Stay Aware, Stay Secure.
Lack of security awareness is a pathway to disaster. Stay ahead in the game with EC-Council’s end-to-end cybersecurity awareness training solutions.
Our training is ideal for all members of an organization, including employees, contractors, temporary workers, and everyone else who completes authorized functions online. Equip them with the information and skills needed to defend malicious actors and secure their organization’s assets from damage and loss.
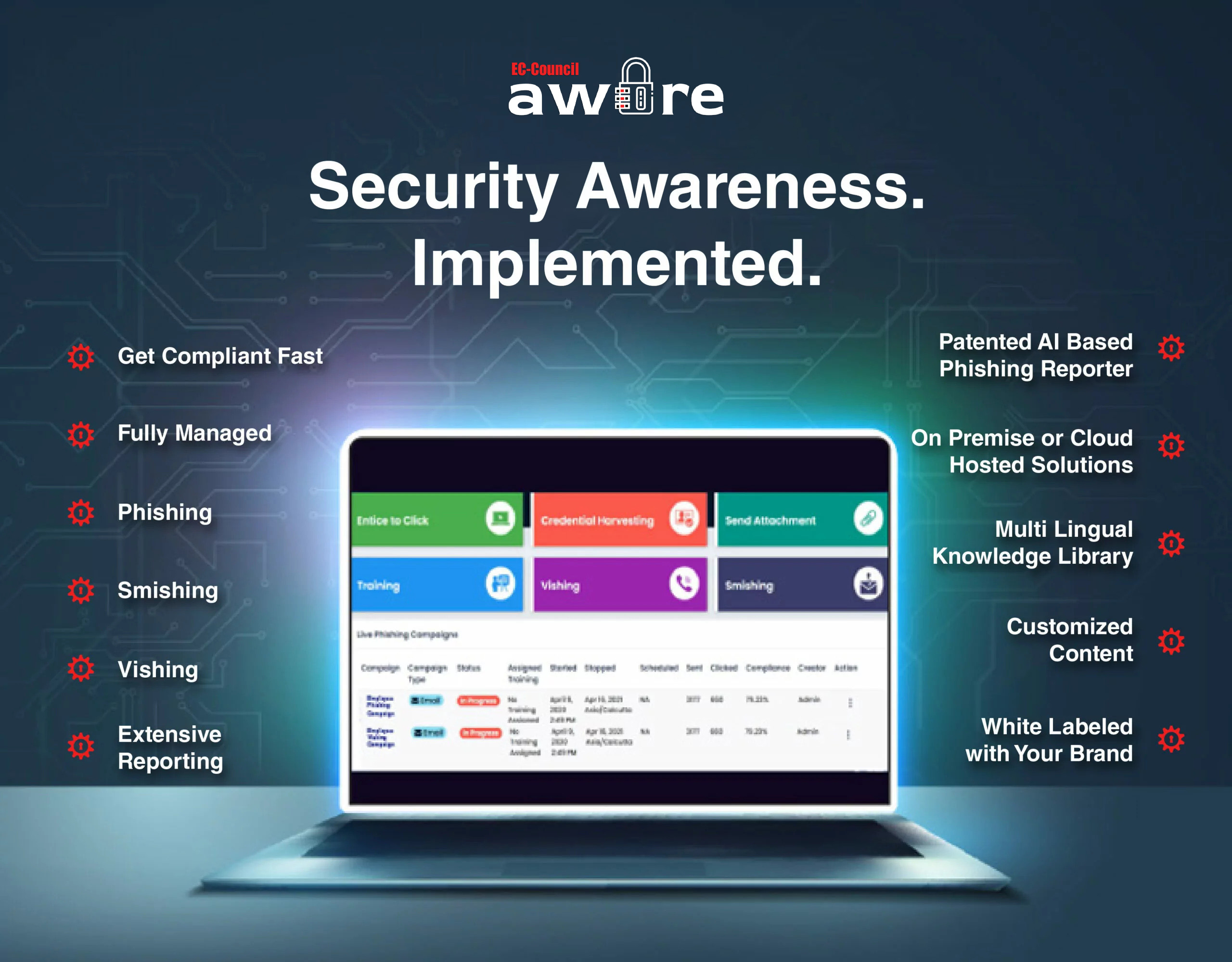
Learning Management System
Compliance Based Training
Extensive Reporting
AI Based Phishing Reporter
Our Solutions
Email Phishing
Train and educate your teams to identify and report phishing attempts. Our comprehensive security package includes phishing simulations and security awareness training.
Vishing
We equip your team with the knowledge and skills they need to defend against vishing attacks through simulation exercises and awareness training.
Smishing
Increase your team’s security awareness through simulations and training and help them to defend against Smishing or SMS Phishing attacks.
Implement Security Awareness with a few clicks!
Schedule a Demo With Us!
What’s Covered in the Demo?
- A complete walkthrough of our intuitive platform
- On-demand customizable options
- Targeted phishing simulations by risk profile
- Integrated gamification for enhanced user participation
- Advance reporting dashboard with key metrics
Fill out the form below to see the security awareness platform in action
"*" indicates required fields
COUNTRIES
CUSTOMERS
SIMULATIONS
EMAILS SENT
Key Features
Training Videos
Leader Board
CheckAPhish
Challenge
Phishing Simulations
Game Time
Frequently Asked Questions
Yes. We offer all prospective clients the opportunity to test our product. Please contact us and we will gladly provide you with a demo. We will also answer any questions that you may have regarding our product.
No, our platform is very easy to use. Even a novice security professional will be able to use it with minimal training.
It depends on how your test is set up. There are many options available. One option is you can provide a message to the user or redirect the user to a landing page with training content related to the area that needs improvement.
It depends on how your test is set up. There are many options available. One option is you can provide a message to the user or redirect the user to a landing page with training content related to the area that needs improvement.
Of course! We will present multiple scenarios for you to choose from. We can also customize phishing emails upon request
Yes. Our dashboard allows you to monitor the progress of your campaign in real time.