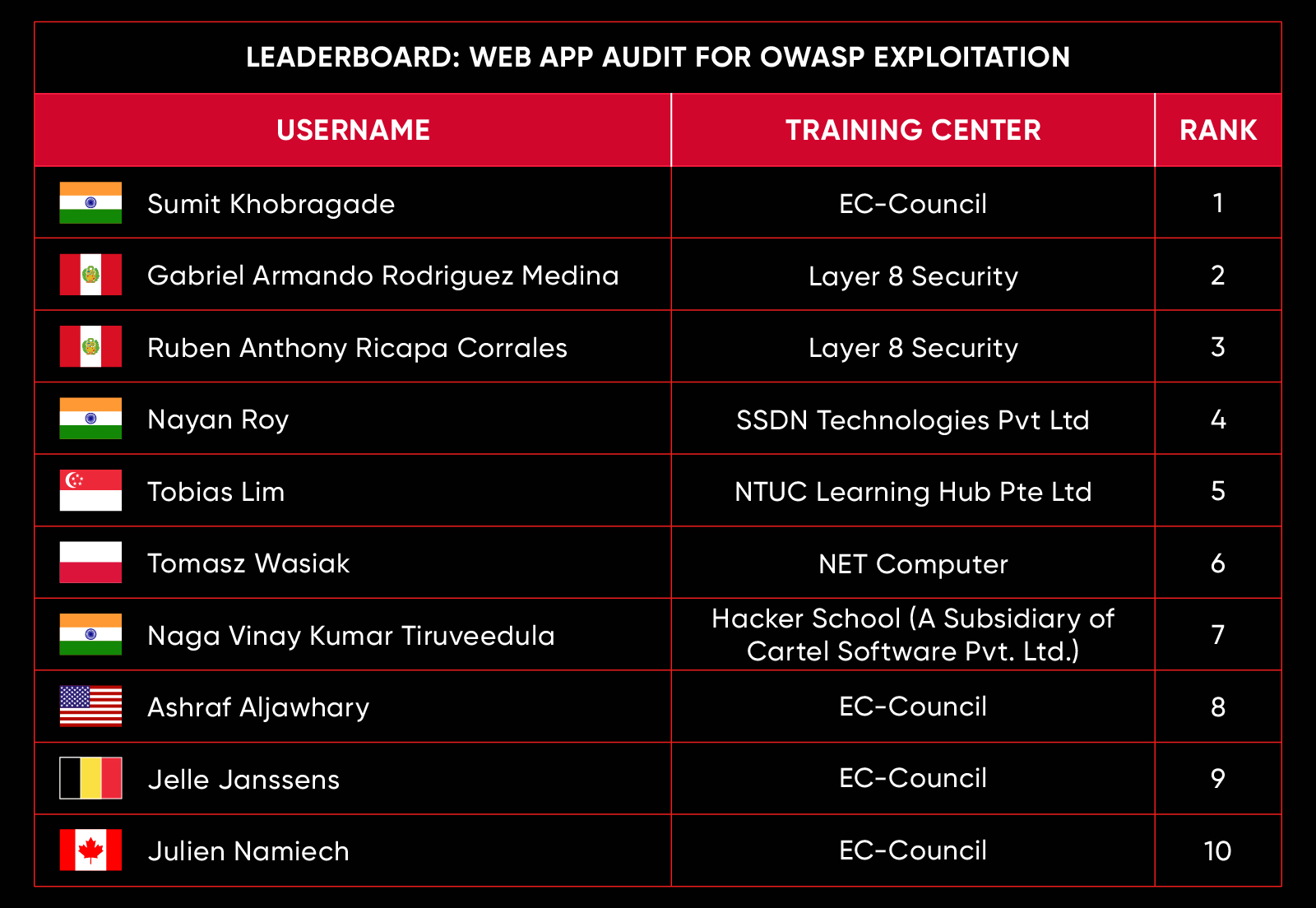
| November 2024 | Web Warriors: Defend Against the OWASP Menace |
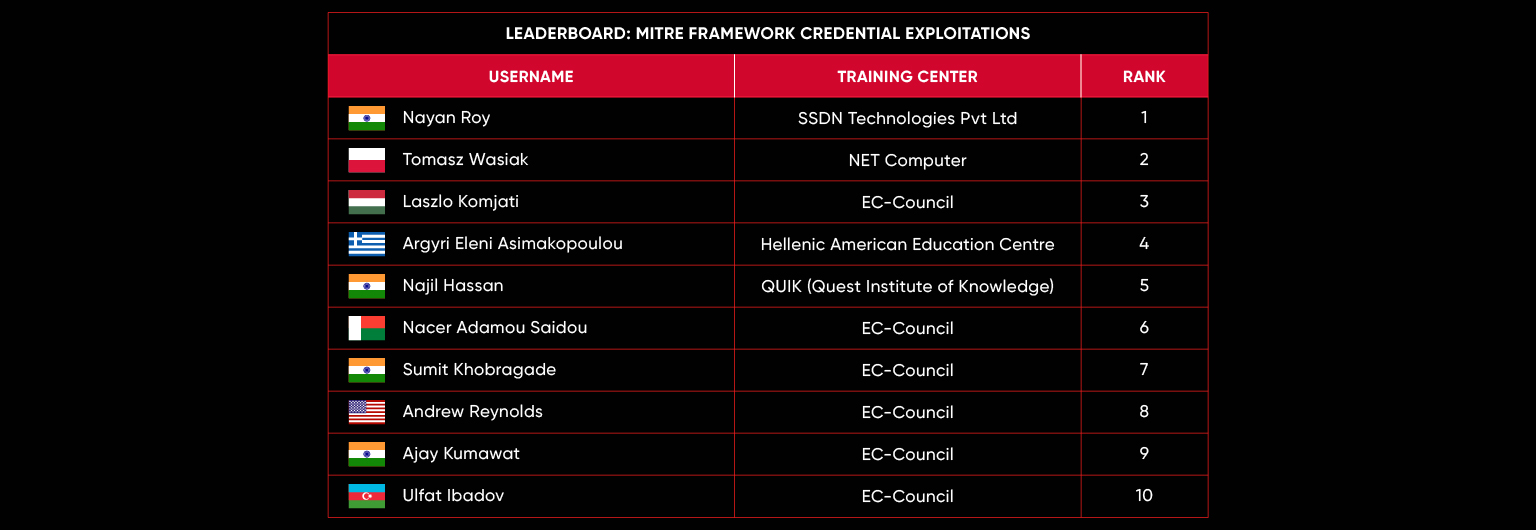
| December 2024 | Operation ATT&CK Unveil: Decoding Cyber Tactics |
| January 2025 | RansomWar: Battle for Decryption |
| February 2025 | Supply Chain Siege: Unravel the Hidden Links |
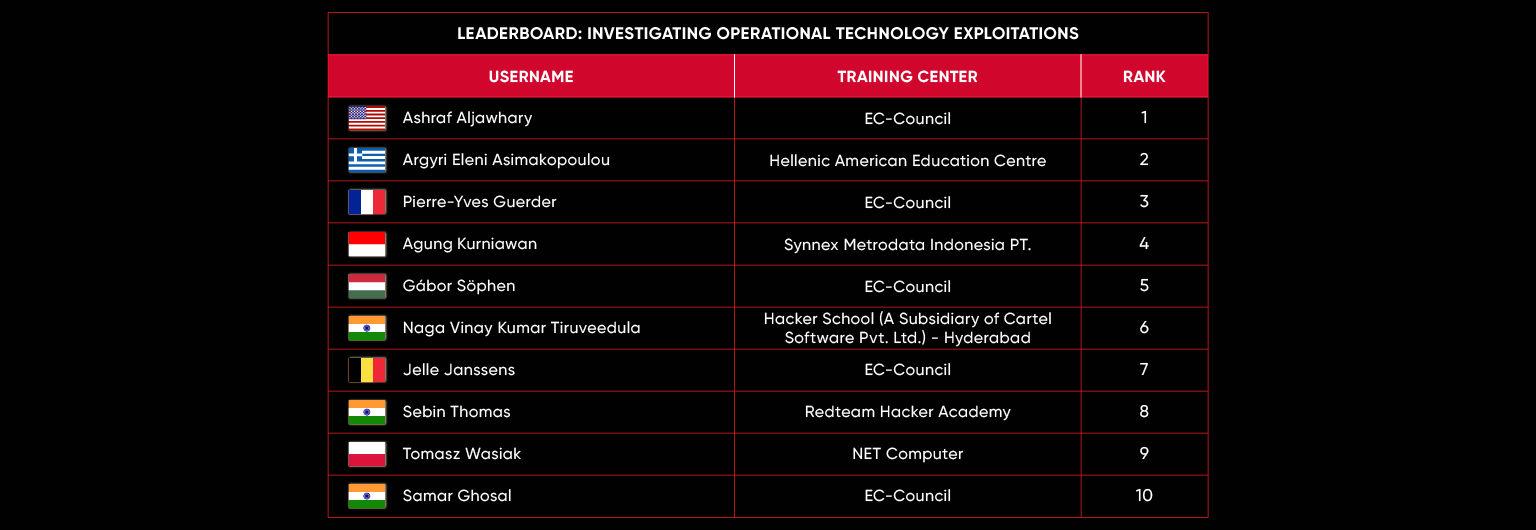
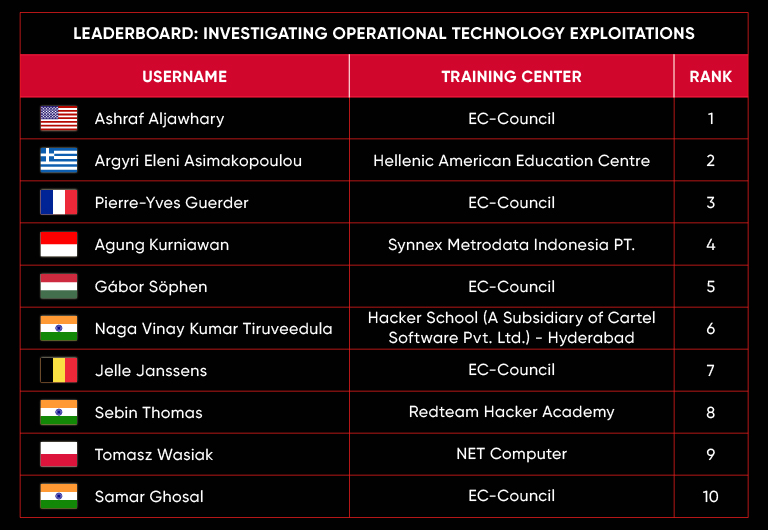
| March 2025 | Operation Nexus: Breach the Grid |
| April 2025 | Identity Infiltration: Breach the Directory |
| May 2025 | API Apocalypse: Breach the Gateways |
| June 2025 | Data Fortress Breach: Cracking the Core |
| July 2025 | Operation Deep Breach: Hack, Escalate, Pivot |
| August 2025 | eCommerce Rampage: Defend the Digital Marketplace |
| September 2025 | Cloud Clash: Battle for Infrastructure Security |
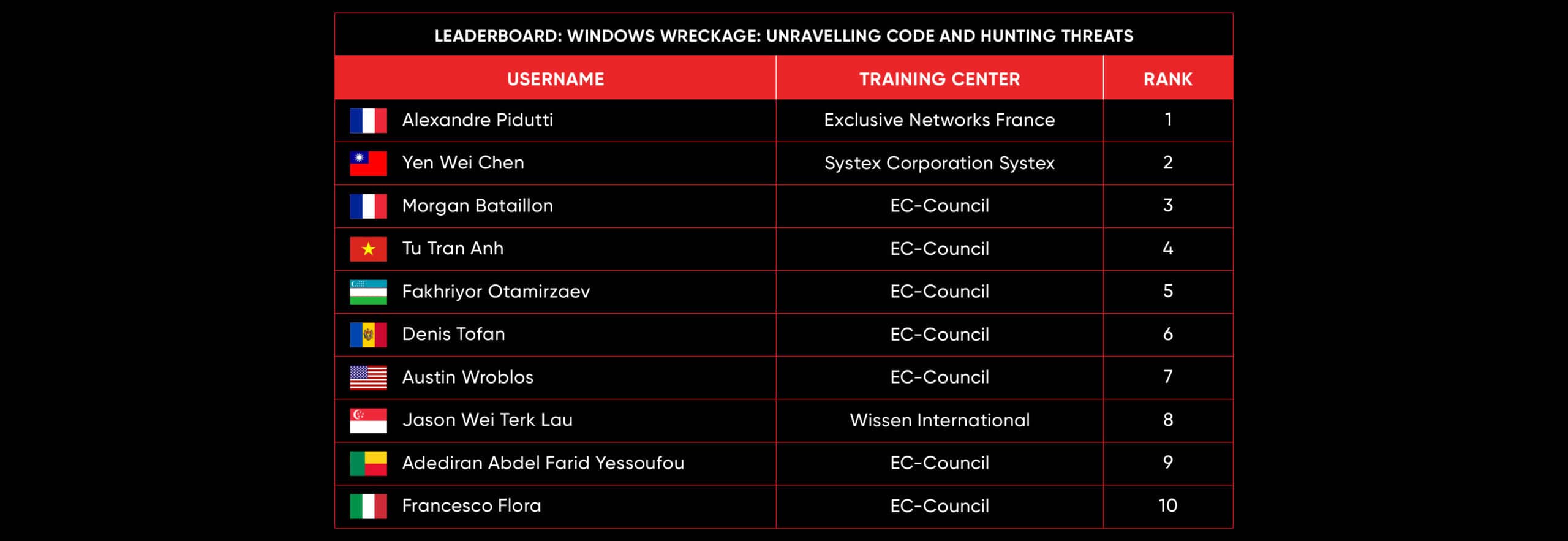
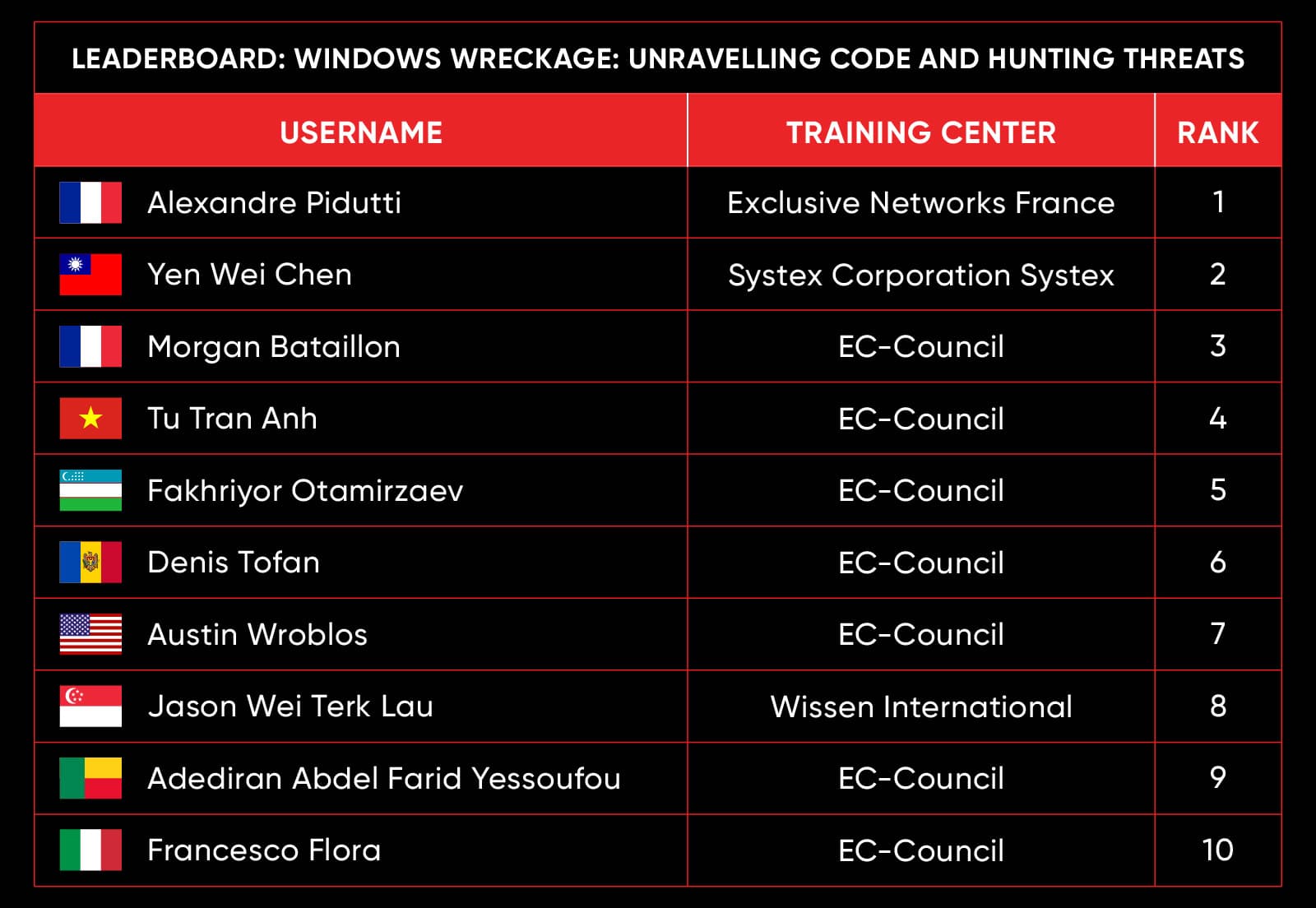
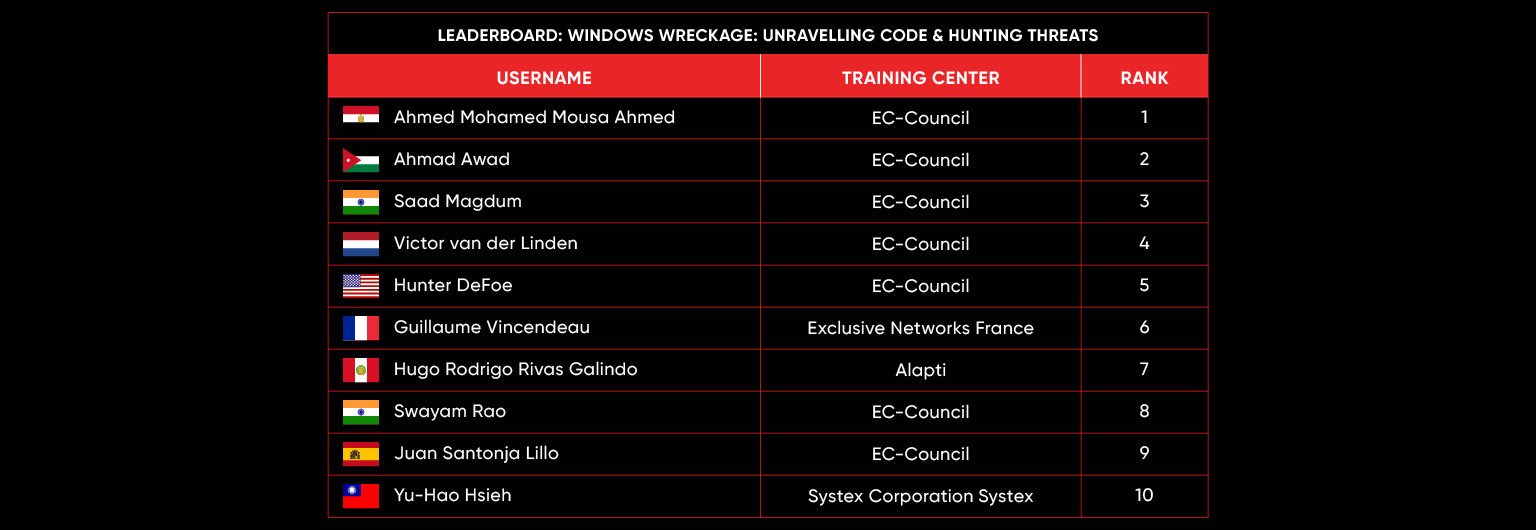
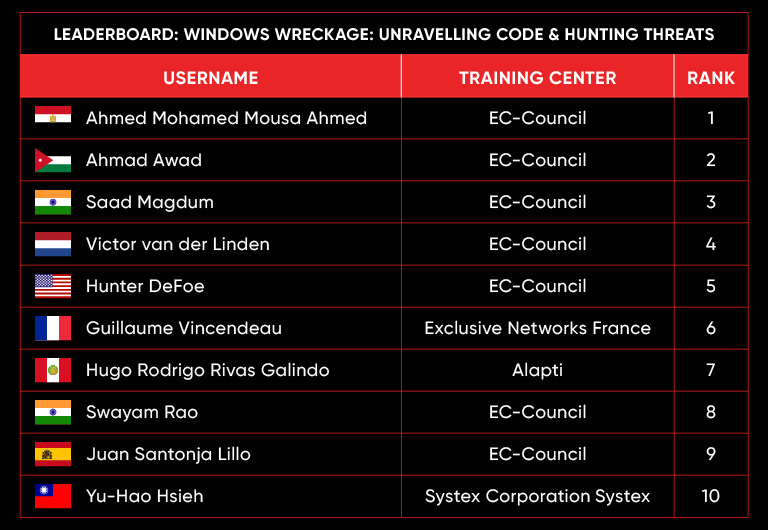
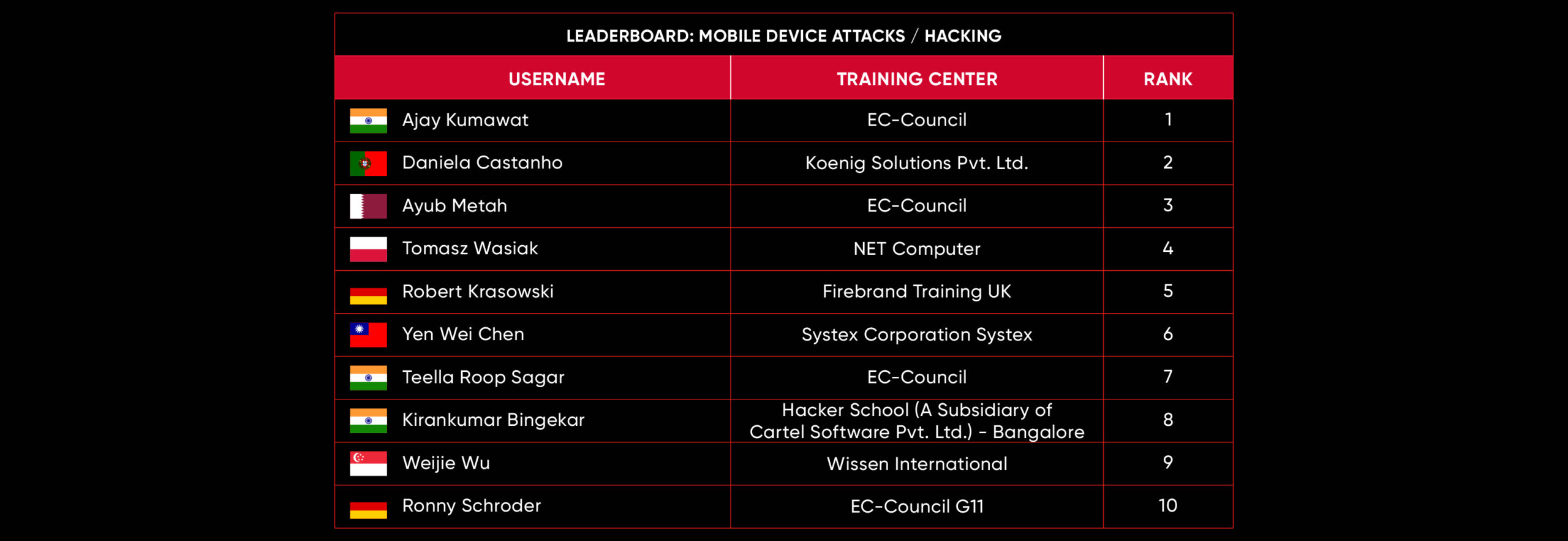
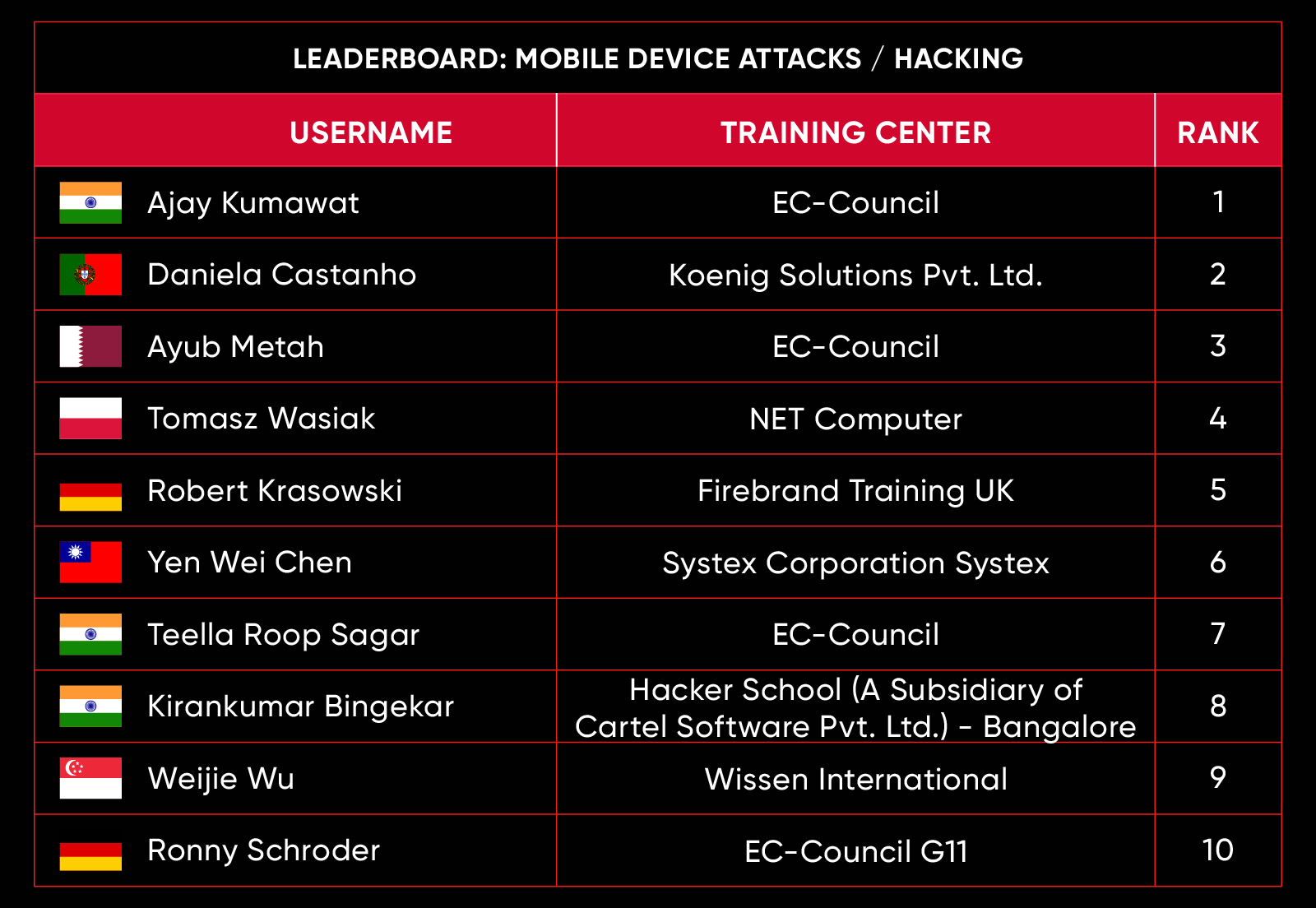
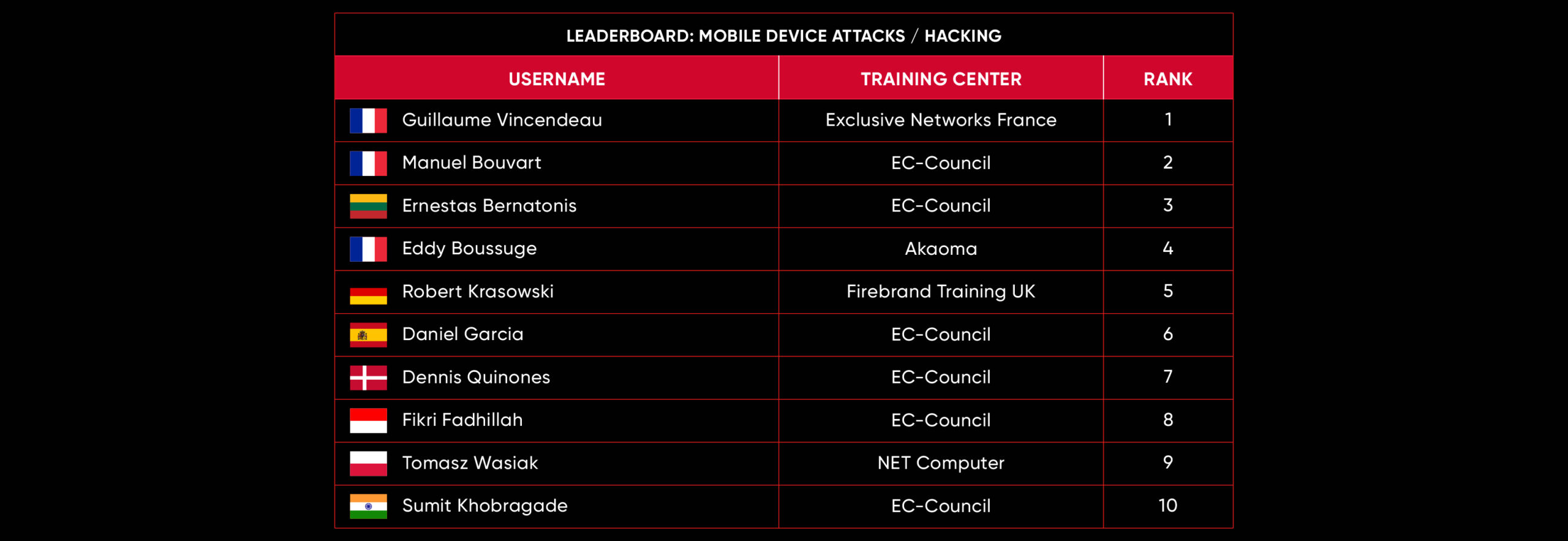
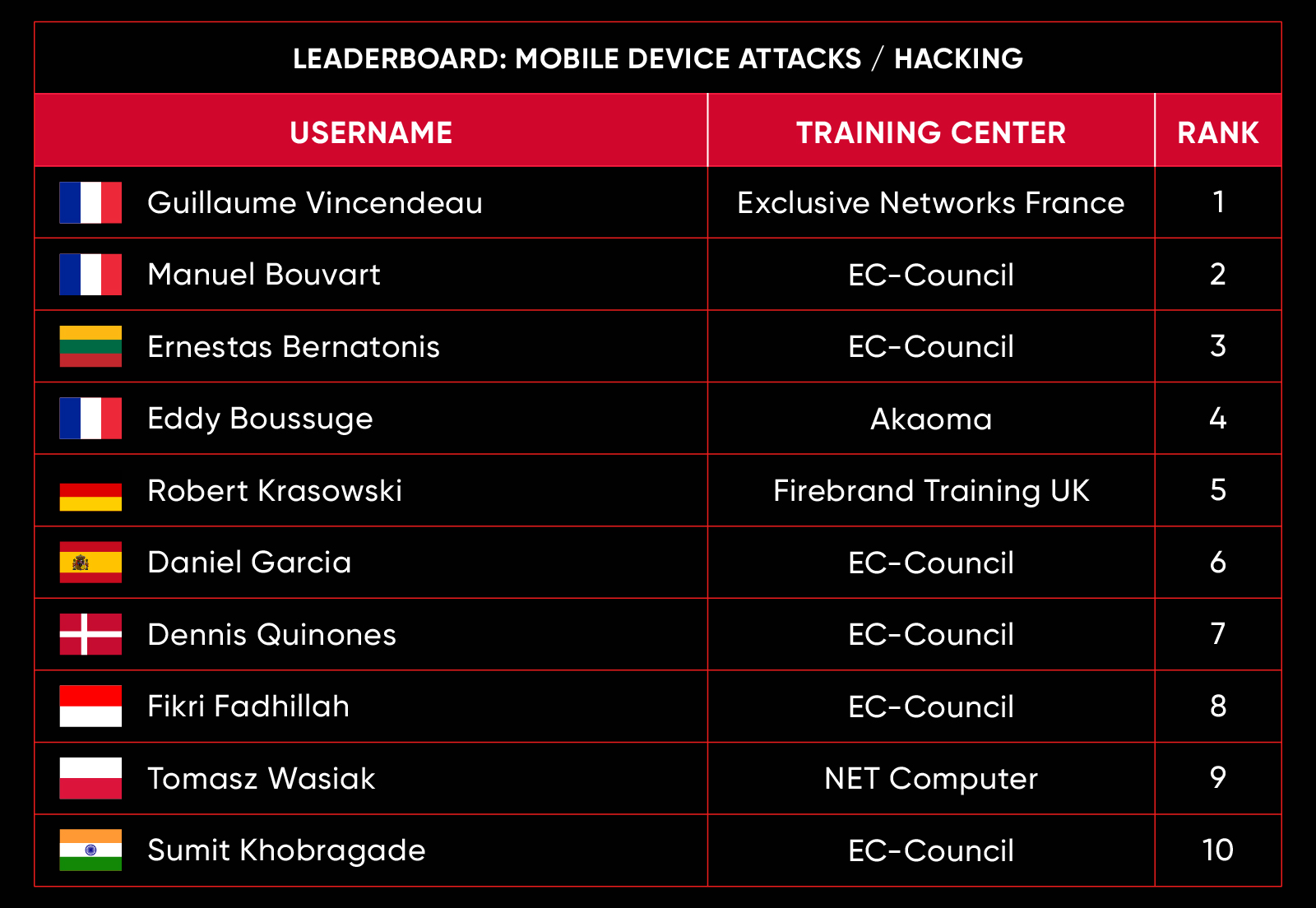
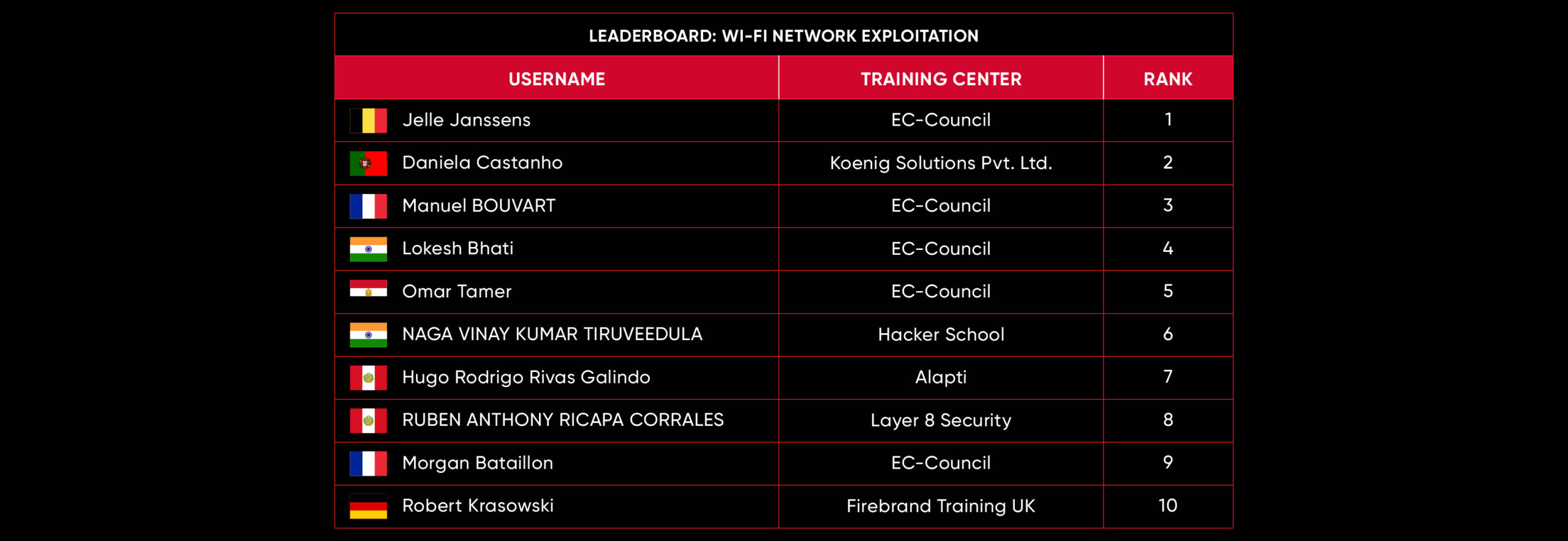
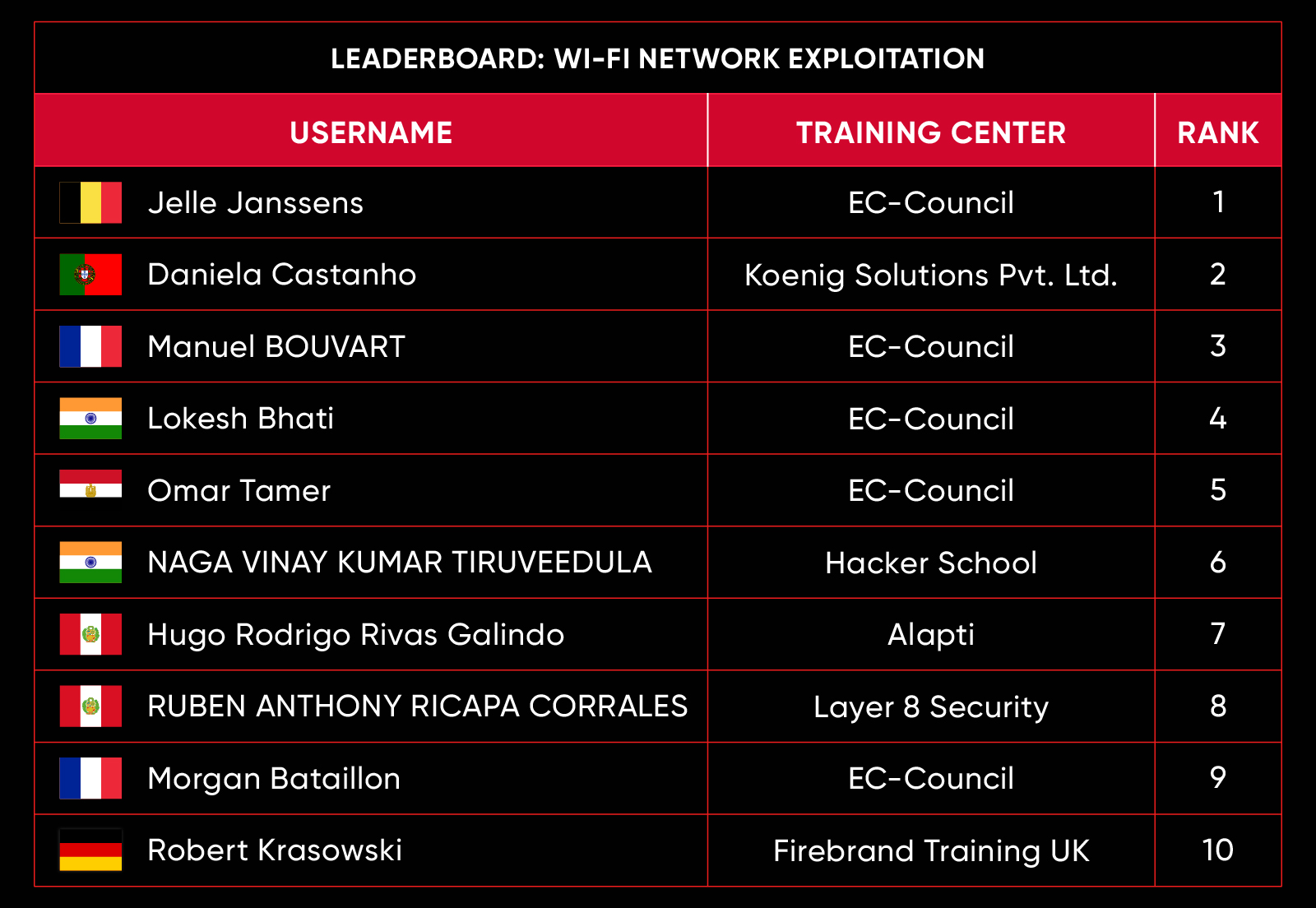
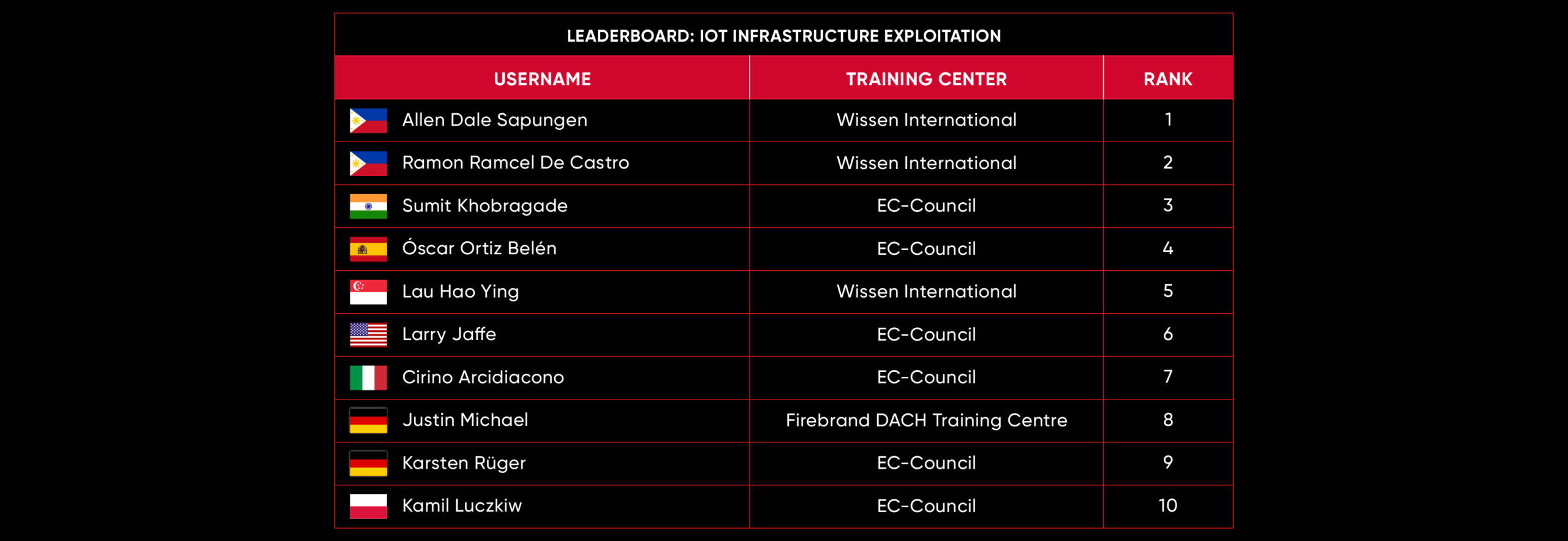
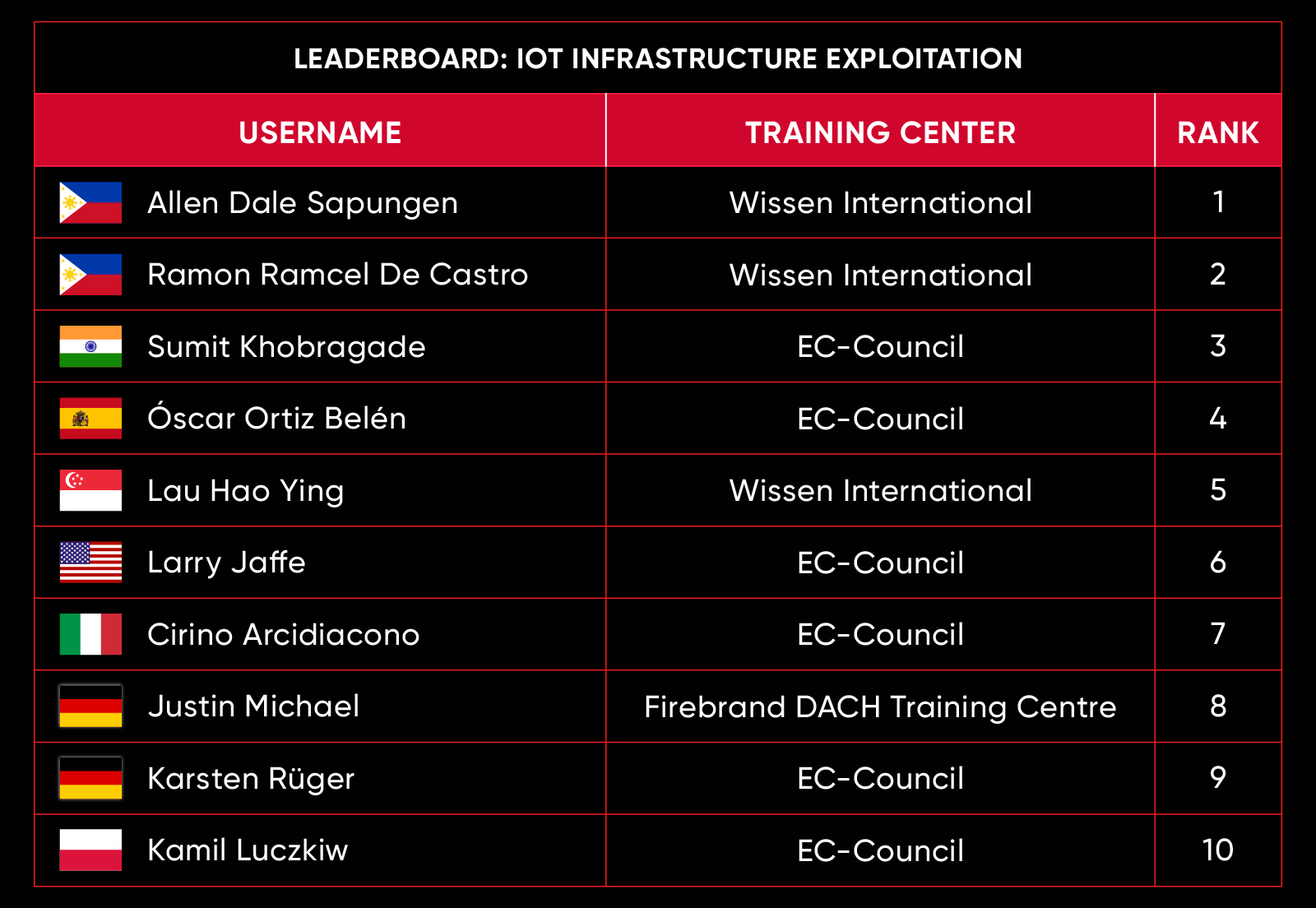
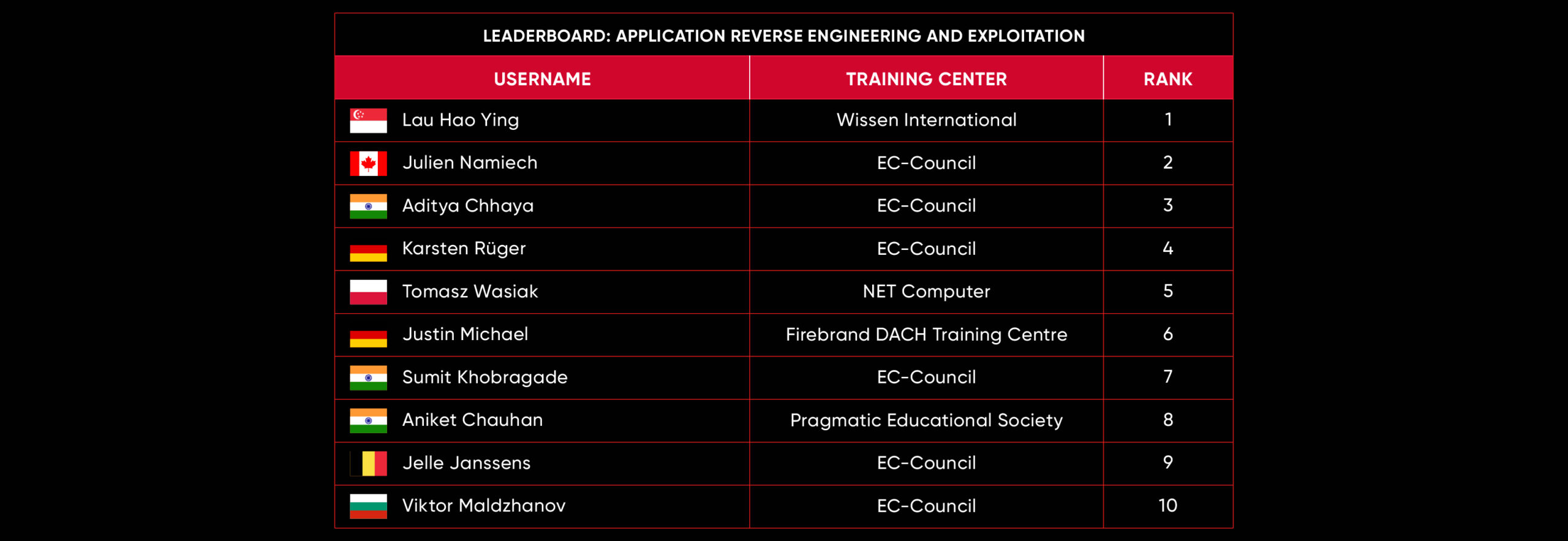
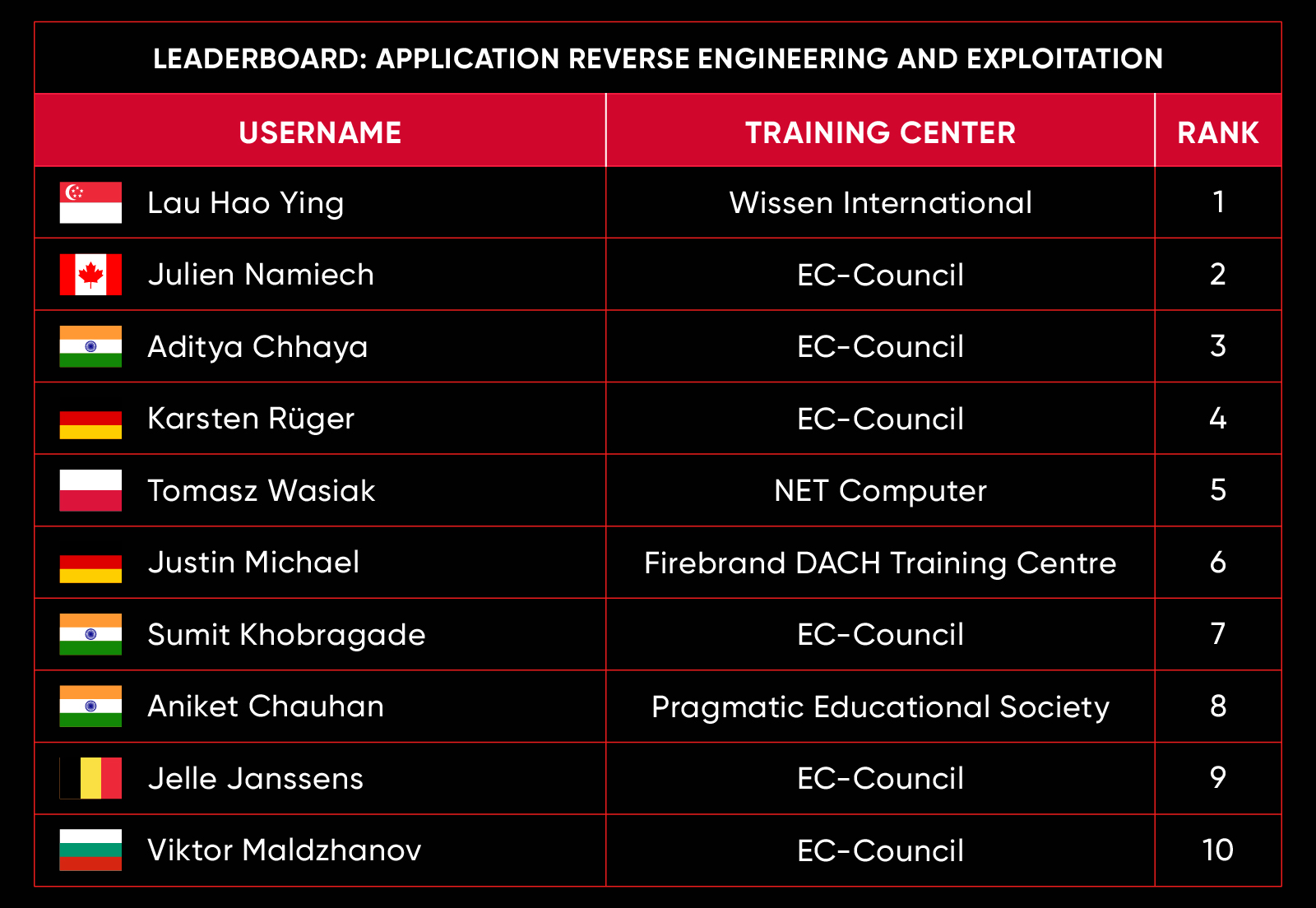
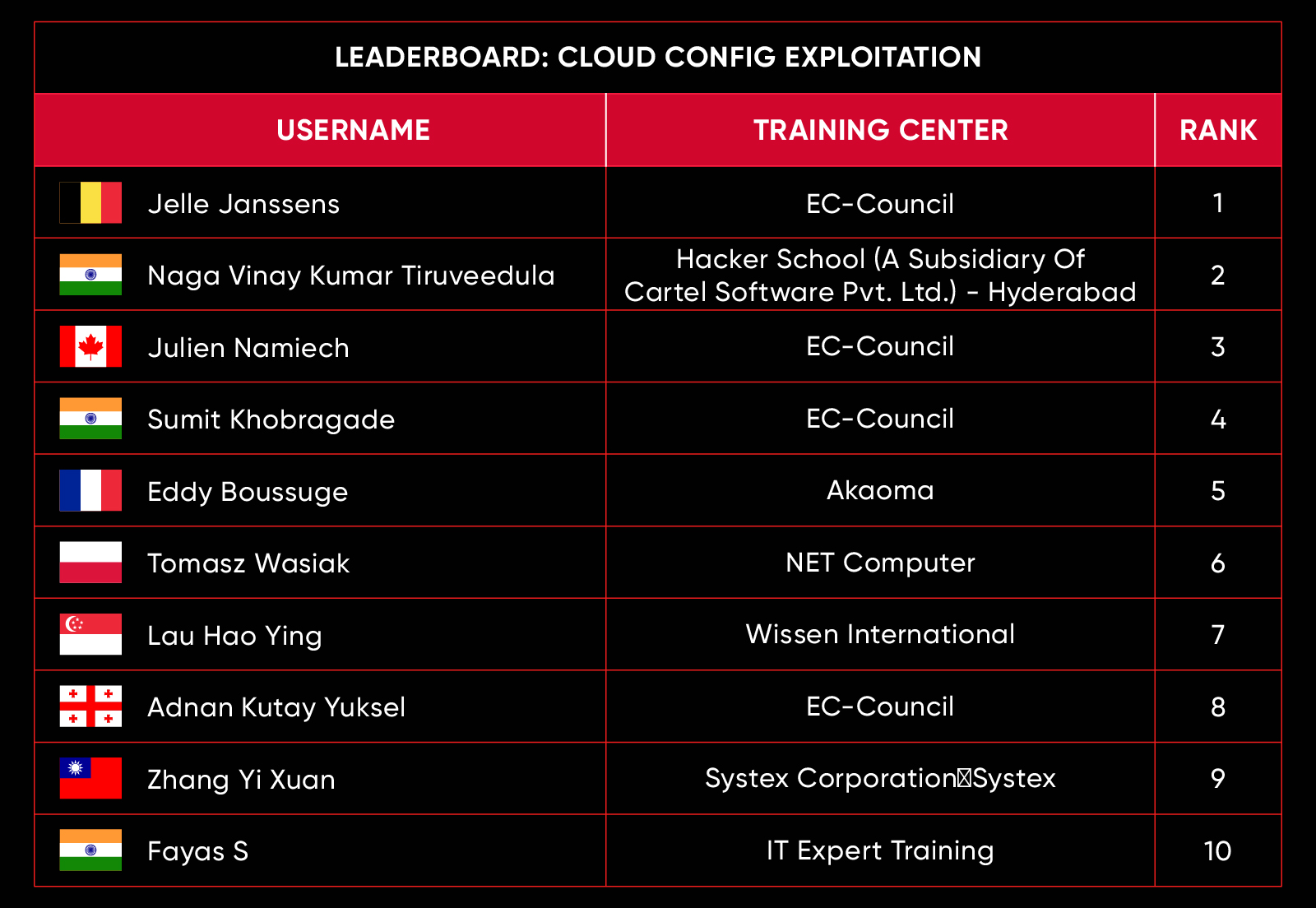
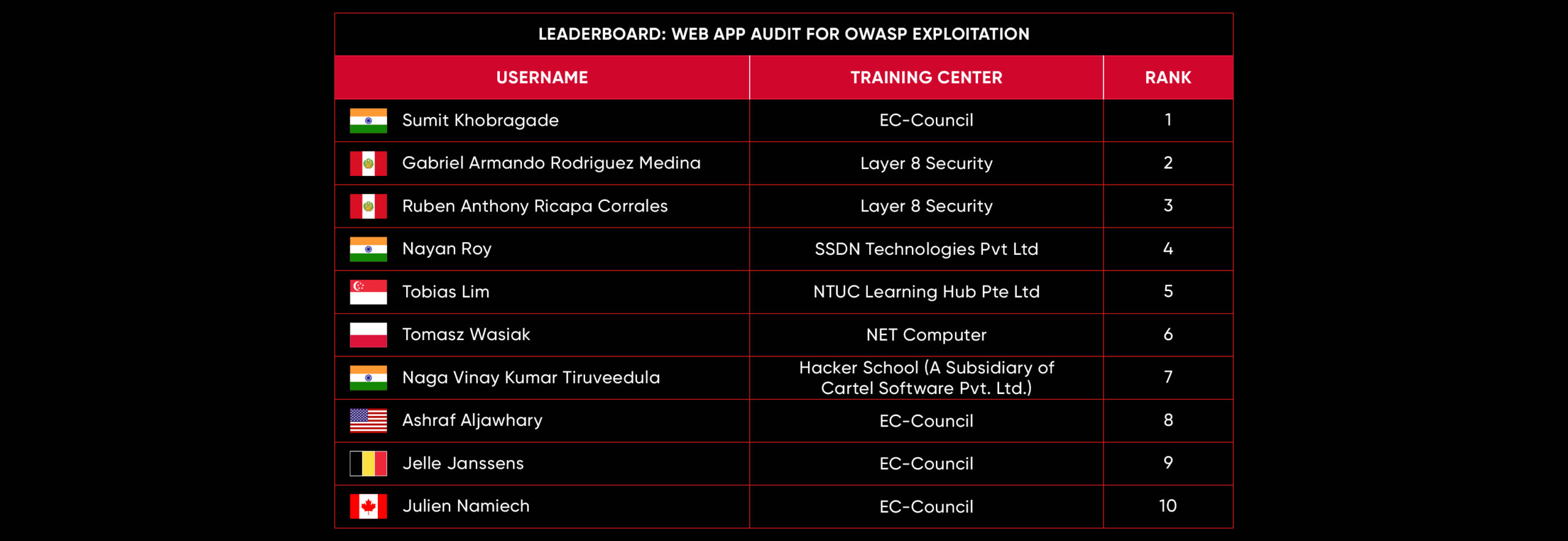
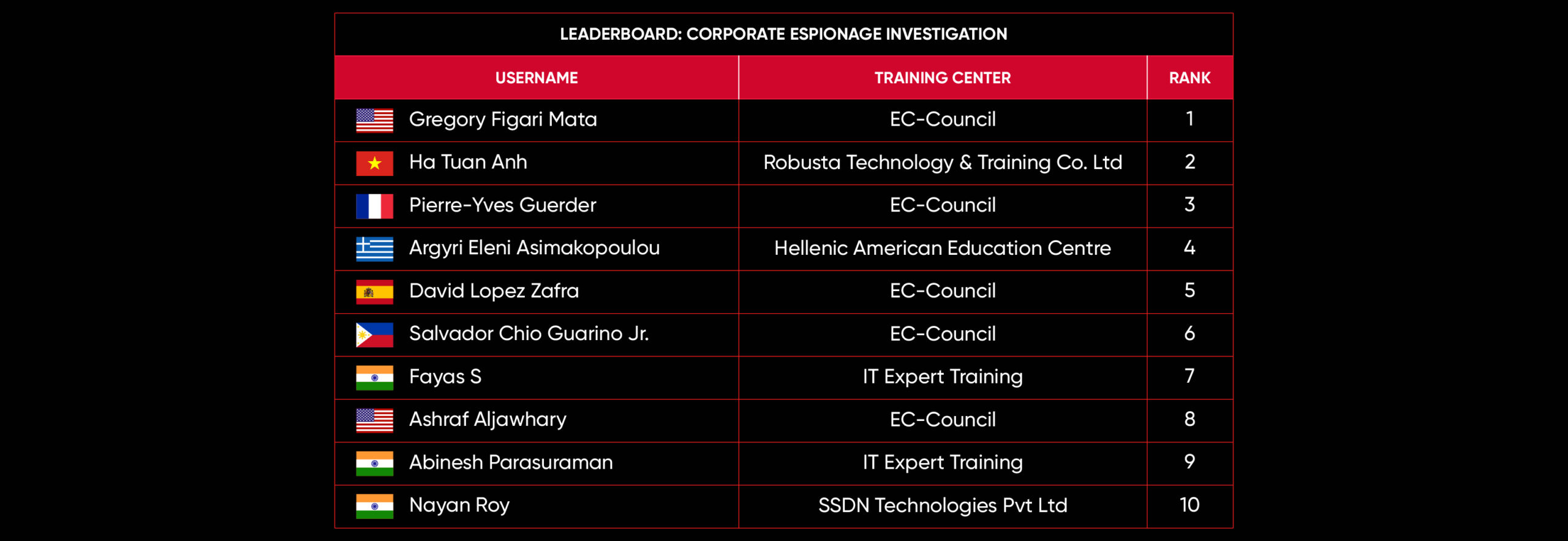
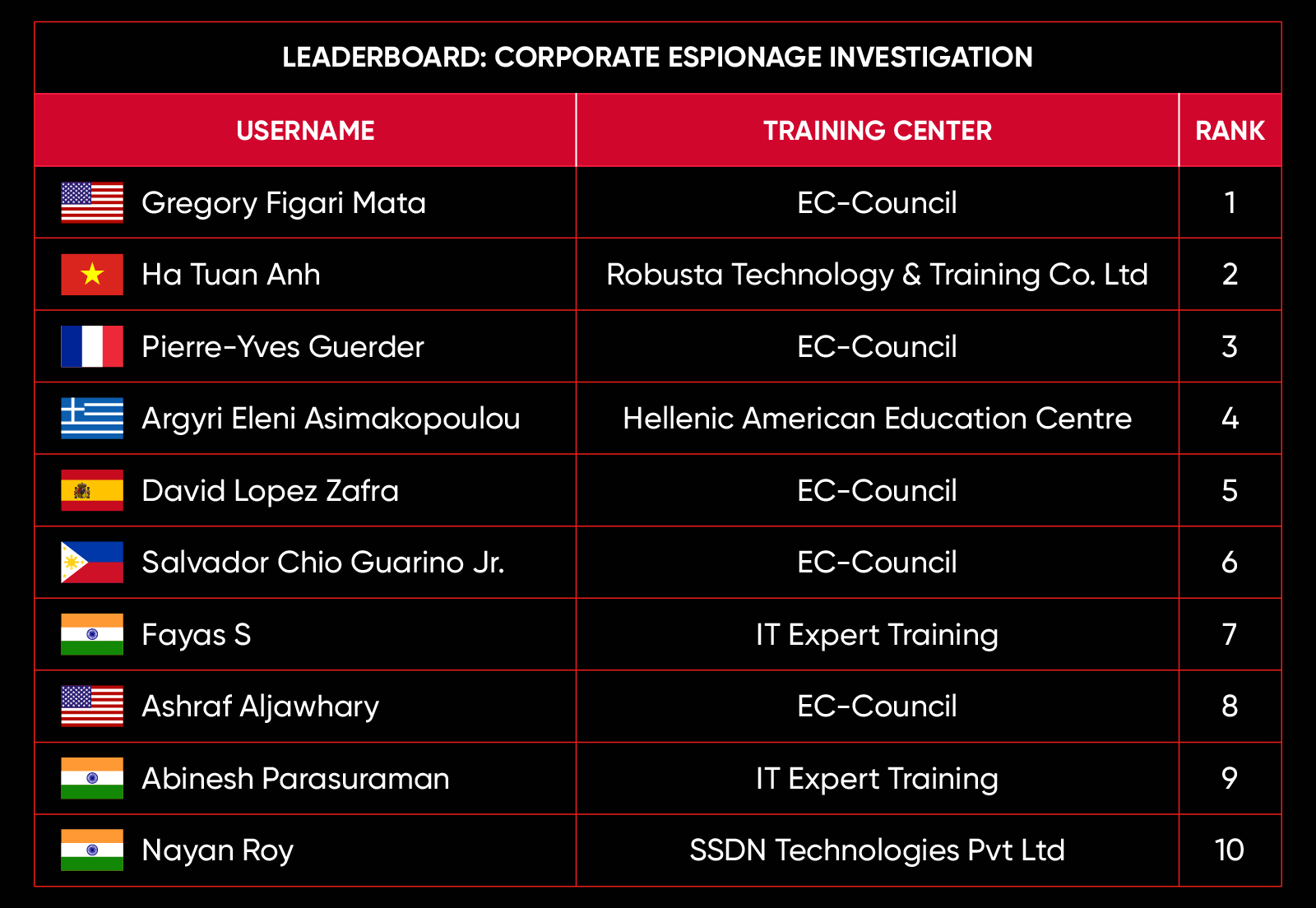
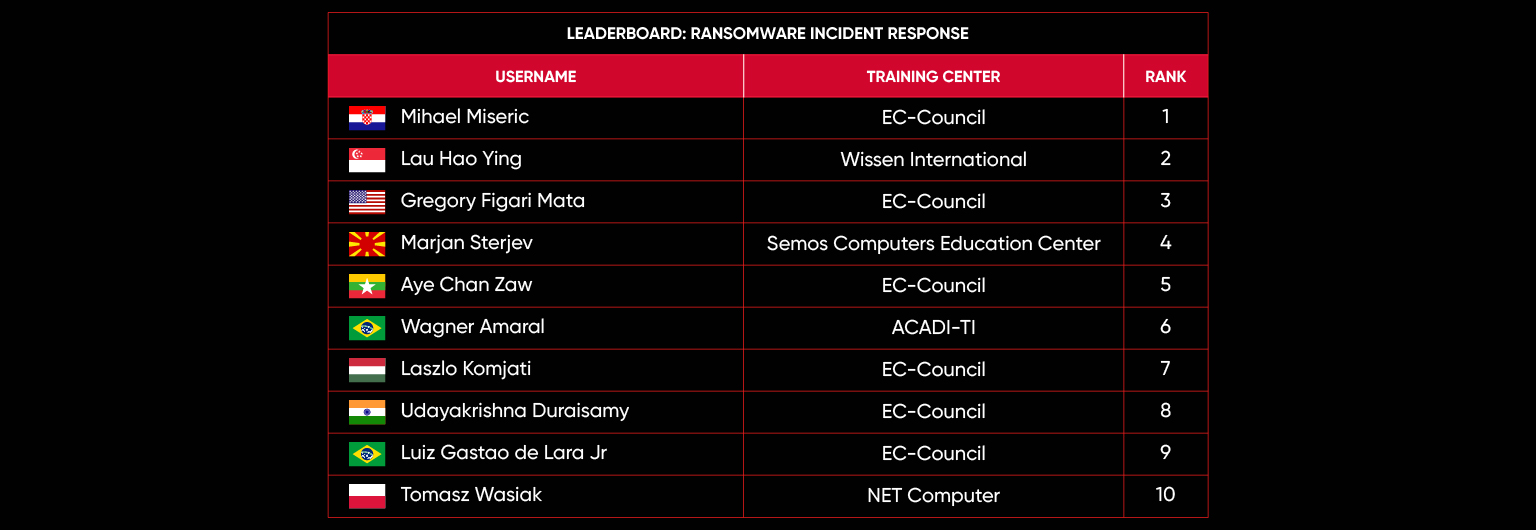
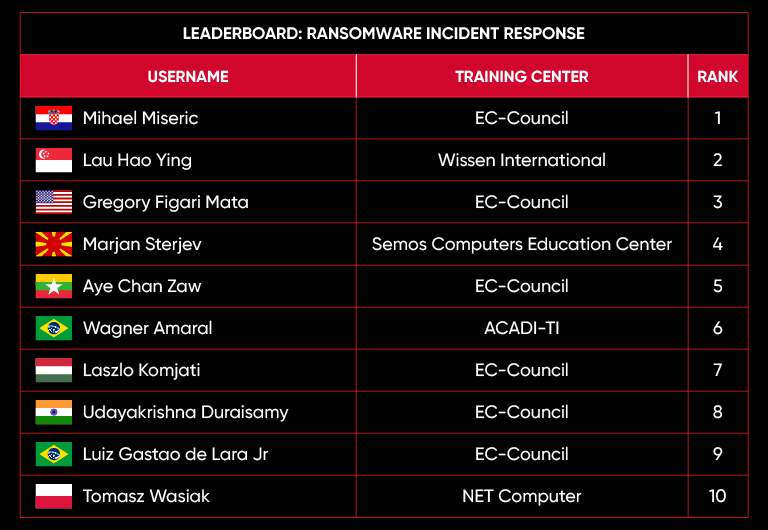
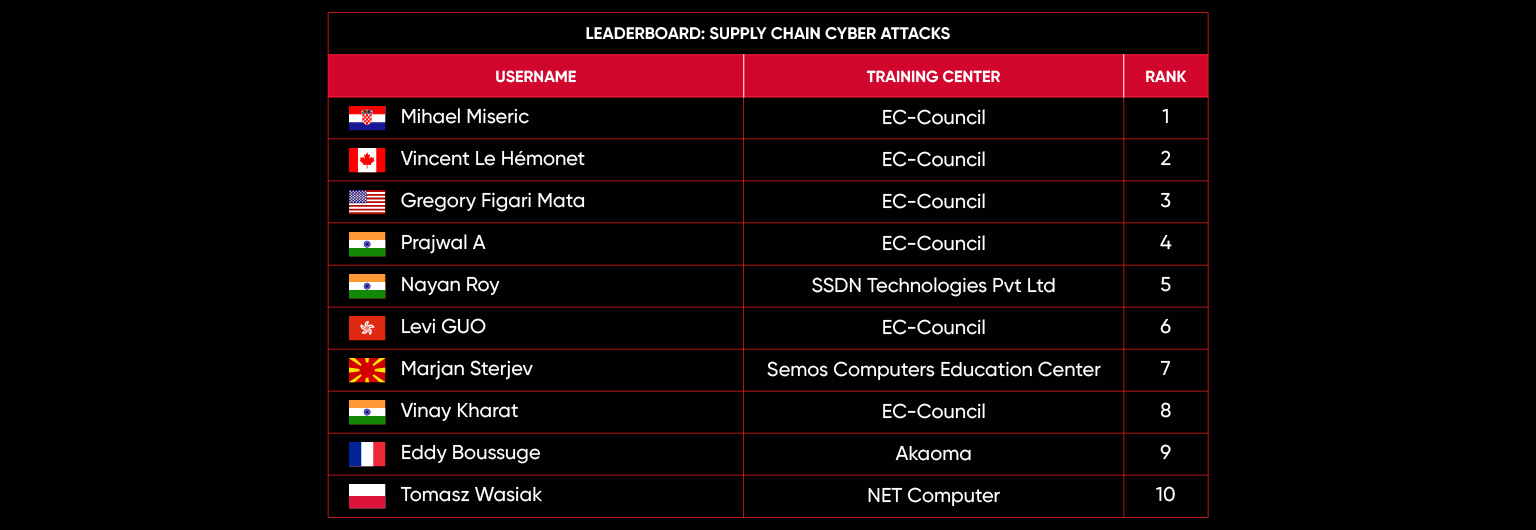
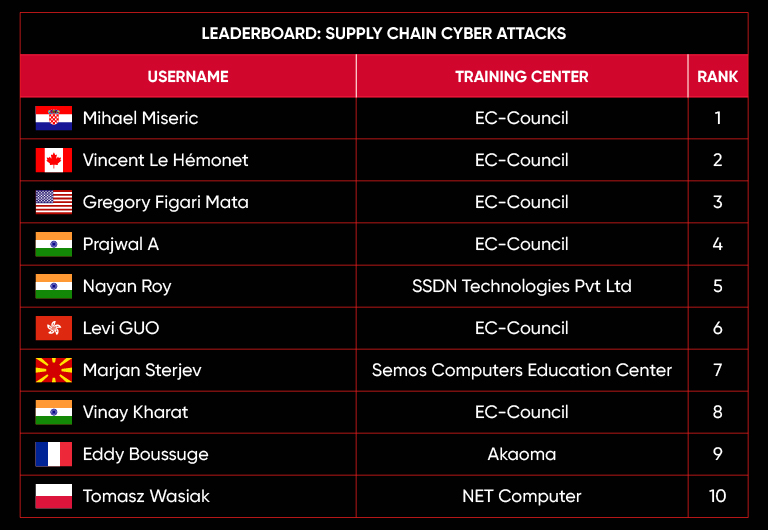
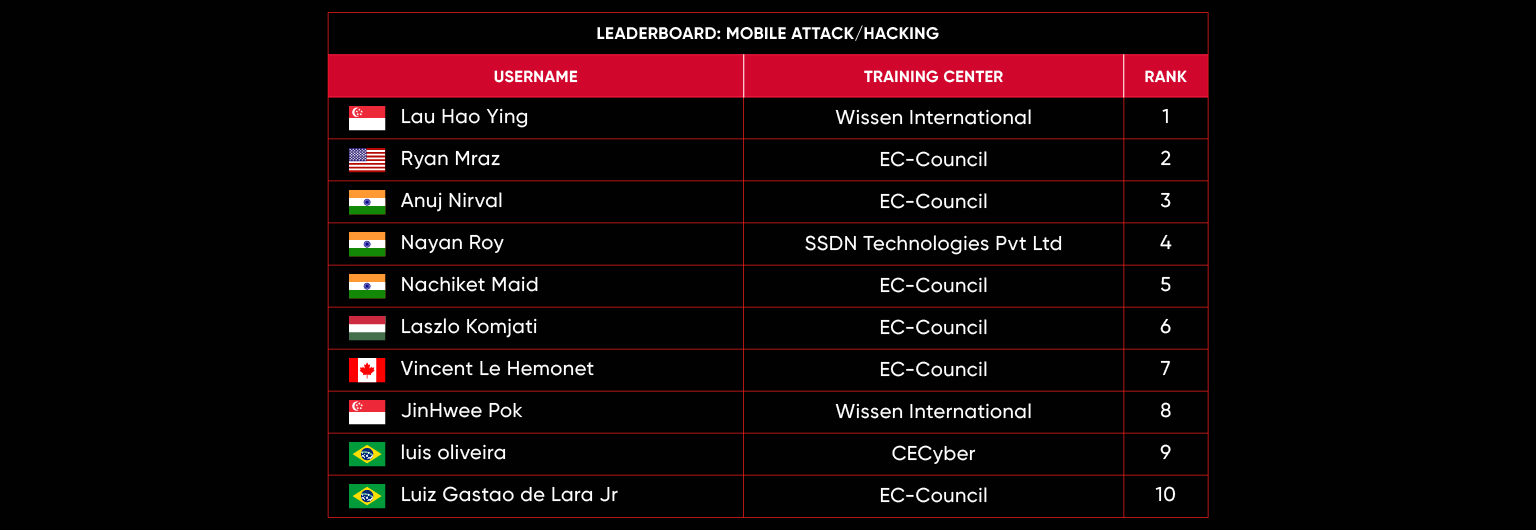
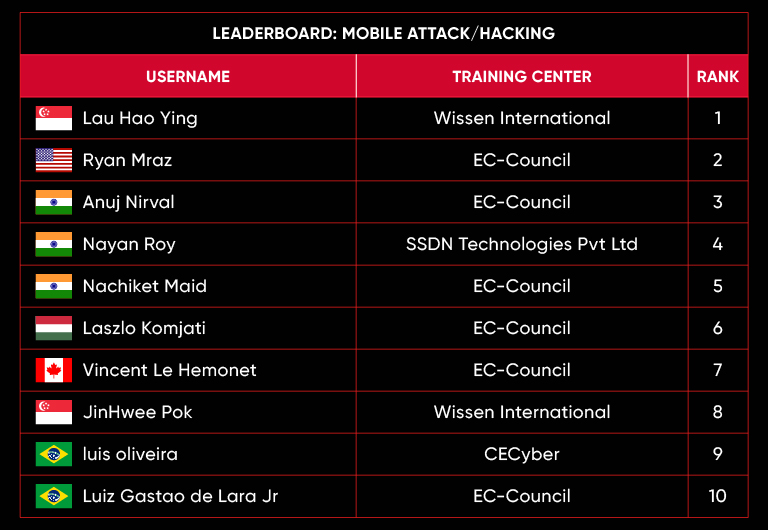
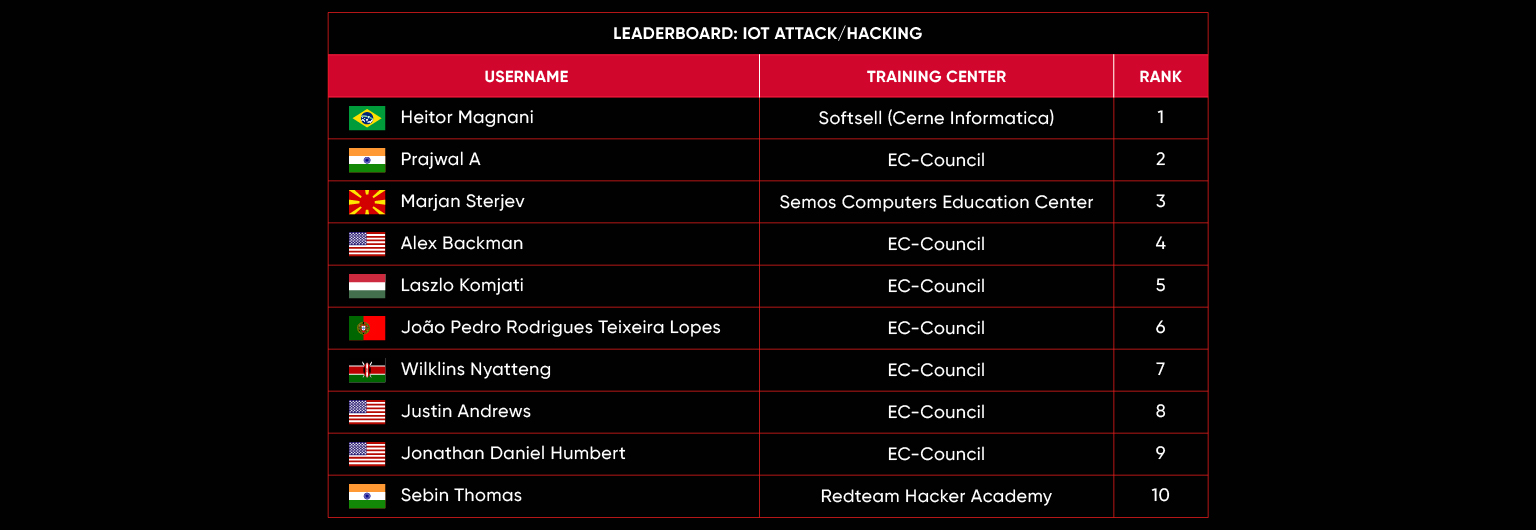
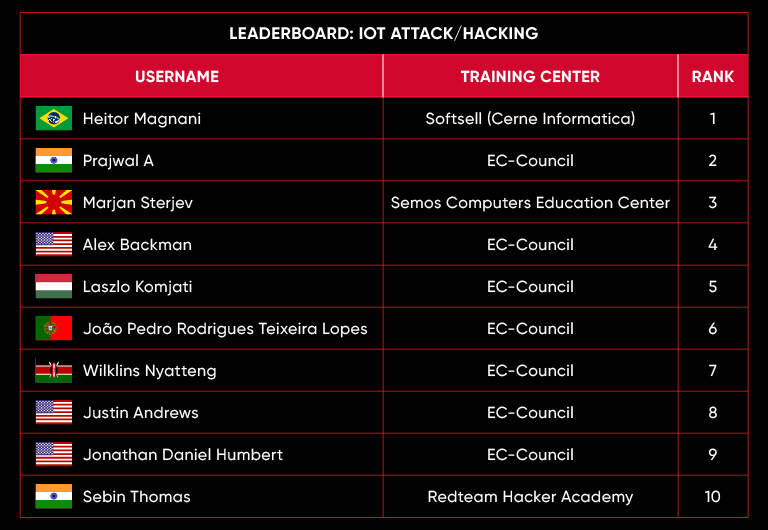
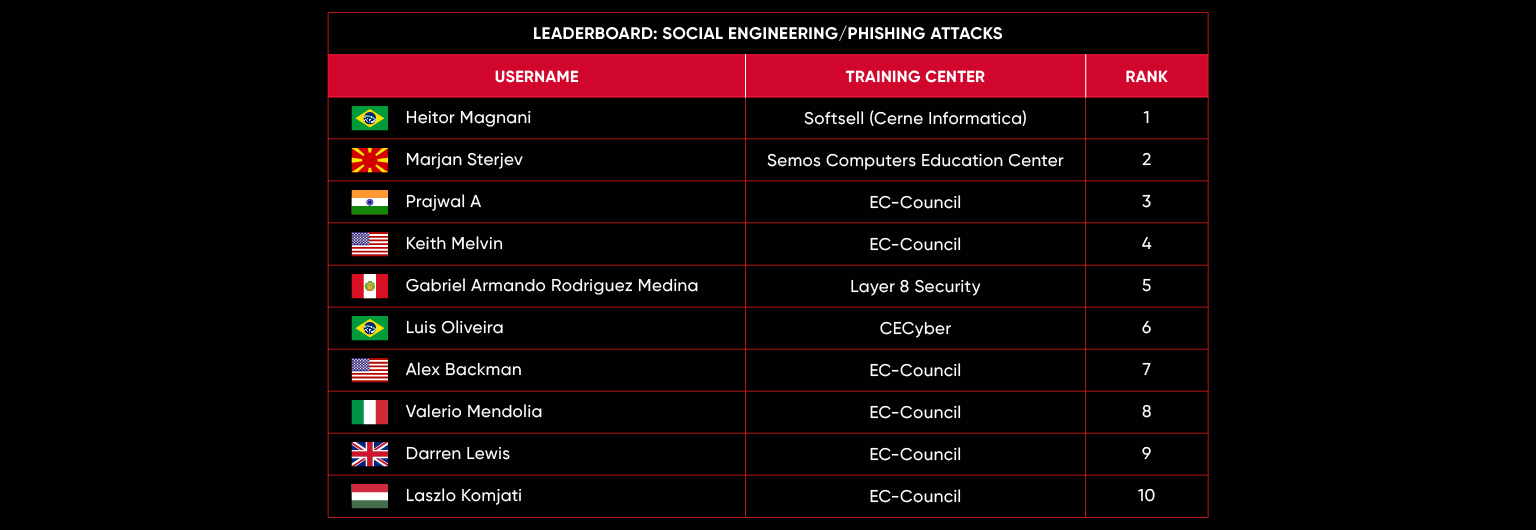
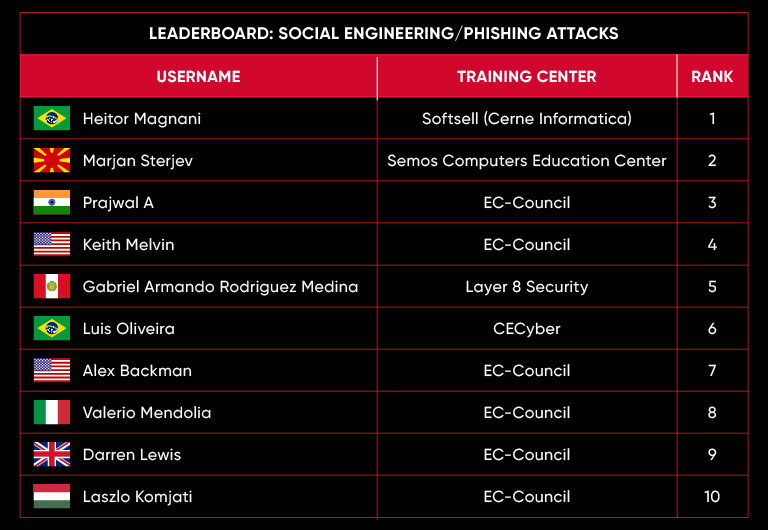
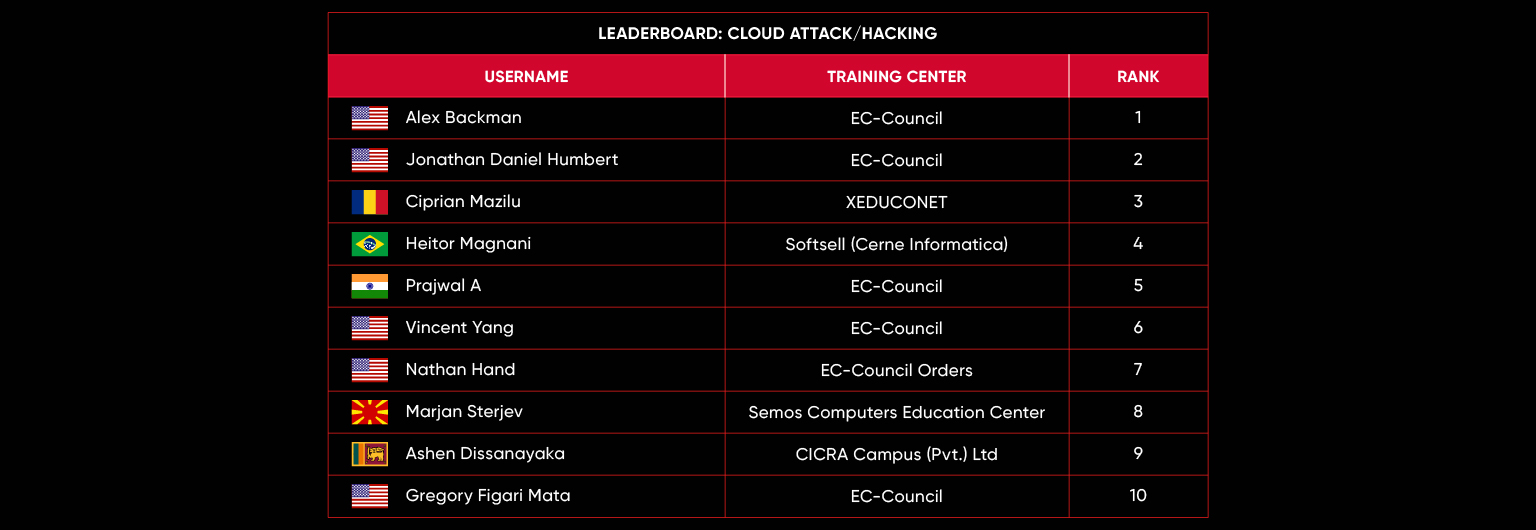
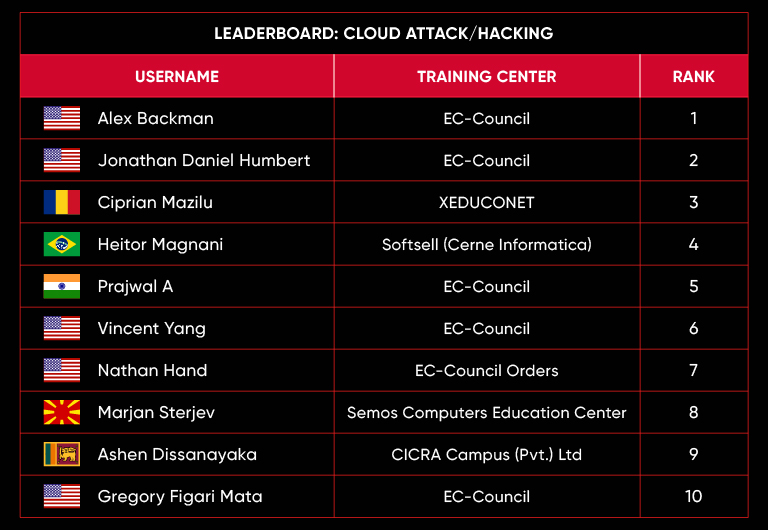
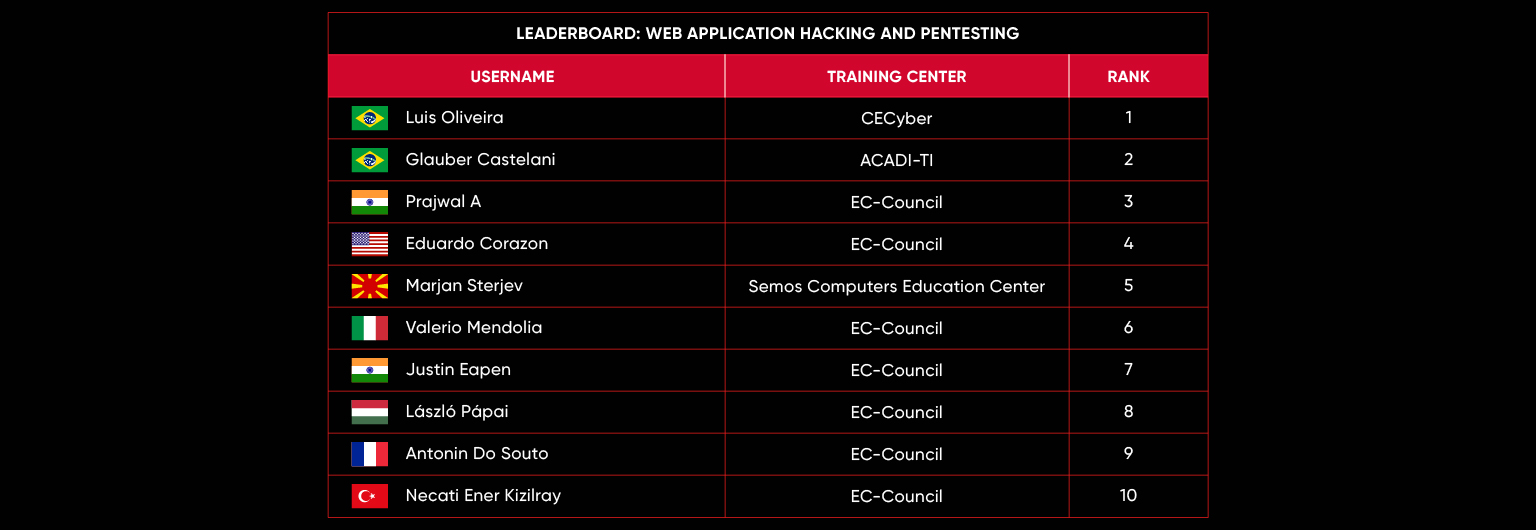
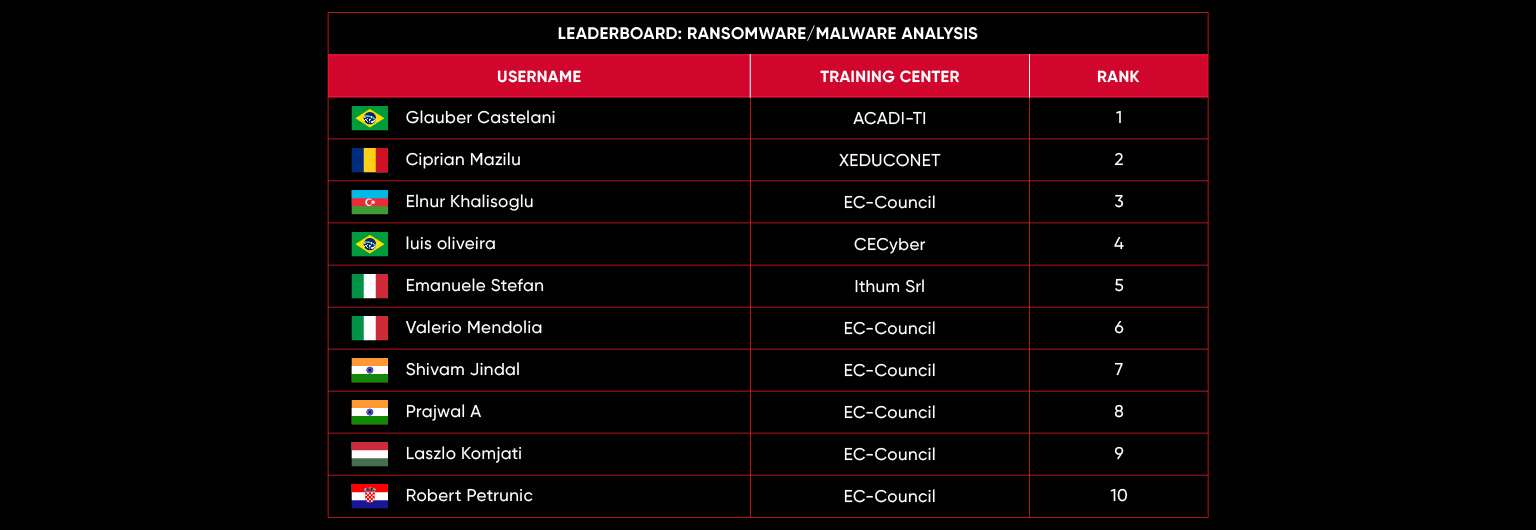
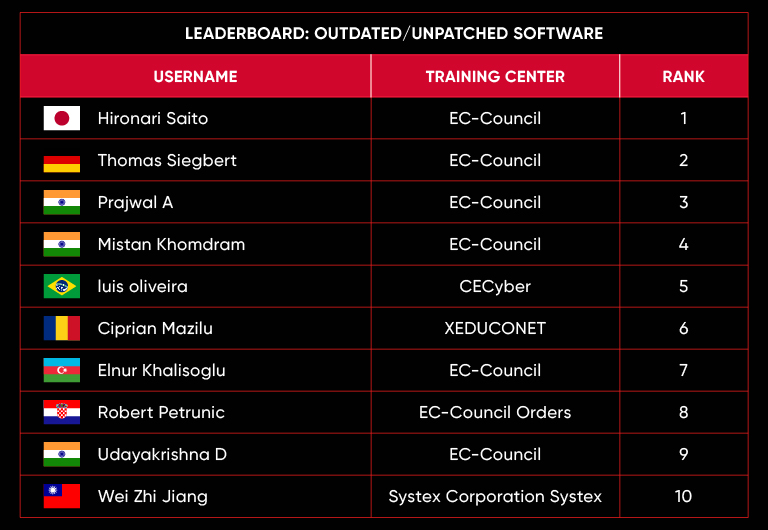
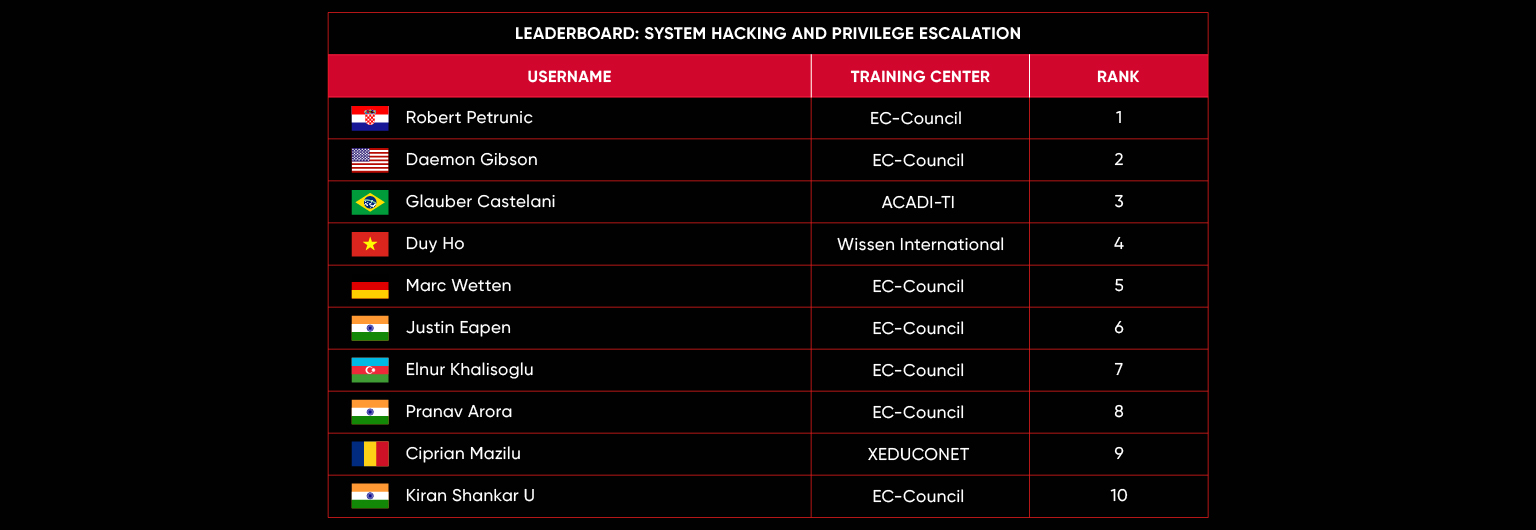
C|EH Compete Leaderboard





Why C|EH Global Challenges?

Gain Skills
- 20 Modules
- Over 221 hands-on labs to practice attack vectors and hacking tools
- 550 attack techniques
- Over 4,000 hacking and security tools
- Labs to Practice AI-driven tools and skills
- AI-integrated skills in the 5 phases of the ethical hacking framework
- Learn how to hack multiple operating systems
- More than 50% of training time is dedicated to labs

Gain Experience
C|EH Knowledge Exam
- 4 hours
- 125 multiple-choice questions
C|EH Practical Exam
- 6-hours
- 20 real scenario-based questions
Both Exams:
ANAB ISO/IEC 17024
US DoD 8140 Accredited

Gain Recognition
- Conduct A Real-World Ethical Hacking Assignment
- Apply The 5 Phases
- Reconnaissance
- Scanning
- Gaining Access
- Maintaining Access
- Covering Your Tracks

Gain Respect
- New Challenges Every Month
- 4-hour CTF competition
- Compete with your peers worldwide
- Hack your way to the top of the leaderboard
- Focus on new attack vectors
- Exploit emerging vulnerabilities
- Continuous learning platform
Learn About the FAQs and the Official Rules of the C|EH Ethical Hacking Global Challenges
FAQ's
Official Rules
FAQ's
- Log in to your ASPEN account. Click here to access ASPEN.
- In the C|EH v13 Competitions pane, you can view Current, Future, and Past competitions by clicking on the arrow (˅) icon.
- To participate in a competition, expand Current Competition and click the + icon.
- Read the competition scenario and click Compete. Note: By participating in the C|EH competitions, you agree to the challenges’ rules.
- Ensure that the Console toggle button is turned on and your nearest lab launch location is selected. Click Play.
- Wait while your lab range is being built.
- Read the about the competition and scenario carefully, then click Launch to participate in the competition.
- In the C|EH Competition console, click Red Flags. This will open competition flags in the right pane.
- Use the console machine to find the answers to the flags, enter the answer in the Answer field, and click Submit.
- Once you have found and submitted answers to all the flags, click Finish to close the cyber range.
C|EH Global Challenges are an exclusive benefit for students of C|EH Version 13. Included with C|EH Elite access, our students and certified members have access to each monthly competition through their student dashboard.
As a student of C|EH v13, you’ve already prepared to compete! Going through C|EH has taught you the tactics, techniques, and procedures necessary to be successful in the C|EH Global Challenges. Though the flags will be challenging, you will apply what you learned during C|EH to solve each flag. Between the coursework, labs, practice time, and Engage range, you can be confident in your skills as an ethical hacker. Trust your training and use it to compete!
You will be connected live to real machines in the EC-Council Cyber Range. This is not a simulation. However, you are flying solo. Each time you connect to the C|EH Global Challenges, you will be in an isolated competition environment. Your machines are yours, and there are no other players in your boxes. The scoring system works by comparing the results of each individual player, but you will not be playing head-to-head in your environment.
Each time you compete, you will have a series of flags (questions that require answers). To solve the flags, you must perform activities in the live target environment. Submitting each answer will award you the points associated with that flag. Time matters and so do hints. Not all competition flags provide hints, but for the ones that do, each use of a hint will deduct points from your flag score. Arriving at a correct answer will lock in your score during the 4-hour competition period. Leaderboards are calculated based on total points earned and overall time spent completing the challenge. To claim your spot at the top, you must be correct, proficient, and precise on the range.
Equipment requirements are basic for our competitions because all targets are located in our cloud infrastructure, including your attack platform. You will need a stable internet connection and an HTML5 capable browser to connect to our environment. All the tools required to compete are provided in the platform that launches when you click Compete.
Competitions are hosted in our cloud-based Cyber Range. Clicking Play will initiate our launch process. It typically takes 1 to 2 minutes to generate your attack console and all target machines required for the event. As you connect to the console view, you will see the desktop of your attack console and a set of flags on the right side of the screen. As you work in the remote view of the machines, you will arrive at solutions to each flag challenge, which you will enter in the answer box to achieve your score.
CTF stands for Capture-the-Flag. This gamified style of challenges provides you with objective-based flags. To get the answer for a flag, you must perform hands-on activities in the target network. Each flag is tracked and has a point value. Our flags are mapped to cyber competencies that you would use in your regular day as an ethical hacker.
Leaderboards and performance metrics are available to you in the C|EH v13 dashboard in ASPEN, EC-Council’s student management system. You can select current or previous month’s challenges and see how you placed overall. You can also see individual flag performance with benchmark comparisons to the total possible points and average points earned by other participants.
Yes! Support is only a click away throughout your competition. When you launch into the competition, a small “Chat with us” support option is available on the screen. It will connect you directly to our customer support team. While they are trained not to give you hints or answers on the content, they are able to support you with any platform-related challenges. Our professional support team is always standing by 24/7 to support whatever challenges you face.
For over 20 years, EC-Council has trained and certified information security professionals as Certified Ethical Hackers. For the past few years, we have been working to provide the best in hands-on experiences with labs and challenges to ensure our classroom experience mimics the real, day-to-day experiences of our Certified Ethical Hacker alumni and certification holders. One common piece of feedback we have received from over 80% of our certification holders is that they dedicate time each week to learning new skills and staying ahead of the curve. Competition drives that research, practice, curiosity, and discipline. With our new CyberQ Cyber Range, we wanted to provide a place to drive our Ethical Hackers to be the best they can be through challenges, applied knowledge, new topics, and changing conditions and standards while bringing in the spirit of fun competition. Our goal with the C|EH Global Challenges is to inspire the continuous development of our professional certified audience and give them an accessible, safe place to test out new tactics as well as expose them to live threats and vulnerabilities as they continuously improve.
There is no prize better than knowledge and experience. Our competitions are not sponsored, and there are no sales gimmicks. The C|EH Global Challenges are provided by EC-Council as a benefit to C|EH Elite students and certified members exclusively for the sole purpose of continuous education, skill development, and pushing our Ethical Hackers to be the best they can be.
Official Rules
The C|EH Global Challenges are open to all C|EH Certified Members with active access to C|EH Version 13 or higher.
The C|EH Global Challenges consist of one (1) cyber challenge each month. Challenges will be available at 00:00:01 UTC on the first calendar day of the month, and each challenge will conclude at 23:59:59 UTC on the last calendar day of the month. Players will be responsible for determining the translation to their respective time zones, given that all start and end times are calculated on the UTC basis as noted above.
Each challenge will have a maximum time of 4 hours. Challengers will not have the ability to pause or restart challenges. Each challenge attempt must be completed from start to finish in one 4-hour session. Once the 4-hour time limit is up, the challenge will automatically end, at which point scores are considered final regardless of the challenger’s progress.
Each challenge will allow one (1) attempt only. Challengers may activate their attempt at any point during the month. Initiating a challenge attempt during an active challenge month will consume the single attempt allotment, and challengers will not be able to initiate their next challenge until the following calendar month when the next challenge becomes available.
Challenge scoring is calculated through the submission of flags. Challenges are hosted in EC-Council’s CyberQ Platform, which generates the live challenge environment with the required tools and targets as well as a flag submission engine. Questions are posed to challengers, and they must find the correct answer to the question by evaluating the target systems and carrying out tactical cyber activities to determine the correct response. In some cases, hints are provided but may reduce the overall points issued for capturing the flag, thereby reducing the candidate’s overall score.
All C|EH Global Challenge scoring metrics are available through the C|EH v13 ASPEN dashboard tile. Near the top of the screen is a section titled “C|EH Competition Dashboard.” Each Challenge you participate in has available metrics centered around your performance. You may use the select boxes to filter by challenge, month, and year. Once you have selected the appropriate challenge, the scenario will be displayed, explaining the context of the challenge as well as your performance metrics as specified below.
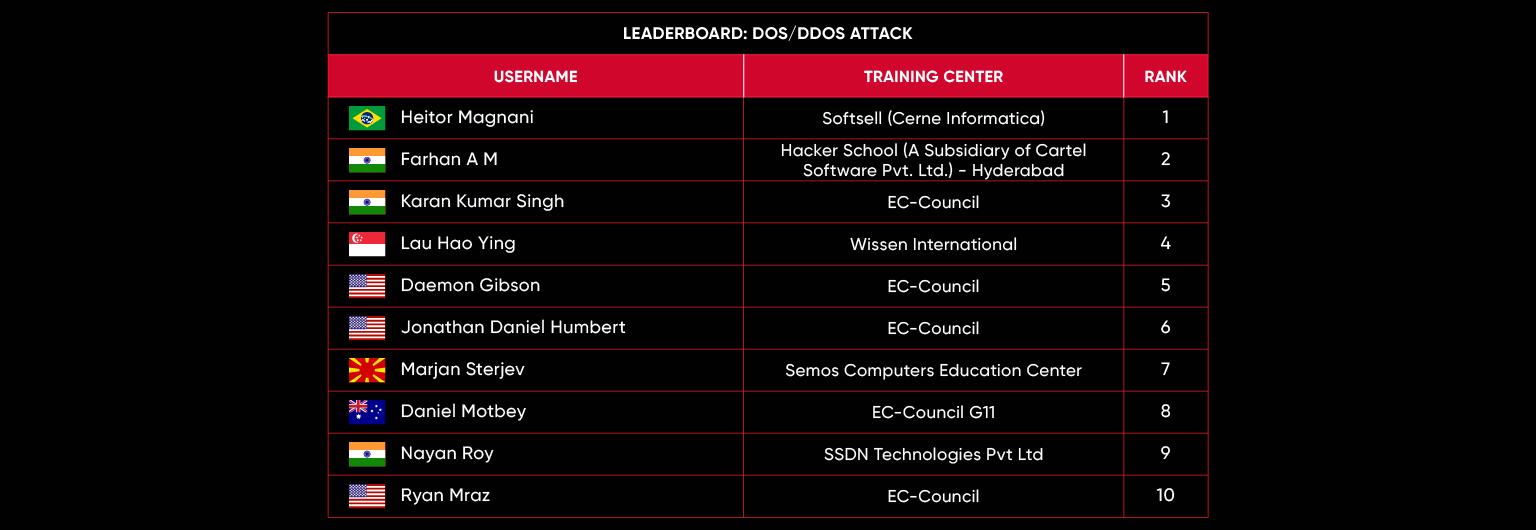
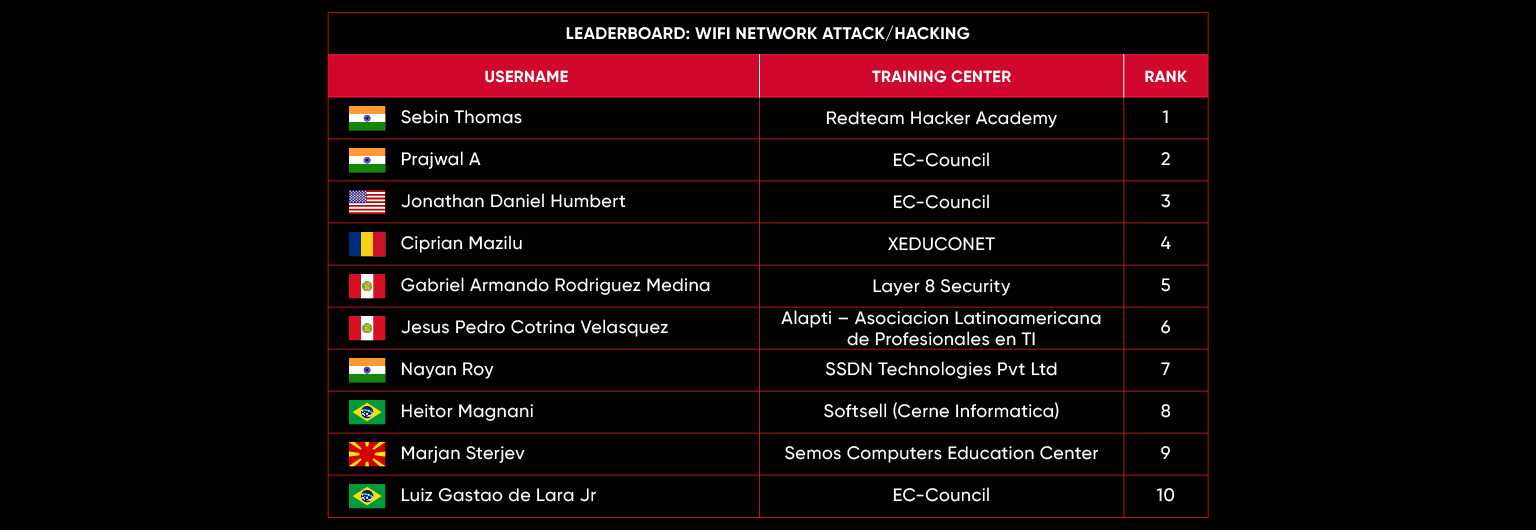
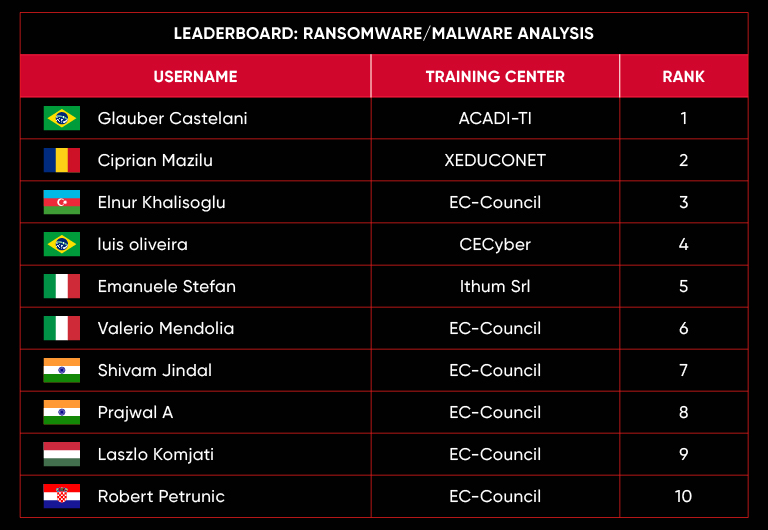
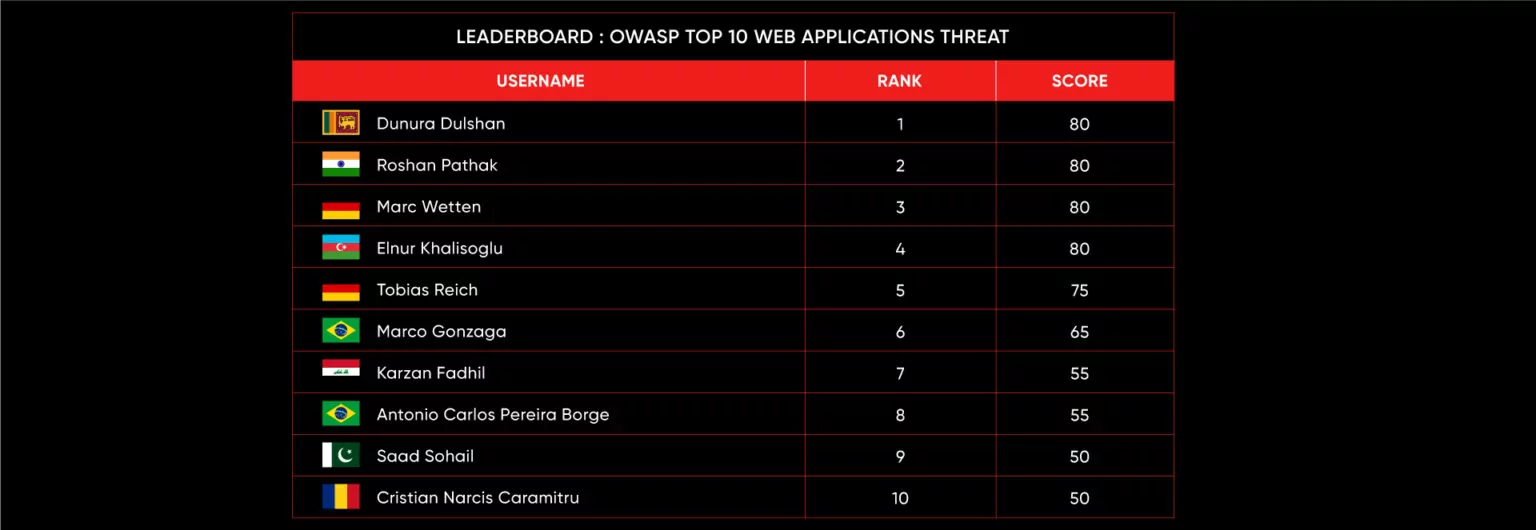
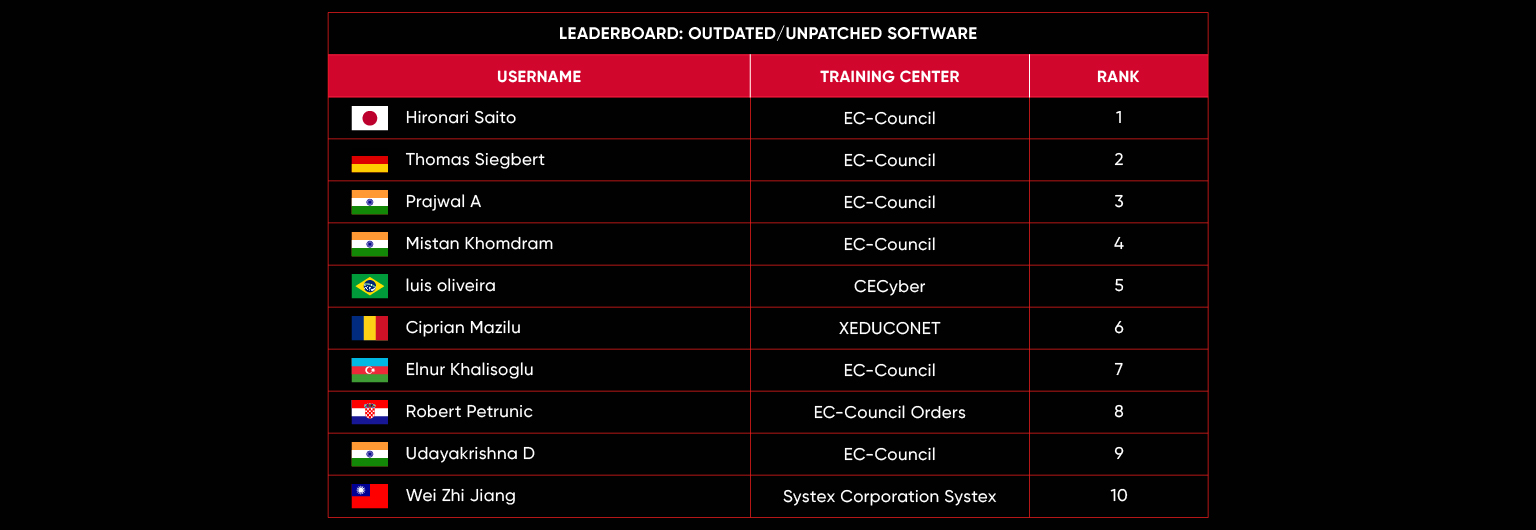
Leaderboard – The Leaderboard provides a view of the top 10 challengers by rank and score, as well as your position either in the Top 10 or in a lower rank based on your performance in the challenge.
Rank –Rank is the relative position of your score in the challenge to other Certified Ethical Hackers who have completed the same challenge. Scores combined with time to complete provide a speed and accuracy variable to determine your overall rank against other challenges.
Score –Score is a number calculated by adding the value of each flag submission you completed correctly or partially correct during your challenge attempt. Each question has a numerical value. In order to earn points on a flag submission, you must answer the question correctly. Some flag values are higher than others, depending on the complexity of the question or task required to determine your response. Once all flags are submitted, your total score is calculated by adding each individual submitted flag’s value together.
My Rank
Rank Position – Your current rank or position is a sequential numerical value that specifies where you stand in relation to other players who have attempted the same challenge.
Change in Rank Position – Throughout the duration of the challenge, your rank is subject to change should another Certified Ethical Hacker score higher than you or complete the entire challenge in a shorter time with as many or more points.
My Score vs. Total Possible
My Score – This is the same metric described above under “Leaderboard.”
Possible Score – This value represents the highest possible score you can earn in a given challenge. It is the maximum available point value from all flags in the challenge.
Overall Percentage Calculated as (My Score/Possible Score)*100, the result is shown as a % value.
My Flag Performance vs. Benchmark
This chart represents your performance for individual flags in the challenge. The graph provides a simple benchmark comparison of your score on a flag-by-flag basis to the total possible score, and the average score achieved by all players in the challenge.
My Score –This is the number of points you earned on each individual flag.
Possible Score –This is the total possible points available for each individual flag.
Average Score –This is the average score earned by all players in the challenge.
All challengers are required to utilize a system with an HTML5 (or newer) capable browser. Challengers must also have a stable, preferably high-speed internet connection. All activities will be carried out in a controlled, virtualized environment. Though challengers are evaluating live target systems and utilizing live attacks, scanners, and tools, all traffic is contained to the challenge environment. No processes are run on challenger machines aside from their active connection to the CyberQ Console via a web site.
EC-Council reserves the right to disqualify a participant at its own discretion. Examples of events leading to disqualification can include but are not limited to: cheating, violating the terms and conditions of use, violating the End User License Agreement in any way, sharing flag answers with others, broadcasting or streaming their attempt, and/or abusing other participants in the challenge in any way, shape, or form.
If a player is disqualified from the C|EH Global Challenges, their score and rank data will be removed from the event in which they were disqualified, and participation in future global challenges will be prohibited. Candidates will be notified in writing at the official email address used to register for their account in ASPEN.
Accreditations, Recognitions & Endorsements




