The Associate C|CISO Program is a professional certification program that equips cybersecurity professionals with the fundamental knowledge required for information security leadership. It is designed specifically for candidates aspiring to become C-suite leaders by training themselves in the 5 domains of the Certified CISO (C|CISO) program, even if they fall short of meeting the minimum 5 years of experience in 3 of the Certified CISO domains.
We Are Trusted By Many Student & Non Student
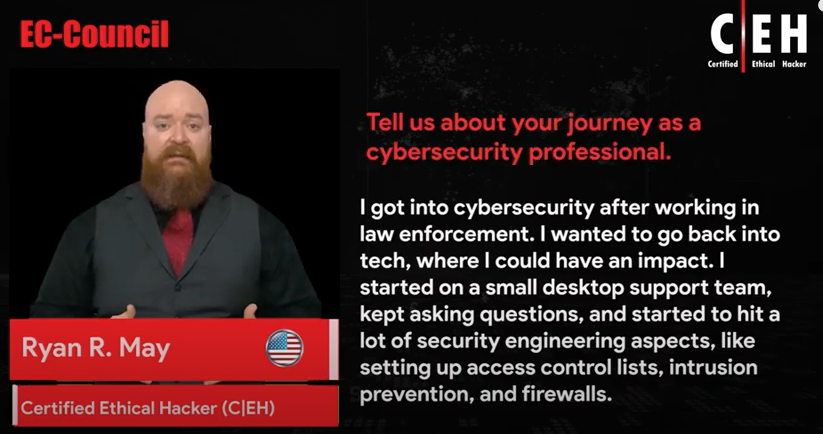
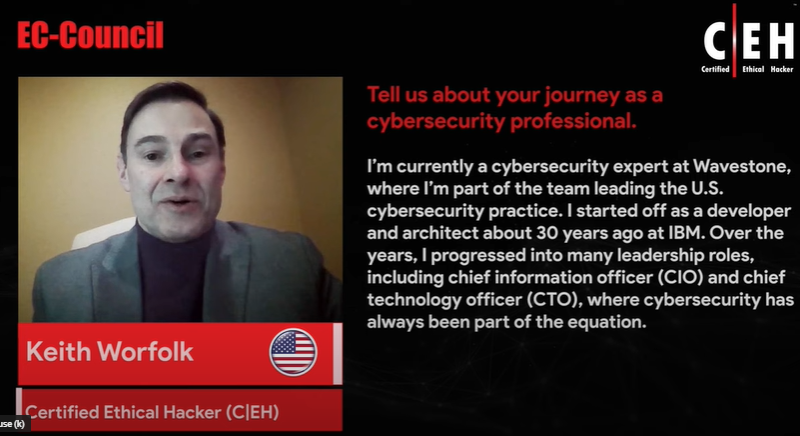
For more than 15 years, EC-Council’s Cybersecurity programs have empowered cybersecurity professionals around the world to exercise their training and expertise to combat cyberattacks. The Hall of Fame celebrates those individuals who have excelled, achieved, and fostered a spirit of leadership among their colleagues and peers within the cyber community.
- 97% Rated the Program topics as directly relevant to current real-world threats.
- 63% Reported a direct pay raise or promotion after attaining their C|EH Certification.
- 95% Responded being able to improve organizational security after completing the program.